-
What Is SASE (Secure Access Service Edge)? | A Starter Guide
- Why do businesses today need SASE?
- What is SASE architecture?
- What are the components of SASE?
- What are the use cases for SASE?
- What are the benefits of SASE?
- What are the potential SASE implementation challenges?
- How to choose a SASE provider and what to look for
- How to execute a successful SASE implementation in 6 steps
- What are the most common SASE myths?
- How SASE works with complementary technologies
- Comparing SASE with other security and technology solutions
- What is the history of SASE?
- SASE FAQs
-
What is the cloud-delivered branch?
- What Is SASE for the Cloud?
-
Secure Access Service Edge (SASE) Key Requirements
-
Protecting Data with a SASE Solution
-
End User Experience Monitoring
What Is SSE? | Security Service Edge (SSE)
Security Services Edge (SSE)
The security services edge (SSE) is an emerging cybersecurity concept Gartner introduced in its 2021 Roadmap for SASE Convergence report. According to Gartner, SSE is a collection of integrated, cloud-centric security capabilities that facilitates safe access to websites, software-as-a-service (SaaS) applications and private applications. Specifically, SSE-related security capabilities include:
- Zero Trust Network Access (ZTNA)
- Cloud secure web gateway (SWG)
- Cloud access security broker (CASB)
- Firewall-as-a-service (FWaaS)
Why SSE is Important?
A comprehensive SSE solution provides organizations with the full set of security technologies they need to provide employees, trusted partners and contractors secure remote access to applications, data, tools and other corporate resources, and monitor and track behavior once users access the network. As the hybrid workforce expands, securing those remote and mobile users, and the data and apps they access remain protected.
What is the Difference between SASE and SSE?
SSE provides the security service elements of a comprehensive SASE (pronounced “sassy”) strategy. In particular, SSE delivers access control, threat protection, data security, security monitoring and acceptable use control functionality into a single cloud-delivered solution. SSE combined with SD-WAN forms a comprehensive SASE platform, providing monitoring and policy enforcement with integrated network controls and application APIs augmented by endpoint-based controls.
SASE is a cybersecurity concept Gartner coined in 2019. SASE is the convergence of software-defined wide area networking or SD-WAN, and network security services like CASB, FWaaS and ZTNA into a single, cloud-delivered service model.
According to Gartner, “SASE capabilities are delivered as a service based upon the identity of the entity, real-time context, enterprise security/compliance policies and continuous assessment of risk/trust throughout the sessions. Identities of entities can be associated with people, groups of people (branch offices), devices, applications, services, IoT systems or edge computing locations.”
With the common framework a SASE architecture provides, organizations can simplify management, get consistent visibility and maximize protections for users, devices, applications and data, no matter their location.
SSE Core Capabilities
A SSE solution requires these four fundamental security capabilities.
Zero Trust Network Access (ZTNA)
Zero Trust Network Access (ZTNA) is a category of technologies that provides secure remote access to applications and services based on defined access control policies. Unlike virtual private networks (VPNs), which grant complete access to a LAN, ZTNA solutions default to deny, providing only the access to services the user has been explicitly granted.
When looking at the full capability set that comprises a comprehensive SSE strategy, ZTNA provides a multi-layered, remote-access, security approach that provides redundant layers of inspection and enforcement, specifically:
- Centralized Visibility and Control: Know who’s accessing your data, where it’s stored, and level of sensitivity – and log network traffic where you can.
- Identity-Based Authentication: ZTNA technologies provide users with precise least-privileged access based on fully customizable authentication methods. Even after access has been granted, network security professionals can monitor user behaviors for malicious activity and signs of credential theft, malware and data loss.
- Uniform Security Policies: Enforce security policies on all corporate-owned and third-party applications regardless of where the data resides.
- Granular, Role-Based Access: Only give a user access to the data they absolutely need for their job. Restrict access based on the type of device and location used to connect.
- Post-Connect Threat Monitoring: If an attacker is still able to access the organizational network, ZTNA capabilities are still working and can detect an attacker based on their network activity.
