-
What Is MITRE ATT&CK Framework?
- MITRE ATT&CK Framework Explained
- Structuring Adversary Behavior by Tactic
- MITRE ATT&CK Tactics and Their Role in Security Intelligence
- MITRE ATT&CK Techniques
- MITRE ATT&CK Use Cases
- Using the MITRE ATT&CK Framework during a Live Attack
- Comparing MITRE ATT&CK and the Cyber Kill Chain
- Advancing Organizational Maturity with ATT&CK
- Toward a Behavioral Framework for Securing AI
- MITRE ATT&CK Framework FAQs
- How Do I Implement MITRE ATT&CK Techniques?
-
What is the MITRE ATT&CK Matrix?
- MITRE ATT&CK Matrix Explained
- Key Components of MITRE ATT&CK: Tactics, Techniques, and Procedures
- Diverse MITRE ATT&CK Matrices: Adapting to Specific Environments
- How Organizations Operationalize MITRE ATT&CK
- Implementing and Maintaining a MITRE ATT&CK Program
- Benefits of Leveraging the MITRE ATT&CK Framework
- Common Challenges and Solutions
- MITRE ATT&CK and the Cybersecurity Landscape
- MITRE ATT&CK Matrix FAQs
-
What Are MITRE ATT&CK Techniques?
- MITRE ATT&CK Techniques Explained
- The Anatomy of a MITRE ATT&CK Technique
- Understanding Common and Emerging ATT&CK Techniques
- Detecting and Mitigating MITRE ATT&CK Techniques
- Leveraging ATT&CK Techniques for Enhanced Security Operations
- The Future Evolution of ATT&CK Techniques
- MITRE ATT&CK Techniques FAQs
-
How Has MITRE ATT&CK Evolved?
- Evolution of MITRE ATT&CK Explained
- The Historical Trajectory of MITRE ATT&CK
- Why TTPs Matter: Shifting the Cybersecurity Paradigm
- Key Milestones in ATT&CK's Expansion and Refinement
- Core Components and Their Evolving Definition
- Why the Evolution Matters: Benefits for Cybersecurity Professionals
- Addressing the Evolving Threat Landscape with ATT&CK
- Operationalizing the Framework: Practical Applications and Challenges
- The Future of MITRE ATT&CK
- Evolution of MITRE ATT&CK FAQs
- What Are MITRE ATT&CK Use Cases?
- How Does MITRE ATT&CK Apply to Different Technologies?
-
What is the Difference Between MITRE ATT&CK Sub-Techniques and Procedures?
- Understanding the MITRE ATT&CK Framework
- Exploring Sub-Techniques in the ATT&CK Framework
- Exploring Procedures in the ATT&CK Framework
- The Role of Sub-Techniques in Cybersecurity Strategies
- Procedures as a Tool for Detailed Threat Analysis
- Continuous Evolution: Staying Updated with ATT&CK Framework
- MITRE ATT&CK Sub-Techniques vs. Procedures FAQs
What Is MITRE ATT&CK for CISOs?
MITRE ATT&CK for CISOs is a comprehensive, globally accessible knowledge base of adversary tactics and techniques based on real-world observations. It provides CISOs with a common language and framework to understand, evaluate, and improve an organization's defensive posture against cyber threats.
MITRE ATT&CK Explained
The MITRE ATT&CK framework is a strategically organized compendium that describes the various stages of a cyberattack lifecycle, from initial reconnaissance to exfiltration and impact.
For CISOs, this framework serves as a critical tool for mapping adversary behavior to defensive capabilities, enabling a proactive approach to cybersecurity that moves beyond traditional signature-based detection to a more nuanced understanding of threats.
