- What is Malware? Detecting, Preventing & Managing Threats
-
Malware vs. Exploits
- What is Multi-Extortion Ransomware?
- What is Malware vs. Ransomware?
- What Is Malware Protection? Best Practices for Modern Businesses
-
Expanding Targets for New SunOrcal Malware Variant
-
What Are Fileless Malware Attacks and “Living Off the Land”? Unit 42 Explains
What is Ransomware as a Service (RaaS)?
Ransomware as a service (RaaS) is a malicious adaptation of the software as a service (SaaS) business model. It is a subscription-based model that sells or rents predeveloped ransomware tools to buyers, called ransomware affiliates, to execute ransomware attacks.
Before introducing the RaaS model, threat actors needed some proficiency in writing or accessing code before attempting a ransomware attack. Ransomware as a service opens these attacks to criminals who lack coding knowledge; however, many RaaS organizations are specific about who is given access. Some high-profile groups even interview potential affiliates or check their background and digital footprint.
The RaaS operations model makes it easy for anyone to execute a ransom campaign, providing threat actors with expert-level software to encrypt and decrypt files as well as 24/7 software support. Once they have access to the ransomware, it is the affiliates’ job to launch a successful attack through phishing or software exploits, for example.
Through its recent success, RaaS has identified itself as a significant cybersecurity threat. Understanding what it is, how it works, and how to safeguard your organization against it is crucial for protecting your valuable data.
How Dangerous Is Ransomware as a Service (RaaS)?
According to the 2022 Unit 42 Ransomware Threat Report, ransomware is seeing significant growth as a cyberthreat:
- Last year, the average ransom demand on cases climbed 144% to $2.2 million.
- The average payment rose 78% percent to $541,010.
- Unit 42® is actively tracking at least 56 active RaaS groups.
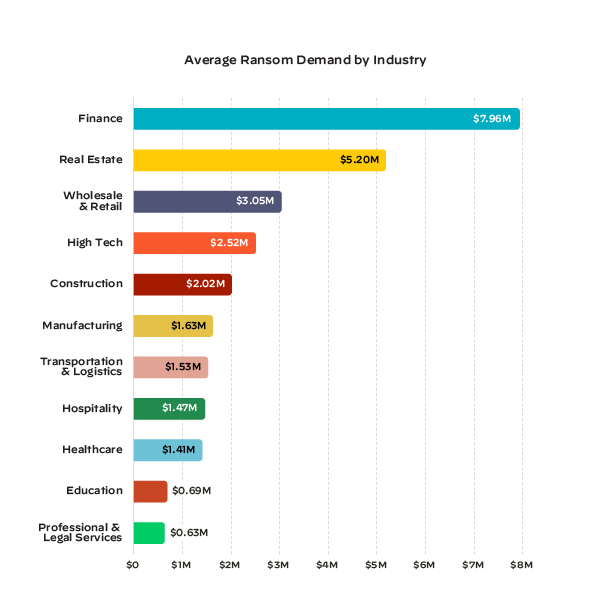
Figure 1: Average ransom demand per industry as seen by Unit 42 over the course of 2022
In addition, the FBI's Internet Crime Complaint Center (ICCC) reported 2,084 ransomware complaints from January to July 31, 2021. This represents a 62% year-over-year increase. More recently, the Cybersecurity and Infrastructure Security Agency (CISA) reported in February 2022 that it is aware of ransomware incidents against 14 of the 16 U.S. critical infrastructure sectors. Ransomware and the groups that design it are expected to continue growing, especially since their business model is both easy and profitable.
How Does the Ransomware as a Service (RaaS) Business Model Work?
A vital component of RaaS-style attacks is that the affiliates have predesigned playbooks and tip sheets for executing a successful attack. As a part of this, they can quickly and effectively scope out victim environments, deploy malware, use tools to harvest credentials, steal sensitive data, and subsequently encrypt files en masse.
