-
What Is MITRE ATT&CK Framework?
- MITRE ATT&CK Framework Explained
- Structuring Adversary Behavior by Tactic
- MITRE ATT&CK Tactics and Their Role in Security Intelligence
- MITRE ATT&CK Techniques
- MITRE ATT&CK Use Cases
- Using the MITRE ATT&CK Framework during a Live Attack
- Comparing MITRE ATT&CK and the Cyber Kill Chain
- Advancing Organizational Maturity with ATT&CK
- Toward a Behavioral Framework for Securing AI
- MITRE ATT&CK Framework FAQs
- How Do I Implement MITRE ATT&CK Techniques?
-
What is the MITRE ATT&CK Matrix?
- MITRE ATT&CK Matrix Explained
- Key Components of MITRE ATT&CK: Tactics, Techniques, and Procedures
- Diverse MITRE ATT&CK Matrices: Adapting to Specific Environments
- How Organizations Operationalize MITRE ATT&CK
- Implementing and Maintaining a MITRE ATT&CK Program
- Benefits of Leveraging the MITRE ATT&CK Framework
- Common Challenges and Solutions
- MITRE ATT&CK and the Cybersecurity Landscape
- MITRE ATT&CK Matrix FAQs
-
What Are MITRE ATT&CK Techniques?
- MITRE ATT&CK Techniques Explained
- The Anatomy of a MITRE ATT&CK Technique
- Understanding Common and Emerging ATT&CK Techniques
- Detecting and Mitigating MITRE ATT&CK Techniques
- Leveraging ATT&CK Techniques for Enhanced Security Operations
- The Future Evolution of ATT&CK Techniques
- MITRE ATT&CK Techniques FAQs
-
How Has MITRE ATT&CK Evolved?
- Evolution of MITRE ATT&CK Explained
- The Historical Trajectory of MITRE ATT&CK
- Why TTPs Matter: Shifting the Cybersecurity Paradigm
- Key Milestones in ATT&CK's Expansion and Refinement
- Core Components and Their Evolving Definition
- Why the Evolution Matters: Benefits for Cybersecurity Professionals
- Addressing the Evolving Threat Landscape with ATT&CK
- Operationalizing the Framework: Practical Applications and Challenges
- The Future of MITRE ATT&CK
- Evolution of MITRE ATT&CK FAQs
- A CISO's Guide to MITRE ATT&CK
- How Does MITRE ATT&CK Apply to Different Technologies?
-
What is the Difference Between MITRE ATT&CK Sub-Techniques and Procedures?
- Understanding the MITRE ATT&CK Framework
- Exploring Sub-Techniques in the ATT&CK Framework
- Exploring Procedures in the ATT&CK Framework
- The Role of Sub-Techniques in Cybersecurity Strategies
- Procedures as a Tool for Detailed Threat Analysis
- Continuous Evolution: Staying Updated with ATT&CK Framework
- MITRE ATT&CK Sub-Techniques vs. Procedures FAQs
What Are MITRE ATT&CK Use Cases?
The MITRE ATT&CK framework is a comprehensive knowledge base of adversarial tactics, techniques, and procedures (TTPs) based on real-world observations. MITRE ATT&CK use cases (the practical applications of the MITRE Att&ck framework) span various domains, offering actionable insights for cybersecurity professionals. Here are the primary use cases for MITRE ATT&CK:
- Threat Intelligence Enhancements
- Read Teaming and Adversary Emulation
- Security Operations Improvement
- Incident Response
- Security Posture Assessment
- Detection and Monitoring
- Training and Awareness
- Tool and Technology Evaluation
Organizations leverage ATT&CK to map adversary behaviors, prioritize defense mechanisms, and validate the effectiveness of security controls. By integrating ATT&CK into their operations, practitioners and CISOs can better understand attack vectors, improve threat intelligence, and foster a proactive security culture.
How MITRE ATT&CK Benefits Organizations
The MITRE ATT&CK framework is a globally recognized repository of Adversarial Tactics, Techniques, and Common Knowledge (TTPs) derived from real-world observations of cyber attacks. Developed by MITRE Corporation, this invaluable resource aids cybersecurity professionals in bolstering their defenses against sophisticated threats in the following ways:
- Practitioners utilize MITRE ATT&CK to simulate adversary tactics, techniques, and procedures (TTPs) in controlled environments. This hands-on approach uncovers vulnerabilities and tests the resilience of existing defenses.