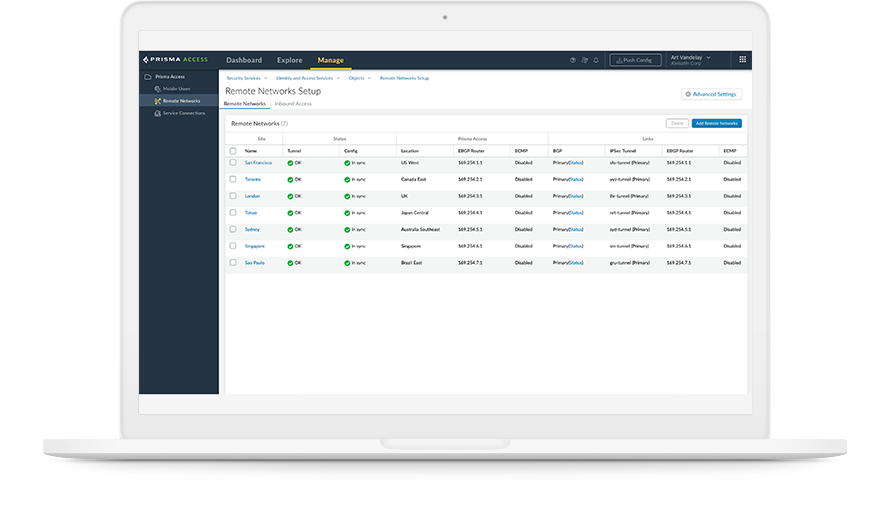
Secure Web Gateway (SWG)
A secure web gateway (SWG) protects users from web-based threats in addition to applying and enforcing corporate acceptable use policies. Instead of connecting directly to a website, a user accesses the SWG, which is then responsible for connecting the user to the desired website and performing functions such as URL filtering, web visibility, malicious content inspection, web access controls and other security measures.
SWGs are an important part of a comprehensive SSE strategy as they provide users secure internet access when they are disconnected from the business VPN. In addition, SWGs enable organizations to:
- Block access to inappropriate websites or content based on acceptable use policies
- Enforce their security policies to make internet access safer
- Help protect data against unauthorized transfer
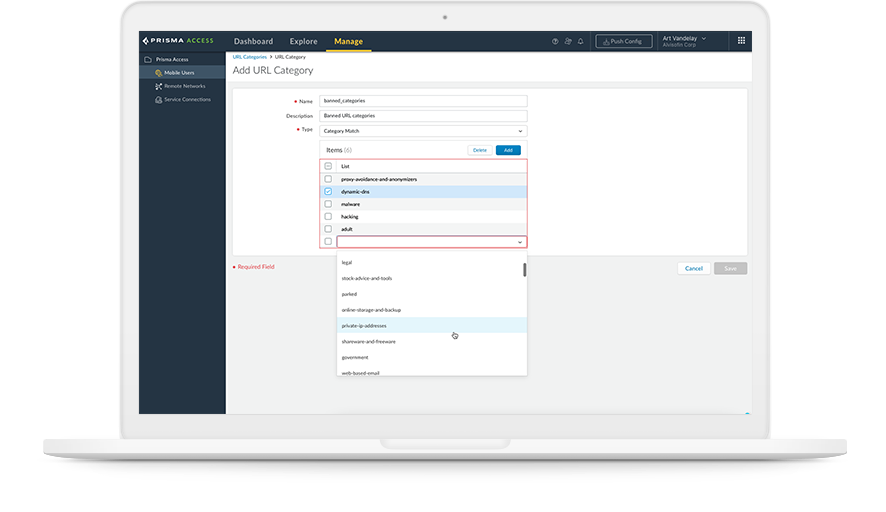
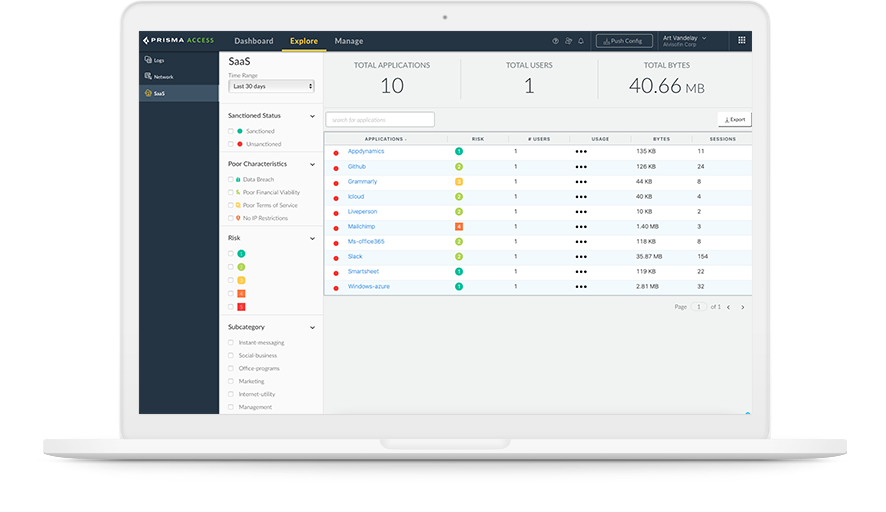
Cloud Access Security Broker (CASB)
CASBs help organizations discover where their data is across multiple software-as-a-service (SaaS) applications and when it’s in motion across cloud environments, on-prem data centers or accessed by mobile workers. A CASB also enforces an organization’s security, governance and compliance policies allowing authorized users to access and consume cloud resources while enabling organizations to effectively and consistently protect their data across multiple locations. There are two types of CASBs available: traditional CASBs and integrated CASBs.
