-
What Is a Cyber Attack?
- Threat Overview: Cyber Attacks
- Cyber Attack Types at a Glance
- Global Cyber Attack Trends
- Cyber Attack Taxonomy
- Threat-Actor Landscape
- Attack Lifecycle and Methodologies
- Technical Deep Dives
- Cyber Attack Case Studies
- Tools, Platforms, and Infrastructure
- The Effect of Cyber Attacks
- Detection, Response, and Intelligence
- Emerging Cyber Attack Trends
- Testing and Validation
- Metrics and Continuous Improvement
- Cyber Attack FAQs
- Dark Web Leak Sites: Key Insights for Security Decision Makers
-
What Is a Zero-Day Attack? Risks, Examples, and Prevention
- Zero-Day Attacks Explained
- Zero-Day Vulnerability vs. Zero-Day Attack vs. CVE
- How Zero-Day Exploits Work
- Common Zero-Day Attack Vectors
- Why Zero-Day Attacks Are So Effective and Their Consequences
- How to Prevent and Mitigate Zero-Day Attacks
- The Role of AI in Zero-Day Defense
- Real-World Examples of Zero-Day Attacks
- Zero-Day Attacks FAQs
-
What Is Lateral Movement?
- Why Attackers Use Lateral Movement
- How Do Lateral Movement Attacks Work?
- Stages of a Lateral Movement Attack
- Techniques Used in Lateral Movement
- Detection Strategies for Lateral Movement
- Tools to Prevent Lateral Movement
- Best Practices for Defense
- Recent Trends in Lateral Movement Attacks
- Industry-Specific Challenges
- Compliance and Regulatory Requirements
- Financial Impact and ROI Considerations
- Common Mistakes to Avoid
- Lateral Movement FAQs
-
What is a Botnet?
- How Botnets Work
- Why are Botnets Created?
- What are Botnets Used For?
- Types of Botnets
- Signs Your Device May Be in a Botnet
- How to Protect Against Botnets
- Why Botnets Lead to Long-Term Intrusions
- How To Disable a Botnet
- Tools and Techniques for Botnet Defense
- Real-World Examples of Botnets
- Botnet FAQs
- What is a Payload-Based Signature?
-
What is Spyware?
- Cybercrime: The Underground Economy
-
What Is Cross-Site Scripting (XSS)?
- XSS Explained
- Evolution in Attack Complexity
- Anatomy of a Cross-Site Scripting Attack
- Integration in the Attack Lifecycle
- Widespread Exposure in the Wild
- Cross-Site Scripting Detection and Indicators
- Prevention and Mitigation
- Response and Recovery Post XSS Attack
- Strategic Cross-Site Scripting Risk Perspective
- Cross-Site Scripting FAQs
- What Is a Dictionary Attack?
- What Is a Credential-Based Attack?
-
What Is a Denial of Service (DoS) Attack?
- How Denial-of-Service Attacks Work
- Denial-of-Service in Adversary Campaigns
- Real-World Denial-of-Service Attacks
- Detection and Indicators of Denial-of-Service Attacks
- Prevention and Mitigation of Denial-of-Service Attacks
- Response and Recovery from Denial-of-Service Attacks
- Operationalizing Denial-of-Service Defense
- DoS Attack FAQs
- What Is Hacktivism?
- What Is a DDoS Attack?
-
What Is CSRF (Cross-Site Request Forgery)?
- CSRF Explained
- How Cross-Site Request Forgery Works
- Where CSRF Fits in the Broader Attack Lifecycle
- CSRF in Real-World Exploits
- Detecting CSRF Through Behavioral and Telemetry Signals
- Defending Against Cross-Site Request Forgery
- Responding to a CSRF Incident
- CSRF as a Strategic Business Risk
- Key Priorities for CSRF Defense and Resilience
- Cross-Site Request Forgery FAQs
- What Is Spear Phishing?
-
What Is Brute Force?
- How Brute Force Functions as a Threat
- How Brute Force Works in Practice
- Brute Force in Multistage Attack Campaigns
- Real-World Brute Force Campaigns and Outcomes
- Detection Patterns in Brute Force Attacks
- Practical Defense Against Brute Force Attacks
- Response and Recovery After a Brute Force Incident
- Brute Force Attack FAQs
- What is a Command and Control Attack?