- CISOs gain a strategic advantage by aligning their security programs with ATT&CK's detailed adversary behavior models. This alignment facilitates a more informed allocation of resources, ensuring critical assets receive the highest protection.
- By mapping detected incidents to ATT&CK techniques, security teams can pinpoint the stages of an attack lifecycle, enabling quicker and more accurate responses. This mapping also aids in threat hunting, as analysts can proactively search for indicators of compromise based on known adversary behaviors.
- The framework's shared language fosters collaboration across teams and organizations, enhancing collective defense efforts.
![]()
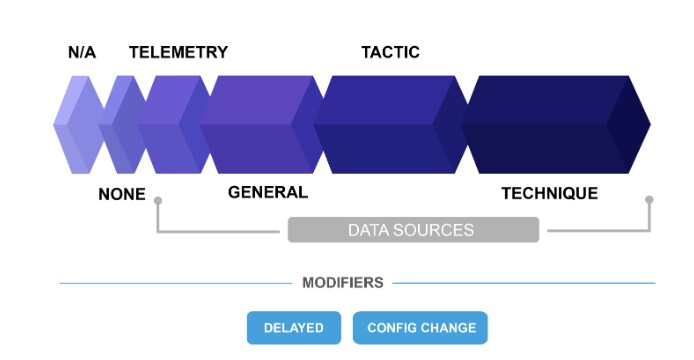
Key Components of the ATT&CK Matrix
Caption: Understanding the MITRE ATT&CK framework
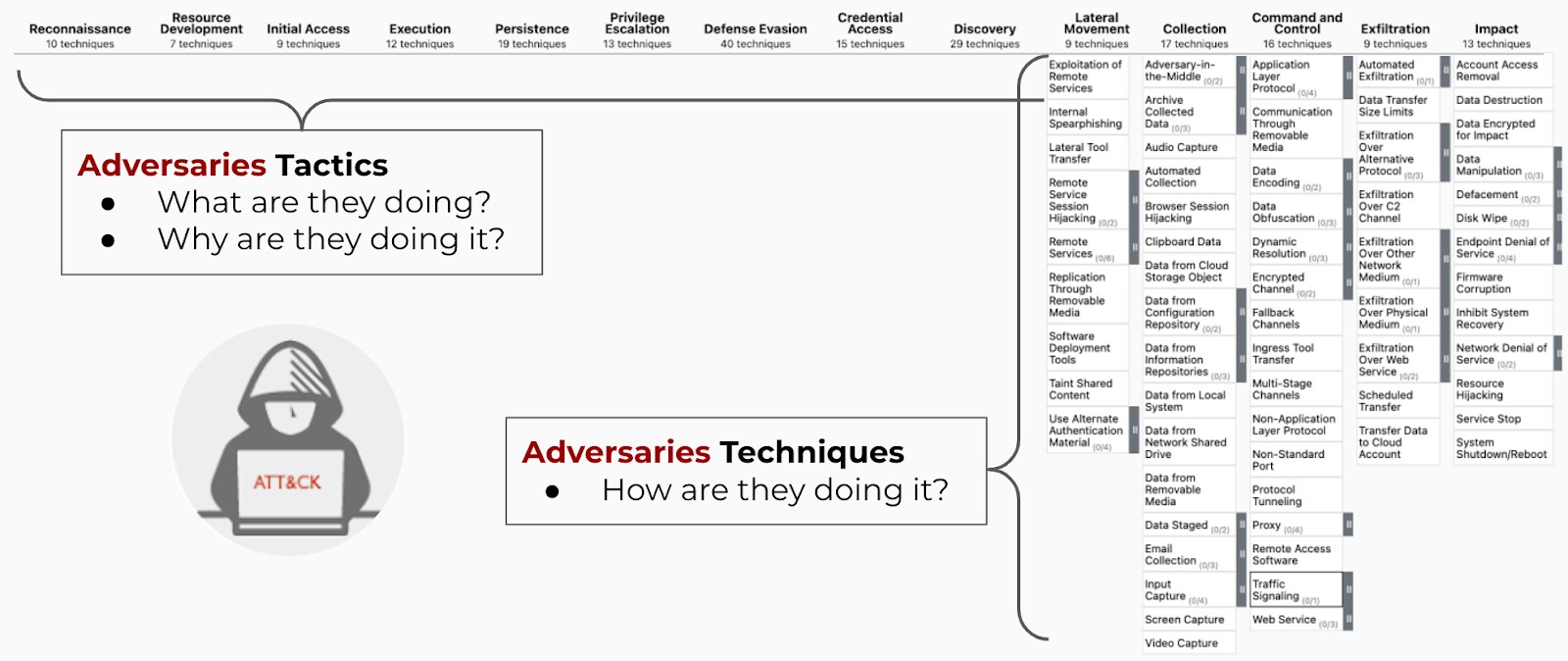
Tactics
Adversaries employ tactics to achieve specific objectives, such as initial access, execution, or exfiltration. Each tactic represents a strategic goal, guiding the selection of techniques and procedures. Security teams analyze these tactics to anticipate threats, disrupt attack chains, and fortify defenses, ensuring a proactive stance against evolving cyber threats.
