-
What is UEBA (User and Entity Behavior Analytics)?
- How UEBA works
- Benefits of Implementing UEBA
- Examples of UEBA
- Common Use Cases for UEBA
- Challenges and Considerations in UEBA Deployment
- Diverse Threats Addressed by UEBA
- Integrating UEBA and XDR
- UEBA vs NTA
- UEBA vs SIEM
- UEBA vs IAM
- Future Trends and Developments in UEBA
- Choosing the Right UEBA Solution
- UEBA FAQs
-
What Is Threat Prevention? [Definition, Explanation, + How-tos]
- Why is threat prevention important?
- How does threat prevention work?
- What are the differences between threat prevention, detection, and protection?
- What are the different types of threat prevention?
- Top 5 threat prevention tips, tricks, and best practices
- Why threat prevention is harder than it sounds (yet more achievable than it used to be)
- Threat prevention FAQs
- What Is Penetration Testing?
- 3 Challenges to Identifying Evasive Threats
What is a Port Scan?
A port scanner is an application which is made to probe a host or server to identify open ports. Bad actors can use port scanners to exploit vulnerabilities by finding network services running on a host. They can also be used by security analysts to confirm network security policies.
How a Port Scan Works
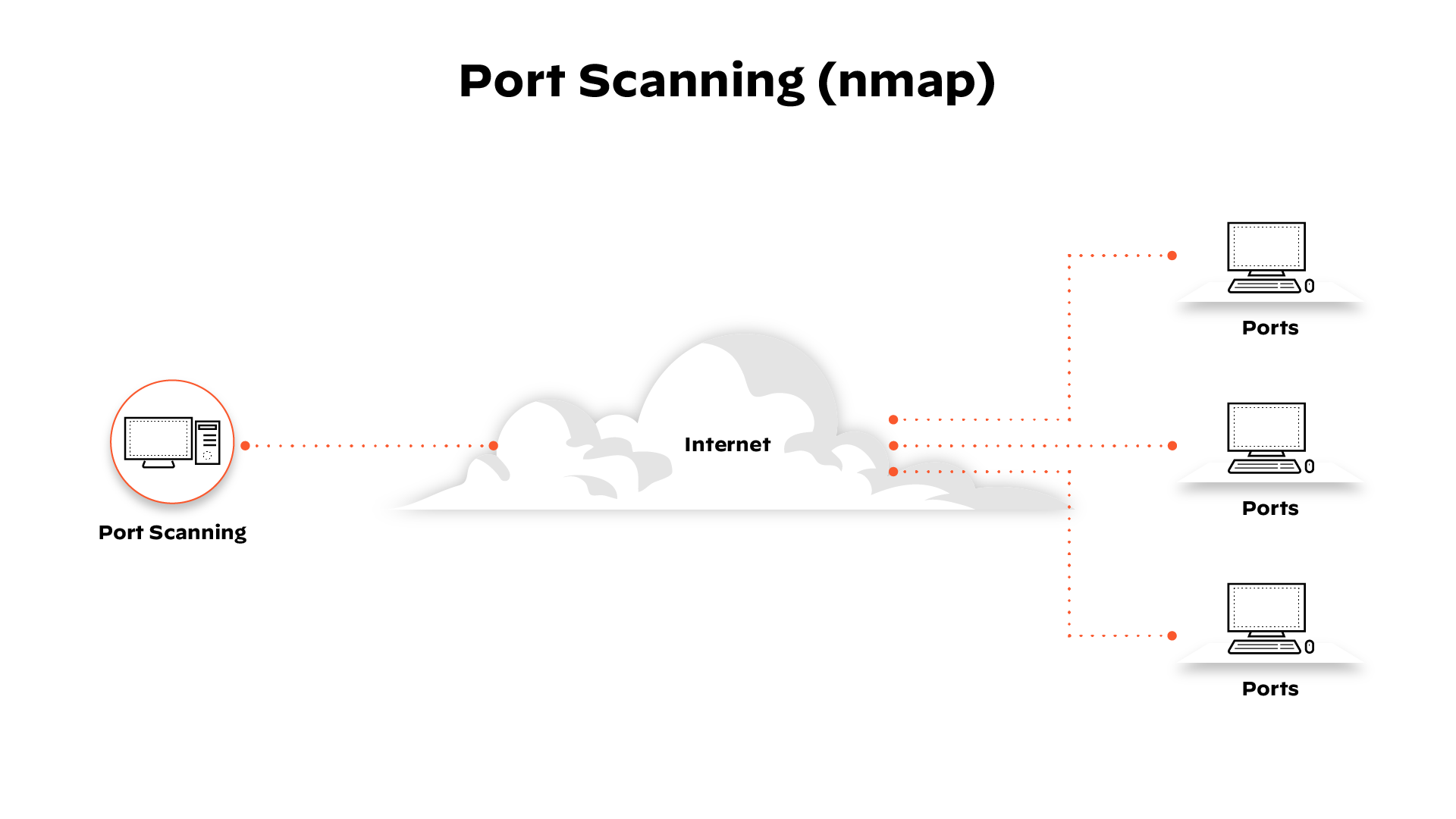
Running a port scan on a network or server reveals which ports are open and listening (receiving information) as well as revealing the presence of security devices, such as firewalls, that are present between the sender and the target. This technique is known as fingerprinting.
