Cloud Incident Response (IR) Explained
The Palo Alto Networks Unit 42 Global Incident Response Report revealed that nearly one-third (29%) of the cases that Unit 42 responded to were cloud-related, highlighting the growing need for specialized cloud incident response capabilities.
Cloud incident response expands upon traditional incident management principles, specifically addressing the complexities of cloud environments. It involves a strategic approach to detecting and recovering from cyber attacks or security events affecting cloud-based infrastructure, applications, and data.
The importance of cloud incident response stems from the dynamic, distributed, and API-driven nature of cloud platforms, which introduces distinct challenges compared to on-premises systems. Effective incident response in the cloud requires specialized knowledge of cloud service provider (CSP) architectures, the shared responsibility model, and cloud-native security controls.
Incident response is part of the "Detect" and "Respond" stages in the Cloud Security Lifecycle. These stages align with cloud security frameworks, such as the NIST Cybersecurity Framework or CIS Controls, which outline a comprehensive approach to securing cloud environments.
Security teams must adapt their processes to account for ephemeral resources, limited physical access, and the rapid pace of change in cloud environments. A well-prepared cloud incident response capability is vital for maintaining business continuity and protecting sensitive information in the face of evolving cyber threats.
Why Cloud IR Differs from Traditional IR
Cloud environments introduce unique complexities for incident response that necessitate a distinct approach from traditional on-premises methods. Understanding these differences is fundamental for effective incident management in the cloud.
Shared Responsibility Model
The shared responsibility model defines the security obligations between the cloud service provider and the customer. The CSP is responsible for the security of the cloud (the underlying infrastructure), while the customer is responsible for security in the cloud, encompassing data, applications, and configurations. This division means incident responders must clearly understand which party is responsible for specific aspects during an incident.
Dynamic and Ephemoral Infrastructure
Cloud environments feature highly dynamic and ephemeral infrastructure, unlike static on-premises systems. Resources like virtual machines, containers, and serverless functions can scale up, down, or disappear rapidly. This dynamism complicates digital forensics and investigation, as evidence may be short-lived or distributed across many temporary instances.
Limited Physical Access
In cloud environments, customers do not have physical access to the underlying hardware or data centers. This absence of physical control means traditional forensic methods, such as imaging physical disks, are not applicable. Incident responders must rely on cloud provider APIs, logging services, and virtualized tools for investigation and data collection.
API-Driven Control Plane
Cloud services are primarily managed through APIs, which form the control plane for all cloud operations. Many cloud incidents involve the compromise of API keys or unauthorized access to the management plane. Incident responders must understand how to monitor and secure these APIs, as well as how to revoke compromised credentials swiftly.
