Use VMRay Analyzer’s Contextual Threat Intelligence for Automated Threat Hunting in Cortex XSOAR
See how VMRay + Cortex XSOAR Accelerate Malware Investigation on our Upcoming Webinar!
The increasing number of previously unseen malware and malicious infrastructure (domains, URLs etc.) makes alert triage, validation, and enrichment very difficult. Security analysts spend a considerable amount of time investigating phishing and endpoint malware alerts. Gaining unmatched insights into the new threats requires a fresh approach to the threat analysis and investigation processes.
To overcome these challenges, defenders need superpowers to rapidly detonate, analyze and extract actionable threat intelligence from unknown files or URLs tied to the alert. VMRay Analyzer is an agentless, hypervisor-based sandbox which uses intelligent monitoring to distinguish between malicious behavior and legitimate activity. Every interaction is monitored, and even the most evasive malware strains fully execute in the sandbox, capturing a complete and accurate record of threat behavior. The data from VMRay’s automated malware analysis is fed into Cortex XSOAR, enriching detection, digital forensics, and threat intelligence, and enhancing incident response and threat hunting.
The VMRay Analyzer pack is available on the Cortex XSOAR Marketplace and can easily be installed with the click of a button, providing Cortex XSOAR customers with next generation sandboxing capabilities by integrating automated malware analysis into XSOAR customer’s playbooks. Designed to speed up alert investigation and enable autonomous response to critical malware incidents within Cortex XSOAR, the prebuilt content pack provides immediate value for security teams. Our joint customers can use this powerful integration to improve threat detection, accelerate incident response and gain actionable threat intelligence to block future threats.
Let’s take a look at why this is so important for your security program
In a fast-evolving threat landscape, VMRay and Cortex XSOAR allow your security team to filter out the noise and respond to the real malware threats faster. Contextual threat intelligence provided by VMRay Analyzer also allows you to start automated threat hunting in seconds.
The VMRay content pack enables you to:
- Streamline phishing and malware alert investigation to protect your business.
- Empower your analysts to make better informed decisions with actionable and accurate threat intelligence.
- Automatically get in-depth malware analysis reports with high-fidelity IOCs including command-and-control addresses.
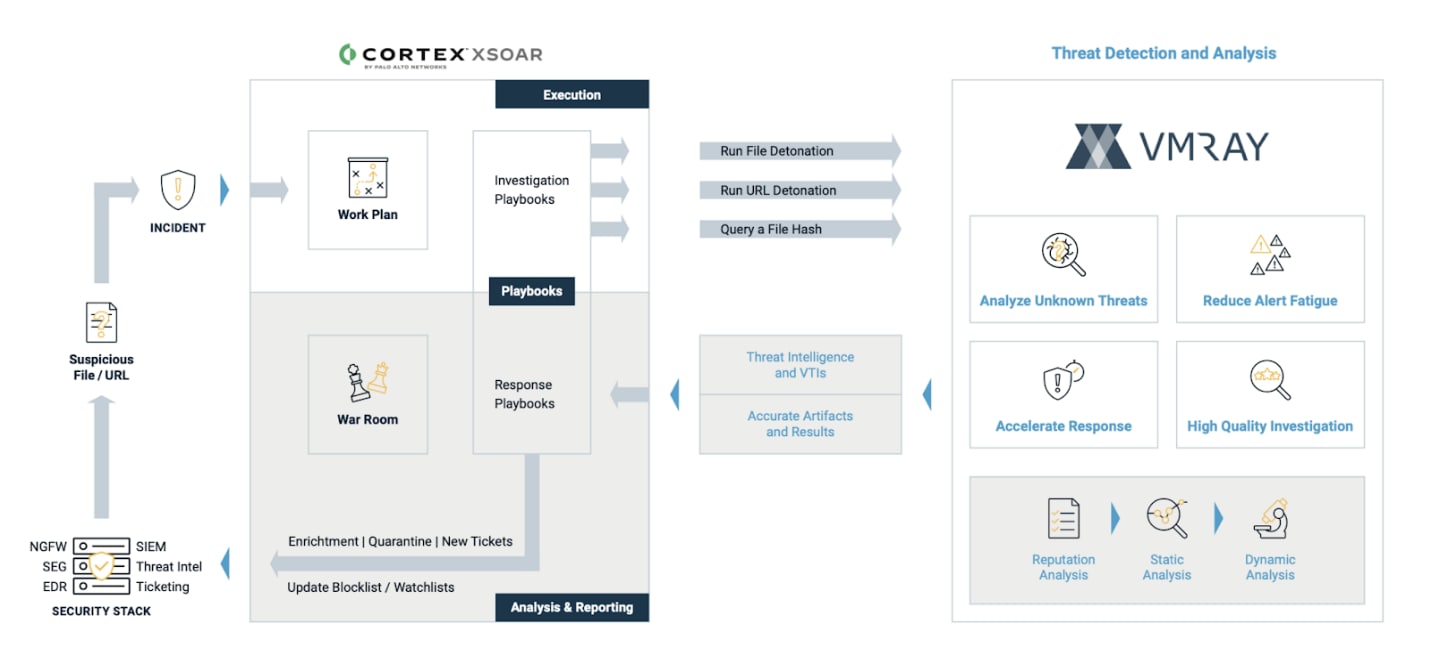
VMRay Analyzer + Palo Alto Networks Cortex XSOAR Malware Analysis
Join us and discover how to accelerate malware investigations and extract actionable threat intelligence with VMRay Analyzer and optimize your Cortex XSOAR incident response workflows during VMray’s Autonomous Response to Critical Malware Alerts webinar hosted live on November 8th at 8 AM PT/11 AM ET - Register now!

Learn More
Build out your security program with the VMRay content pack, available now on the Cortex XSOAR Marketplace. Look up pre-built integrations for your top security tools with over 900 content packs available for Cortex XSOAR, the market’s leading SOAR platform.
Not yet a VMRay Analyzer Enterprise or Standard customer? Looking for better results from your existing sandbox? Easily activate a free 30 day trial or inquire about a Private Offer right in the XSOAR Marketplace. Don’t have Cortex XSOAR? Download the Community Edition to get started.
Learn more about VMRay Analyzer or see the VMRay pack on the XSOAR Marketplace.
Related Blogs
Subscribe to Security Operations Blogs!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.