Techniques
Adversaries utilize credential dumping, lateral movement, and data encryption to achieve their objectives. Security teams dissect these techniques to identify patterns, develop countermeasures, and enhance detection capabilities. By understanding the intricacies of each technique, defenders can anticipate attacker moves and effectively mitigate potential threats.
Sub-Techniques
Adversaries refine techniques into sub-techniques, such as spear-phishing via service or process injection for persistence. These nuanced actions allow for more precise detection and response strategies. Security teams must dissect these sub-techniques to uncover hidden patterns, enhancing their ability to thwart sophisticated attacks and protect critical assets.
Procedures
Security teams meticulously document adversaries' steps, from initial access to data exfiltration. They create detailed playbooks outlining detection methods, response actions, and mitigation strategies. These procedures enable rapid identification of threats, ensure timely and effective countermeasures, and fortify the organization's defenses against evolving cyber threats.
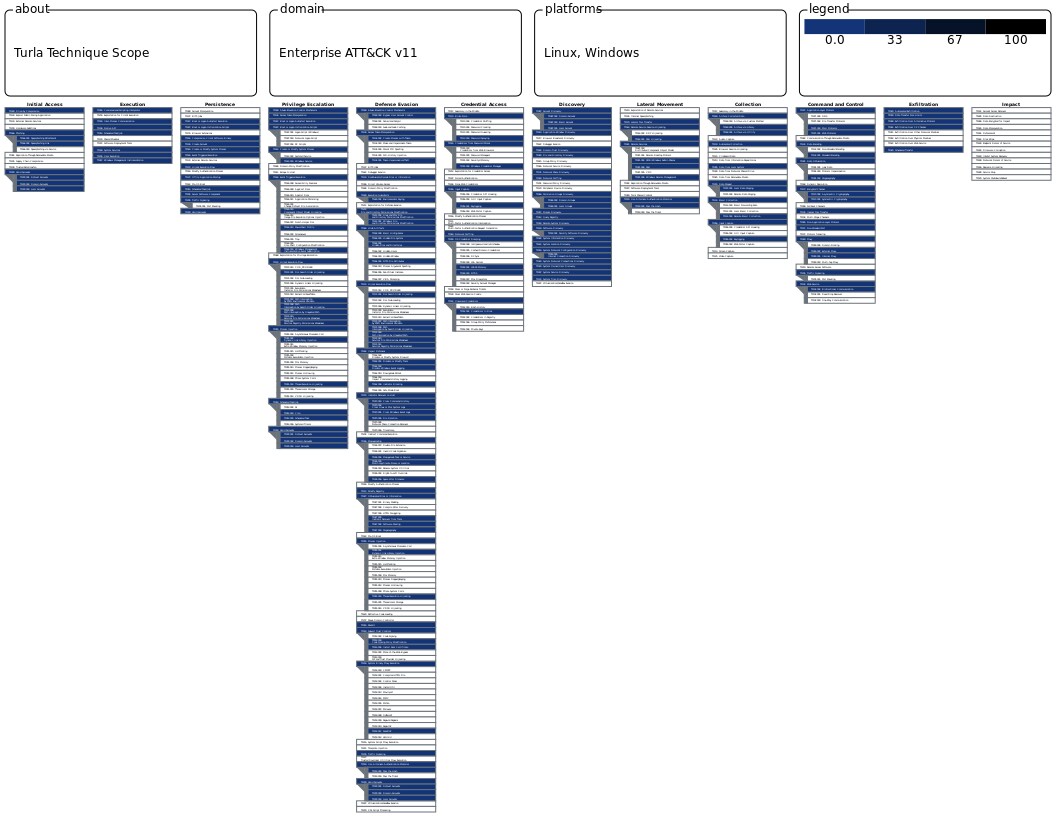
Caption: The MITRE ATT&CK framework: Turla. Explore in ATT&CK Navigator. Note: The items in blue are the techniques in the MITRE ATT&CK Enterprise framework that were emulated.