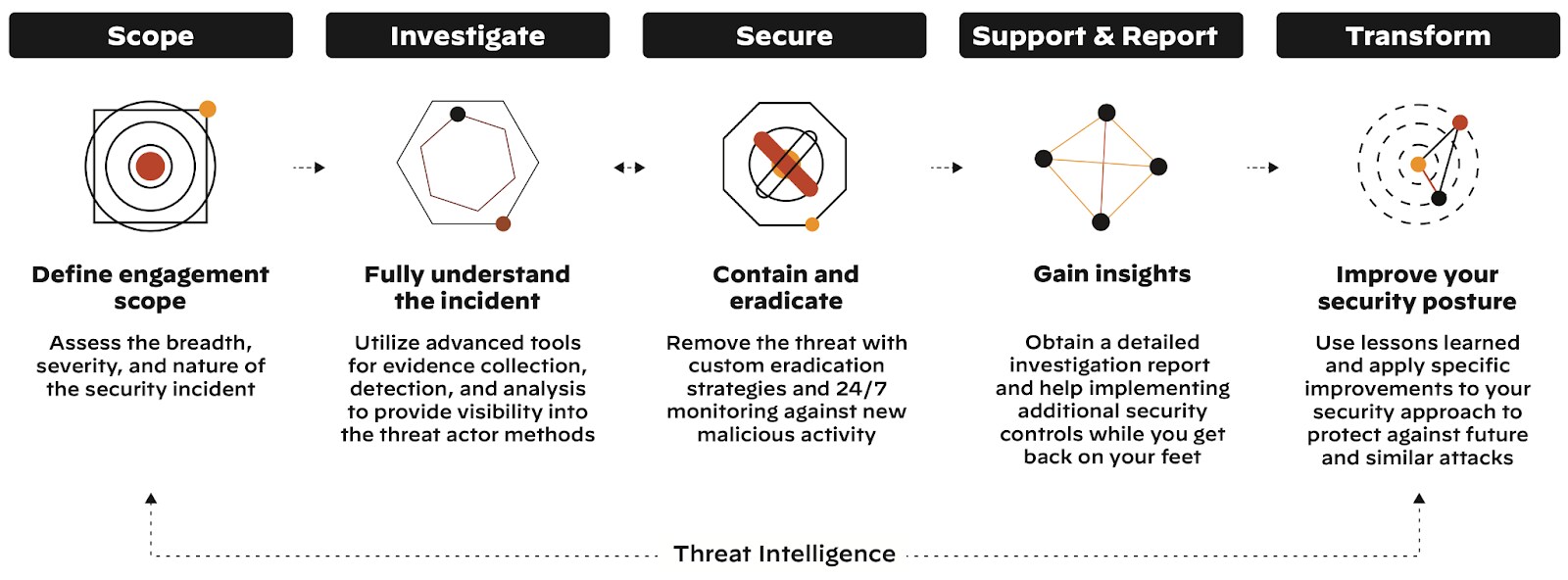
![Incident Response Process Phases Incident response process diagram showing five connected phases: Scope, Investigate, Secure, Support & Report, and Transform, with corresponding icons and detailed descriptions for each phase. Threat Intelligence is shown as an underlying foundation supporting all phases]()
Figure 1: Incident Response Process Phases
The Cloud Incident Response Lifecycle
Effective cloud incident response follows a structured process, adapting established incident handling phases to the unique characteristics of cloud computing. This lifecycle ensures a systematic approach to managing security incidents from preparation through post-incident analysis.
Preparation
This phase involves establishing the necessary foundations before an incident occurs. It includes:
- Developing a Plan: A tailored Cloud IR plan outlines procedures, roles, and responsibilities for handling cloud incidents.
- Building a Team: An effective team requires members with specialized knowledge of cloud platforms, architectures, and security services.
- Implementing Controls: Deploying cloud-native security controls like cloud security posture management (CSPM) and cloud workload protection platforms (CWPP) to prevent and detect incidents.
- Establishing Logging: Comprehensive logging and monitoring are essential for visibility. Services like AWS CloudTrail, Azure Activity Logs, and Google Cloud Audit Logs provide critical audit trails of API activity. Integrating these logs with a centralized security information and event management (SIEM) system or cloud-native threat detection services enhances threat detection capabilities.
Identification
The identification phase focuses on detecting security events and determining if they constitute a cloud incident. Early and accurate identification minimizes potential damage.
Threat Detection in Cloud Environments
Threat detection involves continuously monitoring cloud resources for suspicious activities or indicators of compromise. This includes analyzing logs for anomalous API calls, unauthorized access attempts, or unusual network traffic patterns. Cloud-native threat detection services can automatically identify many common cloud threats.
Alerting Mechanisms for Security Events
Configuring effective alerting mechanisms ensures that security teams are promptly notified of potential incidents. Alerts should be prioritized based on severity and potential impact. Integration with existing security operations center (SOC) workflows is important for timely response.
Initial Triage and Assessment of Cloud Incidents
Once an alert is received, initial triage involves quickly assessing the nature and scope of the potential incident. This includes verifying the alert, determining affected cloud resources, and estimating the potential impact. Rapid assessment helps decide whether to escalate to a full incident response.
Containment
The speed of cloud attacks is a major concern. According to the Unit 42 Global Incident Response Report, in almost one in five cases, data exfiltration occurred in less than an hour. Organizations need to leverage automation to contain threats at machine speed before they can escalate. Containment aims to limit the scope and impact of an ongoing cloud incident. This phase requires swift action to prevent further damage or unauthorized access.
