-
What Is Ransomware?
- Ransomware Key Takeaways
- Why Ransomware Matters
- Stages of a Ransomware Attack
- How Ransomware Uses Psychological Pressure
- Types of Ransomware
- Example Ransomware Strains
- Role of Human Behavior in Cybersecurity
- Ransom Payment and Prevention
- Creating and Testing an Incident Response Plan
- Understanding if You Have a Ransomware Infection
- Difference Between Malware and Ransomware
- What is Multi-Extortion Ransomware?
- Why Ransomware Is Illegal
- Recovery from Ransomware Attacks
- Is Ransomware Still a Threat?
- Future-Proofing Against Ransomware
- Ransomware FAQs
- What Are the Most Common Types of Ransomware?
-
What is Ransomware Response and Recovery?
- How to Respond to a Ransomware Attack
- How Do Ransomware Attacks Begin?
- Reducing Dwell Time
- Common Threat Actor Techniques
- Data Theft and Multi-extortion Ransomware
- How to Uninstall Ransomware and Retrieve Data
- Steps to Recovery After a Ransomware Attack
- ® Incident Response Methodology
- Ransomware Removal and Recovery FAQs
- What is Ransomware Prevention?
What are Ransomware Attacks?
Ransomware attack methods involve malicious software designed to block access to a victim's system or data, demanding a ransom to restore access. Common methods include:
- Phishing Emails
- Exploiting Vulnerabilities
- Remote Desktop Protocol (RDP) Attacks
- Malvertising
- Drive-by Downloads
- Malware-as-a-Service
These methods aim to encrypt files or lock systems, demanding payment for decryption keys or restored access.
How Do Ransomware Attacks Happen?
Ransomware attacks have become a major cybersecurity threat, affecting individuals and businesses worldwide. These attacks typically occur when malicious software is used to block access to a victim's files or system, demanding a ransom to restore access.
Cybercriminals employ a variety of methods to deliver ransomware, ranging from phishing emails and exploiting software vulnerabilities to using remote access tools and malicious ads. Once the ransomware takes hold, it encrypts or locks down critical data, leaving victims with little choice but to pay the ransom in exchange for a decryption key or restored access. Understanding how these attacks happen is crucial for protecting against them.
Ransomware starts with cybercriminals entering a system and encrypting all data, then offering a decryption key if the victim agrees to pay a ransom through cryptocurrency. In addition to entering a system and depositing encryption malware, some ransomware operators will use multi-extortion ransomware techniques to encourage payment, like copying and exfiltrating the unencrypted data, shaming the victim on social media, threatening additional attacks like DDoS, or leaking the stolen information to clients or on the dark web.
Unit 42 has investigated thousands of ransomware attacks launched against various organizations and helped with quick containment and recovery to save them millions of dollars. Detailed in the 2022 Incident Response Report, Unit 42 identified five main attack vectors that threat actors use to deploy ransomware.
Discover attacker tactics and gain real world insights and expert recommendations to safeguard your business: 2025 Unit 42 Global Incident Response Report.
What Are the 5 Main Ransomware Attack Vectors?
To better prevent ransomware, it is crucial to understand the malicious tactics attackers use to compromise organizations in the first place. Reviewing recent trends in ransomware threats enables the security operations center (SOC) to focus resources on potential breach points, reduce the risk of infection and prepare the organization as a whole.
The five main ransomware attack vectors are:
- Exploitable vulnerabilities
- Brute-force credential attacks
- Social engineering
- Previously compromised credentials
- Abuse of trust
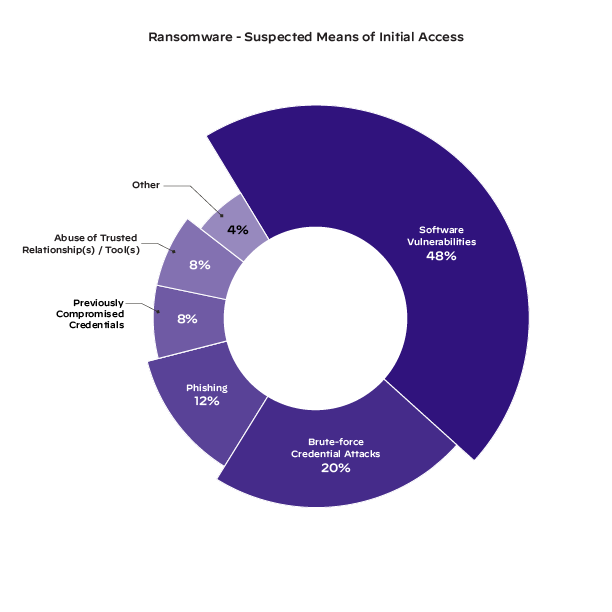
Figure 1: How attackers entered an environment to launch a ransomware attack as observed in Unit 42’s 2022 Incident Response Report
Understanding how these five attack vectors operate and how best to protect them is a crucial first step to ransomware readiness.