Understanding ATT&CK's structure empowers security leaders to:
- Prioritize investments
- Develop more effective security controls
- Train teams with a clear, actionable context
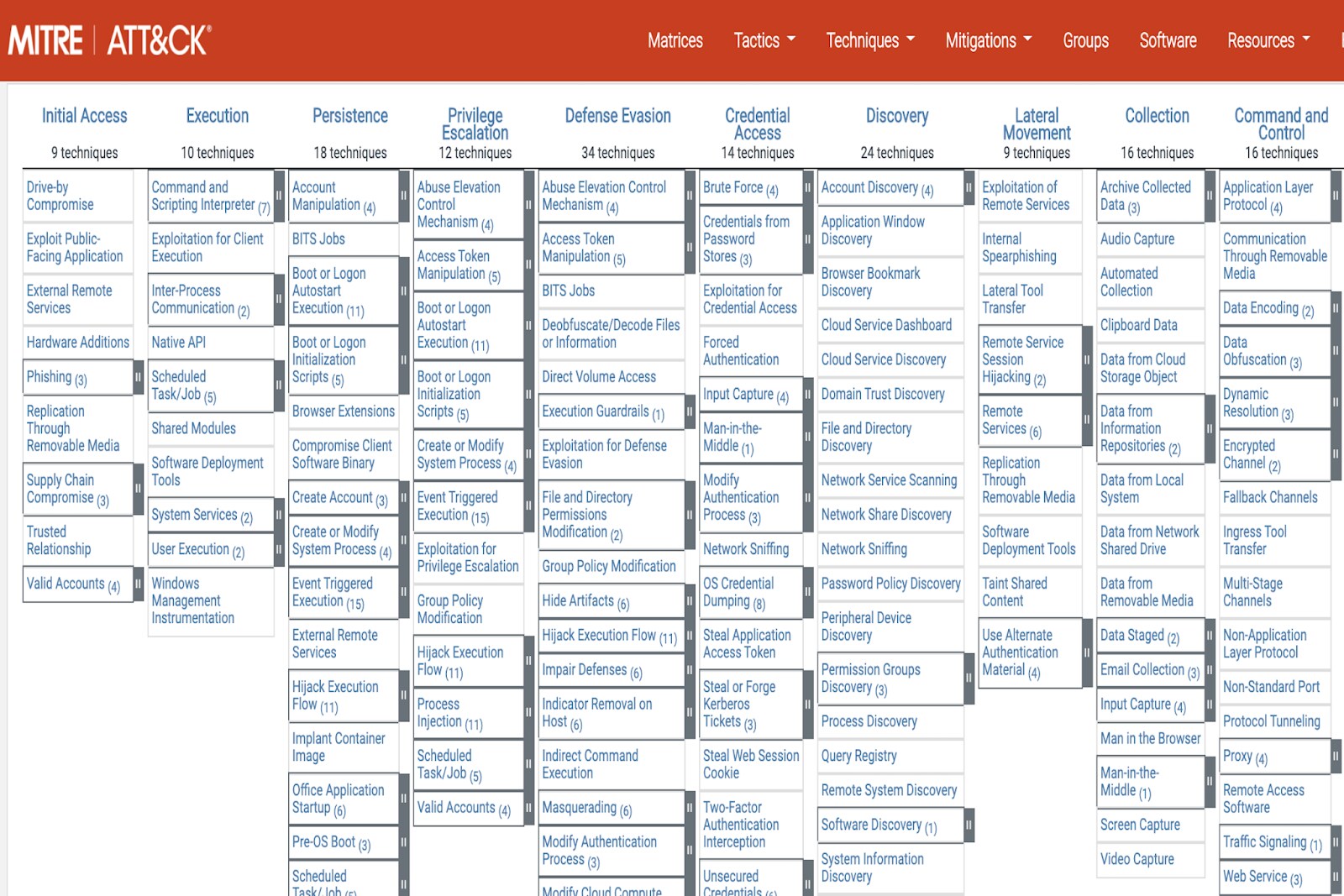
Figure 1: Understanding the MITRE ATT&CK Framework
Benefits of MITRE ATT&CK for CISOs
Leveraging the MITRE ATT&CK framework offers significant advantages for CISOs in enhancing their organization's cybersecurity posture. It provides a structured approach to understanding adversary methodologies.
Enhanced Threat Intelligence Integration
MITRE ATT&CK provides a standardized vocabulary for describing adversary behavior, facilitating the seamless integration of threat intelligence feeds. This common language enables CISOs to correlate external threat data with internal security events more effectively.
It transforms raw threat data into actionable insights, enabling security teams to understand specific tactics and techniques relevant to their environment. For CISOs, this results in a more unified view of the threat landscape and improved strategic decision-making.
Improved Security Control Validation and Optimization
CISOs can map existing security controls against the tactics and techniques outlined in the MITRE ATT&CK framework. This mapping identifies gaps in defensive coverage and validates the effectiveness of current security measures.
It allows for a data-driven approach to optimize security investments, ensuring resources are allocated where they can have the most significant impact on mitigating known adversary behaviors. This validation helps CISOs answer critical questions about the return on their security investments.
Streamlined Incident Response and Analysis
During a security incident, the MITRE ATT&CK framework serves as a common reference point for incident response teams, enabling faster and more accurate analysis of adversary actions by categorizing observed behaviors into known tactics and techniques.
This streamlined analysis reduces dwell time and enhances the efficiency of containment and eradication efforts. For instance, Unit 42 incident response teams frequently utilize ATT&CK to dissect complex attacks, thereby accelerating their understanding of adversary playbooks and enabling swifter resolution.
Proactive Threat Hunting Capabilities
MITRE ATT&CK empowers security teams to transition from reactive defense to proactive threat hunting. By understanding the techniques adversaries commonly employ, analysts can actively search for evidence of these techniques within their network.