It is also valuable for testing network security and the strength of the system’s firewall. Due to this functionality, it is also a popular reconnaissance tool for attackers seeking a weak point of access to break into a computer.
Ports vary in their services offered. They are numbered from 0 to 65535, but certain ranges are more frequently used. Ports 0 to 1023 are identified as the “well-known ports” or standard ports and have been assigned services by the Internet Assigned Numbers Authority (IANA). Some of the most prominent ports and their assigned services include:
- Port 20 (UDP) — File Transfer Protocol (FTP) for data transfer
- Port 22 (TCP) — Secure Shell (SSH) protocol for secure logins, FTP, and port forwarding
- Port 23 (TCP) — Telnet protocol for unencrypted text commutations
- Port 53 (UDP) — Domain Name System (DNS) translates names of all computers on internet-to-IP addresses
- Port 80 (TCP) — World Wide Web HTTP
There are standard services offered on ports after 1023 as well and ports that, if open, indicate an infected system due to its popularity with some far-reaching Trojans and viruses.
Types of Port Scans
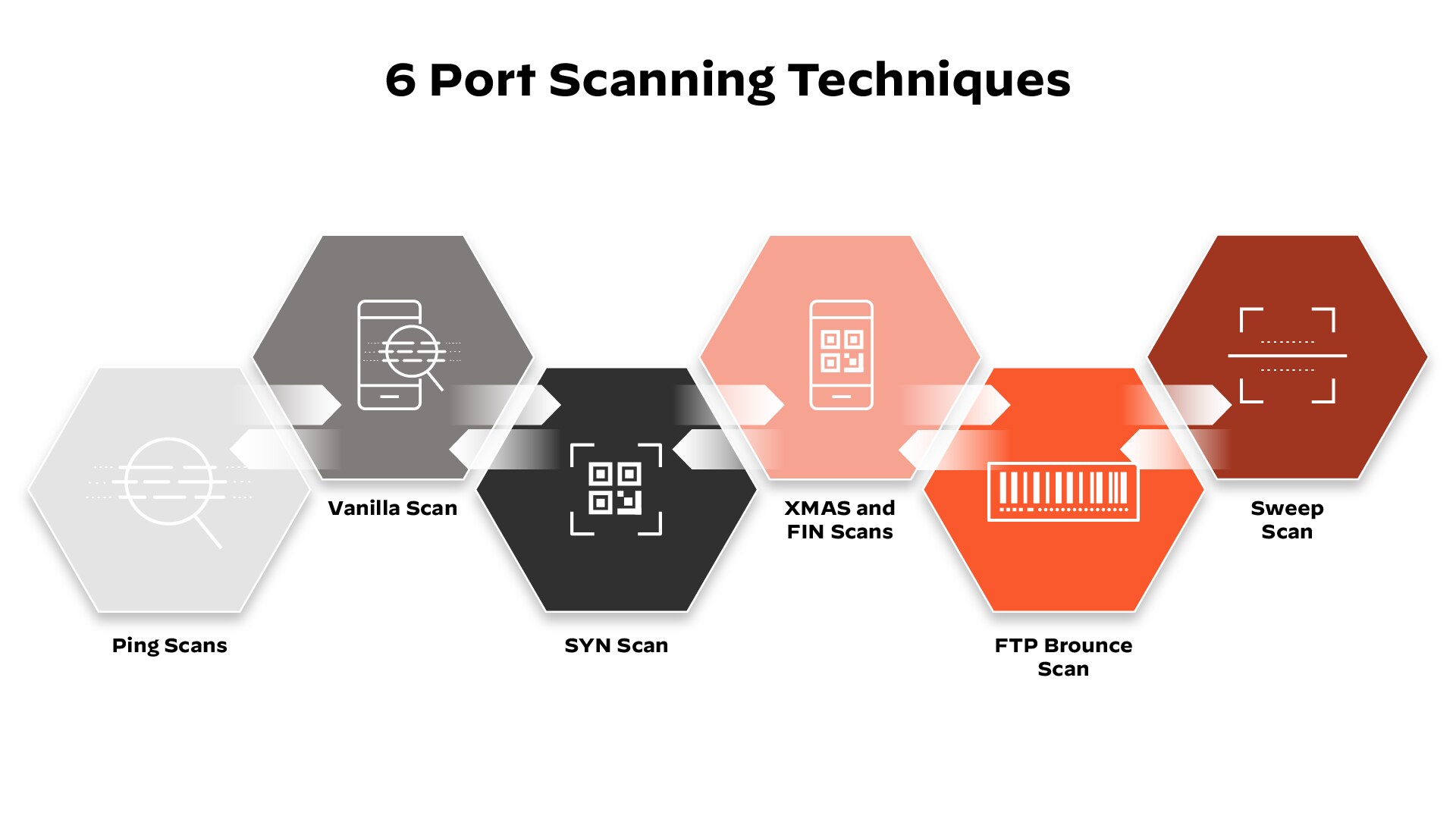
A port scan sends a carefully prepared packet to each destination port number. The basic techniques that port scanning software is capable of include:
- Vanilla — the most basic scan; an attempt to connect to all 65,536 ports one at a time. A vanilla scan is a full connect scan, meaning it sends a SYN flag (request to connect) and upon receiving a SYN-ACK (acknowledgement of connection) response, sends back an ACK flag. This SYN, SYN-ACK, ACK exchange comprises a TCP handshake. Full connect scans are accurate but very easily detected because full connections are always logged by firewalls.