1. Exploitable Software Vulnerabilities
Vulnerabilities come in many forms and can be exploited with code designed to take advantage of the gaps or flaws in a program. In the 2022 Unit 42 Incident Response Report, Unit 42 discovered that 48% of ransomware cases began with software vulnerabilities. When an application is exposed to the internet, threat actors may scan for and exploit known vulnerabilities to gain unauthorized access to an environment.
Another vulnerability technique popular among cybercriminals is using exploit kits, which involves inserting code into compromised websites. These websites look normal but contain malicious programs that scan through a connected device for vulnerabilities. If the exploit kit identifies a vulnerability, it will often download a malware payload designed to provide a threat actor with remote access to the system. Once remote access is established, threat actors will then deploy ransomware into the environment.
The best method of software protection is to ensure that all devices on a network are updated frequently. Software companies will regularly release updates that patch any discovered common vulnerabilities and exposures (CVEs), so it’s crucial to update these vulnerabilities before cybercriminals can access them. SOCs can take protection a step further with extended detection and response (XDR) products like Cortex XDR to detect and block attacks. To identify internet-facing vulnerabilities that need to be remediated and automatically remediate dangerous exposures such as remote desktop protocol (RDP), SOCs can adopt active attack surface management (ASM) tools like Cortex Xpanse.
2. Brute-Force Credential Attacks
Brute-force attacks use trial and error to access a system or application. Cybercriminals create and run scripts that automatically input usernames and passwords until a correct login is discovered. This is one of the oldest cybersecurity attacks, and it has maintained its status as a successful tactic over the years.
Brute-force attacks are one of the many reasons that multifactor authentication (MFA) is so important to implement. Systems with MFA require an additional form of verification, like a code from an application or biometrics, before a user is allowed access to the system.
In the event of a successful brute-force attack, platforms like Cortex XSIAM will notify the SOC of abnormal user behaviors and prompt an investigation. Cortex XSIAM integrates seamlessly with MFA platforms to convey suspicious login information the moment it happens, expediting those alerts to the top of the funnel to inform analysts and stop brute-force attacks in their tracks.
3. Social Engineering
Social engineering methods like phishing emails are sent from sources pretending to be trustworthy to encourage victims to click on links and download malware directly. There is often an underlying sense of urgency or danger with these messages to motivate people to action before they can think it through. These attacks can be very successful and, in the instance of ransomware, extremely dangerous and expensive.
Implementing regular cybersecurity training for employees is the best way to protect against social engineering attacks. When employees identify and report phishing attempts, the SOC can investigate the attack and learn from what happened. If a phishing attack is successful, security orchestration, automation and response (SOAR) platforms like Cortex XSOAR can streamline discovery and remediation, automatically shutting down compromised users until the SOC has investigated and removed the attacker from the system.
4. Previously Compromised Credentials
When user credentials are compromised, it is crucial to replace them as quickly as possible. Unfortunately, credential information can be leaked on the dark web without users knowing they’ve been compromised, allowing attackers of all kinds unfettered access to a system. And to make matters worse, many users will use the same password for multiple services, so if one password is compromised, reused passwords can be used against other systems or applications to gain unauthorized access.
In addition to multifactor authentication, encouraging employees to practice good password hygiene is a proven way to prevent attacks from compromised credentials. Using a password manager, changing passwords regularly, making sure they’re complex and not reusing the same password will protect individuals and the organization. Cortex XDR can leverage behavioral analytics to detect and prevent abnormal user behavior even when previously compromised credentials are used to gain unauthorized access into environments.
