Accelerate SecOps Investigation and Response to the Microsoft Exchange Server Attack with Cortex XSOAR
As the massive scale of the Microsoft Exchange Server attack comes into focus, organizations are rushing to discover if their exchange server is a victim of the 0-day exploits and what is needed to protect servers from being compromised. If your organization has already patched your servers, you are likely looking to know how you can watch for related malicious activities and new indicators and vulnerabilities post patching to take automated action. This blog details step-by-step instructions to help you immediately deploy a monitoring and response system leveraging Cortex XSOAR’s capabilities. Please refer to the Unit 42 blog for specific guidance steps to hunt for the recent attacks targeting Microsoft Exchange servers.
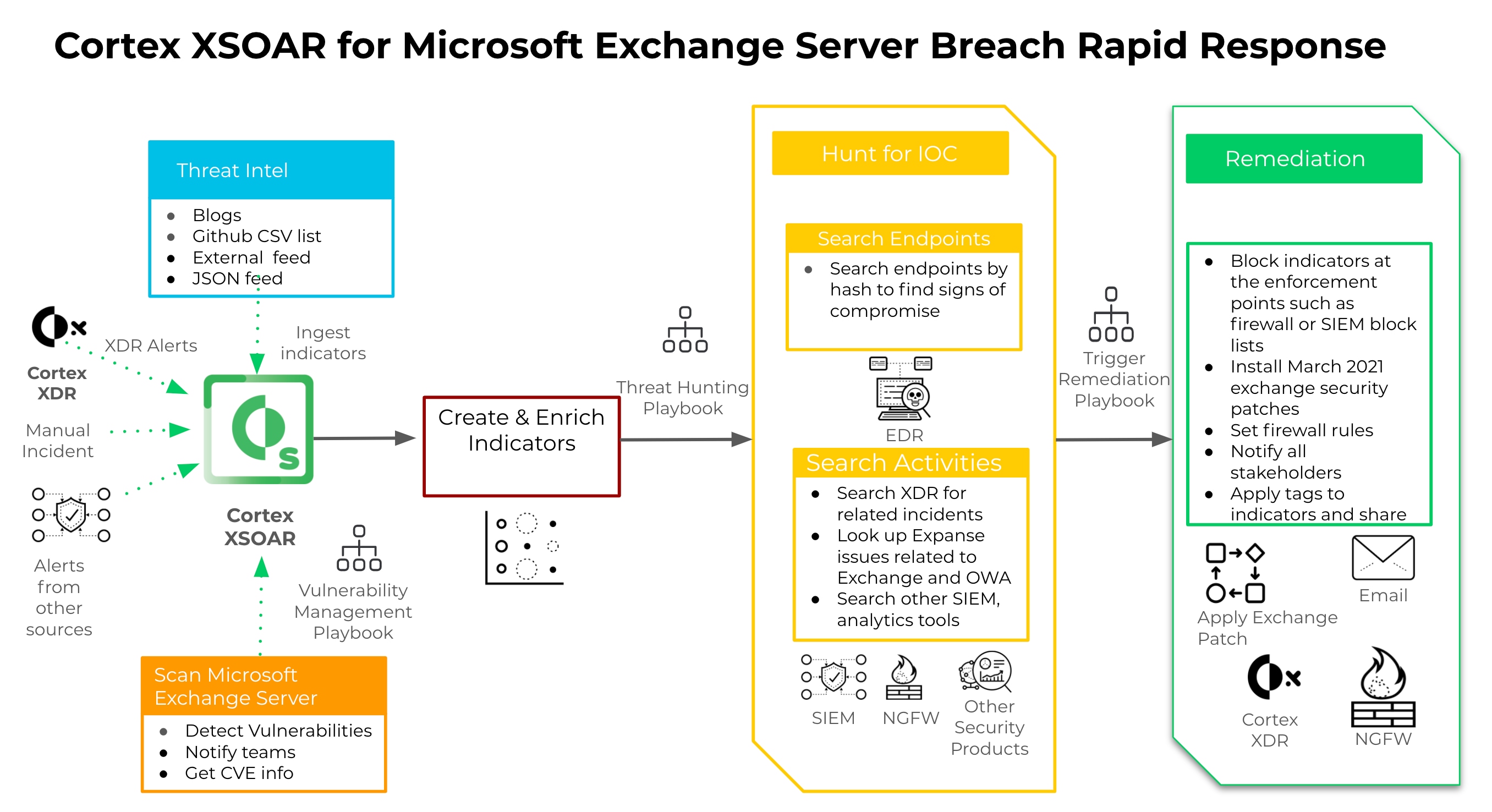
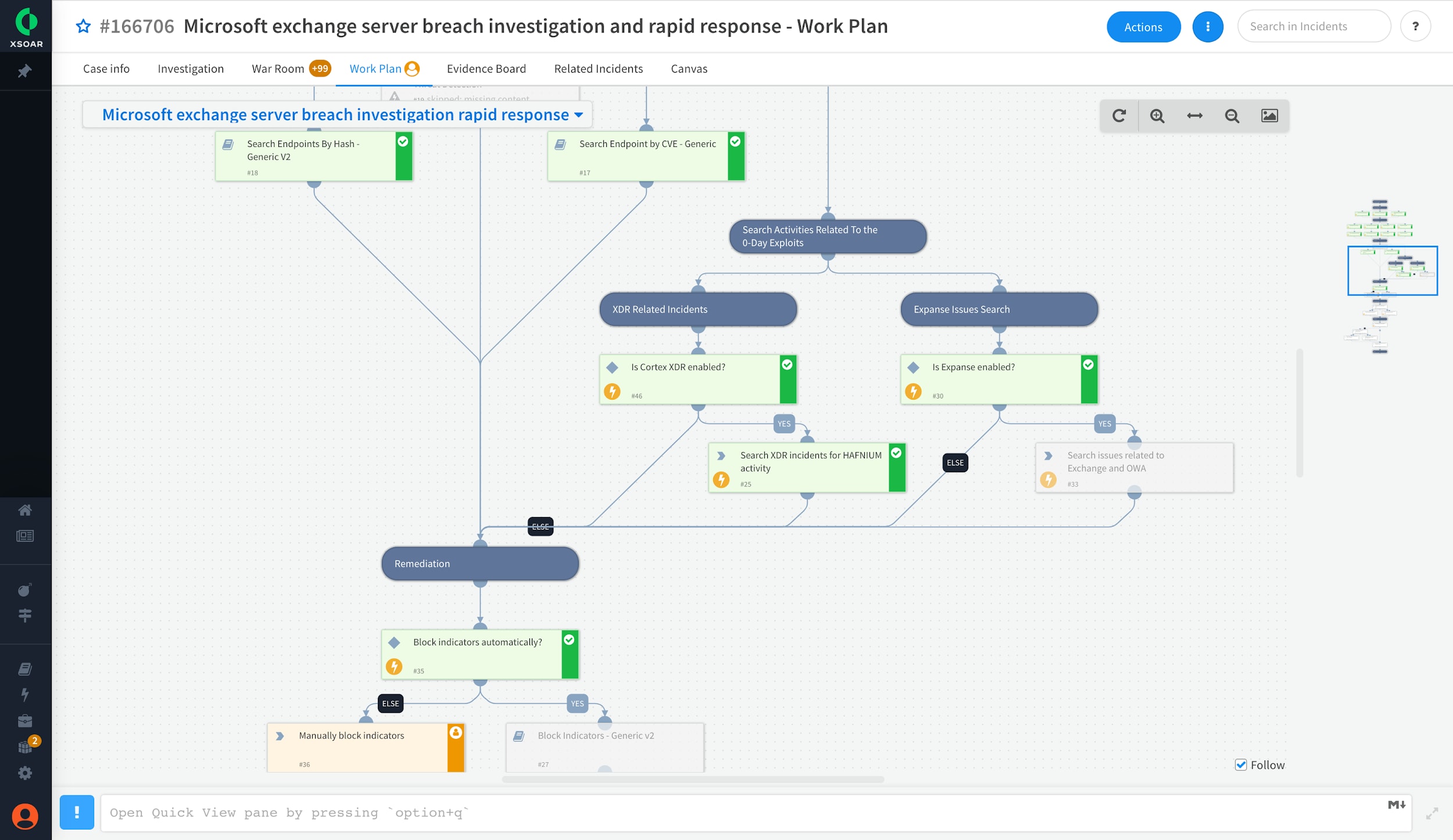
Step 1 - Deploy the Cortex XSOAR HAFNIUM-Exchange 0-day Exploits playbook
Use the Cortex XSOAR HAFNIUM-Exchange 0-day exploits playbook included in the Cortex XSOAR Rapid Response Content Pack to automate response actions and processes associated with collecting, hunting and blocking indicators of attack and compromise. Cortex XSOAR HAFNIUM-Exchange 0-day exploits playbook brings instant response capabilities to SecOps. The same playbook is highly customizable and can also be used as a template to hunt and block malicious indicators using additional tools in your environment. Please refer here for complete documentation of the playbook.
This automated playbook performs the following actions:
- Collects indicators to be used during the threat hunting process
- Retrieves IOCs related to HAFNIUM and the exploited Exchange 0-day vulnerabilities
- Discovers IOCs related to the attack
- Queries firewall logs to detect malicious network activity
- Searches endpoint logs for malicious hashes to detect compromised hosts (Available from Cortex XSOAR 5.5.0).
- Searches for CVEs using integrations
- Blocks malicious indicators
Step 2 - Determine if you have been compromised
Security analysts using Cortex XSOAR can use out of the box integrations with hundreds of other 3rd party alert sources to determine if they’ve been compromised. Refer to your vendor specific advisories to learn more about the exact incident types that detect this hack and configure those into the integration alert source. Once configured, those alerts are automatically ingested into Cortex XSOAR and enable you to take automated response actions.