- SYN Scan — also referred to as a half-open scan, it only sends a SYN, and waits for a SYN-ACK response from the target. If a response is received, the scanner never responds. Since the TCP connection was not completed, the system doesn’t log the interaction, but the sender has learned if the port is open or not.
- Xmas and FIN Scans — an example of a suite of scans used to gather information without being logged by the target system. In a FIN scan, an unsolicited FIN flag (used normally to end an established session) will be sent to a port. The system’s response to this random flag can reveal the state of the port or insight about the firewall. For example, a closed port that receives an unsolicited FIN packet, will respond with an RST (an instantaneous abort) packet, but an open port will ignore it. An Xmas scan simply sends a set of all the flags, creating a nonsensical interaction. The system’s response can be interpreted to better understand the system’s ports and firewall.
- FTP Bounce Scan — allows for the sender’s location to be disguised by bouncing the packet through an FTP server. This is also designed for the sender to go undetected.
- Sweep scan — pings the same port across a number of computers to identify which computers on the network are active. This does not reveal information about the port’s state, instead it tells the sender which systems on a network are active. Thus, it can be used as a preliminary scan.
Port Scanning Results
A port scanner sends a UDP or TCP network packet that asks the port about its status. The results will uncover network or server status, which can be one of the following: open, closed and filtered.
1. Open — Accepted
An open port indicates the following:
- The target network/service is accepting datagrams/connections.
- The target network/service has responded with a TCP SYN packet to indicate that it’s listening
- The service utilized for the port scan is in use (usually UDP or TCP).
For bad actors, locating open ports is the mission. This creates a challenge for security personnel faced with the task of blocking open ports with firewalls (while avoiding cutting off access for authorized users).
2. Closed — Not Listening
A closed port indicates the following:
- The target network/server has received the request, but no service is listening
Although the port is closed, it can still be accessed, and therefore useful in confirming that a host is present on an IP address. Security personnel should continuously monitor closed ports and consider barricading them with firewalls (making them filtered ports).
3. Filtered — Dropped/Blocked
A filtered port indicates the following:
- A request packet was sent. The host is not listening and does not respond.
- The request packet was likely blocked by a firewall or an intrusion prevention system.
As long as packets do not reach the target, bad actors will have no way to uncover further insights. Typically, packets sent to filtered ports will not receive a response, but when they do, the error message is usually “communication prohibited” or “destination unreachable.”