Main Use Cases for MITRE ATT&CK
MITRE ATT&CK is a cornerstone for various cybersecurity applications, offering a structured approach to understanding and mitigating adversary behaviors. Understanding and leveraging MITRE ATT&CK's primary use cases is crucial for any organization aiming to bolster its defenses against increasingly sophisticated attacks. By delving into these use cases, cybersecurity professionals can harness ATT&CK’s structured knowledge to anticipate better, detect, and counteract adversarial activities.
Security Operations Improvement
Teams utilize MITRE ATT&CK to pinpoint weaknesses in their security operations, focusing on specific adversary techniques that pose the highest risk. By mapping incidents to ATT&CK techniques, they identify patterns and trends, enabling proactive threat hunting and more effective incident response.
Based on ATT&CK's comprehensive database, automated detection rules enhance alert accuracy and reduce false positives. Continuous monitoring aligned with the framework ensures real-time visibility into potential threats. Integrating ATT&CK with SIEM and SOAR platforms streamlines workflows, allowing for quicker threat mitigation. This structured approach fosters a dynamic, adaptive security posture crucial for defending against evolving cyber threats.
Red Teaming and Adversary Emulation
Teams simulate real-world cyber threats by adopting known adversaries' tactics, techniques, and procedures (TTPs). This approach tests defenses under realistic conditions, revealing vulnerabilities that traditional assessments might miss.
Leveraging the MITRE ATT&CK framework, red teams craft sophisticated attack scenarios that mirror the behavior of advanced persistent threats (APTs). Organizations gain invaluable insights into their security posture, identifying gaps and weaknesses.
Adversary emulation exercises foster a deeper understanding of potential attack vectors, enabling the development of robust, targeted defenses. These proactive measures enhance resilience and prepare organizations to respond swiftly and effectively to genuine cyber threats.
Maturity Assessment
Evaluating SOC maturity involves mapping current capabilities against the MITRE ATT&CK framework. Analysts identify gaps in detection and response by comparing their security operations center's (SOC) practices to the framework's comprehensive threat matrix.
This assessment highlights areas needing improvement, such as monitoring specific TTPs or enhancing incident response protocols. By systematically addressing these deficiencies, organizations can elevate their SOC's effectiveness.
Regular maturity assessments ensure continuous alignment with evolving threat landscapes, fostering a proactive security posture. Leveraging ATT&CK for these evaluations benchmarks progress and drives strategic investments in technology and training, ultimately fortifying the organization's defense mechanisms.
Threat Intelligence Assessments
Integrating MITRE ATT&CK into threat intelligence programs transforms raw data into actionable insights. Analysts map threat actor behaviors to the framework, identifying patterns and predicting future attacks. This proactive approach enhances threat detection and prioritization, enabling swift responses to emerging threats.
Organizations can leverage ATT&CK's detailed adversary tactics and techniques to enrich their threat intelligence feeds, making them more relevant and timely. Security teams stay ahead of adversaries by continuously updating their threat models with ATT&CK data, reducing the risk of successful breaches. This dynamic intelligence capability ensures a robust defense against sophisticated cyber threats.
Behavioral Analytics Development
Security teams harness MITRE ATT&CK for behavioral analytics development, transforming raw logs into meaningful patterns. By analyzing adversary tactics and techniques, they pinpoint anomalies and predict malicious activities.
Machine learning models trained on ATT&CK data enhance detection capabilities, identifying sophisticated threats that traditional methods miss. Organizations create custom detection rules aligned with ATT&CK, improving their ability to spot and mitigate attacks in real time.
This approach refines incident response and strengthens overall cybersecurity posture. Through continuous refinement and adaptation, behavioral analytics driven by ATT&CK data empower organizations to stay resilient against evolving cyber threats.
Incident Response
Security teams leverage MITRE ATT&CK to streamline incident response; mapping detected threats to known adversary techniques. This framework enables rapid identification of attack vectors and potential impacts.
Analysts use ATT&CK to prioritize response actions, ensuring critical threats receive immediate attention. By correlating incidents with ATT&CK tactics, teams can uncover hidden connections between seemingly isolated events. This method enhances threat hunting, allowing for proactive measures against future attacks.
Real-time integration with SIEM tools facilitates automated responses, reducing the time required to contain and remediate breaches. Utilizing ATT&CK in incident response accelerates recovery and fortifies defenses against recurrent threats.