One out of hundreds of integrations, the Cortex XDR integration in Cortex XSOAR is critical for detecting and responding to the Microsoft Exchange attack. Let’s take a look!
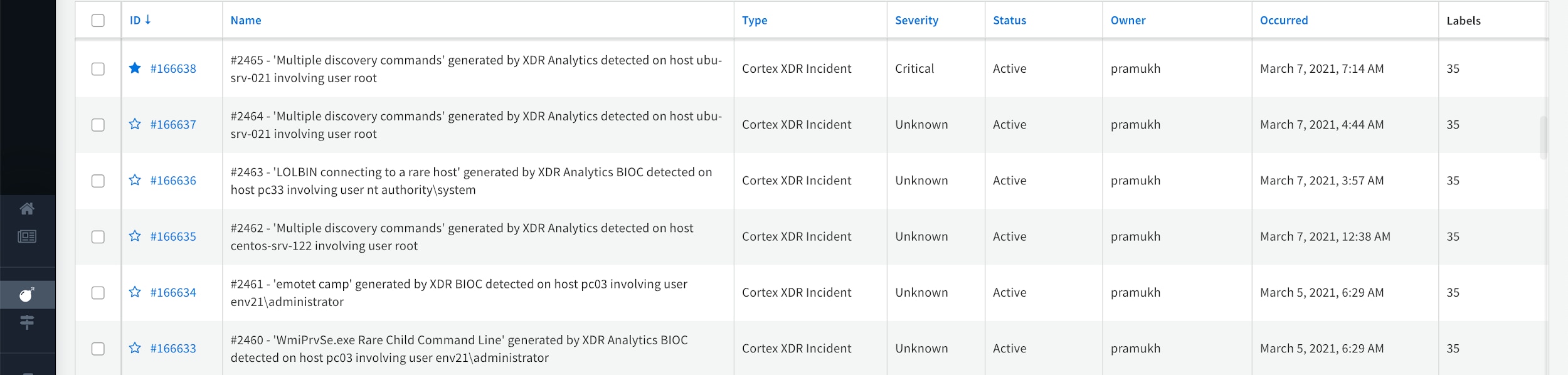
Sample Cortex XDR incidents in Cortex XSOAR
The investigation page on Cortex XSOAR provides full visibility into Cortex XDR alerts and file artifacts as shown. You can easily configure alerts to get auto-notified including on your Cotex XSOAR mobile application to watch out for the Microsoft exchange processes writing aspx type files, along with other potential Cortex XDR alerts generated by Cortex XDR BIOC or other supported types of incidents that will help you confirm signs of compromise. For more information on activities observed by our Unit 42 research team including file types and artifacts, please refer to our Unit 42 blog.
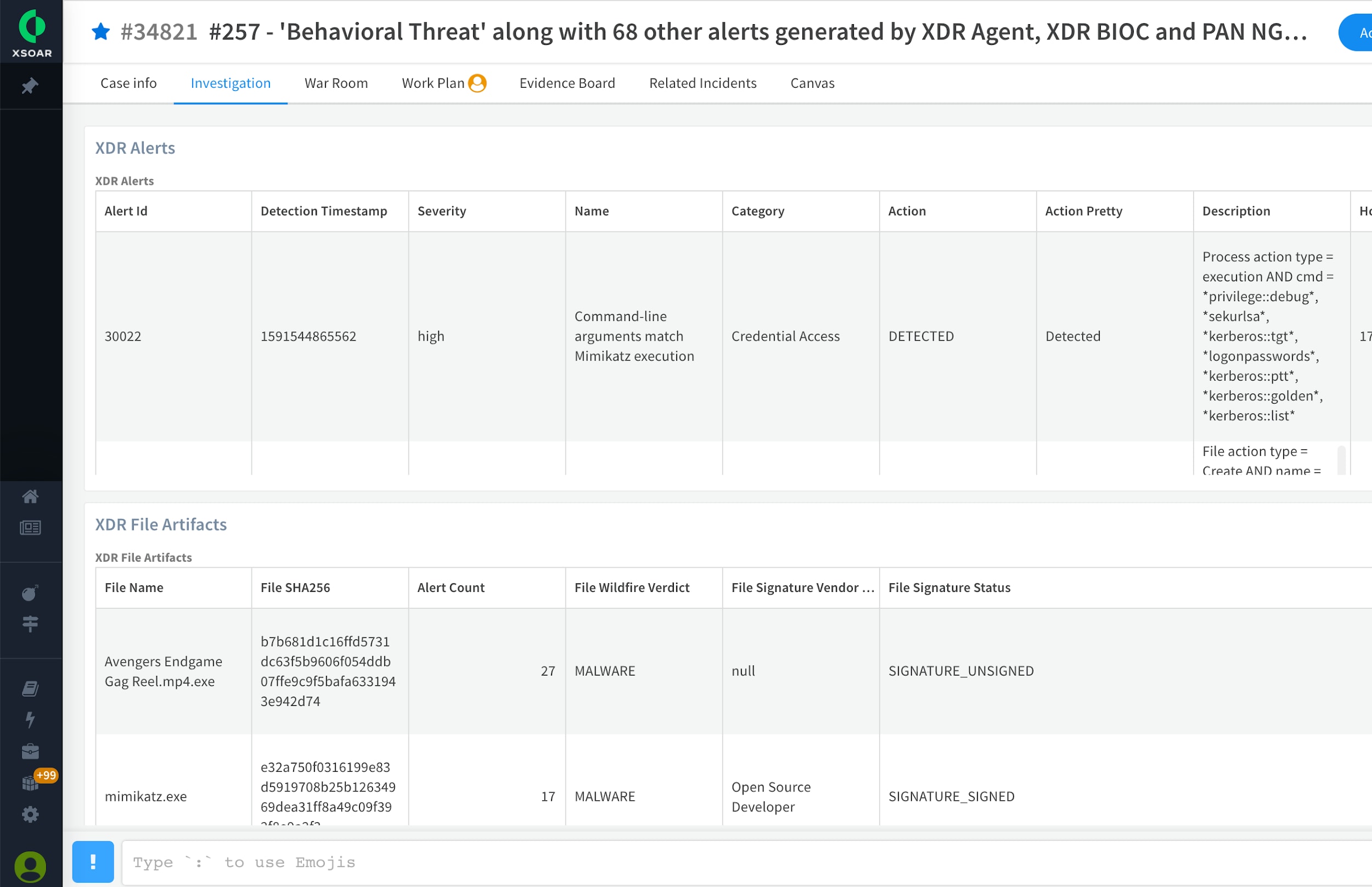
The investigation page on Cortex XSOAR is highly customizable and captures investigation-related information including process, file artifacts, indicators, etc. from a single console. This is a representational image.
Integrate additional alert sources:
Likewise, if you have other alert sources and have configured the corresponding integrations, Cortex XSOAR should have already created incidents and triggered corresponding playbooks to automatically ingest and enrich alerts. Similar steps can be followed to confirm signs of compromise. For example, if you have the NGFW syslog integration enabled, then you can use the NGFW and Syslog integrations in Cortex XSOAR to monitor for syslogs containing the following sample Threat IDs. There are multiple signatures. Please refer here to learn more about it. The following is a sample set of relevant threat IDs for reference:
Microsoft Exchange Server Remote Code Execution Vulnerability Unique Threat ID: 90815
Microsoft Exchange Server Remote Code Execution Vulnerability Unique Threat ID: 90796
Microsoft Exchange Server Remote Code Execution Vulnerability Unique Threat ID: 90800
Microsoft Exchange Server Remote Code Execution Vulnerability Unique Threat ID: 90797
Step 3 - Monitor for Indicators of Compromise (IoCs)
The HAFNIUM-Exchange 0-day exploits playbook can be used to monitor IoCs by automatically ingesting indicators from several trusted and reliable sources, adding them to enforcement points such as NGFW EDL or SIEM block lists. Cortex XSOAR also supports the configuration of custom feeds such as CSV feeds to ingest indicators from other internal or external sources. As an example, if you want to directly ingest indicators made available by Microsoft that includes malicious hashes and file path information corresponding to the recent Exchange server hack, then you can configure Cortex XSOAR CSV feed integration. This integration will auto-fetch the feed information in real time and add it to Cortex XSOAR’s indicator repository, helping your team to stay updated on the latest known indicator information shared by Microsoft. This feed data is further used by Cortex XSOAR to automatically enrich incidents.