- What Is an Advanced Persistent Threat?
- What is an Exploit Kit?
- What Is Credential Stuffing?
- What Is Smishing?
-
What is Social Engineering?
- The Role of Human Psychology in Social Engineering
- How Has Social Engineering Evolved?
- How Does Social Engineering Work?
- Phishing vs Social Engineering
- What is BEC (Business Email Compromise)?
- Notable Social Engineering Incidents
- Social Engineering Prevention
- Consequences of Social Engineering
- Social Engineering FAQs
-
What Is a Honeypot?
- Threat Overview: Honeypot
- Honeypot Exploitation and Manipulation Techniques
- Positioning Honeypots in the Adversary Kill Chain
- Honeypots in Practice: Breaches, Deception, and Blowback
- Detecting Honeypot Manipulation and Adversary Tactics
- Safeguards Against Honeypot Abuse and Exposure
- Responding to Honeypot Exploitation or Compromise
- Honeypot FAQs
- What Is Password Spraying?
- How to Break the Cyber Attack Lifecycle
-
What Is Phishing?
- Phishing Explained
- The Evolution of Phishing
- The Anatomy of a Phishing Attack
- Why Phishing Is Difficult to Detect
- Types of Phishing
- Phishing Adversaries and Motives
- The Psychology of Exploitation
- Lessons from Phishing Incidents
- Building a Modern Security Stack Against Phishing
- Building Organizational Immunity
- Phishing FAQ
- What Is a Rootkit?
- Browser Cryptocurrency Mining
- What Is Pretexting?
What Is Cryptojacking?
Cryptojacking is the unauthorized use of computing resources to mine cryptocurrency. Often delivered via browser scripts, infected software, or compromised infrastructure, cryptojacking silently consumes CPU cycles, increases power costs, degrades system performance, and introduces hidden operational risk without overt signs of compromise. The cyber attack is stealthy, scalable, and difficult for organizations to detect in cloud and hybrid environments.
Understanding Cryptojacking
Cryptojacking involves a covert process where cyber attackers hijack computing resources to mine cryptocurrency without user consent. In the MITRE ATT&CK framework, it’s classified under MITRE ATT&CK technique T1496: Resource Hijacking. While it doesn't exfiltrate data or encrypt files like traditional malware, it degrades system performance, spikes energy consumption, and introduces security blind spots that attackers can exploit for persistence or lateral movement.
Cryptojacking operations often execute JavaScript-based mining scripts (e.g., Coinhive or its successors) in users’ browsers or deploy native miners via compromised servers, containers, or endpoint software. It can target CPUs, GPUs, and cloud infrastructure alike. In containerized or serverless environments, attackers often abuse misconfigured APIs or exposed IAM roles to escalate privileges and launch distributed mining payloads.
Commonly associated terms include drive-by mining, browser-based mining, and CPU hijacking. While once dominated by browser mining, cryptojacking has shifted heavily toward cloud-native exploitation. Attackers now favor persistent agents that evade detection tools by blending into routine telemetry or abusing legitimate orchestration tooling like Kubernetes or Terraform.
The evolution of cryptojacking reflects a broader trend. Financially motivated attackers increasingly seek quiet sustainability over disruptive visibility. That makes cryptojacking a uniquely persistent and often overlooked security concern.
Types of Cryptojacking and Resource Abuse Attacks
Cryptojacking spans a spectrum of tactics, each tailored to the attacker’s access level, environment, and target infrastructure. The following outlines the main types, focusing on how they differ in visibility, complexity, and operational control.
Browser Mining
Browser-based cryptojacking runs mining scripts in a victim’s browser without their consent. It requires no installation, only that the user visits a compromised site. The attack ends when the tab closes, which limits its duration and efficiency. Most scripts target Monero due to its CPU-friendliness and privacy features.
Drive-By Mining
Drive-by mining is a subset of browser mining where the miner runs automatically during web browsing sessions — often injected into ad networks, compromised CMS plugins, or media-streaming pages. Victims typically have no indication of the CPU usage spike unless their browser or endpoint protection alerts them.
Stealth Mining
Stealth mining refers to persistent cryptojacking that prioritizes invisibility over speed. It may throttle CPU consumption, execute only when user activity is low, or stop during known backup windows. Stealth tactics increase dwell time, allowing attackers to mine over weeks or months without detection.