Security Posture Assessment
Organizations employ MITRE ATT&CK for comprehensive security posture assessments, identifying gaps in defenses by simulating adversary behaviors. Security teams map existing controls against ATT&CK techniques to pinpoint vulnerabilities and areas requiring enhancement.
This approach reveals how well current defenses can detect and mitigate specific tactics, techniques, and procedures (TTPs). Organizations stay ahead of evolving threats by continuously updating their security measures based on ATT&CK findings.
Regular assessments foster a proactive security culture, ensuring defenses evolve with the threat landscape. This method bolsters resilience and aligns security investments with actual risk exposure.
Detection and Monitoring
Security teams leverage MITRE ATT&CK for real-time detection and monitoring of adversarial activities. By mapping observed behaviors to ATT&CK techniques, they swiftly identify and respond to threats.
Automated systems integrate ATT&CK data to enhance alert accuracy and reduce false positives. Analysts use ATT&CK matrices to contextualize alerts, enabling quicker prioritization and investigation.
Continuous monitoring aligned with ATT&CK ensures that emerging threats are detected early, minimizing potential damage. This proactive approach allows organizations to adapt their defenses dynamically, maintaining robust security postures in the face of evolving cyber threats.
Training and Awareness
Employees engage with simulated attack scenarios mapped to MITRE ATT&CK, enhancing their ability to recognize and counteract real-world threats. Interactive training modules incorporate ATT&CK techniques, fostering a deeper understanding of adversary behaviors.
Regular workshops and drills ensure that staff remain vigilant and proficient in identifying suspicious activities. Organizations use ATT&CK-based assessments to gauge the effectiveness of their training programs, adjusting strategies as needed.
This continuous learning environment cultivates a culture of security awareness, empowering employees to act decisively against potential breaches. Companies bolster their defense mechanisms by embedding ATT&CK into training, creating a more resilient cybersecurity framework.
Tools and Technology Evaluation
Organizations leverage MITRE ATT&CK to evaluate cybersecurity tools and technologies rigorously. By mapping tool capabilities against ATT&CK techniques, they identify gaps and strengths in their defenses.
Security teams simulate adversary tactics to test the effectiveness of detection and response solutions. This systematic approach ensures that investments in cybersecurity yield tangible improvements. Real-world attack emulations provide actionable insights, enabling fine-tuning of security measures.
Continuous evaluation against the ATT&CK framework helps maintain an adaptive and robust security posture, ensuring that tools evolve in response to emerging threats. This proactive stance significantly enhances an organization's resilience against sophisticated cyber adversaries.
Real-World Applications of MITRE ATT&CK
Organizations use MITRE ATT&CK to enhance cybersecurity strategies. Security teams simulate adversary behavior, identify weaknesses, and improve defenses. CISOs align security programs with ATT&CK's models, allocating resources for critical assets.
Incident mapping to ATT&CK allows for precise attack analysis and enables faster responses. The framework supports proactive threat hunting and fosters collaboration. Continuous adaptation to ATT&CK helps organizations stay ahead of threats, strengthening their security posture.
Examples of Use Cases in Action
- Security analysts at a global financial institution utilize MITRE ATT&CK to detect and mitigate advanced persistent threats. By mapping detected activities to ATT&CK techniques, they identify patterns indicative of sophisticated cyber-attacks.
- A healthcare provider employs ATT&CK for threat hunting, discovering previously undetected lateral movement within their network.
- In the energy sector, companies simulate attacks using ATT&CK’s adversary emulation plans, revealing critical vulnerabilities in industrial control systems.
- Law enforcement agencies leverage ATT&CK to analyze cybercrime tactics, enhancing their investigative capabilities.
- A multinational tech firm integrates MITRE ATT&CK into its security operations center, drastically reducing incident response times. By correlating real-time alerts with ATT&CK techniques, analysts swiftly pinpoint the root cause of breaches.
- A government agency employs ATT&CK to train cybersecurity teams, using simulated attack scenarios to enhance defensive strategies.
- In the retail sector, a major chain leverages ATT&CK to audit third-party vendor security, identifying gaps that could lead to supply chain attacks.
These practical applications demonstrate ATT&CK’s versatility in fortifying diverse sectors against evolving cyber threats, its pivotal role in strengthening cybersecurity frameworks across various industries, and its practical utility in real-world scenarios.
Through the innovative creation of ATT&CK, MITRE is actively working towards solving complex challenges to make the world safer. By fostering collaboration within communities, MITRE aims to enhance cybersecurity measures. ATT&CK is openly accessible and can be utilized by individuals and organizations at no cost.