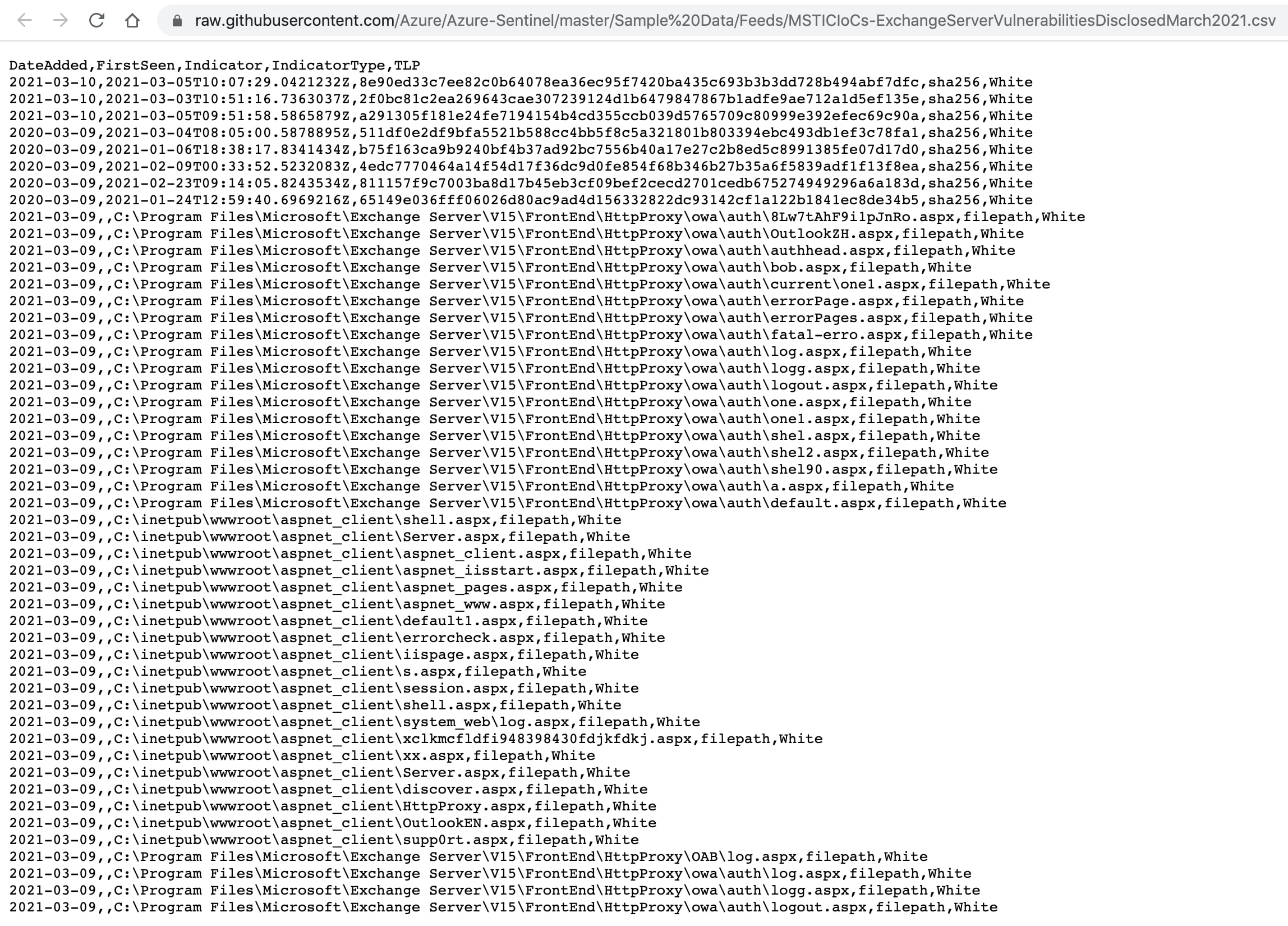
Observed indicators from Microsoft feed that include file paths where attackers are known to have created webshell files.
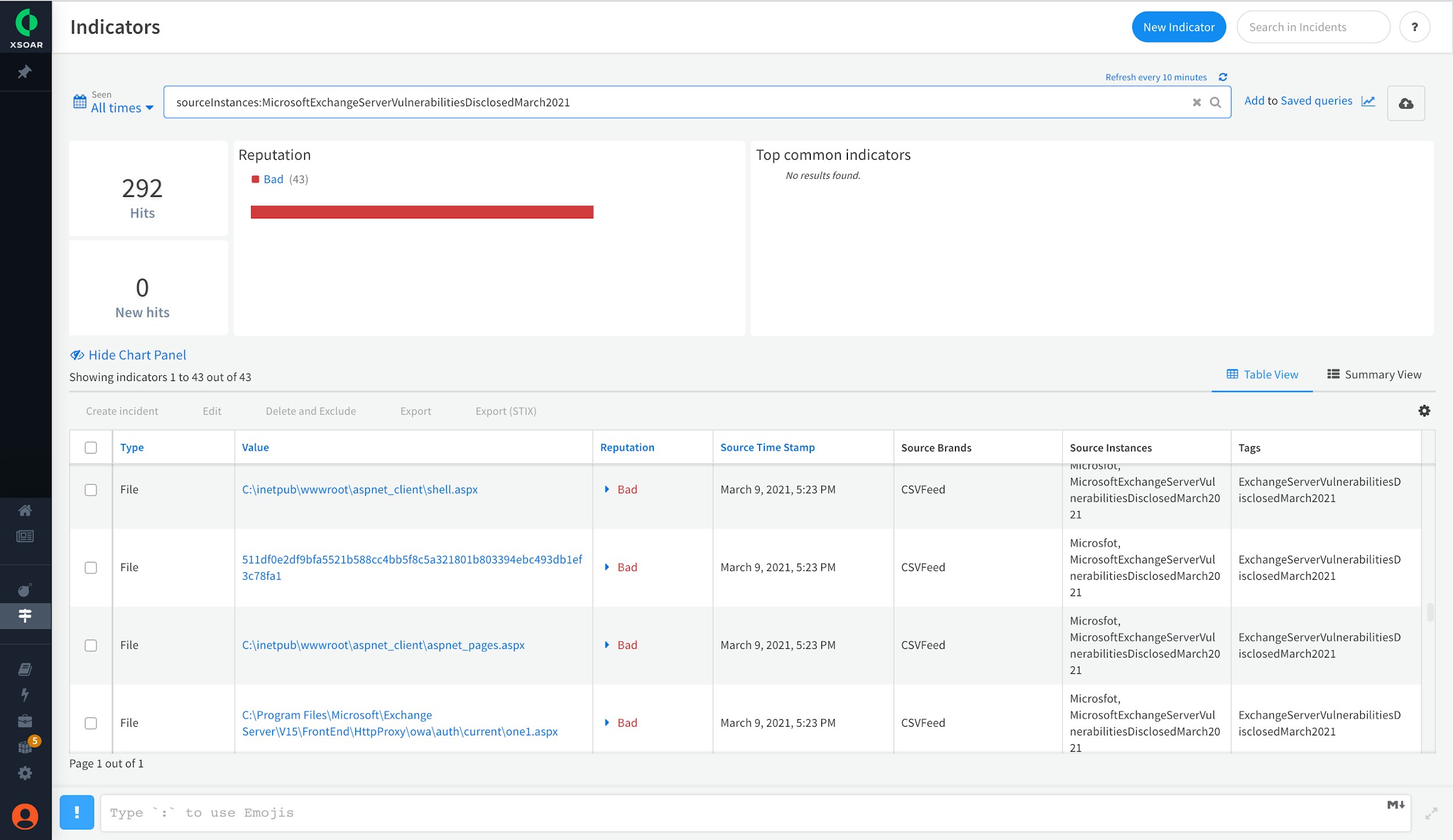
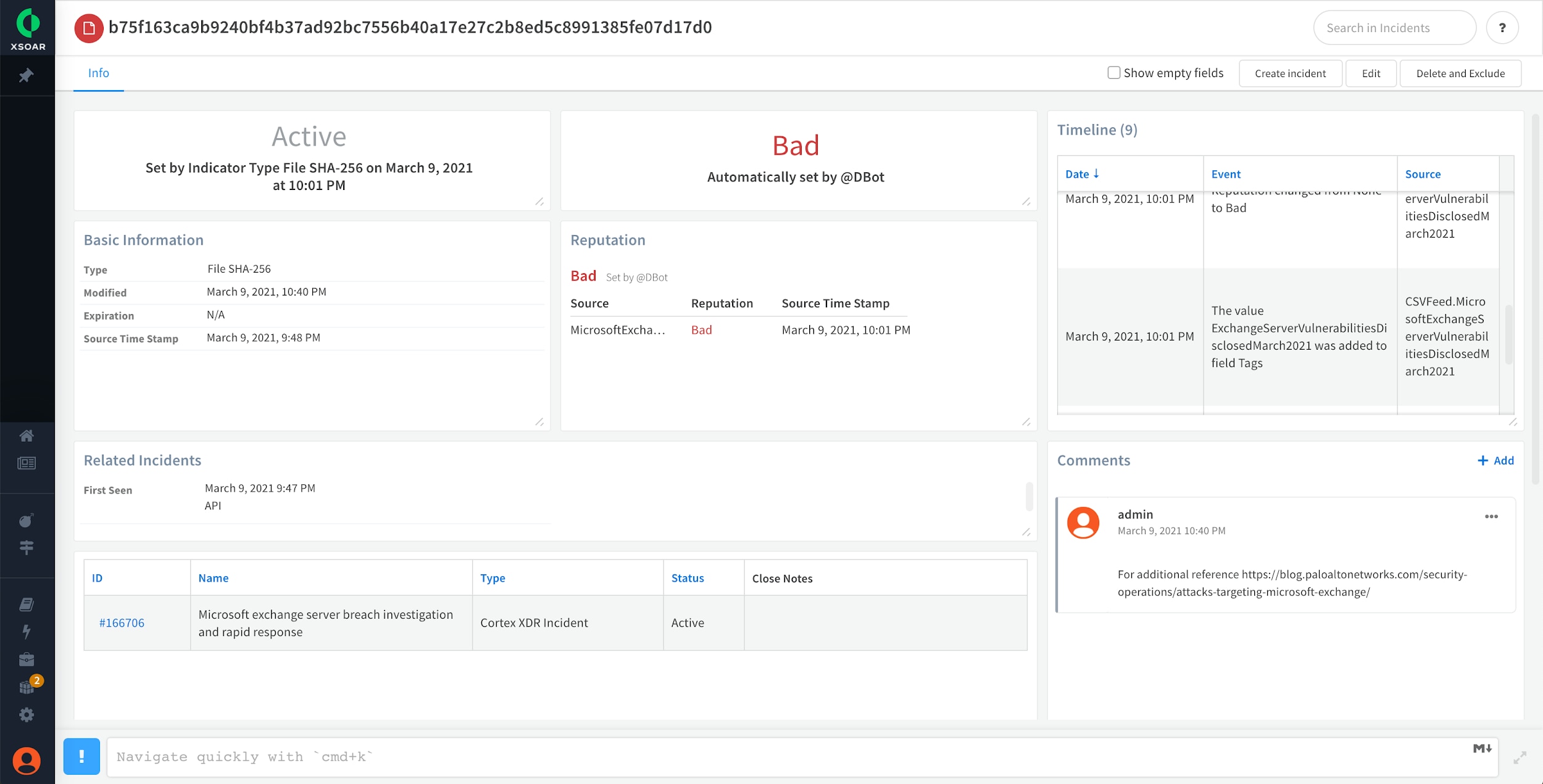
Each indicator has a full-blown indicator lifecycle page that helps threat hunting teams dive deeper and receive an instant view of current details, including the timeline info, indicator reputation, and expiration status as shown here.