5. Abuse of Trust
In the chaos of the current threat landscape, it’s important for security professionals to keep an eye on internal threats. Whether an employee feels wronged by their employer or was approached by a threat actor, one of the easiest ways for ransomware to enter an environment is from someone who already has legitimate access.
In case of an abuse of trust incident, products like Cortex XSOAR or platforms like Cortex XSIAM can automate incident response handling to inform security teams and isolate the user in question. Additional protection can be implemented with offboarding best practices to reduce the number of opportunities that a disgruntled employee might have to retaliate.
How to Protect Against Ransomware Attacks
All five methods are damaging ways that an attacker can invade your system. To summarize, we recommend SOCs implement the following if they haven’t already:
- EDR platforms to identify and block attacks
- Cortex XSIAM for full, automated visibility on endpoints, networks and more
- Active ASM platforms like Cortex Xpanse for quick identification and automatic remediation of internet-facing attacks
- SOAR platforms like Cortex XSOAR to streamline discovery and automatically isolate any compromised users
- MFA to verify users before allowing full access to an environment
- Good security practices, like phishing training and password hygiene, among employees to reduce the likelihood of social engineering or brute-force attacks
- Streamlined offboarding for ex-employees to prevent insider attacks
While these methods and platforms are extremely helpful, they will only take you so far. For ransomware specifically, there’s an additional method of preparation that is the most beneficial.
How to Assess Your Ransomware Readiness
Defending against ransomware starts with a plan. Unit 42 offers a Ransomware Readiness Assessment to prepare you to better prevent, detect, respond to and recover from ransomware attacks. Achieve a state of ransomware readiness by validating your response strategy, detecting hidden risks and more.
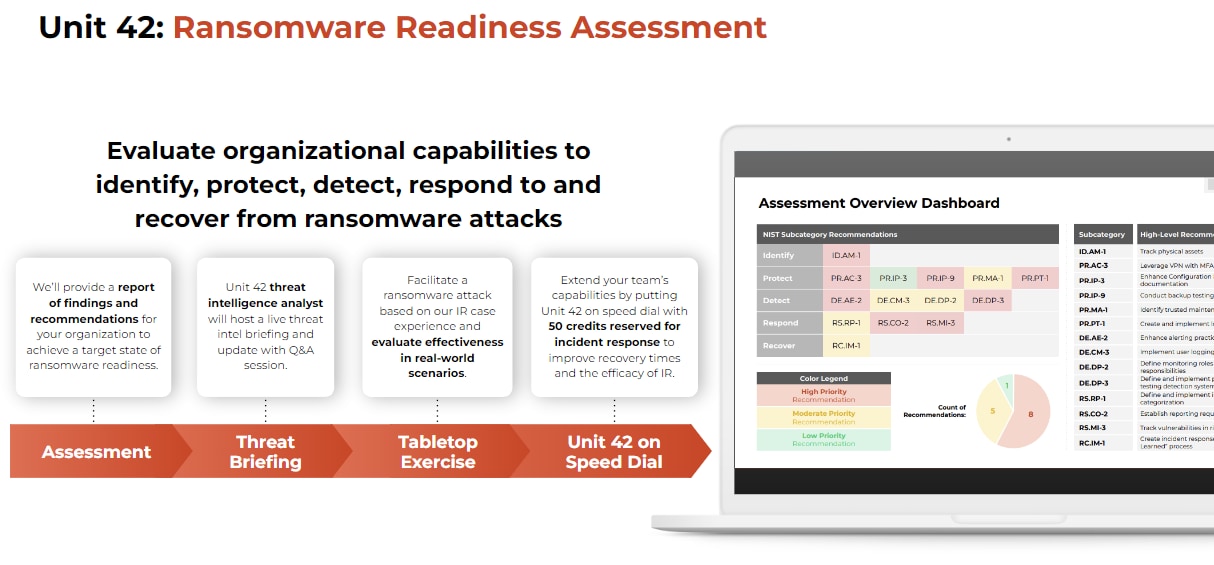
Figure 2: Graphic outlining the Unit 42 Ransomware Readiness Assessment
Our team is here to help you prepare for and respond to the most challenging and malicious cybersecurity threats. If you are experiencing an active breach or think you may have been impacted by a cyber incident, contact Unit 42.