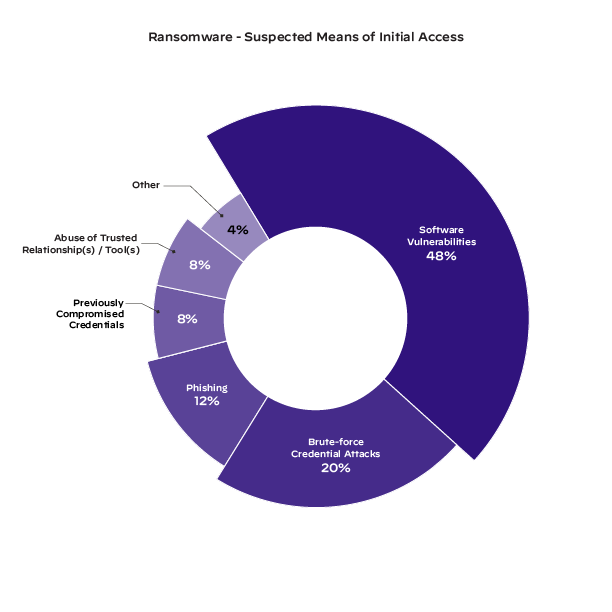
Figure 2: Types of attacks that occurred once ransomware entered an environment
In addition to the ransomware, RaaS organizations provide quality-of-life features to their affiliates. These include infrastructure and services for negotiation communications as well as platforms for publishing stolen data, like leak sites or Telegram channels, if victims don’t pay the ransom demand. Profits from a successful ransom are divided between the RaaS and the affiliate based on a specific revenue model.
What Are the RaaS Revenue Models?
Business occurs on the dark web, and payments are made through different cryptocurrencies. While the exact payment details vary depending on the RaaS revenue model, affiliates tend to take the significant cut of a ransom — about 70-80%. There are four ways profits can be split:
- Affiliate RaaS: If successful, a small percentage of profits go to the RaaS creator to run a more efficient service and streamline their ransomware attacks.
- Subscription-based RaaS:Users pay a monthly flat fee for access to the ransomware.
- Lifetime license: Users pay a one-time fee and have unlimited access. They do not have to share any profit with the RaaS group if they're successful. Along with this comes the ability for ransomware operators to buy source code and modify it to fit their needs, as seen with Dharma and Phobos.
- RaaS partnerships: Profit split is defined when an affiliate gains access to the ransomware. This split is larger than the affiliate model, but payment only occurs if an attack is successful.
The more advanced RaaS operators will build a portal for subscribers to see the status of all infections, ransom payments and other sensitive information about their targets. Quality-of-life efforts are worth it, as ransomware remains one of the most financially devastating attacks in the current threat landscape.
How Does Ransomware as a Service (RaaS) Attacks Work?
Developers focus on creating and supplying the necessary RaaS tools to interested affiliates. Affiliates identify network intrusion opportunities and deploy the actual ransomware.
If an attack is successful, the ransomware sends an extortion message to the victim demanding a ransom. This can include threats like posting the organization’s data on the dark web or deleting it entirely if the victim does not pay by a specified deadline. Some groups prefer to threaten in specific ways, while others let affiliates do as they would prefer.
Ransomware as a Service (RaaS) Examples
There is an abundance of ransomware as a service in circulation, and while cyber professionals are aware of and tracking many different groups, it’s important to be on guard and prepared for anything. Unit 42 has done a lot of research on different RaaS groups to prepare SOCs for potential attacks. Here are some groups that Unit 42 has observed who are active as of November 2022.
LockBit
This ransomware emerged in June 2021 and exploits SMB and PowerShell to spread malware through a compromised network. It claims to have the fastest market encryption and has compromised over 50 organizations across different industries.
BlackCat
Also known as ALPHV, BlackCat is coded in the Rust programming language and is easy to compile against different operating architectures. This ransomware is dangerous as it’s highly customizable and easy to individualize.
Hive
First observed in June 2021, the Hive RaaS group pressures victims to pay by releasing details of the attack on different leak sites and even social media, including the date and time of attacks and a countdown to information leaks.