Isolating Affected Cloud Resources
Incident responders must quickly isolate compromised cloud resources, such as virtual machines, containers, or storage buckets. This might involve changing network security group rules, detaching compromised instances from the network, or suspending user accounts. The goal is to prevent the attacker from moving laterally or exfiltrating more data.
Preventing Further Spread of the Incident
Beyond isolation, containment strategies focus on preventing the incident from spreading to other cloud resources or connected systems. This could involve blocking malicious IP addresses, disabling compromised credentials, or segmenting networks. Rapid response is critical due to the interconnected nature of cloud environments.
Leveraging Cloud-Native Capabilities for Rapid Containment
Cloud providers offer various native capabilities that can be leveraged for rapid containment. These include automated remediation actions triggered by security alerts, policy-based enforcement, and the ability to quickly provision or de-provision resources. Automation significantly accelerates containment efforts.
Eradication
Eradication focuses on removing the threat from the cloud environment and eliminating its root cause. This phase ensures the attacker no longer has access or persistence.
Removing the Threat from the Cloud Environment
This involves deleting malicious files, removing backdoors, and revoking any unauthorized access. For cloud incidents, this often means deleting compromised instances, containers, or serverless functions and deploying clean versions. It also includes removing any persistent access mechanisms established by the attacker.
Patching Vulnerabilities, Correcting Misconfigurations
Identifying and remediating the underlying vulnerability or misconfiguration that allowed the incident to occur is crucial. This might involve applying security patches, updating insecure configurations, or strengthening IAM policies. Addressing the root cause prevents recurrence.
Restoring Affected Systems
After the threat is eradicated, affected systems and data must be restored to a secure, pre-incident state. This often involves deploying from trusted backups or golden images. Verification steps ensure that no malicious artifacts remain and systems are functioning correctly.
Recovery
The recovery phase focuses on restoring normal operations and ensuring the long-term integrity and security of cloud systems. This involves bringing affected services back online in a controlled manner.
Restoring Operations to Normal
This step involves systematically bringing affected cloud services and applications back online. A phased approach is often used to minimize disruption and allow for continuous monitoring. Prioritization of critical services ensures business continuity.
Validating System Integrity
Thorough validation ensures that all restored systems are clean, secure, and functioning as expected. This includes security scans, integrity checks, and performance monitoring. Verification helps confirm that the eradication efforts were successful and no new vulnerabilities were introduced.
Ensuring Business Continuity
The ultimate goal of recovery is to ensure that business operations can resume with minimal interruption. This involves coordinating with business units and stakeholders to manage expectations and communicate progress. A successful recovery minimizes financial and reputational damage.
Post-Incident Activity (Lessons Learned)
The final phase involves a comprehensive review of the incident to learn from the experience and improve future incident response capabilities. This continuous improvement loop is vital for enhancing cloud security posture.
Analyzing the Incident (Post-Mortem)
A detailed post-mortem analysis examines what happened, how it happened, and why. This includes reviewing logs, timelines, and response actions. Identifying the root cause and contributing factors is paramount.
Identifying Root Causes and Areas for Improvement
This step focuses on pinpointing specific vulnerabilities, misconfigurations, or process gaps that led to the incident. Insights gained inform improvements to security controls, policies, and procedures. For example, a recent analysis of cloud breaches showed that over 60% were linked to cloud misconfigurations, highlighting the need for continuous posture management.
Updating Plans and Security Controls
Based on lessons learned, the cloud incident response plan, security policies, and technical controls are updated. This might involve refining detection rules, enhancing automation, or providing additional training to the incident response team. This iterative process strengthens overall cloud security.
![Cortex Detection Engine Cortex Detection Engine]()
Figure 2: Cortex Detection Engine
Cloud Detection and Response (CDR): The Next Evolution
Cloud Detection and Response (CDR) is a specialized security solution built for the cloud. It focuses on detecting threats, investigating incidents, and responding quickly by continuously monitoring cloud environments for suspicious activity like malware and privilege escalation. CDR provides real-time visibility and protection for everything in the cloud—from workloads and data to user identities and control plane activities.
CDR is a necessary evolution because older tools like Endpoint Detection and Response (EDR) and Network Detection and Response (NDR) were not designed for the dynamic, distributed nature of the cloud. CDR uses the cloud's own services and APIs to automatically and efficiently detect threats at scale.
