Playbook of the Week: MITRE ATT&CK—Courses of Action with Cortex XSOAR
Threat response can often be an ad-hoc, reactive process as alerts come in, especially if an organization doesn’t have standardized best-practices in place for certain instances. The MITRE ATT&CK framework was created to organize the real-world industry observations of threat actors into a standardized language of tactics, techniques and procedures (TTPs) to help organizations share information and recommendations which can be used to harden security programs. This is the current industry standard and most used framework for understanding and communicating how attacks work. With XSOAR’s powerful automation, your team can map incoming alerts and indicators to the tactics and techniques of the MITRE ATT&CK framework to take advantage of industry best practices for threat remediation. From there, they can leverage that knowledge to better understand the attacks against your organization.
What is MITRE ATT&CK?
Before we jump into the playbook, it’s important to understand what the MITRE ATT&CK framework is. MITRE ATT&CK stands for MITRE Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK). The MITRE ATT&CK framework is a globally-accessible curated knowledge base and model for cyber adversary behavior, as well as adversary tactics and techniques based on real-world observations. These behaviors reflect the various phases of an adversary's attack lifecycle and the platforms they are known to target. The ATT&CK knowledge base is used as a foundation for the development of specific threat models and methodologies in various different industries including the private sector, government, and in the cybersecurity product and service community.
Whilst the MITRE ATT&CK has various different uses to help organizations, the framework can be applied specifically to SOCs and Threat Intelligence to provide an industry approved and standardized threat response protocol.
- SOC Maturity Assessment: Similar to Defensive Gap Assessment, ATT&CK can be used to determine how effective a security operations center (SOC) is at detecting, analyzing, and responding to breaches.
- Cyber Threat Intelligence Enrichment: Enhances information about threats and threat actors. ATT&CK allows defenders to assess whether they are able to defend against specific Advanced Persistent Threats (APT) and common behaviors across multiple threat actors.
Introducing the Palo Alto Networks MITRE ATT&CK Courses of Action (COA) Content Pack
As you can imagine, understanding, consuming and mapping the tactics and techniques within the MITRE ATT&CK framework to incident response can be a time consuming and complicated task. Using the Palo Alto Networks Unit 42 MITRE ATT&CK — Courses of Action (COA) content pack available in the Cortex XSOAR Marketplace, security teams can automatically map their incident response to MITRE ATT&CK techniques and sub-techniques in an organized and automated manner. This pack provides both manual or automated remediation of MITRE ATT&CK techniques and kill chains.
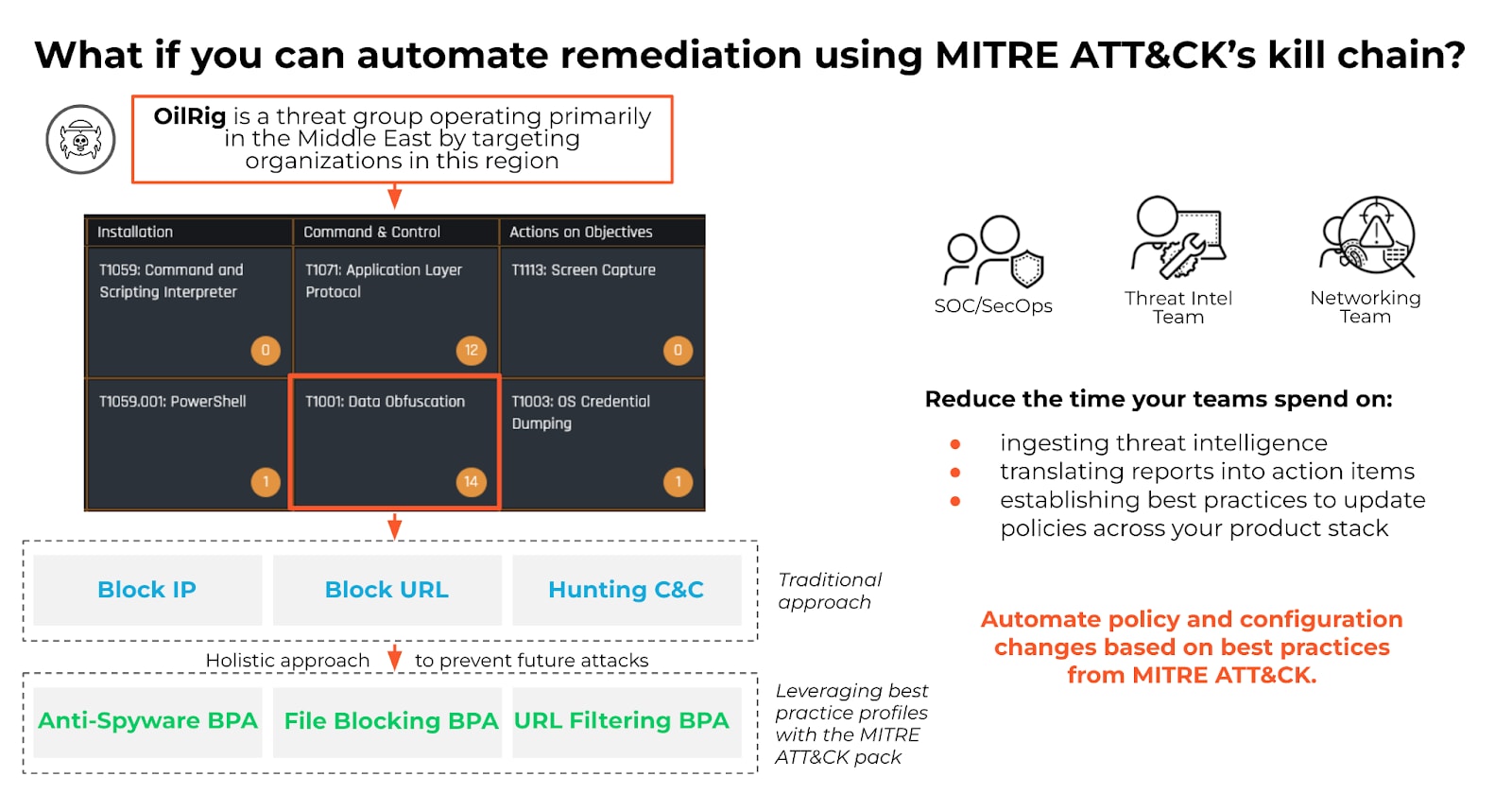
Image 1: MITRE ATT&CK Kill Chain
Focused on Indicators of Compromise (IOCs), the content pack also includes automated playbooks to block IOCs that have been predefined by your SOC as unsafe, reducing the overall amount of alerts without putting strain on your team. Every technique is mapped out-of-the-box, saving your SOC time and offering a more holistic approach to preventing future attacks.