Integrate recommended Unit 42 feed integration
In addition to fetching indicators of compromise from the above sources automatically using the HAFNIUM - Exchange 0-day exploits playbook, customers are highly encouraged to configure the out-of-the-box, Palo Alto Networks Unit 42 feed integration to ingest indicators and reports using TAXII for additional threat coverage. This feed is approved by the Palo Alto Networks Unit 42 research team, and Cortex XSOAR provides out-of-the-box layouts for mapping Unit 42 data.
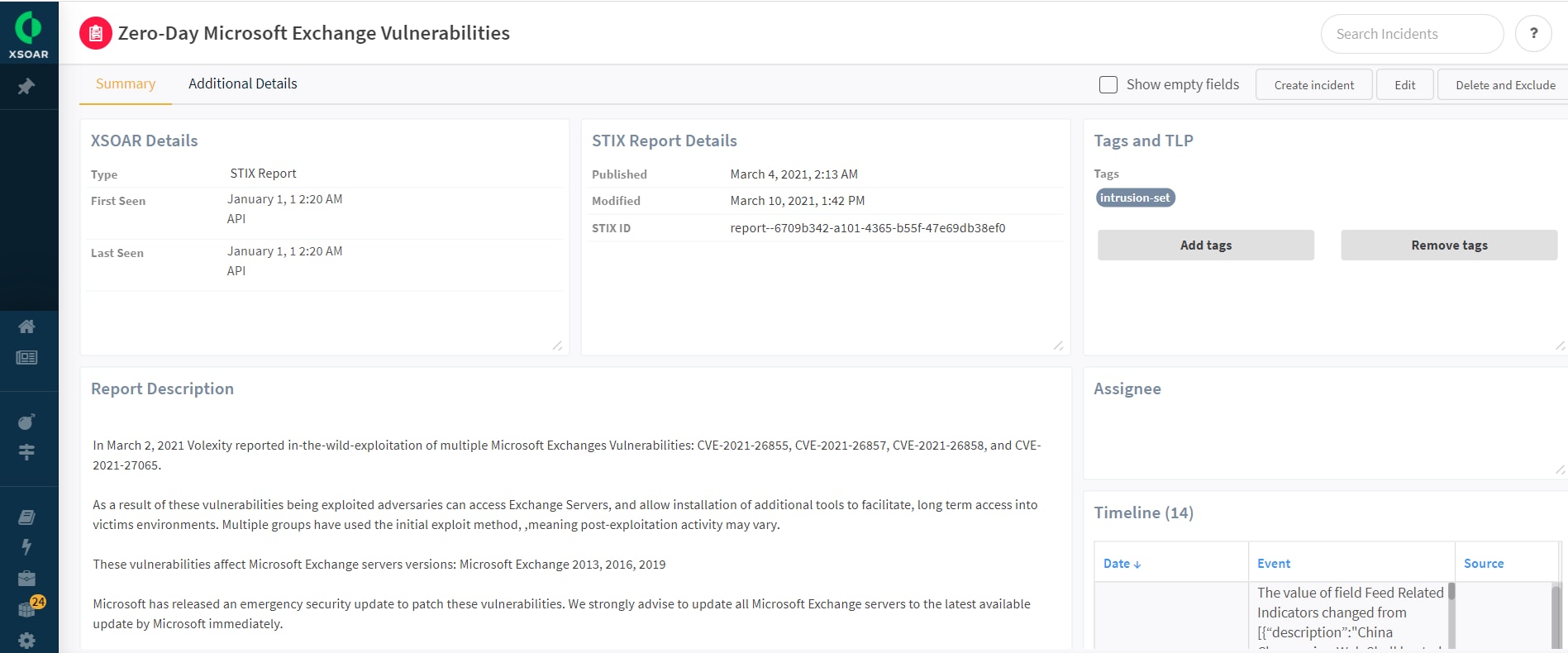
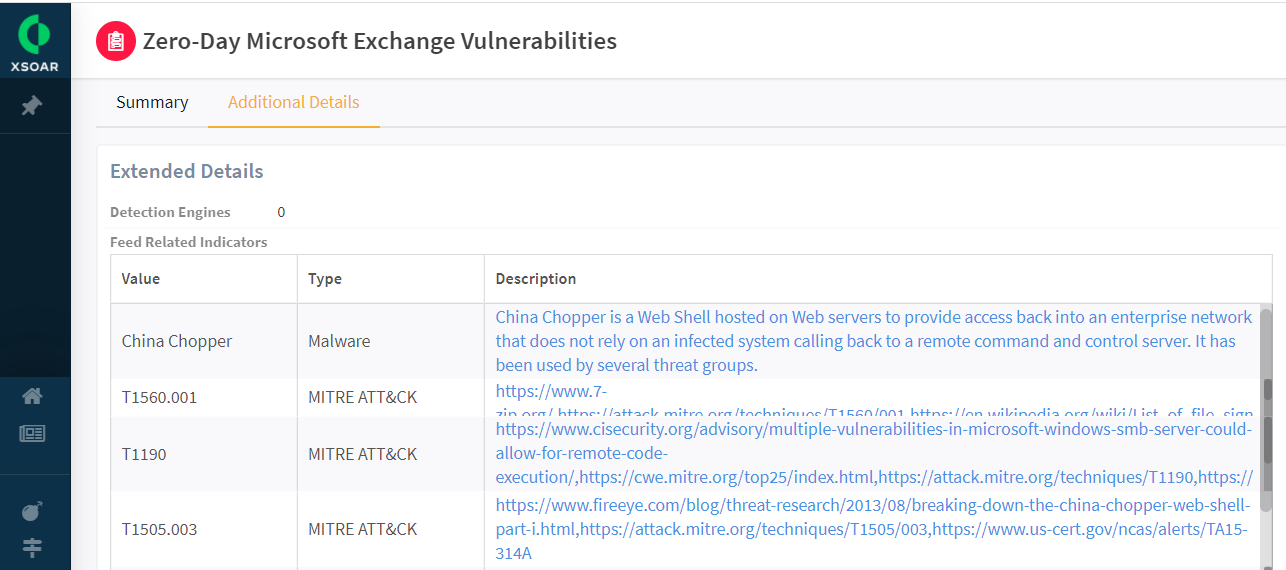
One of the other ways to learn about the initial signs of compromise is to refer to the Cortex XSOAR Canvas section that provides a visual correlation between detections and indicators of compromise. No need to worry if your standard operating procedures mandate that you must save this as a piece of evidence. Cortex XSOAR users can add the Canvas as well as other War Room artifacts to the evidence board. SecOps analysts can also manually export a PNG image, add it to the War Room with just a few simple clicks, and share it with other stakeholders using War Room’s Slack-like chatOps functionality.
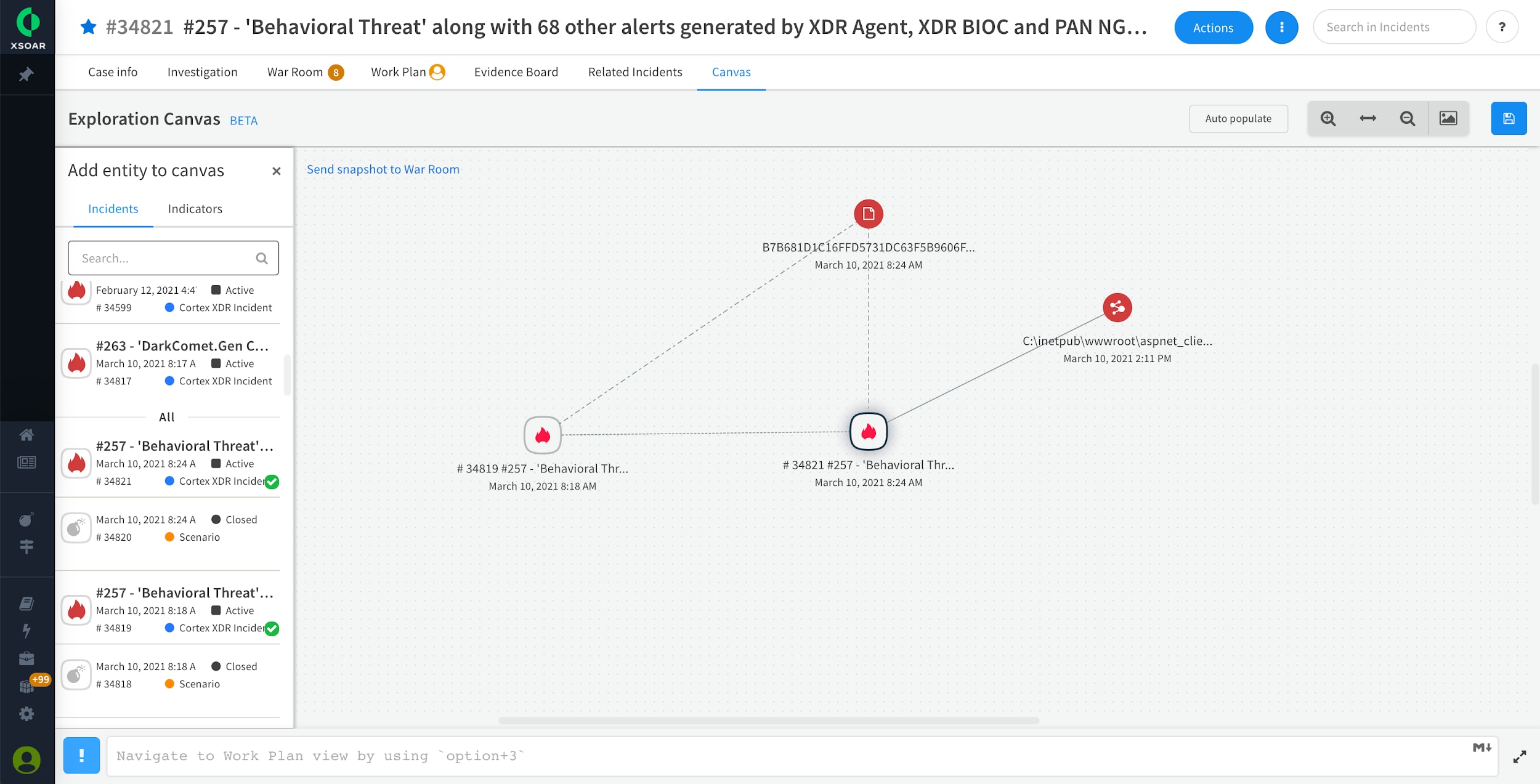
Cortex XDR incident related to a bad SHA256 hash and a file path. This provides quick visual correlation. This is a representational image.
