Secure Remote Access | Protect Remote Employees from Cyberthreats
Learn how secure remote access enables employees to connect safely to internal networks from offsite locations and its role in protecting remote workers.
The pandemic accelerated the shift to a remote working environment, requiring IT organizations to quickly enable employees to safely work from home. Businesses have seen several positive outcomes as a result of enabling a remote workforce, cementing the remote employee as part of a company’s success moving forward.
Unfortunately, most organizations’ IT networks were not built to support a large population of remote employees long-term. IT professionals need to revisit their network and security strategies to ensure they can expand secure remote access capabilities to a substantially larger remote employee population. What’s more, IT staff need consistent visibility, management, and enforcement to protect their growing remote workforce from cyberthreats while ensuring an optimized user experience, and they need to do this in addition to supporting employees within the corporate perimeter (i.e., within corporate headquarters or branch offices).
This article provides a comprehensive look at secure remote access, the technologies that enable it, and the benefits organizations realize when they deploy a successful secure remote access strategy.
What Is Secure Remote Access?
Secure remote access is the collection of rules, processes, software, and hardware that provide secure access to and availability of data, including LANs or cloud-hosted applications and services for employees, vendors, and other trusted partners who are not physically located within an organization’s corporate headquarters or branch offices. Secure remote access enables these individuals to use the same resources as employees who are physically located within the organization’s corporate perimeter.
Why Is Secure Remote Access Important?
Secure remote access is important for three reasons: to safeguard and protect intellectual property; to increase employee productivity, and to enhance an organization’s competitive advantage. Organizations can confidently deliver on their current goals and innovate to achieve new ones when employees can work securely from everywhere.
The Secure Remote Workforce
A secure remote workforce includes the employees, vendors, and other trusted partners who are not physically located within an organization’s corporate headquarters or branch offices. The secure remote workforce requires secure remote access to an organization’s IT network to maintain productivity while not physically present at a corporate site.
Secure Remote Access Technologies
There are multiple hardware and software technologies that work together to provide secure remote access for an organization’s remote workforce. The technologies an organization chooses depend upon the organization’s size, culture, and the number of onsite employees it maintains compared to the size of its remote workforce. Here, we review commonly used secure remote access technologies.
Secure Access Service Edge (SASE)
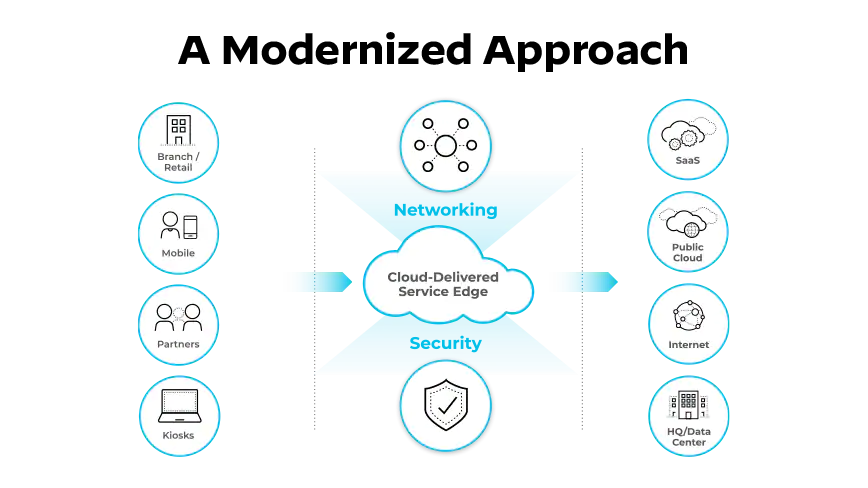
SASE is the convergence of wide area networking (WAN) and network security services—like CASB, SWG, FWaaS, and Zero Trust Network Access (ZTNA)—into a single, cloud-delivered service model.
![]()
The SASE model provides secure remote access to corporate applications, data, and tools to the remote workforce.
The SASE model for secure remote access migrates enterprises away from a perimeter- and hardware-based network security approach to one that provides secure remote access to corporate applications, data, and tools for a dispersed workforce that works from anywhere—their homes, branch offices, or corporate headquarters.
Virtual Private Network (VPN)
The virtual private network, or VPN, provides secure remote access via an encrypted tunnel to connect a user’s computer or device to an organization’s IT network. A VPN makes an internet connection more secure and offers both privacy and anonymity online.
Organizations, governments, and businesses of all sizes use VPNs for secure remote access to data center resources or corporate local area networks (LAN). Personal VPNs have also become widely popular as they keep users’ locations private, safely encrypt data, and allow users to browse the web anonymously.
VPNs can be deployed with client software on an endpoint or through a clientless web browser. With the latter, a user typically navigates to an HTTP/HTTPS portal which establishes an SSL/TLS encrypted connection to a server or an application through the VPN service provider.
