-
What Is MITRE ATT&CK Framework?
- MITRE ATT&CK Framework Explained
- Structuring Adversary Behavior by Tactic
- MITRE ATT&CK Tactics and Their Role in Security Intelligence
- MITRE ATT&CK Techniques
- MITRE ATT&CK Use Cases
- Using the MITRE ATT&CK Framework during a Live Attack
- Comparing MITRE ATT&CK and the Cyber Kill Chain
- Advancing Organizational Maturity with ATT&CK
- Toward a Behavioral Framework for Securing AI
- MITRE ATT&CK Framework FAQs
- How Do I Implement MITRE ATT&CK Techniques?
-
What Are MITRE ATT&CK Techniques?
- MITRE ATT&CK Techniques Explained
- The Anatomy of a MITRE ATT&CK Technique
- Understanding Common and Emerging ATT&CK Techniques
- Detecting and Mitigating MITRE ATT&CK Techniques
- Leveraging ATT&CK Techniques for Enhanced Security Operations
- The Future Evolution of ATT&CK Techniques
- MITRE ATT&CK Techniques FAQs
-
How Has MITRE ATT&CK Evolved?
- Evolution of MITRE ATT&CK Explained
- The Historical Trajectory of MITRE ATT&CK
- Why TTPs Matter: Shifting the Cybersecurity Paradigm
- Key Milestones in ATT&CK's Expansion and Refinement
- Core Components and Their Evolving Definition
- Why the Evolution Matters: Benefits for Cybersecurity Professionals
- Addressing the Evolving Threat Landscape with ATT&CK
- Operationalizing the Framework: Practical Applications and Challenges
- The Future of MITRE ATT&CK
- Evolution of MITRE ATT&CK FAQs
- What Are MITRE ATT&CK Use Cases?
- A CISO's Guide to MITRE ATT&CK
- How Does MITRE ATT&CK Apply to Different Technologies?
-
What is the Difference Between MITRE ATT&CK Sub-Techniques and Procedures?
- Understanding the MITRE ATT&CK Framework
- Exploring Sub-Techniques in the ATT&CK Framework
- Exploring Procedures in the ATT&CK Framework
- The Role of Sub-Techniques in Cybersecurity Strategies
- Procedures as a Tool for Detailed Threat Analysis
- Continuous Evolution: Staying Updated with ATT&CK Framework
- MITRE ATT&CK Sub-Techniques vs. Procedures FAQs
What is the MITRE ATT&CK Matrix?
The MITRE ATT&CK Matrix is a globally accessible knowledge base that categorizes adversary tactics and techniques based on real-world observations and experiences. It helps organizations understand how cyberattacks unfold—providing a common language for describing adversary behavior and supporting threat detection, response, and strategic planning.
Built on actual incident data, the matrix is continuously updated, making it a living framework. Security teams use it to anticipate threats, identify gaps in coverage, and align defenses with known adversary behaviors.
Key Points
-
Behavioral Focus: The MITRE ATT&CK Matrix catalogs adversary tactics and techniques observed in real-world attacks. -
Standardized Framework: It provides a common language for discussing cyber threat behaviors, fostering better communication among cybersecurity professionals. -
Enhanced Defenses: Understanding ATT&CK helps organizations proactively improve their detection capabilities and incident response strategies. -
Strategic Application: The matrix is valuable for red teaming, blue teaming, and purple teaming, aligning offensive and defensive security efforts. -
Beyond Signatures: ATT&CK moves past traditional signature-based detection to focus on attacker methodologies and actions.
MITRE ATT&CK Matrix Explained
The MITRE ATT&CK Matrix provides a standardized lexicon for detailing adversary behavior, moving beyond simple malware signatures to focus on the actions attackers take during an intrusion. This framework is crucial for cybersecurity professionals as it enables more effective threat intelligence sharing, improved defensive capabilities, and enhanced incident response.
It categorizes techniques by tactics—the "why" an adversary acts—and techniques—the "how" an adversary achieves a tactical goal. This structured approach enables organizations to anticipate, detect, and mitigate attacks by understanding the common paths and methods that adversaries employ.
The significance of ATT&CK lies in its practical application for red teaming, blue teaming, and purple teaming exercises, offering a common ground for offensive and defensive security operations to collaborate and strengthen an organization’s security posture.