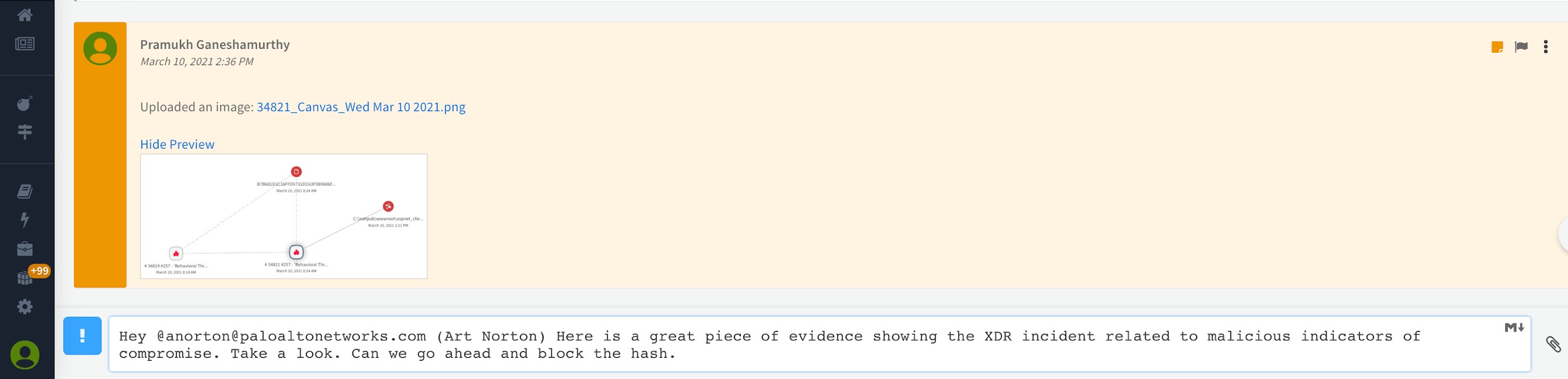
The command line interface doubles up as a ChatOps functionality where you can easily share the signs of compromise with other team members. The same command line can be further used to take ad-hoc actions.
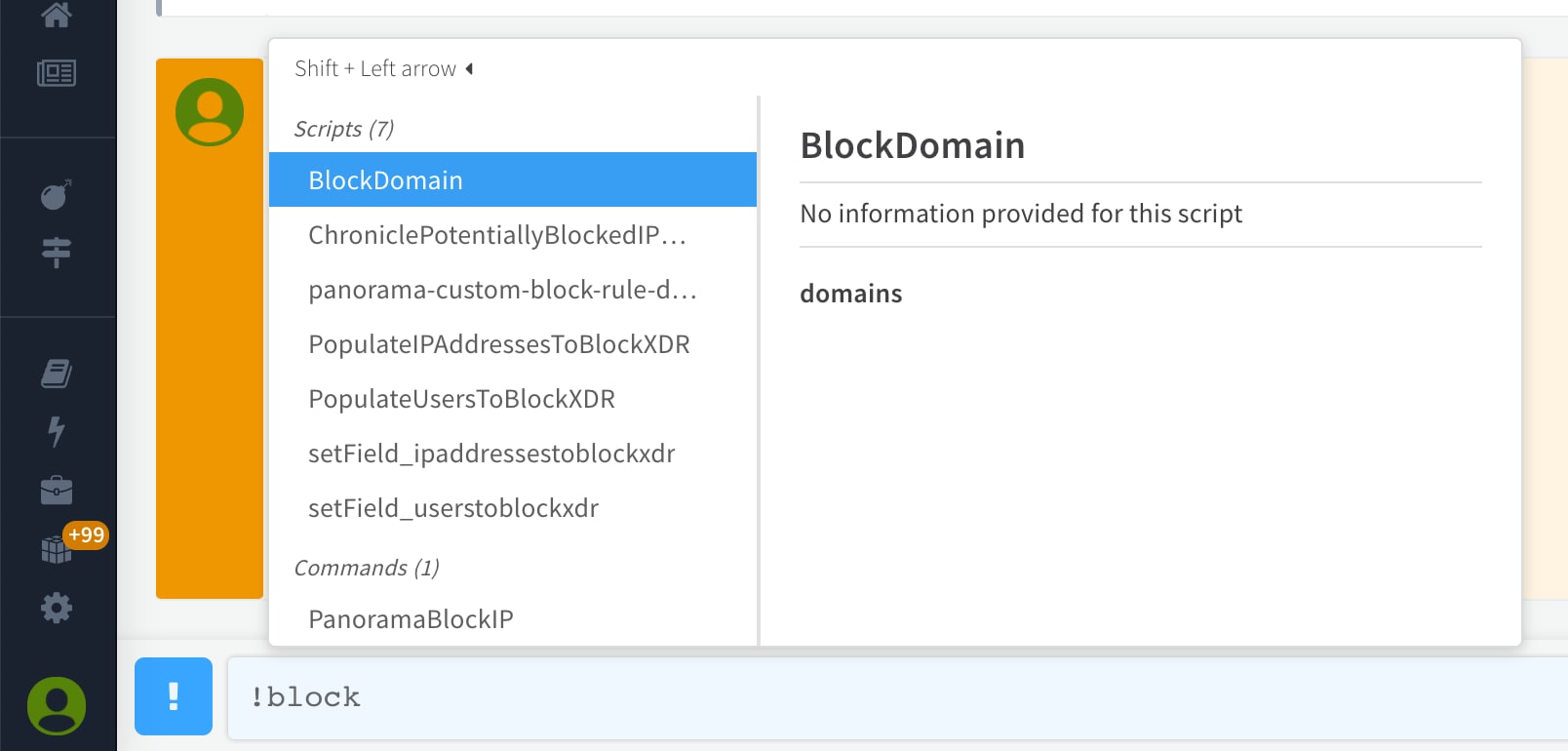
Command line interface can be used to fetch information and artifacts or block indicators on an ad-hoc basis if need be. You can always choose to automate response actions using playbooks.
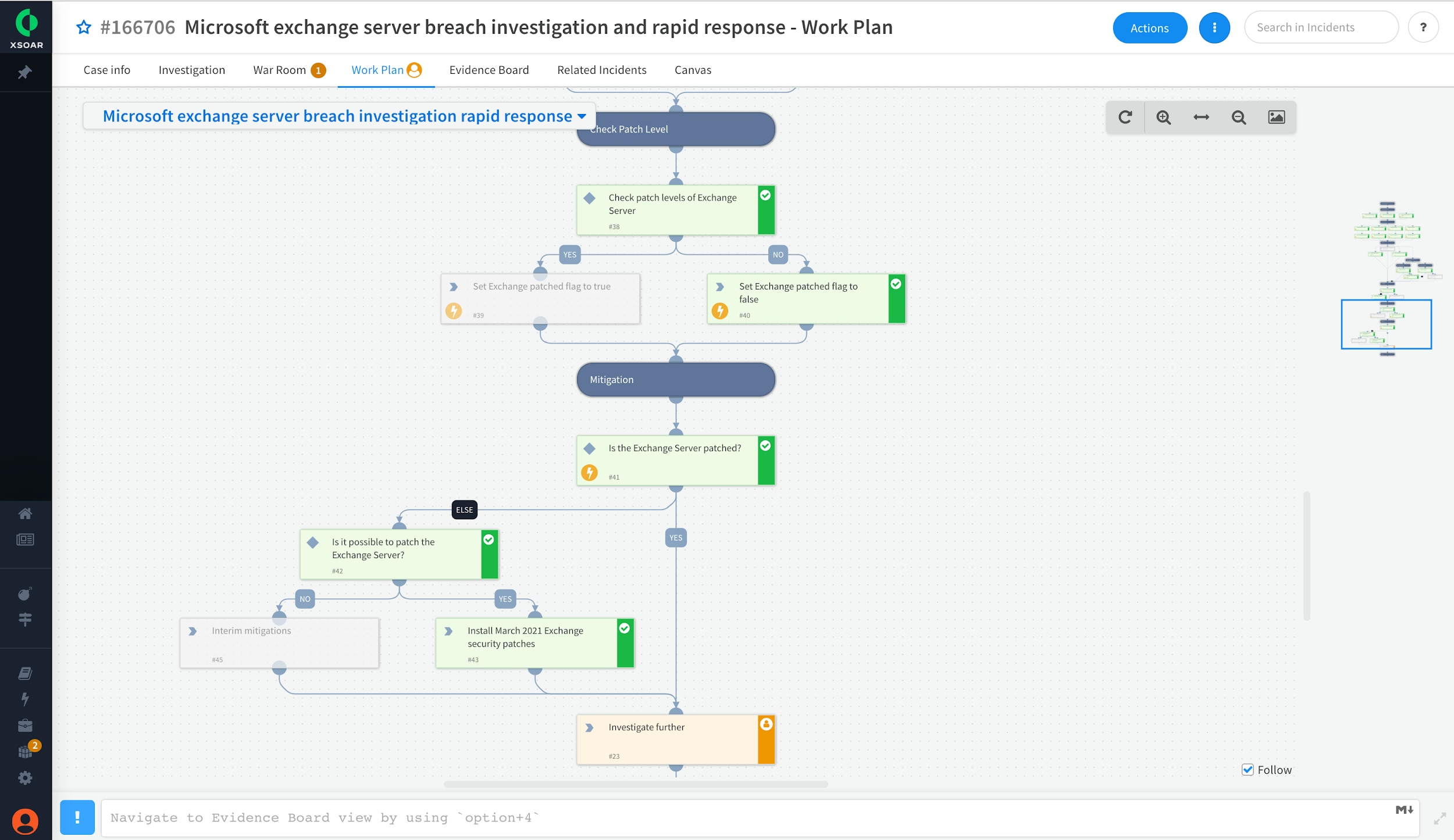
Step 4 - Stay Prepared: Launch vulnerability scans to discover new Exchange vulnerabilities
Cortex XSOAR’s out-of-the-box integrations with popular vulnerability management tools helps vulnerability management and SecOps teams regularly scan Microsoft Exchange Servers to detect new vulnerabilities and notify relevant teams with vulnerability information, including the CVE details. We recommend configuring the vulnerability management playbooks as jobs for periodic scanning of Microsoft Exchange Servers to detect new vulnerabilities.