How Bad Actors Use Port Scanning as an Attack Method
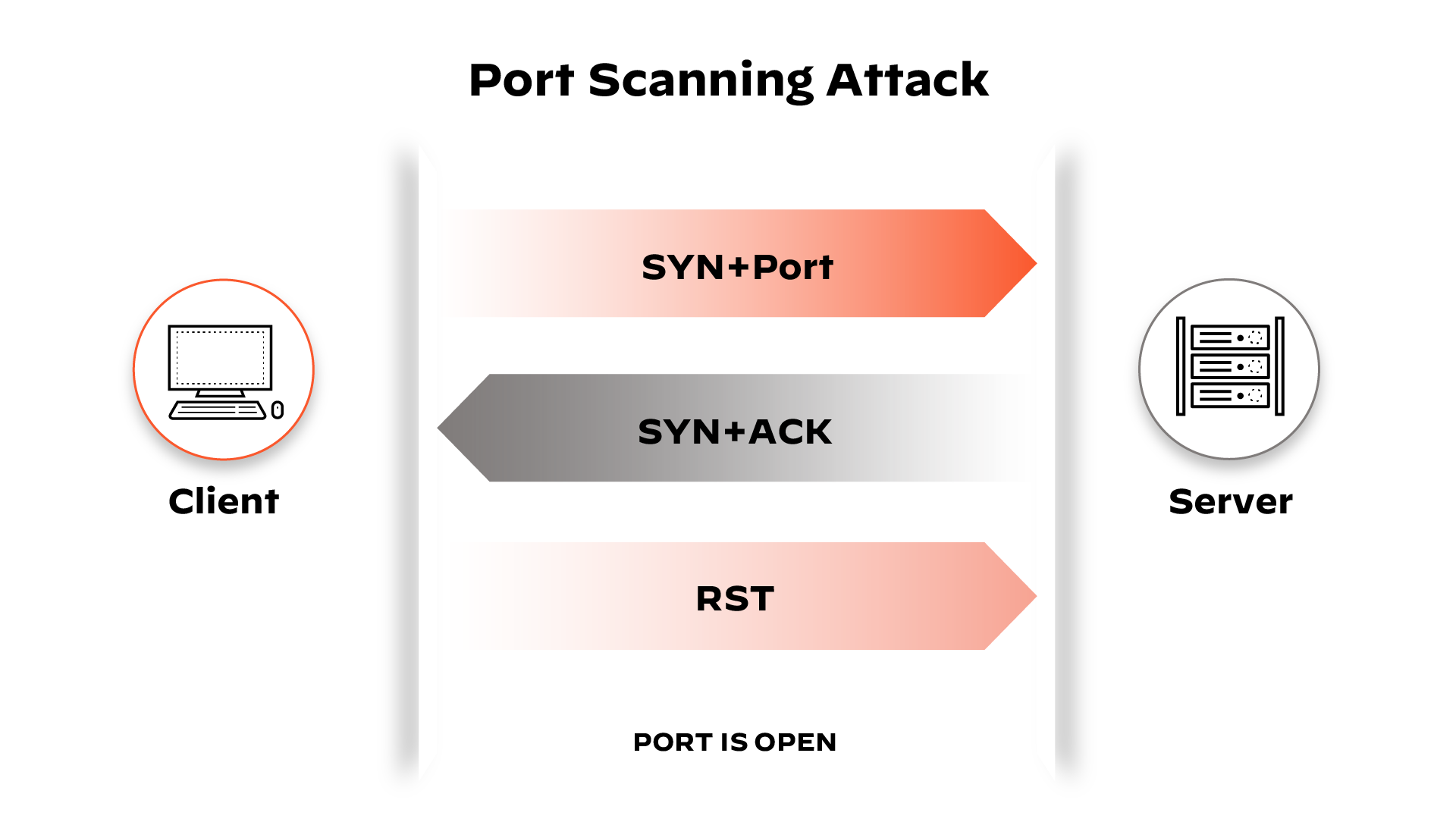
Port scanning is one of the most popular tactics bad actors use when in search of a vulnerable server, according to the SANS Institute. When targeting networks, port scanning is typically the first step. The port scan delivers useful information about the network environment, such as:
- Defenses that are present, such as firewalls
- Details about the targeted system
- Machines that are online
- Applications that are running
- Who might have a vulnerable network or server
This type of information is highly valuable to malicious actors who are looking for vulnerabilities in software. Being able to identify that an organization is running a specific DNS or web server makes finding those vulnerabilities much easier. There are several TCP protocol techniques that allow bad actors to use decoy traffic for port scans, hiding their network address and location entirely.
Scans that are developed for the sender to go undetected by a receiving system’s log are known as stealth scans and are of particular interest to attackers. Despite its popularity in this area, port scanning is a valuable tool for fingerprinting a network and for a penetration tester to assess the strength of network security.
Port Scan FAQs
There are several methods for conducting port scans:
- SYN Scan (Half-Open Scan): Involves sending a SYN packet and waiting for a SYN-ACK response without completing the TCP handshake, making it harder to detect.
- FIN Scan: Technique sends a FIN packet to closed ports, which triggers a reset (RST) response. It is commonly used to bypass firewall detection.
- XMAS Scan: Transmits a packet with all flags set, resembling a "lit-up" Christmas tree, and helps identify the firewall presence and the state of the ports.
- UDP Scan: Determines which UDP ports are open by sending UDP packets and waiting for a response, as this protocol does not require a handshake.
Port scanning often serves as a prelude to various types of cyberattacks. For instance, it can be utilized to:
- Detect open ports that may be exploited for unauthorized entry.
- Act as an initial step for launching more specific attacks, such as Denial of Service (DoS) or data breaches.
- Supply attackers with critical information needed to inject malware or execute malicious code by exposing network vulnerabilities.