JavaScript Miners
JavaScript-based miners — like those used in early Coinhive campaigns — leverage simple script tags embedded in web pages. These scripts call remote mining APIs and execute cryptographic workloads client-side. While easy to deploy, they’re highly detectable by browser extensions, endpoint monitoring, and content security policies.
WebAssembly Miners
WebAssembly (Wasm) miners represent the evolution of JavaScript miners, offering faster execution and better CPU access. Wasm modules perform hashing functions more efficiently and evade some script-based detection tools. Attackers prefer Wasm for high-volume browser mining or advanced cloud-resident payloads.
Inline Script Injection
Inline injection embeds malicious miner code directly into HTML or JavaScript served by a trusted source. It often occurs via compromised CDN assets, outdated CMS components, or vulnerable third-party integrations. Inline miners run on page load and appear native unless closely inspected.
Obfuscated JavaScript
Obfuscated miners disguise their logic using encoding, variable mangling, or dynamic script loaders to avoid static analysis. Some use domain generation algorithms (DGAs) to rotate C2 domains, while others encrypt payloads until runtime. Obfuscation slows detection but increases script size and execution time.
Coinhive Exploitation
Coinhive was a now-defunct Monero mining service often abused for unauthorized mining. Attackers embedded its scripts in thousands of websites before its shutdown in 2019. Even post-shutdown, similar codebases and clones persist under different branding, using the same client-server architecture.
CPU Hijacking
CPU hijacking refers to cryptojacking on traditional endpoints, often using PowerShell, bash, or compiled binaries. The payload may run as a scheduled task, Windows service, or embedded DLL, hijacking CPU cycles for mining while evading simple process tree monitoring. Hijacking often leverages privilege escalation for persistence.
Cloud Resource Abuse
Cloud environments offer scalable compute, which attackers exploit by abusing stolen credentials or poorly secured APIs. Payloads may deploy in containers, serverless functions, or spun-up VMs. Cloud mining attacks often result in massive cost spikes, throttled services, and operational outages if not quickly detected. Cloud-native cryptojacking tends to scale horizontally across regions and services using automation scripts.
Each method represents a trade-off between stealth, scalability, and technical complexity. Organizations need layered defenses that account for both web-facing injection such as SQL injection and infrastructure-level resource hijacking to detect and contain the full range of cryptojacking activity.
How Cryptojacking Works
Cryptojacking attacks prioritize persistence, stealth, and efficiency, embedding miners in client browsers, cloud workloads, or vulnerable infrastructure. Successful campaigns often avoid data exfiltration or destructive behavior, instead remaining quietly embedded while consuming CPU and memory over extended periods.
Initial Access and Execution
Most cryptojacking campaigns begin with one of three entry vectors — browser injection, server exploitation, or supply chain compromise. In browser-based attacks, attackers load JavaScript miners — once commonly hosted through services like Coinhive — into legitimate websites via malicious ads, compromised CMS plugins, or unsecured CDNs. The script runs in the background when a user visits the page, consuming their device’s resources until the tab is closed.
In server-based attacks, attackers scan for misconfigurations in cloud workloads, exposed Docker APIs, vulnerable Jenkins instances, or Kubernetes dashboards. Once inside, they drop ELF-based binaries designed to mine silently in the background. They often modify crontabs or systemd units for persistence and disable monitoring agents like CloudWatch, OSSEC, or container-native runtime security tools.
Common Tools and Payloads
Popular tools include xmrig (for Monero mining), kdevtmpfsi, and custom forks of open-source miners compiled with hardcoded wallet addresses and throttling logic to reduce detection. Command-and-control infrastructure is often minimal, with miner configuration baked into the binary or fetched from GitHub, Pastebin, or attacker-controlled Gist files.
Miners may use encrypted communications over HTTPS or SSH tunnels to blend into legitimate traffic. DNS tunneling is also common for out-of-band instructions or payload retrieval. Many variants detect CPU type and disable themselves on ARM or low-power architectures to reduce footprint.
Cloud-Scale Variants
In cloud environments, attackers frequently hijack IAM credentials to spin up short-lived VMs optimized for mining. Others abuse serverless functions or autoscaling policies to generate new compute resources automatically. An attacker who gains access to a CI/CD pipeline or IaC deployment mechanism can embed miners at the provisioning layer, persisting across infrastructure resets.