This proactive approach helps detect sophisticated threats that might evade traditional signature-based defenses, significantly improving an organization's resilience. CISOs can direct their teams to hunt for specific, high-priority ATT&CK techniques relevant to their industry or threat profile.
Enhanced Communication with Stakeholders
CISOs often struggle to articulate cybersecurity risks and the value of security investments to non-technical stakeholders. MITRE ATT&CK provides a clear, universally understood framework for explaining potential attack scenarios and the protective measures in place.
This enhances communication, fostering a better understanding and support for cybersecurity initiatives throughout the organization. CISOs can utilize the framework to demonstrate residual risk and the strategic impact of security programs to boards and executive leadership.
How MITRE ATT&CK Works for Cybersecurity Leaders
MITRE ATT&CK functions by cataloging adversary behaviors across various stages of an attack. It provides a detailed breakdown of tactics, which represent the "why" of an adversary's action (e.g., initial access), and techniques, which represent the "how" (e.g., spearphishing attachment).
The ATT&CK Matrix: Tactics and Techniques
The core of the MITRE ATT&CK framework is its matrix structure, which categorizes adversary behaviors. Each tactic in the matrix encompasses multiple techniques, providing a granular view of how adversaries achieve their objectives. Understanding this structure is fundamental for CISOs to grasp the full scope of adversary methods.
Tactics: Adversary Goals
Tactics represent the high-level objectives adversaries aim to achieve during an attack. These include:
- Reconnaissance: Gathering information to plan future attacks.
- Resource Development: Establishing resources to support operations.
- Initial Access: Gaining a foothold in a network.
- Execution: Running malicious code.
- Persistence: Maintaining access to systems.
- Privilege Escalation: Gaining higher-level permissions.
- Defense Evasion: Avoiding detection by security measures.
- Credential Access: Stealing usernames and passwords.
- Discovery: Learning about the environment.
- Lateral Movement: Moving through the network.
- Collection: Gathering data of interest to the adversary.
- Exfiltration: Stealing data from the network.
- Command and Control: Communicating with compromised systems.
- Impact: Disrupting, corrupting, or destroying systems or data.
Techniques: Adversary Methods
Techniques are the specific methods adversaries use to achieve a tactical objective. Each tactic has multiple associated techniques, often with sub-techniques for even greater specificity.
For example, under "Initial Access," techniques include "Phishing: Spearphishing Attachment" or "External Remote Services." Understanding these granular techniques enables CISOs to focus on specific, actionable defensive countermeasures, ensuring their security teams are prepared for varied attack approaches.
Mapping Controls to ATT&CK
CISOs can gain a clear understanding of their defensive posture by systematically mapping security controls to the MITRE ATT&CK framework. This process involves identifying how existing security solutions and processes detect, prevent, or mitigate specific ATT&CK techniques, thereby revealing areas of strong coverage and potential blind spots.
Identifying Coverage Gaps
By overlaying current security tools and policies onto the ATT&CK matrix, CISOs can visually identify tactics and techniques for which they lack adequate protection. This gap analysis is crucial for making informed decisions about where to invest in new technologies or enhance existing capabilities.
For example, if "Lateral Movement: Remote Services" techniques are not adequately covered, it signals a need to strengthen network segmentation or authentication policies to reduce an adversary's ability to move freely within the network.
Prioritizing Remediation Efforts
The insights gained from mapping controls allow CISOs to prioritize remediation efforts based on the most prevalent or impactful adversary techniques. This ensures that resources are directed toward addressing the highest-risk areas, aligning security strategy with observed threat landscapes.
Prioritization also considers the organization's specific risk profile and critical assets, allowing CISOs to make data-driven decisions that balance risk and resource allocation. This strategic prioritization is key to maximizing the effectiveness of security investments.
Implementing MITRE ATT&CK in Your Security Operations
Integrating MITRE ATT&CK into daily security operations requires a strategic approach. It involves a shift in mindset from simply blocking known threats to understanding and countering adversary behaviors. CISOs must champion this shift to build a truly threat-informed defense.
Assessing Current Security Posture
A baseline assessment of an organization's security posture against the MITRE ATT&CK framework is the initial step. This assessment helps identify current capabilities and limitations, providing CISOs with the foundational knowledge needed to build an effective security roadmap.
Gap Analysis and Heatmaps
Conducting a gap analysis involves comparing an organization's existing defenses against the comprehensive list of ATT&CK techniques. This process often results in a "heatmap" visualization, where different colors indicate the level of coverage for each technique, ranging from fully mitigated to no coverage.
This visual representation provides CISOs with a quick and intuitive understanding of their defensive strengths and weaknesses, facilitating executive-level discussions about security priorities.