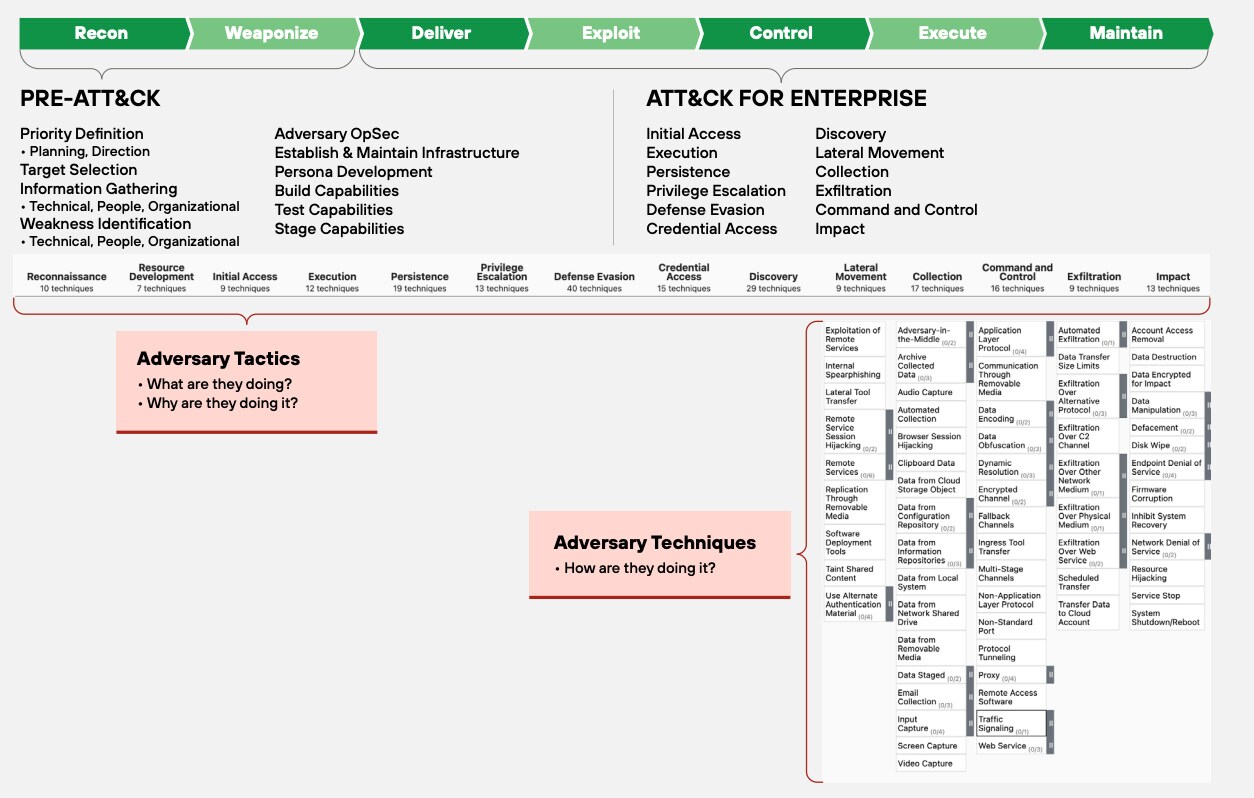
Figure 1: Understanding the MITRE ATT&CK Framework
Key Components of MITRE ATT&CK: Tactics, Techniques, and Procedures
The MITRE ATT&CK framework meticulously categorizes adversary behavior, providing a common language for understanding cyber attacks. This structured approach enables security teams to analyze and defend against threats more effectively.
Adversary Tactics: The "Why"
Adversary tactics represent the high-level adversarial goals during a cyber attack—the "why" an adversary acts. These columns of the ATT&CK matrix outline the phases of an attack.
- Reconnaissance: Collecting information to plan future operations.
- Resource Development: Establishing resources to support operations.
- Initial Access: Gaining first footholds in a network.
- Execution: Running malicious code on a system.
- Persistence: Maintaining a foothold across reboots or credential changes.
- Privilege Escalation: Gaining higher-level permissions.
- Defense Evasion: Avoiding detection by security controls.
- Credential Access: Stealing credentials like usernames and passwords.
- Discovery: Understanding the network environment.
- Lateral Movement: Moving through the network to gain control of additional systems.
- Collection: Gathering data of interest from the target.