An effective CDR solution monitors and protects across multi-cloud environments in real time. It uses behavioral threat detection and intelligence to find complex attack paths and can correlate threat signals from various cloud sources.
By triggering automated responses, CDR helps reduce the time it takes to detect and respond to threats, making it a critical component of any cloud security strategy. It also integrates with other security platforms, like CNAPP and SIEM, to provide a centralized defense, reduce tool sprawl, and speed up incident response.
SOC IR vs. Cloud IR
Security Operations Center (SOC) Incident Response and Cloud Incident Response share the same goal: to detect, analyze, contain, and mitigate security incidents. However, they differ significantly in their focus and operational challenges.
- SOC IR: A broad, centralized function that oversees the entire IT infrastructure, including on-premises systems, networks, and endpoints. The SOC team uses a wide array of tools to gain a unified view and coordinate responses.
- Cloud IR: A specialized discipline that focuses exclusively on cloud environments. Cloud IR requires specific expertise in cloud-native tools (e.g., AWS CloudTrail, Azure Monitor) and an understanding of dynamic configurations like IAM roles and virtual private clouds (VPCs). It is a vital component of a modern SOC's broader responsibilities.
Best Practices for Cloud Incident Response
Adopting strategic practices significantly enhances an organization's cloud incident response capabilities. These best practices focus on proactive measures, automation, and continuous improvement.
- Develop a Cloud-Specific Plan: Create a tailored incident response plan (IRP) that defines roles, responsibilities, and communication protocols for cloud incidents, accounting for the shared responsibility model.
- Embrace Automation: Automate threat detection, alert triage, and initial containment actions to reduce response times.
- Prioritize CSPM: Continuously monitor cloud environments for misconfigurations, compliance violations, and security risks. Of all incidents that Unit 42 responded to, 41% contained at least one contributing factor that was related to IAM issues, such as overly permissive accounts and roles, highlighting the need for continuous posture management.
- Enhance Cloud Visibility: Centralize logs from all cloud services into a unified platform to gain comprehensive visibility for detection and investigation.
- Regularly Test and Drill: Conduct tabletop exercises and simulated incidents to validate your plan and identify gaps.
- Invest in Training and Expertise: Continuously develop cloud security skills within your incident response team through training and certifications.
Cloud Incident Response Frameworks and Standards
Leveraging established frameworks provides a structured and systematic approach to cloud incident response. These frameworks offer guidance on developing, implementing, and improving incident handling capabilities in cloud environments.
Cloud Incident Response Frameworks and Standards
Leveraging established frameworks provides a structured and systematic approach to Cloud IR.
- NIST SP 800-61 R2: Provides a widely recognized guide for incident handling, and its core phases are adaptable to cloud environments.
- CSA Cloud Incident Response Framework: Addresses the unique challenges of cloud computing, such as the shared responsibility model and the dynamic nature of cloud resources.
- ISO/IEC 27035: A broader standard for information security incident management that is applicable across various IT environments, including the cloud.
The Role of Cloud-Native Security Tools
Cloud-native security tools are essential for effective incident response in the cloud, providing capabilities specifically designed for dynamic cloud environments. These tools offer deep integration with cloud platforms, enhancing visibility, detection, and automated response.
- Cloud Security Posture Management (CSPM): Continuously assesses cloud configurations against security best practices and compliance standards to prevent incidents.
- Cloud Workload Protection Platforms (CWPP): Provides security for workloads like virtual machines and containers, offering runtime protection and micro-segmentation.
- Cloud-Native Logging and Monitoring: Services like CloudTrail and Azure Monitor are indispensable for capturing API calls and activity for forensic analysis.
- Identity and Access Management (IAM): Comprehensive IAM controls are fundamental for managing user permissions and detecting anomalous access patterns.
Future Trends in Cloud Incident Response
The landscape of Cloud IR continues to evolve rapidly, driven by technology and changes in cloud adoption.
- AI and Machine Learning: These technologies will improve threat detection by identifying subtle anomalies in vast amounts of data.
- Serverless and Container Security: The adoption of these technologies introduces new challenges, requiring specialized security tools for ephemeral environments.