Dharma
First identified in 2016, Dharma targets victims through malware attachments in phishing emails. Several other ransomware groups have used Dharma as source code.
While these are some of the most infamous groups, unfortunately, there are many more RaaS groups. You can learn about other groups and affiliate programs that Unit 42 has investigated here. Unit 42 continues to observe and reveal the illegal tactics of these groups to prepare organizations and keep them safe.
Is Ransomware as a Service (RaaS) Legal?
RaaS is an illegal industry developed by organized crime syndicates, and involvement in any ransomware campaign is unlawful. This includes buying RaaS kits on the dark web with the intent of causing damage or transmitting unwanted code to victims as well as breaching networks, stealing, encrypting and downloading system data and files, and extorting ransom from victims.
Ransomware cases are investigated by the FBI and prosecuted under the Computer Fraud and Abuse Act, and more information is discovered and made public by threat intelligence groups like Unit 42. An organization can prepare for RaaS attacks by being familiar with how the programs operate and taking preventive measures in their environment.
7 Ways to Protect Yourself Against Ransomware as a Service (RaaS) Attacks
There are several effective ways to safeguard against a RaaS attack. Methods to minimize damage and prevent these attacks from happening include:
- Patch and monitor vulnerabilities with the help of attack surface management platforms like Cortex Xpanse to limit entryways into your system.
- Restrict administrative and system access to users who absolutely need it.
- Ensure your endpoint passwords are highly secure and updated regularly.
- Educate staff on social engineering tactics like phishing and other cybersecurity practices.
- Back up data regularly on external media or immutable storage. Refrain from relying exclusively on cloud storage.
- Use a combination of antivirus and endpoint detection and response (EDR) solutions like Cortex XDR.
- Consider lining up an incident response retainer in advance. Many IR firms are overflowing with work, but having a retainer with a guaranteed SLA will ensure help in the event of a cybersecurity attack.
Implementing these best practices will reinforce both your SOC and your organization against RaaS. For a deeper dive into understanding and testing your environment, many SOCs choose to undergo a ransomware readiness assessment.
How to Assess Your Ransomware Readiness
Knowing exactly how an environment will react to an attack is the best way to prepare for one. Unit 42 offers a Ransomware Readiness Assessment to help develop a comprehensive understanding of your ability to prevent and respond to these types of threats. Let a threat researcher test your system in a non-disruptive way with tabletop exercises, purple teaming and more.
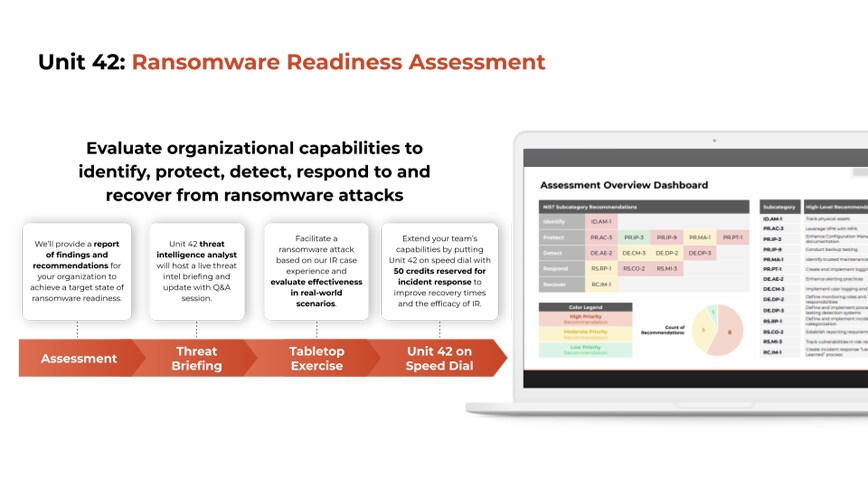
Figure 3: Graphic outlining the Unit 42 Ransomware Readiness Assessment
Our team is here to help you prepare for and respond to the most challenging cyberthreats. If you are experiencing an active breach or think you may have been impacted by a cyber incident, contact Unit 42.