- Command and Control (C2): Communicating with compromised systems.
- Exfiltration: Stealing data out of the network.
- Impact: Disrupting, corrupting, or destroying systems and data.
Adversary Techniques: The "How"
MITRE ATT&CK techniques describe the specific methods adversaries use to achieve a tactical objective—the "how." Each tactic comprises various techniques, detailing the actual actions an attacker takes.
- Techniques often involve the misuse of legitimate system functions, known as "living off the land," making them harder to detect by traditional signature-based security tools.
- Examples include Process Injection for defense evasion or Command and Scripting Interpreter for execution, as frequently observed in real-world attacks.
Sub-techniques: Granular Detail
Many techniques are further broken down into sub-techniques, providing a more granular understanding of specific adversary behaviors. This level of detail enables more precise detection and mitigation strategies.
- Sub-techniques enable organizations to fine-tune their defenses, taking into account diverse implementations of the same adversarial intent.
- For instance, User Execution (T1204) under Initial Access can include sub-techniques like Malicious Link (T1204.001) or Malicious File (T1204.002).
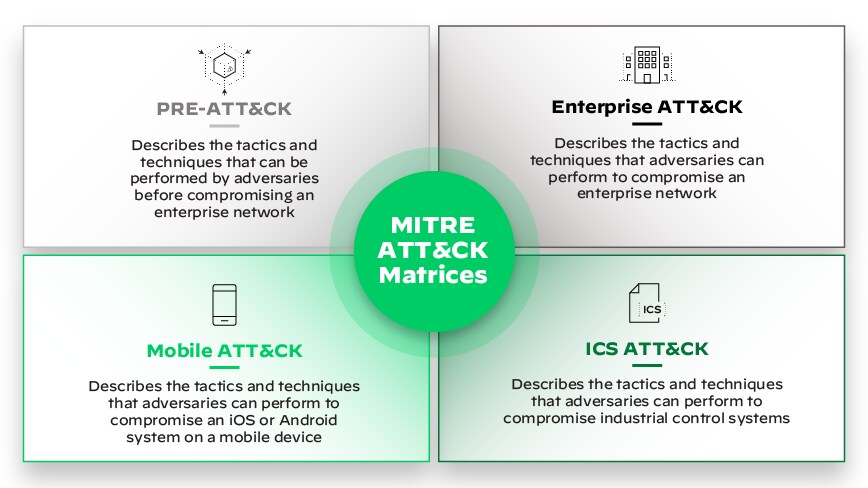
Figure 2: MITRE ATT&CK Matrices
Diverse MITRE ATT&CK Matrices: Adapting to Specific Environments
MITRE ATT&CK extends beyond the general enterprise network, providing specialized matrices tailored to unique technology domains. These matrices ensure comprehensive coverage across varied operational environments.
Enterprise Matrix
The most extensive and widely recognized matrix, the Enterprise Matri, covers tactics and techniques used against Windows, macOS, Linux, cloud (AWS, GCP, Azure, Office 365, Azure AD, SaaS), and network infrastructure.
- This matrix details threat actors, their objectives, and the detection and prevention methods applicable to these diverse platforms.
Mobile Matrix
Dedicated to mobile platforms, the Mobile Matrix focuses on threats and attack vectors specific to Android and iOS devices. It includes tactics and techniques for gaining unauthorized access, exploiting vulnerabilities, and other mobile-centric attacks.
- The Mobile Matrix also incorporates techniques related to "Network Effects" and "Remote Service Effects," addressing actions an adversary can take without direct device access.
Industrial Control Systems (ICS) Matrix
The ICS Matrix addresses the unique cybersecurity challenges of industrial control systems, including SCADA systems and other operational technology (OT). It outlines adversary tactics and techniques aimed at disrupting, damaging, or controlling industrial processes.
- This matrix is crucial for organizations operating critical infrastructure, offering insights into attacks that can have significant physical consequences.
PRE-ATT&CK Matrix
While often discussed separately from the post-compromise ATT&CK matrices, PRE-ATT&CK focuses on adversary actions taken before an attack, specifically during the reconnaissance and resource development phases.
- It helps organizations identify early signs of targeting and understand the information attackers might gather to plan their operations.
How Organizations Operationalize MITRE ATT&CK
The MITRE ATT&CK framework is not merely a reference document; it is a practical tool that empowers cybersecurity teams to enhance their defensive posture and proactive threat management.
