What Is a Circuit Level Gateway? [+ How It Works & Examples]
A circuit level gateway is a firewall that monitors and validates network sessions at the session layer of the OSI model.
It establishes two separate TCP or UDP connections—one with the internal host and one with the external host—and relays packets only for approved sessions. It does not inspect packet contents but ensures that each connection follows the required handshake and security rules before data transfer occurs.
How does a circuit level gateway work?
A circuit level gateway works at Layer 5, the session layer of the OSI model.
Its job is to make sure that a network session is legitimate before data starts flowing. In other words, it validates the connection itself, not the information being exchanged.
A circuit level gateway can manage both TCP and UDP sessions, verifying that each connection follows the correct handshake or session initiation process.
Here's how it happens.
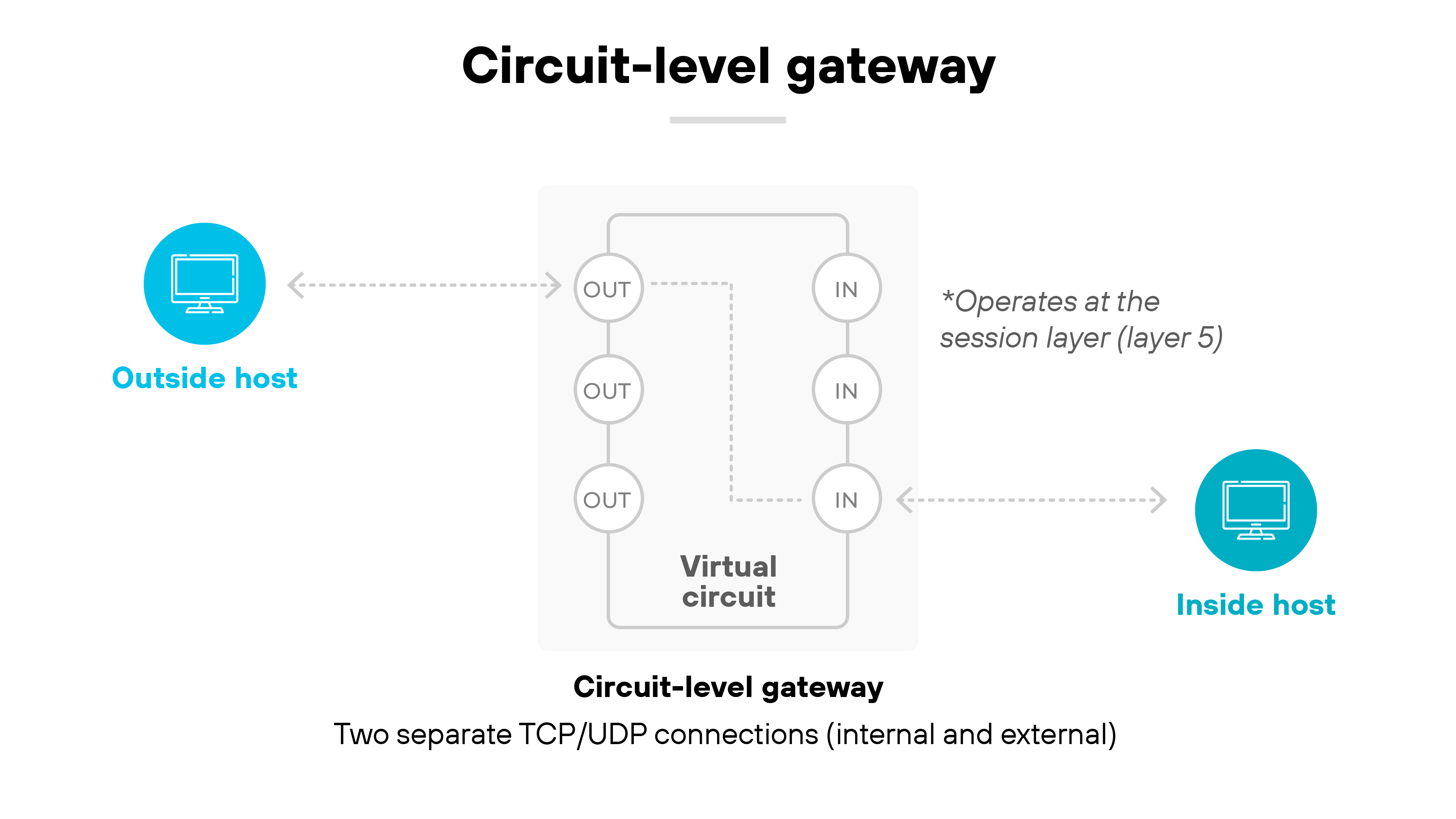
When a user on an internal network tries to connect to an external host, the gateway steps in. It doesn't allow a direct link. Instead, it creates two separate TCP connections: one between the internal system and the gateway, and another between the gateway and the external host.