Web Proxies
Web proxies are a popular connection method and are often used in conjunction with secure web gateways (SWGs). Proxy servers terminate the connection between the user and the network, and then send a request to the end destination on the user’s behalf. Web proxies can provide an additional level of privacy for the application or the connecting user. Similar to traditional VPNs, web proxy traffic is not typically inspected for threats, adding additional risk for the application and the user. Web proxies only work for web requests and do not provide encryption of all device traffic.
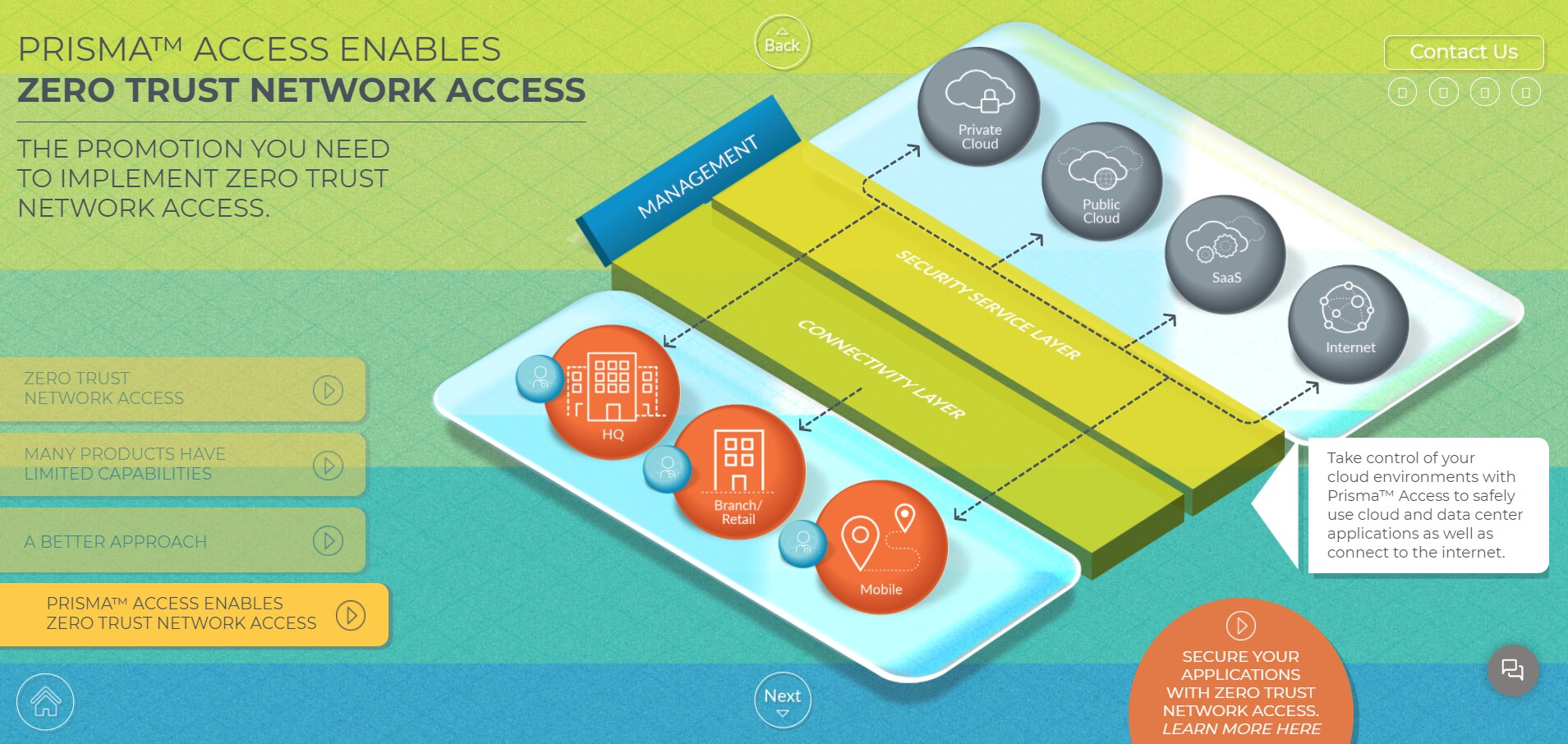
Zero Trust Network Access (ZTNA)
Zero Trust Network Access (ZTNA) technologies provide secure remote access to applications and services based on defined access control policies. By default, secure remote access via ZTNA denies all users network access. Instead, network administrators set up user permissions so they can access only the applications and services that have been identified as necessary for a user to do their job. Once the user has been authenticated to the ZTNA service, the ZTNA service then provisions the user with application- and service-level access through a secure, encrypted tunnel. This encrypted tunnel provides secure remote access by shielding IP addresses that would otherwise be publicly accessible.