Enhancing Threat Intelligence
ATT&CK provides context to threat intelligence by mapping observed adversary behaviors to specific tactics and techniques. This enables organizations to understand not only what happened, but also how and why.
- By correlating threat intelligence with ATT&CK, security teams can build relevant threat models based on real-world campaigns, moving beyond static indicators of compromise (IOCs).
- Understanding the TTPs of known threat actors helps predict likely next actions in an attack chain.
Improving Threat Detection and Hunting
Security operations centers (SOCs) leverage ATT&CK to develop and refine their detection capabilities. By mapping existing security controls and logs to ATT&CK techniques, organizations can identify gaps in coverage.
- Gap Analysis: Organizations assess their current visibility and detection capabilities against the ATT&CK matrix to pinpoint areas where they are vulnerable. This enables a prioritized approach to improving defenses.
- Behavioral Detections: Instead of relying solely on signatures, ATT&CK encourages building detections based on adversary behaviors, which are more resilient to changes in malware variants. For instance, detecting the execution of common scripting interpreters (cmd.exe, PowerShell) when observed in unusual contexts.
- Threat Hunting: Security analysts use ATT&CK to proactively search for evidence of adversary activity that might have bypassed existing controls. This involves hypothesis-driven searches based on specific techniques.
Assessing Security Posture and Tooling
ATT&CK serves as a benchmark for evaluating the effectiveness of security tools and controls. Organizations can map the capabilities of their security solutions (e.g., EDR, SIEM, firewalls) against the matrix to identify overlaps and deficiencies.
- Control Validation: Regularly validating that security controls can detect or prevent specific ATT&CK techniques helps ensure their efficacy.
- Security Investments: ATT&CK guides strategic security investments by highlighting areas where new technologies or enhancements are most needed to address critical adversarial techniques.
Facilitating Red Teaming and Blue Teaming Exercises
ATT&CK provides a common framework for offensive (red team) and defensive (blue team) security exercises. Red teams can utilize ATT&CK to emulate specific adversary behaviors, while blue teams can leverage it to test and enhance their detection and response capabilities.
- Purple Teaming: The framework enables effective purple teaming, where red and blue teams collaborate to share insights and improve overall security effectiveness, ensuring that defensive measures are validated against realistic attack scenarios.
Streamlining Incident Response and Reporting
During incident response, mapping observed adversary actions to ATT&CK techniques helps responders understand the scope of an attack, predict next steps, and develop effective containment and eradication strategies.
- Standardized Reporting: ATT&CK provides a standardized vocabulary for reporting on incidents, making it easier to communicate threat information within an organization and with external partners.
- Remediation Efforts: By understanding the specific techniques used, remediation efforts can be precisely targeted to undo the attacker's actions and prevent recurrence.
Mapping Security Controls to ATT&CK Techniques
Security Control |
Primary MITRE ATT&CK Tactics Covered |
Example ATT&CK Techniques |
Palo Alto Networks Solution Alignment |
Endpoint Detection and Response (EDR) |
Execution, Persistence, Privilege Escalation, Defense Evasion, Credential Access, Discovery, Lateral Movement, Collection, Impact |
Process Injection, Scheduled Task/Job, Brute Force, Obfuscated Files or Information, Credential Dumping, Network Share Discovery, Remote Services, Data Staged, Data Encrypted for Impact |
Cortex XDR: Provides broad coverage across 121 out of 136 techniques, with automated detection and prevention of endpoint threats, including advanced ransomware and macOS/Linux attacks. |
Initial Access, Command and Control, Exfiltration, Defense Evasion |
Phishing, Exploit Public-Facing Application, Standard Application Layer Protocol, Data Compressed, Encrypted Traffic, Port Scan |
Palo Alto Networks Next-Gen Firewalls (PAN-OS): Prevent initial intrusions, detect and block malicious command and control communications, and prevent data exfiltration by inspecting traffic at various layers. |
|
Security Information and Event Management (SIEM) / Security Operations Platform |
All Tactics (through correlation and analysis) |
Tactic-level and Technique-level Detections (aggregates data from various sources) |
Cortex XSOAR / Cortex XSIAM: Ingests and correlates data from various sources, including endpoint, network, and cloud, mapping events to ATT&CK techniques for comprehensive visibility, automated threat correlation, and accelerated incident response. |
Cloud Security Posture Management (CSPM) / Cloud Workload Protection (CWPP) |
Initial Access, Persistence, Privilege Escalation, Defense Evasion, Discovery, Exfiltration, Impact (Cloud-specific) |
Cloud API Attacks, Exploitation for Privilege Escalation, Impair Defenses, Instance Metadata API, Data from Cloud Storage, Resource Hijacking |
Prisma Cloud: Offers real-time cloud security, identifying tactics and techniques per MITRE ATT&CK's Cloud Matrix, including network anomaly detection (e.g., port scans), user and entity behavior analytics (UEBA), and threat intelligence-based detections for cloud-native applications and infrastructure. |
Initial Access, Persistence, Privilege Escalation, Credential Access, Defense Evasion |
Valid Accounts, Account Manipulation, Brute Force, Steal or Forge Kerberos Tickets |
Palo Alto Networks Identity-based Security (e.g., integration with directory services): Enforces granular access controls, detects anomalous login behaviors, and prevents credential misuse. |
Table 1: Mapping Security Controls
Implementing and Maintaining a MITRE ATT&CK Program
Successfully integrating MITRE ATT&CK into an organization's cybersecurity operations requires a structured approach and continuous effort.