Why?
Because this setup gives the gateway control over both sides of the conversation. It acts as a middle point that mirrors the TCP handshake on each side. Once both handshakes succeed, the gateway considers the session trusted.
At that point, it creates what's called a virtual circuit.
This is a temporary, logical connection used to move data between the two hosts through the gateway. The gateway keeps a table of active sessions with details like source and destination IP addresses, port numbers, and session state.
Which means:
It knows which sessions are open, which have ended, and which are legitimate.
Once a session is approved, traffic moves through transparently. The gateway doesn't look inside the packets or analyze content. It simply forwards data as long as the session remains valid.
And that's the limitation. Circuit-level gateways enforce handshake legitimacy but can't detect malicious payloads or application-level attacks hidden within the session.
How did circuit level gateways shape the evolution of firewalls?
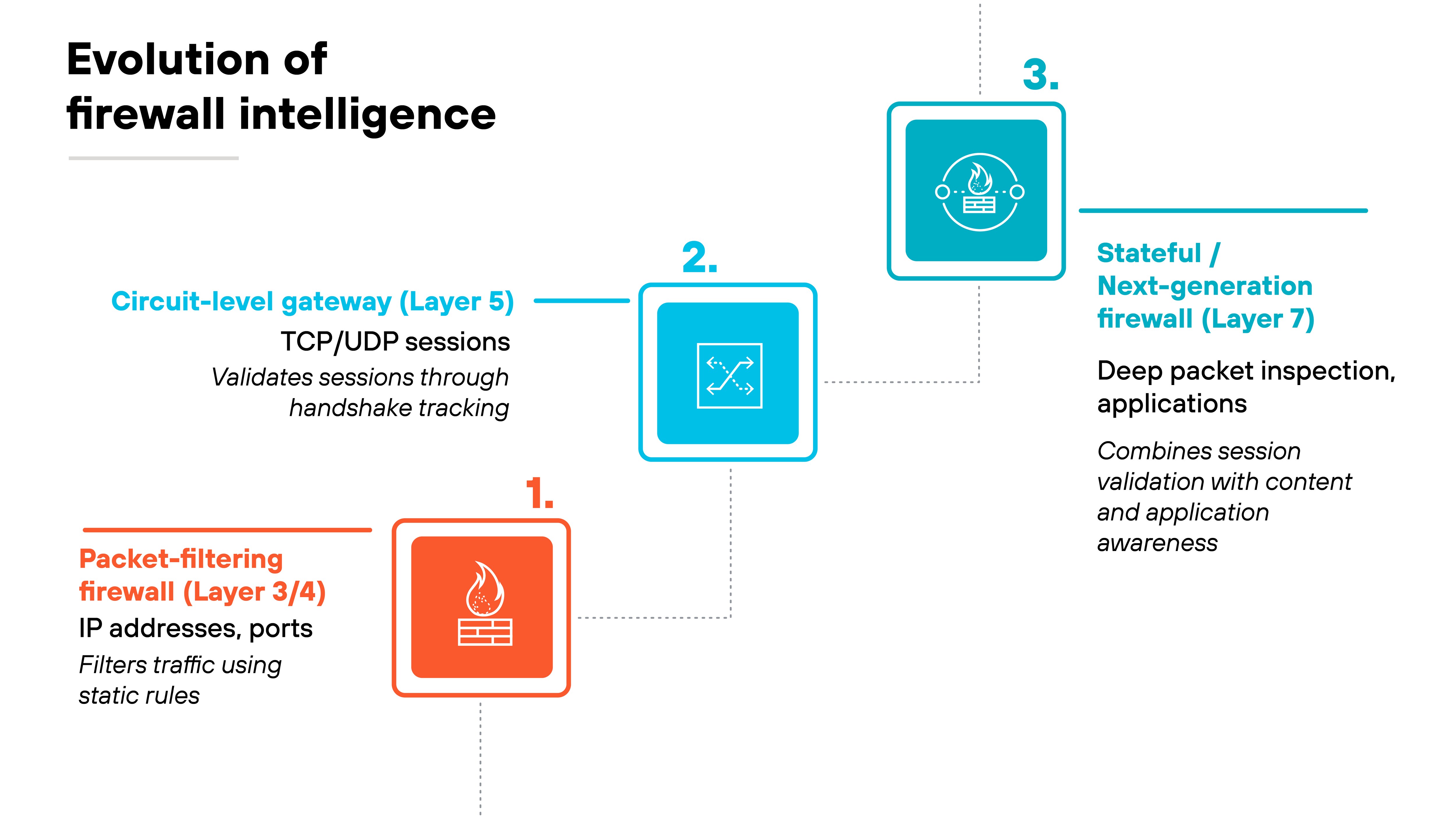
Circuit level gateways marked the first real step “up the stack” in firewall design.