Zero Trust Network Access (ZTNA) with Prisma AccessRemote Desktop Access
Remote desktop access is an older and still popular method for accessing resources, typically on a corporate LAN. In this case, a user will connect to a physical or virtual computing instance located on the LAN. Popular examples include Remote Desktop Protocol (RDP) and Virtual Network Computing (VNC).
While remote desktop access can have convenience advantages, this method is not typically recommended as it introduces significant security risks to the corporate network. With much of organizations’ data distributed in third-party SaaS apps, accessing these applications directly is another alternative. Security teams may implement web application firewalls (WAFs), data loss prevention (DLP), or cloud access security broker (CASB) solutions to secure the data in the applications.
Secure Web Gateway (SWG)
A secure web gateway (SWG) protects users from web-based threats and includes the application and enforcement of corporate acceptable use policies. A SWG provides secure remote access by connecting users to a SWG instead of directly to a website. The SWG then connects the user to the desired website and performs functions such as URL filtering, malicious content inspection, web access controls, and other security measures.
Remote Browser Isolation (RBI) solutions complement SWG capabilities to provide additional means of securing user web traffic. RBI solutions isolate web-based browsing content so that the user can see the content they requested, but the content itself is not sent to the endpoint device. This approach enables the expected user experience, but the content itself lives on an isolated server where it cannot threaten network security.
Network Access Control (NAC)
Network Access Control (NAC) is a combination of IT technologies and policies that manage and monitor network access for all devices attempting to access an enterprise network within the corporate perimeter. A NAC allows only authenticated mobile devices that comply with predefined security policies to retrieve proprietary resources available from the corporate network when the user is in the office.
A NAC strategy can help IT professionals view and manage a device’s network access without having issued the device directly to a user who connects the device to the network. Overall, however, NAC is a less effective secure remote access approach than other technologies and strategies.
Single Sign-On (SSO)
Single sign-on (SSO) technologies enable a user to access multiple network applications with a single username and password. Users like this security approach as they only have to remember one username and password to access multiple applications and systems. However, the ease of use benefits inherent with SSO also makes it easier for malicious actors to penetrate an organization’s network. Due to the potential security vulnerabilities posed by SSO, these technologies should be used in conjunction with additional security strategies and technologies to provide secure remote access.
Privileged Access Management (PAM)
Privileged Access Management (PAM) is a combination of technologies and processes that provide users access to various applications, systems, or processes based on their assigned access level, or “privileges,” and are considered a part of an organization’s Identity and Access Management (IAM) strategy. The PAM approach to cybersecurity identifies different roles within an organization and then assigns those roles access to only the tools and applications they need to do their work. For example, a typical office employee may be assigned access to basic office applications and document drives, but they would not have access—or “privileges”—to change information within the organization’s employee directory. This approach is useful for employees who access the organizational network within the corporate perimeter or via secure remote access.
Benefits of Secure Remote Access
With a comprehensive secure remote access strategy, cybersecurity professionals can simply and efficiently do three things: provide secure access from any device; secure web browsing; and develop security awareness across their organization. Secure remote access empowers employees to work securely from everywhere, helping their organizations confidently deliver on current goals and innovate to achieve new ones.
Secure Access from Any Device
With a comprehensive secure remote access strategy and technologies in place, cybersecurity professionals can monitor and manage network connections to their data, from anywhere, and on any device. Regardless of whether network connections are made from personal mobile devices, vendor laptops, or the growing number of internet-enabled items comprising the Internet of Things (IoT), an organization’s cybersecurity team can see everything and ensure all devices are engaging with corporate applications and data safely and securely.
Secure Web Browsing
Most web browsers, like Google Chrome, provide some level of security for a secure web browsing experience. However, a successful secure remote access strategy provides organizations more control of the web browsing experience, eliminating reliance solely on web browser vendors for a secure web browsing experience. With multiple secure remote access technologies in place, cybersecurity professionals can maintain a secure web browsing experience that minimizes network exposure to potential security threats or malicious actors.
Security Awareness Development
Employee security awareness remains an organization’s biggest security challenge. A secure remote access strategy provides organizations the technologies to automate and simplify many day-to-day network security management operations. This support enables cybersecurity professionals to focus their attention on both educating users regarding the latest security threats and monitoring new or evolving vulnerabilities that could threaten organizational users, data, and operations.
Secure Remote Access Solutions
Organizations have multiple secure remote access solutions available for consideration. Network and cybersecurity professionals need to keep in mind their organization’s size, culture, and the number of employees within the corporate perimeter compared to their remote workforce population when developing and deploying an effective secure remote access solution.
Discover how you can provide secure remote access and ensure your employees can work securely from everywhere, now and in the future.