Step-by-Step Implementation
Organizations can adopt a phased approach to implementing ATT&CK, focusing on gradual improvements and building maturity over time.
- Understand Your Environment: Begin by documenting your critical assets, network architecture, and existing security controls.
- Assess Your Threat Landscape: Identify the most relevant threat actors and their common TTPs that are likely to target your industry or organization. Palo Alto Networks' Unit 42 reports, for example, often detail threat actor TTPs, which can be mapped to ATT&CK techniques.
- Map Current Capabilities: Use the ATT&CK matrix to map your existing security tools, detection rules, and incident response procedures to the techniques they cover. This provides a baseline understanding of your current defensive posture.
- Identify and Prioritize Gaps: Based on the mapping, pinpoint critical techniques that are not adequately covered by current controls. Prioritize these gaps based on their likelihood of being exploited and their potential impact.
- Develop an Implementation Roadmap: Create a plan to address identified gaps, which may involve deploying new security tools, developing custom detection rules, or enhancing existing processes.
- Leverage Available Resources: Utilize tools like MITRE ATT&CK Navigator to visualize and manage ATT&CK mappings, and consult community resources for best practices and shared detections.
Continuous Improvement and Updates
The threat landscape is constantly evolving, and so is the MITRE ATT&CK framework. Regular updates by MITRE incorporate new adversarial behaviors and refinements.
- Organizations must continuously update their ATT&CK mappings and detection strategies to reflect the latest framework versions and emerging threats.
- Staying informed about new adversary TTPs, often detailed in threat intelligence reports, is crucial for maintaining an effective ATT&CK program.
Benefits of Leveraging the MITRE ATT&CK Framework
Adopting the MITRE ATT&CK framework provides significant advantages for organizations seeking to enhance their cybersecurity defenses and cultivate a more proactive security posture.
- Common Language: Provides a standardized vocabulary for describing adversary behavior, enhancing communication among security teams and stakeholders.
- Threat-Informed Defense: Shifts focus from merely blocking known signatures to understanding and defending against actual adversary tactics and techniques.
- Improved Detection: Enables the development of more comprehensive and behavior-based detection rules, reducing reliance on easily bypassed indicators.
- Prioritized Investments: Helps organizations make informed decisions about where to invest security resources by highlighting critical gaps and the most prevalent attack techniques.
- Enhanced Collaboration: Fosters better collaboration between red teams, blue teams, and purple teams, leading to more realistic security testing and validated defenses.
- Proactive Security: Supports a proactive approach to cybersecurity, allowing organizations to anticipate attacks and build resilience rather than reacting solely to incidents.
Common Challenges and Solutions
While the MITRE ATT&CK Matrix offers immense value, organizations often encounter challenges during its implementation and ongoing use. These can range from a lack of internal expertise to difficulties integrating ATT&CK into existing security workflows.
Understanding these common hurdles and their corresponding solutions can help organizations navigate the adoption process more smoothly and achieve a more mature ATT&CK-driven security program. It's about adapting the framework to specific organizational needs and resources.