Cryptojacking Campaigns and Variants
Notable campaigns include TeamTNT and Rocke Group, both of which specialize in cryptojacking across containerized and cloud-native environments. TeamTNT, for instance, has exploited exposed Docker APIs and harvested AWS credentials to deploy miners across clusters. Another campaign exploited Oracle WebLogic vulnerabilities to push mining scripts onto high-performance backend servers without triggering alarms.
In some cases, attackers chain exploits — combining credential-based attacks with privilege escalation — to embed miners within environments that remain unaffected by conventional endpoint detection.
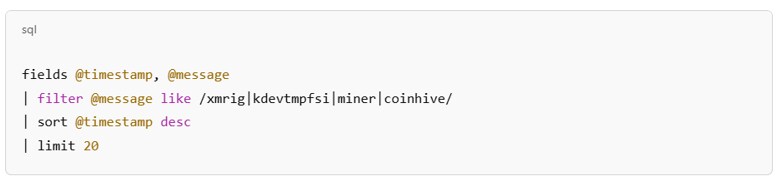
Figure 1: Example detection query (Cloudwatch logs insights)
Cryptojacking’s technical simplicity masks its operational complexity. Well-run operations prioritize staying unnoticed, using environmental awareness, self-throttling payloads, and stealth techniques to mine for weeks or months before discovery. That persistence makes understanding the inner workings of cryptojacking critical for defenders managing cloud workloads at scale.
Cryptojacking in the Adversary Kill Chain
Cryptojacking rarely occurs in isolation. It’s often the end goal of a broader attack sequence that includes initial access, lateral movement, privilege escalation, and persistence. Unlike data theft or ransomware, the intent isn’t to exfiltrate or encrypt but to remain undetected while harvesting compute cycles at scale.
Initial Access and Positioning
Attackers commonly gain access through misconfigured cloud services, vulnerable software (e.g., Jenkins, Jupyter notebooks, or Apache Struts), or phishing campaigns that deliver credential-stealing malware. Once inside, they move laterally or escalate privileges to reach systems with high-performance CPUs or GPUs. Some campaigns abuse cloud provisioning APIs to spin up crypto-optimized virtual machines directly.
Privilege escalation, while not always necessary, increases mining efficiency by allowing attackers to disable security agents, modify logging configurations, or install miners with root-level persistence mechanisms. Elevated access also enables the deployment of systemd services or crontab entries to respawn mining processes on reboot or termination.
Post-Compromise Objectives
Persistence becomes a top priority after installation. In cloud environments, attackers often deploy miners as daemonized processes or embed them in container images within CI/CD pipelines. They may also tamper with monitoring agents or abuse IAM permissions to create backdoor accounts that silently reintroduce mining payloads even after remediation attempts.
In some campaigns, attackers chain cryptojacking with resource hijacking techniques like API abuse, autoscaling manipulation, or container sprawl to maximize compute output without raising cost alarms. Others exploit container escape techniques or exposed kubelets to spread laterally across clusters.
Operational Obfuscation and Stealth
Cryptojacking often coexists with low-noise tactics like DNS tunneling, domain fronting, or idle-cycle scheduling. Some payloads detect user activity or battery level and suspend operations to avoid alerting the user. Others throttle CPU usage dynamically or use watchdog scripts to restart miners if terminated.
Advanced campaigns may install fallback mechanisms alongside the miner — such as rootkits, reverse shells, or hidden C2 check-ins — creating pathways for future exploitation, including pivoting into ransomware staging or data theft if mining becomes unviable.
Intersection with Other Attack Types
Cryptojacking often follows cloud credential theft, phishing, or supply chain compromise. For example, a phishing email might harvest credentials that grant access to a CI/CD platform, where a malicious post-build script drops a miner across production workloads. Alternatively, attackers might exploit a known vulnerability (e.g., Log4Shell or Confluence RCE) and install both a miner and a remote shell to maintain long-term control.
While cryptojacking lacks the immediate visibility of ransomware, it can serve as an early indicator of broader compromise. Its low-risk, high-reward nature makes it an attractive secondary objective for threat actors already inside a network — especially in environments with weak monitoring or lax IAM governance.