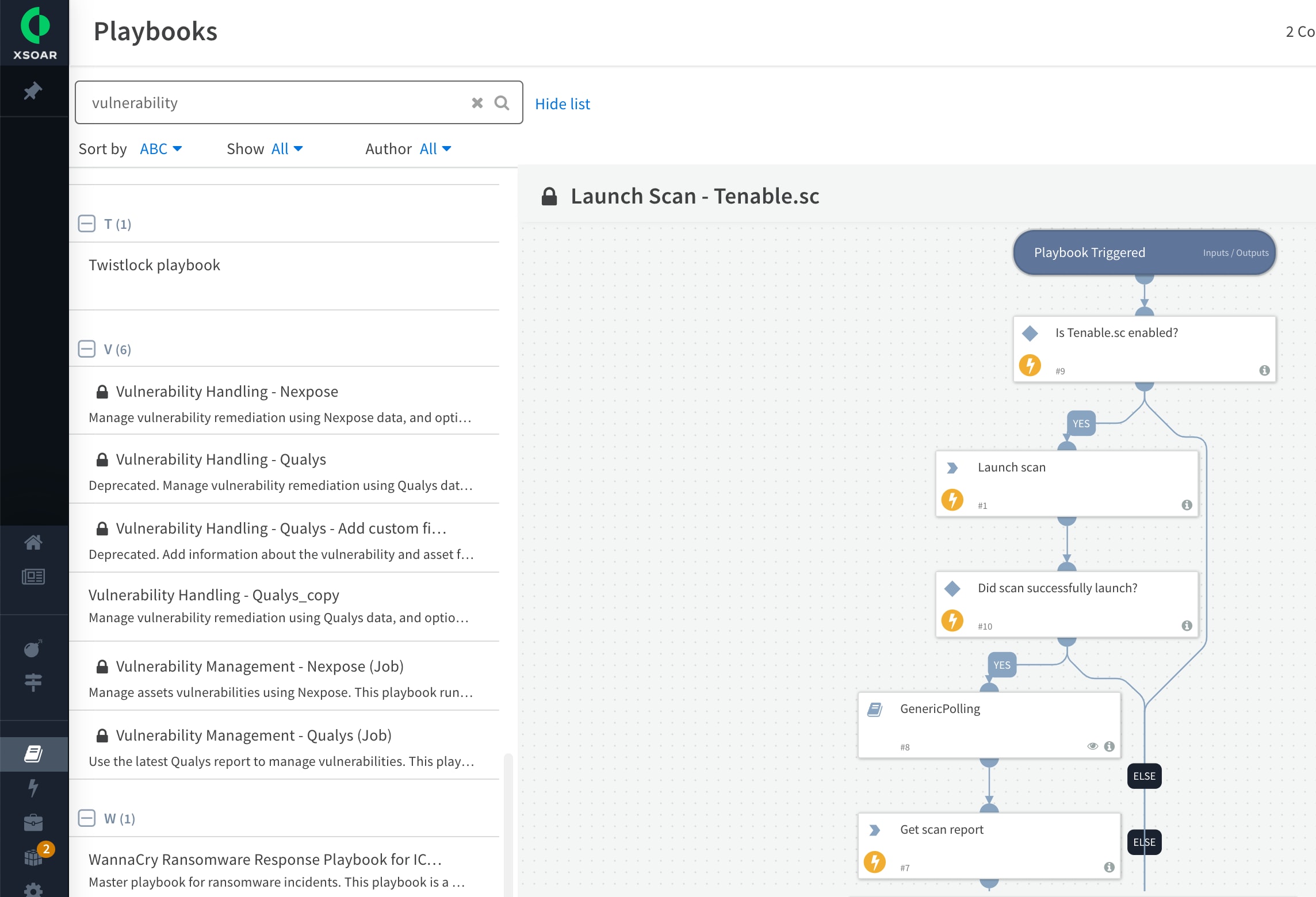
Example of a vulnerability management playbook in Cortex XSOAR. Each playbook can be easily configured to run as a job for periodic scanning of servers in your network
New CVE indicators are automatically created in Cortex XSOAR. Security analysts can get an instant snapshot of the relationships between incidents and indicators to arrive at meaningful conclusions and make security decisions.
The following are the supported vulnerability management partner products. Please refer to our integrations page for most up to date information.
- Tenable
- Qualys
- Nexpose
- Rapid7
- RiskSense
Step 5 - Collect Microsoft Exchange forensics information
Once we have successfully collected the detection alerts, vulnerabilities, and indicators of compromise, the next step is to collect forensics information from different sources. The Cortex XSOAR War Room plays a critical role in situations where SecOps need to interact with forensics teams and subject matter experts to gather forensics information during an ongoing investigation. Forensics teams can share the malicious activity data with the SecOps team from within the War Room using the ChatOps functionality.