Prioritizing Techniques Based on Risk
Not all ATT&CK techniques pose the same level of risk to every organization. CISOs must prioritize techniques based on factors such as:
- Their likelihood of being exploited
- The potential impact of a successful attack
- The specific threat actors targeting their industry.
This risk-based prioritization ensures that resources are allocated efficiently to address the most critical threats, aligning security efforts with business objectives.
Integrating ATT&CK with Security Tools
Seamless integration of the MITRE ATT&CK framework with existing security tools maximizes its utility and operational efficiency. This integration transforms threat intelligence into actionable insights within the security ecosystem, providing CISOs with greater visibility and control.
SIEM and EDR Correlation
Security Information and Event Management (SIEM) and Endpoint Detection and Response (EDR) systems are crucial for operationalizing ATT&CK. By configuring these tools to ingest and correlate events with ATT&CK techniques, security analysts can quickly identify patterns of adversary behavior.
This enables faster detection and response by providing context to isolated security alerts. For instance, an EDR detecting a suspicious PowerShell command can be correlated with the "Execution: PowerShell" technique, informing a more targeted response.
Automated Playbooks and Response
Automating response actions based on detected ATT&CK techniques significantly reduces response times. Security orchestration, automation, and response (SOAR) platforms can be configured to trigger specific playbooks when certain ATT&CK techniques are identified. This automation streamlines the incident response process, allowing security teams to focus on more complex analytical tasks, while CISOs gain assurance in rapid, consistent responses.
Training and Skill Development
Effective utilization of MITRE ATT&CK requires that security teams possess the necessary knowledge and skills to leverage it effectively. Continuous training and development are essential to ensure proficiency in applying the framework, a critical investment for CISOs.
Upskilling Security Analysts
Security analysts should understand the ATT&CK framework very well, including its various tactics, techniques, and sub-techniques. Training should focus on:
- How to map observed behaviors to the framework
- How to use ATT&CK for threat hunting
- How to interpret ATT&CK-tagged alerts
This upskilling empowers analysts to make more informed decisions during investigations and helps build a stronger, more capable security operations center.
Red Team and Blue Team Collaboration
Encouraging collaboration between red teams (offensive security) and blue teams (defensive security) using MITRE ATT&CK as a common language can really make a difference in the strength of an organization’s security posture. Red teams can simulate adversary techniques outlined in ATT&CK, while blue teams can practice detecting and responding to these simulations.
This iterative process enables continuous improvement of defensive capabilities, providing CISOs with a clear understanding of their security program's effectiveness in real-world scenarios. This form of "purple teaming" helps bridge the gap between offensive and defensive security.
Challenges and Best Practices for CISOs
Implementing MITRE ATT&CK effectively comes with its own set of challenges, but adopting best practices can help CISOs overcome these hurdles and maximize the framework's benefits.
Overcoming Implementation Hurdles
Organizations often face initial challenges when integrating MITRE ATT&CK into their security operations. These hurdles can range from a lack of internal expertise to the sheer volume of data involved.
Data Overload and Prioritization
The vastness of the ATT&CK framework can lead to data overload, making it challenging for teams to prioritize their focus. CISOs should avoid the temptation to address every single technique simultaneously. Instead, prioritize based on threat intelligence relevant to the organization's industry, its specific attack surface, and the critical assets that need protection.
Unit 42 research indicates that focusing on the most prevalent techniques used by active threat groups yields better defensive outcomes, enabling CISOs to make targeted, high-impact decisions.
Maintaining Up-to-Date Mappings
The threat landscape is constantly evolving, and new adversary techniques emerge regularly. Therefore, maintaining up-to-date mappings between security controls and ATT&CK techniques is an ongoing challenge.
Regular reviews and updates to these mappings are crucial to ensure the continued relevance and effectiveness of the defensive posture. This requires a commitment to continuous learning and adaptation within the security team, a responsibility CISOs must actively manage.
Best Practices for Maximizing ATT&CK Value
Adopting certain best practices can significantly enhance the value derived from the MITRE ATT&CK framework. These practices ensure the framework is not just a theoretical concept but a practical tool for improving cybersecurity:
Continuous Assessment and Improvement
MITRE ATT&CK should be viewed as a living framework that requires continuous assessment and improvement. Regular exercises, such as red team engagements and purple teaming (collaborative red and blue teaming), can validate the effectiveness of existing controls against specific ATT&CK techniques.
The findings from these exercises should inform iterative improvements to security processes and technologies, providing CISOs with measurable progress.
Culture of Threat-Informed Defense
Building a threat-informed defense is crucial, as it shifts the focus from compliance to anticipating adversary actions based on real-world intelligence. This requires training, leadership support, and integrating ATT&CK into all security operations, from design to incident response. CISOs play a key role in embedding this proactive mindset.