Challenge |
Solution |
Overwhelmed by Complexity |
Start small; focus on relevant tactics using tools like ATT&CK Navigator |
Lack of Integration with Tools |
Prioritize platforms with native ATT&CK support (e.g., Palo Alto Networks) |
Skill Gaps in Staff |
Invest in training, certifications, and expert guidance |
Difficulty Measuring ROI |
Define KPIs (coverage, detection, response time) and run simulations |
Table 2: MITRE ATT&CK Matrix Common Challenges and Solutions.
Overwhelmed by Scale and Complexity
The sheer size and detail of the MITRE ATT&CK Matrix can be daunting for organizations new to the framework. With hundreds of techniques and sub-techniques, it's easy to feel overwhelmed and unsure where to begin. This complexity can hinder initial adoption and lead to incomplete implementations.
Solution:
- Start small and prioritize.
- Focus on the tactics and techniques most relevant to your organization's specific threat landscape and critical assets.
- Leverage tools and resources that provide curated views or guided pathways through the matrix, such as MITRE's ATT&CK Navigator, which allows for visual representation and filtering of techniques.
Lack of Integration with Existing Tools
Many organizations struggle to integrate the MITRE ATT&CK Matrix with their existing security information and event management (SIEM) systems, endpoint detection and response (EDR) solutions, or threat intelligence platforms. Without seamless integration, the utility of ATT&CK as an operational framework is limited.
Solution:
- Prioritize security tools that offer native ATT&CK mapping and reporting capabilities. For tools that don't, develop custom parsers or scripts to align their outputs with ATT&CK techniques.
- Consider investing in security orchestration, automation, and response (SOAR) platforms that can automate the correlation of events with ATT&CK techniques, streamlining analysis and response.
Palo Alto Networks solutions, for instance, are designed with strong ATT&CK integration, providing visibility and protection mapped directly to the framework.
Insufficient Expertise and Training
Effectively utilizing the MITRE ATT&CK Matrix requires a thorough understanding of adversary behaviors and how they align with the framework. Many security teams lack the specialized expertise needed to fully leverage ATT&CK for threat hunting, incident response, or control validation.
Solution:
- Invest in comprehensive training for security analysts, incident responders, and security architects.
- Encourage certifications related to threat intelligence and ATT&CK.
- Foster a culture of continuous learning and knowledge sharing within the security team.
- Consider engaging with external experts or consulting services to jumpstart ATT&CK adoption and provide specialized guidance.
Difficulty in Measuring Effectiveness
Organizations often struggle to measure the effectiveness of their ATT&CK-driven security improvements quantitatively. Without clear metrics, it's challenging to demonstrate return on investment (ROI) or justify further resources for ATT&CK initiatives.
Solution:
- Establish clear key performance indicators (KPIs) related to ATT&CK coverage, detection rates, and response times for specific techniques.
- Use simulation tools to test defensive capabilities against ATT&CK techniques and track improvements over time.
- Regularly perform red team exercises or adversary emulation based on ATT&CK to validate and measure the effectiveness of controls.
MITRE ATT&CK and the Cybersecurity Landscape
The MITRE ATT&CK framework has become a cornerstone of modern cybersecurity, influencing how organizations approach threat intelligence, defense, and overall security strategy.
Evolution of Cybersecurity Practices
ATT&CK has driven a shift from purely reactive, signature-based security to a more proactive, threat-informed defense model. This evolution emphasizes understanding adversary intent and capabilities.
- It encourages security teams to think like attackers, anticipating their moves and building defenses that disrupt their typical attack paths.
Integration with Other Frameworks
While comprehensive, ATT&CK often complements other cybersecurity frameworks, such as the Lockheed Martin Cyber Kill Chain or the NIST Cybersecurity Framework.
- Cyber Kill Chain: The Cyber Kill Chain provides a high-level view of the stages of an attack, while ATT&CK offers granular detail on the techniques used within each stage. They can be used together to provide both strategic and tactical perspectives.
- NIST Cybersecurity Framework: NIST provides a framework for managing cybersecurity risk, and ATT&CK can be used to inform specific implementation details within the "Detect" and "Respond" functions of the NIST framework.
The Future of Threat-Informed Defense
As AI and machine learning continue to evolve, their integration with ATT&CK will likely deepen, enabling more sophisticated automated detection and response capabilities.
- The framework's adaptability ensures it will remain a critical resource for defenders as new threats and technologies emerge.