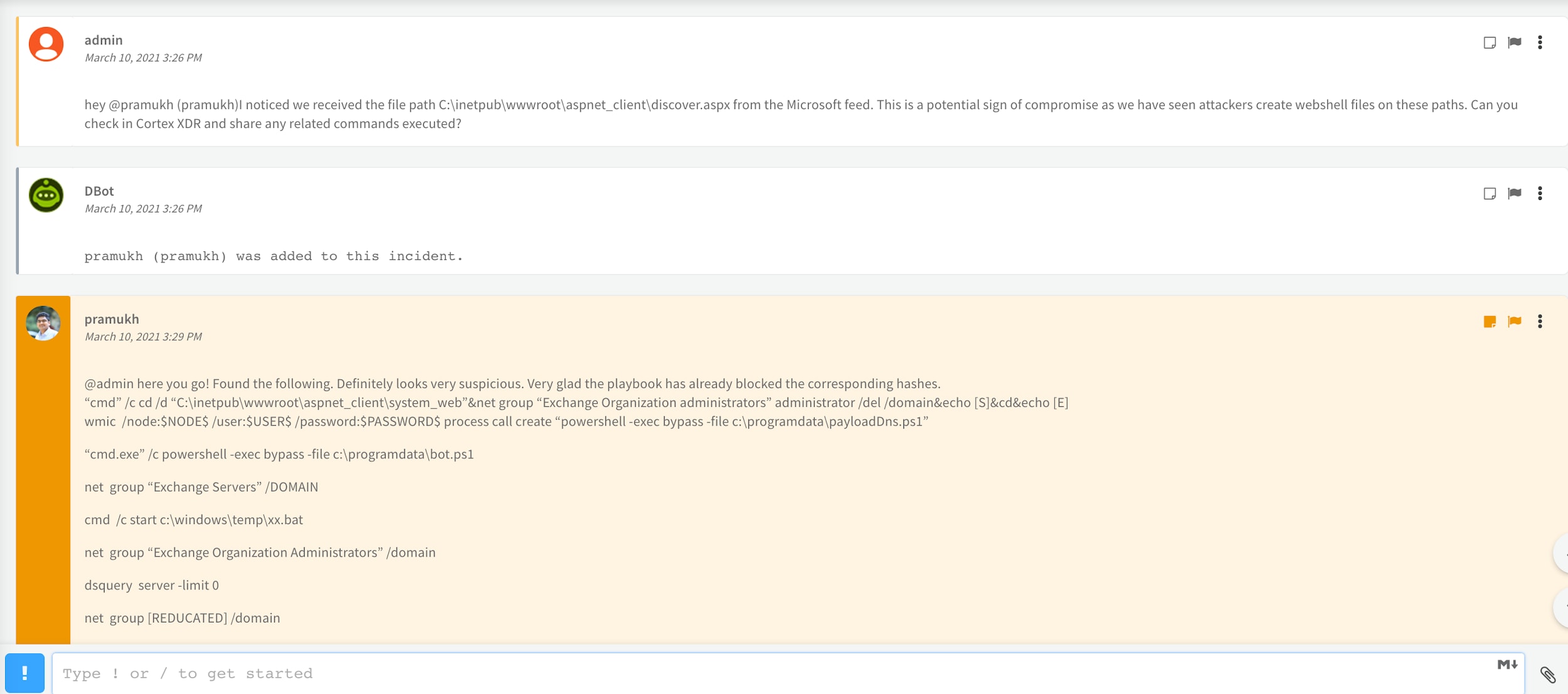
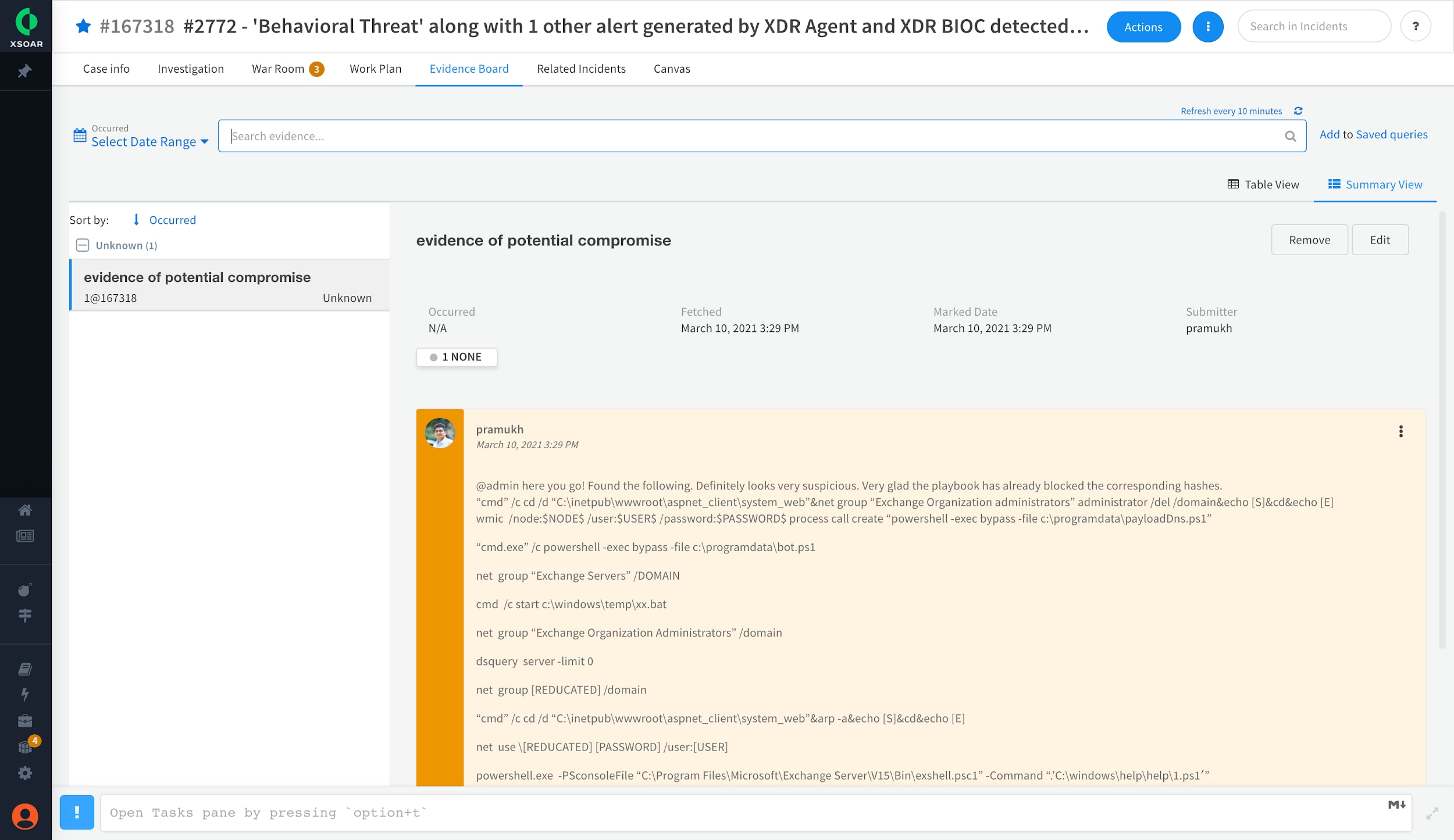
Representational image showing the evidence board in Cortex XSOAR capturing evidence of potential compromise
Cortex XSOAR’s integrations with Cortex XDR, Expanse, and several other SIEM and security analytics tools are also of immense help. By automatically searching for suspicious related activities and looking up issues related to Exchange Servers and OWA, signs of detected potential compromise can be added to the evidence board on Cortex XSOAR for future reference and retrospective analysis.
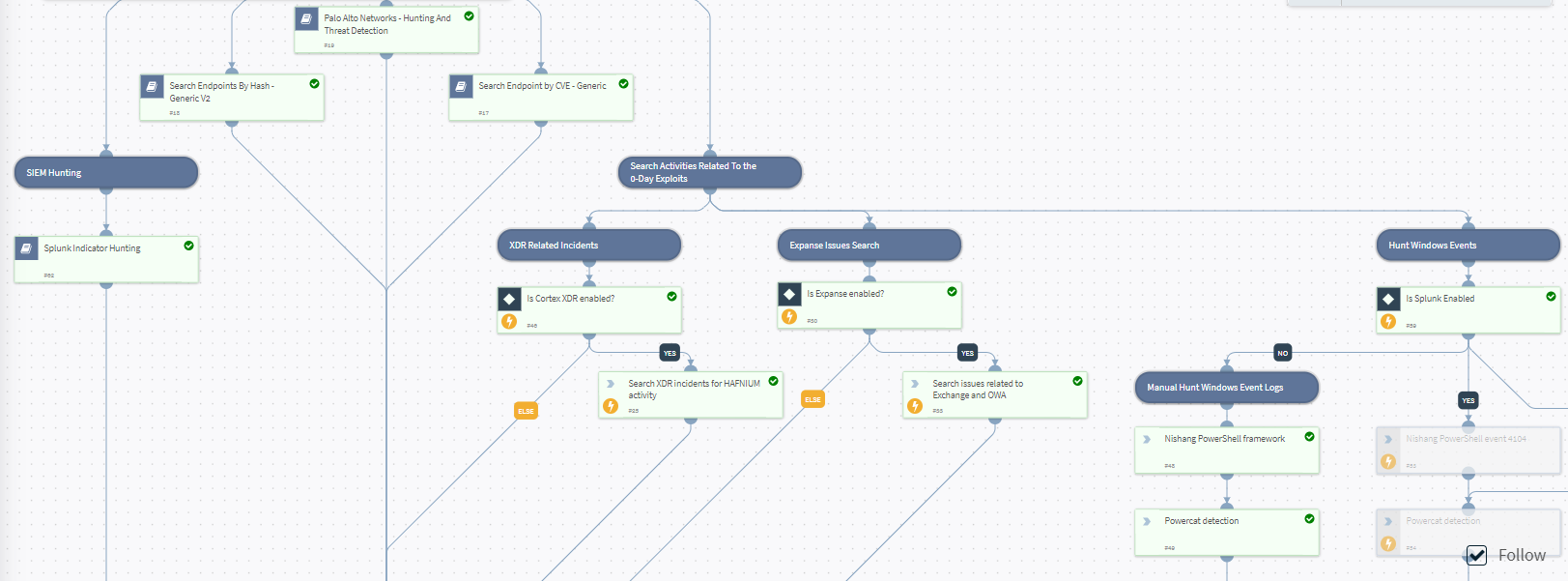
HAFNIUM - Exchange 0-day exploit playbook automates the entire look up process and saves precious analyst time
The playbook uses built-in integrations with other security information and event management, and security analytics tools to hunt for related activities
For example, Cortex XSOAR out-of-the-box integration with Splunk enables Cortex XSOAR to automatically run predefined queries in Splunk and other SIEMs. You can view a list of all available out of the box integrations.