Real-World Cases of Cryptojacking
Cryptojacking has evolved from opportunistic browser-based mining into a persistent, cloud-scale threat. Adversaries now weaponize automation and misconfigurations to covertly hijack compute resources, often going undetected for weeks. Below are recent examples that reveal the scale, techniques, and business impact of modern cryptojacking campaigns.
Atlassian Confluence Exploited for Cryptojacking
In mid-2024, attackers exploited CVE-2023-22527 — a critical remote code execution vulnerability in Atlassian Confluence Data Center and Server — to deploy XMRig cryptocurrency miners on unpatched systems. Threat actors utilized shell scripts to terminate competing mining processes, disable security tools, and establish persistence via cron jobs. Some campaigns propagated laterally through SSH, compromising additional hosts. The cryptojacking operations led to significant resource consumption and performance degradation across affected enterprise environments.
Cryptojacking in Educational Infrastructure
In 2023, cybersecurity researchers uncovered a cryptojacking campaign targeting over 200 university subdomains across North America and Europe. Attackers exploited outdated CMS plugins to embed obfuscated JavaScript miners, which executed in-browser Monero mining as soon as users loaded the page. No data was stolen, but the victims incurred significant reputational damage and bandwidth strain. Detection was delayed for weeks due to the script’s polymorphic nature and limited system telemetry.
Cloud Compute Exploitation at Tesla
Tesla suffered a high-profile incident when a Kubernetes administrative console was discovered exposed to the internet without password protection. Attackers used the access to deploy mining software within a container and concealed the operation using an open reverse proxy and custom pool settings. The attackers throttled CPU consumption to remain under monitoring thresholds, which delayed detection. The mining activity was ultimately discovered by a third-party cloud security audit.
Nation-State Cryptojacking Indicators
In late 2022, multiple reports from international CERTs linked cryptojacking activity to North Korean state-sponsored groups using the Kimsuky and Lazarus malware ecosystems. Infections originated from spearphishing emails disguised as cryptocurrency investment platforms. The campaigns deployed multistage loaders that installed WebAssembly miners and manipulated process names to appear as system daemons. The group prioritized persistence and evasion over aggressive mining speeds, likely to blend into environments for long-term passive income.
Cryptomining Attacks Trends
A 2023 Symantec report indicated that cryptojacking detections increased by 399% over the previous year, primarily due to improved scanning of container workloads and increased attacker preference for low-risk, profit-driven malware. Detection remains difficult due to evasive mining modules that mimic legitimate processes, employ user-agent spoofing, and abuse obfuscated script loaders to delay static analysis.
Key Behavioral Indicator
Cryptojacking operations frequently generate consistent low-rate outbound network traffic to unknown mining pools, often using ports 3333 or 14444. Load variance across similar workloads may signal illicit CPU utilization.
Prevention and Mitigation
Effective cryptojacking mitigation requires layered, context-aware defenses that detect abuse patterns, enforce architectural guardrails, and constrain unauthorized compute usage across endpoints, browsers, and cloud environments.
Segment Critical Resources and Constrain Compute
Cryptojacking attacks succeed when compute resources remain accessible, unmonitored, or misconfigured. Eliminate unnecessary exposure by segmenting critical workloads, limiting container-to-host interaction, and disabling unused services. Deploy strict egress controls from cloud workloads to reduce outbound communication with mining pools. Use resource quotas in Kubernetes and serverless functions to limit CPU and memory exploitation without impacting performance.
Strengthen Identity and Access Boundaries
Enforce least-privilege access using role-based access control (RBAC) for both cloud workloads and developer environments. Audit cloud IAM policies to remove overly permissive roles such as *:* or wildcarded permissions in AWS, GCP, and Azure. Require multifactor authentication (MFA) for all admin accounts and enforce short-lived credentials via automatic session expiration.
Secure the Build Pipeline and Dependencies
Secure build pipelines with verified dependency checks, signature validation, and runtime code integrity verification. Attackers frequently inject mining code into open-source dependencies or CI/CD scripts. Use software composition analysis (SCA) tools to detect injected or backdoored mining scripts in NPM, PyPI, and container base layers. Block obfuscated JavaScript loaders from executing in browser-exposed surfaces using Content Security Policy (CSP) headers and script integrity attributes.