An effective SSE strategy uses an integrated CASB to help organizations keep pace with the SaaS explosion. An integrated CASB uses an in-line security mechanism to automatically discover and control all SaaS risks with existing SaaS applications and the thousands of emerging ones. It also has an API-based security mechanism to scan SaaS applications for sensitive data, malware and policy violations while maintaining compliance and preventing threats in real time without dependence on third-party tools.
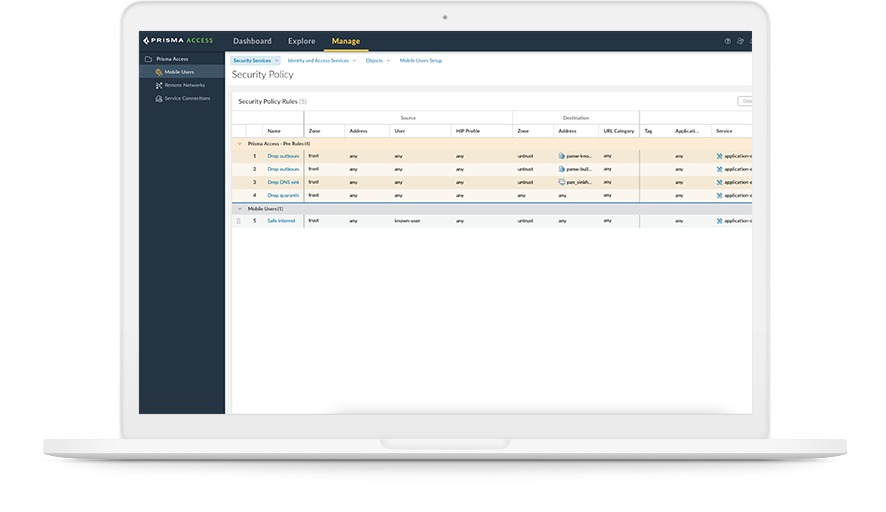
Firewall-as-a-Service (FWaaS)
FWaaS enables firewalls to be delivered as part of a company’s cloud infrastructure to protect cloud-based data and applications.
An SSE strategy uses FWaaS capabilities to enable organizations to aggregate traffic from multiple sources – whether from on-site data centers, branch offices, mobile users or cloud infrastructure. It also provides consistent application and security enforcement of policies across all locations and users while giving complete network visibility and control without deploying physical appliances.
SSE Use Cases & Benefits
Secure Access
With SSE, utilizing a SWG helps to enforce internet access policy control no matter where users are or what data or apps they are accessing. SWGs are an important part of a comprehensive SSE strategy as they provide users secure internet access when they are disconnected from the business VPN. In addition, SWGs enable organizations to:
- Block access to inappropriate websites or content based on acceptable use policies
- Enforce their security policies to make internet access safer
- Help protect data against unauthorized transfer
Better Security
Protecting users and apps is done through CASBs, through inspection, classification, and quarantining malware before the damage is done. An effective SSE strategy uses an integrated CASB to help organizations keep pace with the SaaS explosion.
Visibility & Control
ZTNA 2.0 provides visibility and control over what users are accessing as well as limits exposure by enforcing application-level as opposed to network-level access. ZTNA 2.0 delivers:
- True least-privileged access
- Continuous trust verification
- Continuous security inspection
- Protect all data
- Secure all apps
SSE Deployment & Solutions
Organizations can approach the design and deployment of an effective SSE in two ways.
- Organizations can evaluate separate vendors for each required security technology set and then use internal or third-party resources to knit those capabilities together for a consolidated SSE solution.
While this approach may provide an organization with their favorite capabilities or functionality across the various requirements, it also opens organizations up to a significant integration investment – both at the time of deployment and long term. This approach also requires substantial management and monitoring to ensure all products and services continue to work together as a unified platform, in addition to managing multiple vendor relationships and their various SLAs.
- Organizations can evaluate vendors that provide comprehensive security platforms with each of the necessary SSE capabilities – FWaaS, CASB, SWG, and ZTNA – already integrated. This approach immediately eliminates the management and integration headaches associated with the multi-vendor approach. It also simplifies troubleshooting and system maintenance needs throughout the system life cycle.
Prisma Access offers consolidated best-in-class security in a leading cloud native SSE platform that delivers ZTNA 2.0 with the best user experience on a single unified platform.