- Zero Trust Principles: The Zero Trust model will become increasingly relevant, continuously verifying every user and device to minimize the impact of compromised credentials.
- Supply Chain Security: As organizations rely on third-party cloud services, supply chain security will become a critical concern for incident response.
Key Challenges in Cloud Incident Response
Cloud environments present specific hurdles for incident responders, requiring specialized strategies and tools. Addressing these challenges is crucial for building an effective cloud incident response program.
Visibility and Data Collection
Gaining visibility is challenging because cloud environments are distributed and logs are spread across multiple services. The ephemeral nature of cloud resources means that evidence can disappear quickly, and traditional digital forensics techniques (like imaging a physical disk) don't apply.
Skills Gaps
Many security professionals lack deep expertise in cloud security. Incident response teams may be proficient in on-premises environments but require specialized training to understand cloud-native services, architectures, and the nuances of the shared responsibility model.
Speed and Scale
The rapid pace of change and the massive scale of cloud environments can overwhelm manual processes. Attackers often use automation to launch attacks quickly, necessitating an equally automated and rapid response from defenders.
Multi-Cloud Complexity
Organizations using multiple cloud providers face additional challenges due to inconsistent tools, policies, and APIs across different platforms, which complicates managing a unified response.
Misconfigurations
Cloud misconfigurations are a leading cause of security incidents, often exposing sensitive data or creating vulnerabilities. In fact, in 41% of incidents, at least one contributing factor was related to IAM issues, such as overly permissive accounts and roles. Proactive, continuous monitoring is crucial to address this.
Need for Continuous Configuration Monitoring
Continuous Cloud Security Posture Management (CSPM) is essential to detect and remediate misconfigurations in real time. Automated tools can scan cloud environments for deviations from security best practices and compliance standards. This proactive approach significantly reduces the attack surface.
Solutions to Overcome Cloud IR Barriers
Overcoming the unique challenges of the cloud requires a strategic blend of proactive planning, specialized tools, and a shift in operational mindset to ensure rapid and effective incident response.
Proactive Strategies
- Establish a proactive approach: Be prepared for incidents before they escalate to reduce damage and downtime. This includes creating a cloud incident response plan, training teams on cloud-specific threats, and implementing automated monitoring tools.
- Regularly test and update plans: Conduct tabletop exercises and incident response drills to find weaknesses in your plan and help teams practice responses. Keep the plan fresh to adapt to new threats and cloud changes.
- Utilize security frameworks: Use proven methodologies like the CIS Controls or the MITRE ATT&CK Matrix to improve incident detection and define tactics. The CSA is also creating a holistic Cloud Incident Response Framework.
- Adopt a Zero Trust model: Zero Trust is an extension of the principle of least privilege. It assumes a breach has occurred and works to minimize the blast radius with micro-segmentation, continuous monitoring, and automated threat detection.
Operational and Technical Solutions
- Automate detection and response: Implement automated tools to monitor cloud resources and trigger responses in real-time. Automated runbooks, for example, can be automatically executed to resolve certain types of incidents, speeding up resolution and ensuring consistency. Tools like Security Orchestration, Automation, and Response (SOAR) platforms can automatically isolate compromised systems and revoke permissions.
- Enhance visibility and logging: Maintain visibility and auditing across all cloud platforms to track administrative and anomalous events. Implement a centralized logging and analytics platform, such as a Security Information and Event Management (SIEM) system, to consolidate logs and monitor for suspicious activity in real-time.
- Prioritize training: Ensure your team is familiar with cloud environments and tools through cloud-specific training and certifications. Well-trained teams can respond faster and more effectively during an incident.
- Use cloud-native and third-party tools: Leverage cloud-native tools like Cortex XSOAR, an AI-driven security orchestration, automation, and response platform, that can automatically isolate compromised systems and revoke permissions.. Third-party solutions can enhance visibility across multi-cloud environments, provide advanced analytics, and automate configuration checks.
- Secure identities and access: Implement strong access controls, multi-factor authentication (MFA), and the principle of least privilege. Regularly review and revoke access permissions for users who no longer need them.
Cloud Incident Response FAQs