Detect Behavioral Anomalies at Runtime
Deploy behavior-based monitoring agents to profile expected CPU usage for workloads. Alert on persistent deviation, especially in high-granularity metrics like CPU throttling, abnormal process forking, or known mining pool DNS contact. Many cryptojacking campaigns evade static detection but falter under runtime inspection.
Implement Network Egress Filtering and DNS Controls
Implement DNS filtering, blocklist feeds, and domain generation algorithm (DGA) detection at the egress firewall level to prevent pool registration. Rate-limit outbound requests from internal services, especially those that shouldn’t initiate external connections. Where supported, use microsegmentation to isolate high-risk containerized applications from privileged backplane resources.
Train Teams to Recognize and Report Threats
Train developers and DevOps teams to identify signs of mining abuse within CI/CD jobs, container layers, or browser behaviors. Educate end users on avoiding browser extensions or links that spawn mining processes. Include cryptojacking scenarios in threat modeling exercises and tabletop drills for incident response planning.
Common Missteps to Avoid
Blocking cryptocurrency domains alone won’t prevent embedded miners from communicating over proxy tunnels, custom subdomains, or through browser-based relay chains. Static allow/deny lists are insufficient. Similarly, endpoint protection that focuses solely on malware signatures can miss custom or obfuscated mining scripts. Without behavioral telemetry and egress enforcement, detection is delayed or entirely absent.
Related Article: Playbook of the Week: Cloud Cryptojacking Response
Response and Recovery
Effective incident response in cryptojacking prioritizes speed. Rapid containment matters, not because data is exfiltrated, but because every second drains compute budgets, degrades performance, and conceals broader compromise. Recovery isn't just about cleaning infected hosts — it’s about validating cloud spend, reasserting control over runtime environments, and tracing initial access paths to prevent repeat exploitation.
Isolate and Contain the Compromised Workload
The first priority is to halt unauthorized resource consumption. Identify the source workload or user session responsible for the mining activity. Quarantine the affected container, VM, function, or browser context to prevent lateral movement. In cloud-native environments, revoke IAM credentials and session tokens associated with compromised roles.
Kill Processes and Reclaim Resources
Terminate malicious processes immediately, whether they're CPU-intensive shell scripts, browser-executed JavaScript, or embedded WebAssembly modules. In managed Kubernetes clusters or serverless runtimes, reinitialize affected components with known-good images. In VMs, inspect cron jobs and user-scheduled tasks to prevent respawning.
Audit for Persistence Mechanisms
Cryptojacking actors often maintain access through misconfigured startup scripts, pre-installed malware in AMIs, or hidden IAM credentials. Search for persistence indicators, such as unauthorized container init scripts, systemd services, or base image tampering. Rebuild compromised nodes from clean templates rather than patching in place.
Engage Incident Response and Cloud Security Teams
Cryptojacking incidents cross multiple domains: application, infrastructure, and IAM. Assemble a multidisciplinary team with cloud platform owners, threat analysts, and FinOps stakeholders. Cloud detection and response (CDR) platforms or extended detection and response (XDR) tools are vital for correlating resource anomalies with identity activity.
Communicate Internally and Evaluate Blast Radius
Inform DevOps, FinOps, and security leadership as early as possible. Evaluate the financial and operational blast radius. Prolonged mining can lead to significant cost spikes, degraded SLAs, and potential customer impact. Review usage trends, billing dashboards, and anomalous compute billing activity across all accounts.
Perform a Forensic Investigation
Capture runtime memory, process listings, and file artifacts from affected systems. Identify miner binaries, config files, and outbound connection targets. If browser-based, log all script sources, XHR calls, and DOM manipulations. Assess whether the attacker exploited supply chain weaknesses, vulnerable dependencies, or exposed secrets.
Post-Mortem and Remediation Planning
After containment, conduct a root cause analysis. Document the attack path, the assets affected, and the defenses that failed. Prioritize hardening steps — enforce stricter image controls, improve egress filtering, tighten IAM scopes, and upgrade runtime protections. Validate all fixes through red team simulation or purple teaming.
Update Threat Models and Monitoring Playbooks
Integrate learnings into security engineering processes. Update detection rules in your SIEM, CDR, and cloud-native telemetry tools to account for miner behaviors, DNS tunneling, and throttled CPU abuse. Modify threat models to reflect new mining TTPs. Incorporate cryptojacking scenarios into your incident response tabletop exercises.