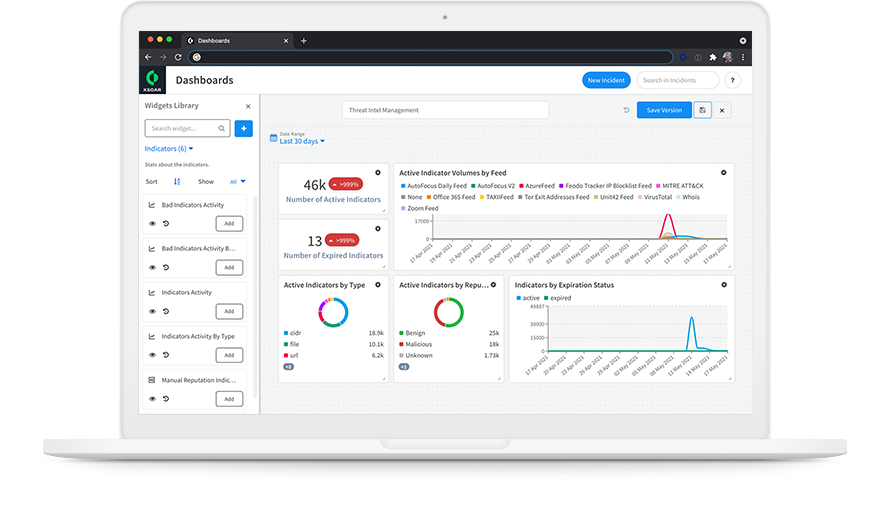
Centralize and manage all threat intelligence
Leverage a global threat landscape with native access to the massive Palo Alto Networks threat intelligence repository from Unit42.
Proactive defense against attacks
Rich threat intelligence findings by Unit 42 threat researchers are automatically embedded in an analyst’s existing tools for instant, unrivaled context and understanding of every event and threat.
Centralized threat intelligence library
Better model your threat landscape with threat data from hundreds of sources automatically aggregated into a single, cohesive set. Discover new sources of threat intelligence from the hundreds of threat feed integrations within our Cortex Marketplace.