Before them, firewalls worked only at the network and transport layers, filtering packets based on IP addresses and ports.
Circuit-level gateways changed that. This type of firewall added awareness of the session layer, which meant they could understand when a connection—TCP or UDP—was being established, maintained, or closed.
Here's why that mattered.
By tracking handshakes and session state, these gateways introduced the idea that network traffic could be validated at a higher level than packet headers alone. So it was the first time firewalls could make decisions based on connection behavior rather than just static rules.
That concept directly influenced stateful inspection.
Stateful firewalls built on the same logic—recording session details—but expanded it to include packet context and limited application awareness.
Next-generation firewalls took that even further by adding deep packet inspection and integrating multiple network security functions into one platform.
Essentially:
Circuit-level gateways were the bridge between simple packet filters and the intelligent, multi-layer firewalls used today. They proved that tracking session state was possible—and essential—for securing modern networks.
- The History of Firewalls | Who Invented the Firewall?
- What Is a Stateful Firewall? | Stateful Inspection Firewalls Explained
- What Is a Next-Generation Firewall (NGFW)? A Complete Guide
What are the strengths and limitations of circuit level gateways?
Circuit-level gateways offered a balance between performance and basic security.
They worked efficiently at the session layer, handling fewer data details than deeper inspection firewalls. Because of that, they introduced almost no noticeable latency.
Another advantage was anonymity.
Internal host addresses were never exposed to external systems because the gateway relayed sessions on their behalf. This made internal networks harder to profile.
They were also simple to configure and maintain, since they relied on predefined rules for session validation rather than complex traffic policies.
However: that simplicity came at a cost.
| Strengths and limitations of circuit-level gateways |
|---|
| Strengths | Limitations |
|---|---|
| High performance with minimal latency due to limited data inspection. | Cannot inspect payloads or detect application-level threats. |
| Hides internal network details by relaying sessions on behalf of hosts. | Blind to malicious content or commands within legitimate sessions. |
| Simple to configure and maintain using predefined session rules. | Offers limited policy control and coarse-grained traffic filtering. |
| Efficient for validating TCP and UDP session integrity. | Lacks visibility into applications and user-level activity. |
Circuit-level gateways could not inspect the data payload inside packets. They were blind to application-level threats, malicious commands, or data exfiltration hidden in legitimate sessions.
Plus, their policies were coarse-grained and offered minimal control over specific applications or behaviors.
In short: the trade-offs that made them efficient also made them limited. And that helped pave the way for more advanced, content-aware firewall architectures.
Where circuit level gateways persist today
Circuit-level gateways are no longer used as standalone devices, but their underlying logic remains active in modern systems.
The same session-based validation model still shapes how many security tools manage traffic today. So the idea survived even as the original technology faded.
For example, the SOCKS proxy protocol operates almost identically to a circuit level gateway. It sets up two TCP connections and relays packets only for approved sessions.
The same principle also appears in tunneling protocols that use virtual circuits to securely pass data between networks or services.
Modern firewalls and cloud security platforms still rely on this model.
In next-generation firewalls, session validation tracks active connections before deeper inspection begins. In cloud and container environments, sidecar proxies in microservice architectures use similar session-based logic to control service-to-service communication.
Even threat actors use it. Attackers often deploy SOCKS tunnels to hide command-and-control traffic within trusted connections.
Ultimately, circuit level logic persists everywhere. It's simply evolved from a product into a core function of secure network design.