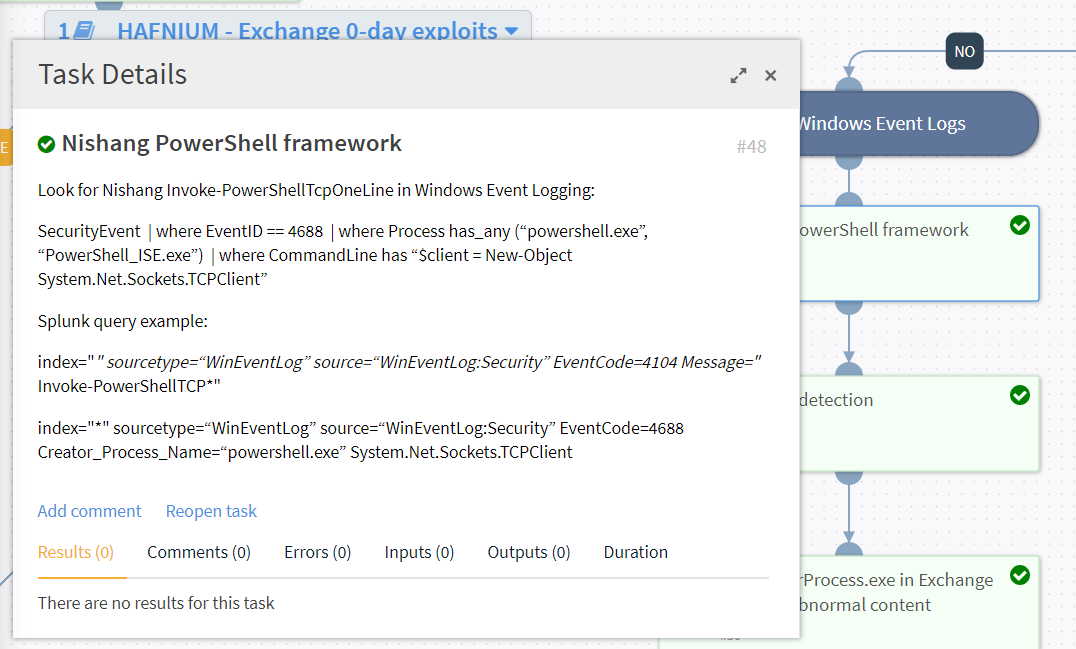
Suggested predefined queries to use in your SIEM tool to hunt for related activity
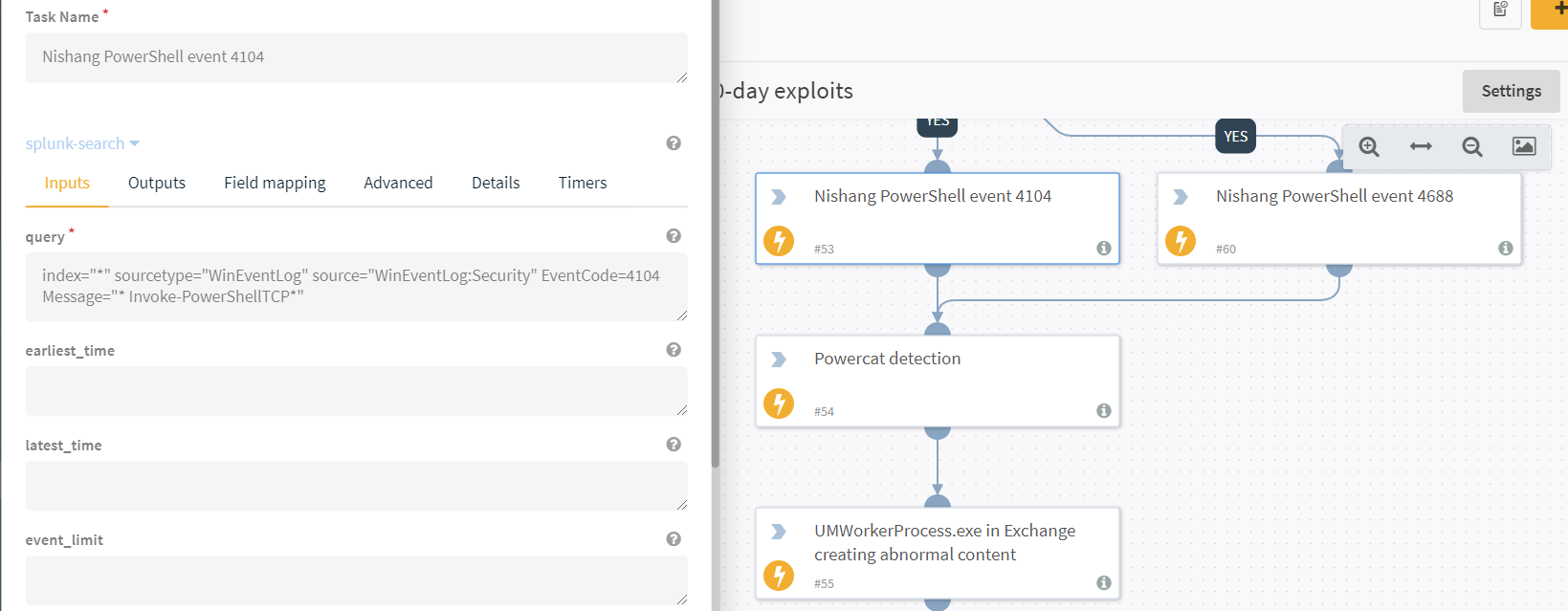
The playbook automates querying process for a subset of SIEMs, for example- splunk search command wrapping the query
As another example, the Cortex Expanse issues below that pertain to the ongoing hack can be automatically looked up by the playbook. These look ups can help confirm the presence of vulnerabilities and signs of compromise.
- Insecure Microsoft Exchange Server
- This issue calls out the on-premises Microsoft Exchange Servers that are vulnerable to the zero-day exploits described by Microsoft in March 2021 and used by the Hafnium threat actor. The vulnerabilities identified by Microsoft are CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, and CVE-2021-27065. Additional details can be found here
- Microsoft Exchange Server
- This issue flags all on-premises Microsoft Exchange Servers. It includes results for POP3, SMTP, IMAP, and HTTP (via Outlook Web Access) services associated with Microsoft Exchange.
- Microsoft OWA Server
- This issue flags all Microsoft Outlook Web Access (OWA) servers. Results for this issue include OWA instances deployed on on-premises Microsoft Exchange servers and cloud-based Office365 tenants. OWA is also known as “Outlook on the Web”, “Outlook Web App” and “Exchange Web Connect”. In most instances, Microsoft OWA servers are not concerning from a security perspective.
Step 6 - Automate remediation procedures for Microsoft Exchange
The last and final step is to take remediation actions by installing the March 2021 Microsoft exchange security patches and block malicious indicators at the relevant enforcement points such as SIEM block lists or NGFW EDLs.
Remediation actions as seen on a live run of Cortex XSOAR playbook
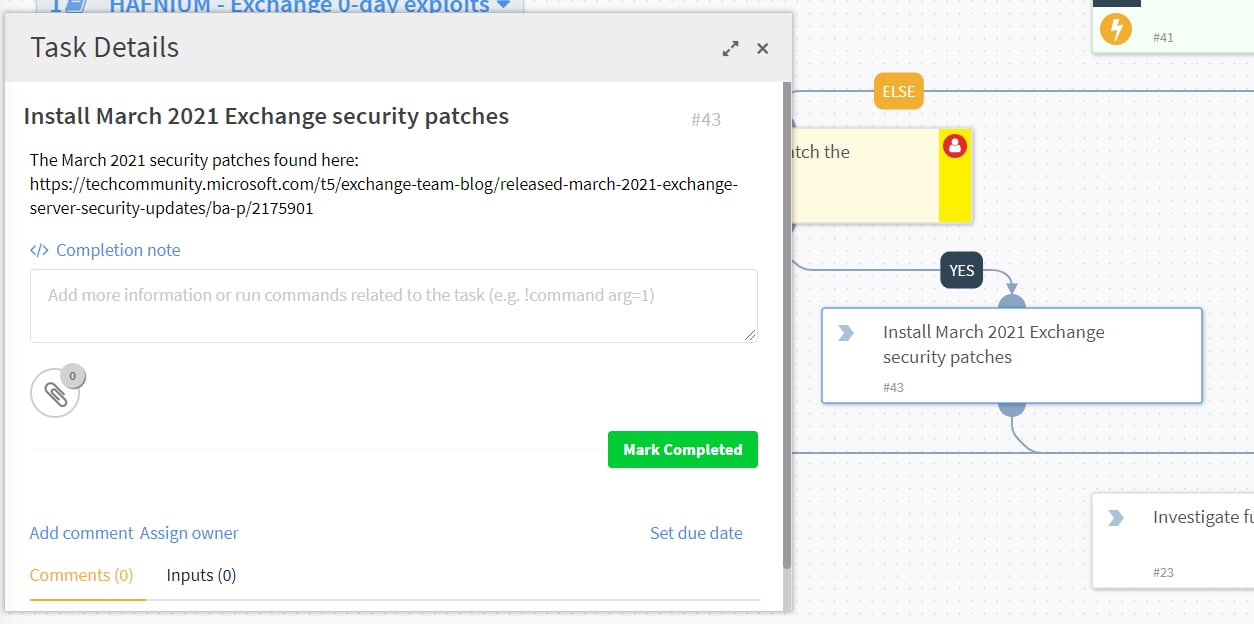
The HAFNIUM - Exchange 0-day exploits Playbook task refers to the March 2021 exchange security patches as shown here
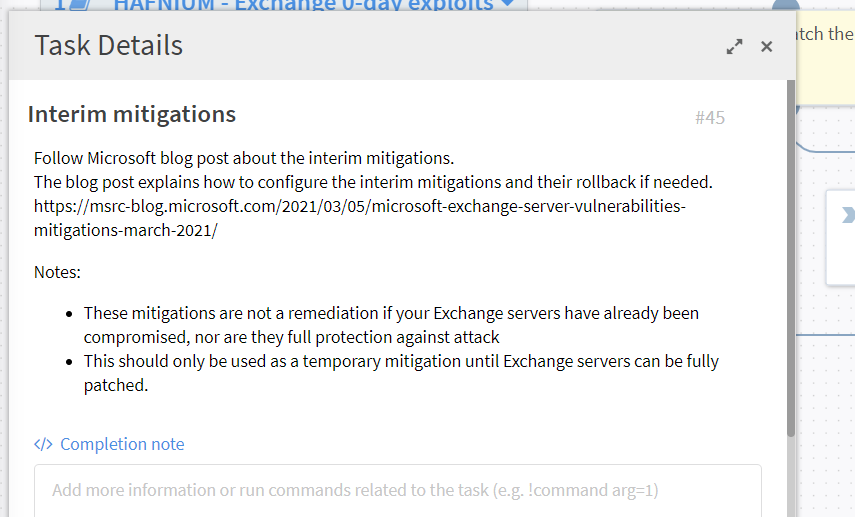
Cortex XSOAR Playbook task mentions the interim mitigation steps and points to the Microsoft blog.
Conclusion
With the help of the HAFNIUM - Exchange 0-day exploit playbook and Cortex XSOAR core capabilities and integrations, your SecOps and threat intel teams can save many hours of manual labor chasing down compromised Microsoft Exchange servers and trying to piece disparate sources of information together from multiple tools. Cortex XSOAR can automate the whole process of data enrichment and threat hunting by orchestrating across SIEM, firewalls, endpoint security and threat intelligence sources so you can quickly shut down HAFNIUM - Exchange 0-day exploits and limit its impact on your enterprise.
You can find the Rapid Breach Response content pack in our Cortex XSOAR Marketplace. Don’t have Cortex XSOAR yet? Try the free Community Edition today.
Related Blogs
Subscribe to Security Operations Blogs!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.