In addition to aiding in SOC incident response standardization, the COA content pack uses MITRE ATT&CK techniques to provide threat intelligence insight using the Unit 42 feed and its Actionable Threat Objects and Mitigations (ATOMs) so your team gets playbook notifications as soon as there is a new threat actor report, with recommendations for immediate remediation action. While this step does require some manual action, the content pack makes the process easy and efficient. The security analyst simply needs to choose the techniques that are significant to their security program and run the prebuilt playbooks that leverage expert remediation workflows. This can be found in the built-in XSOAR MITRE ATT&CK dashboard (as seen below).
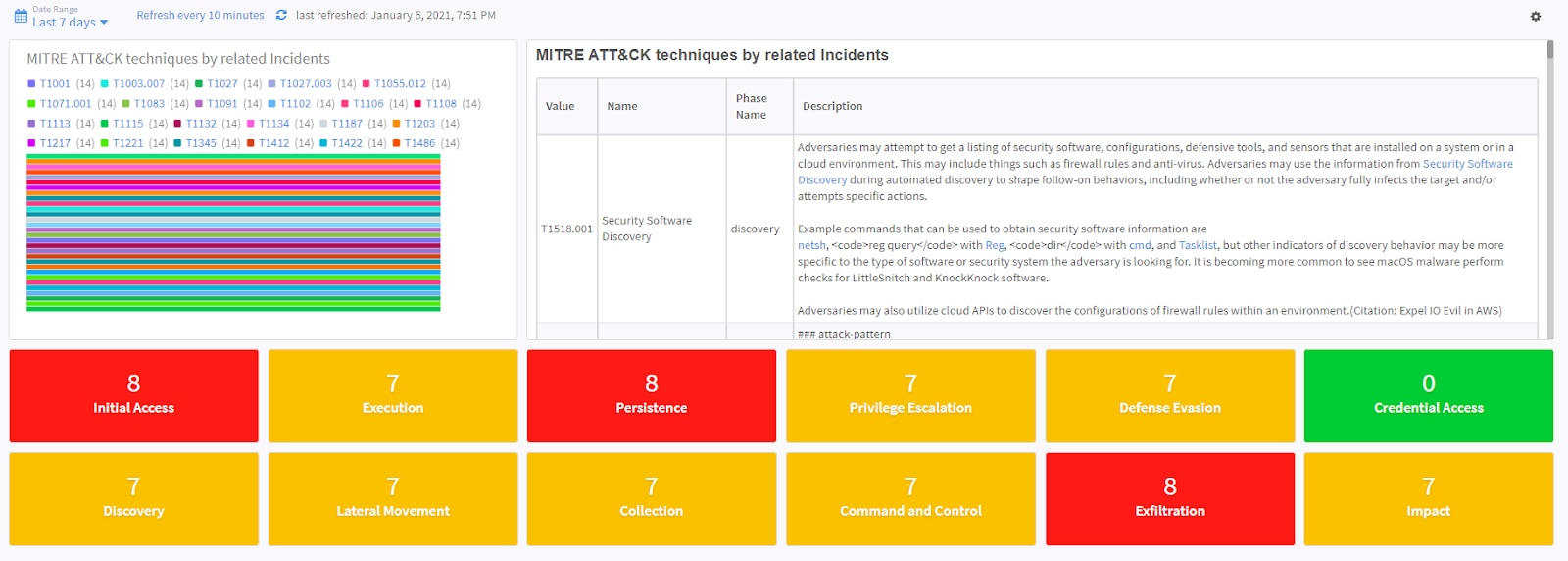
Image 2: MITRE ATT&CK Dashboard
Each technique is mapped out of the box into the specific Courses of Action that your organization needs in order to stay protected. You can also reduce the time your teams spend on consuming threat intelligence and translating the reports into action items, as well as sustain best practice policies for your security ecosystem.
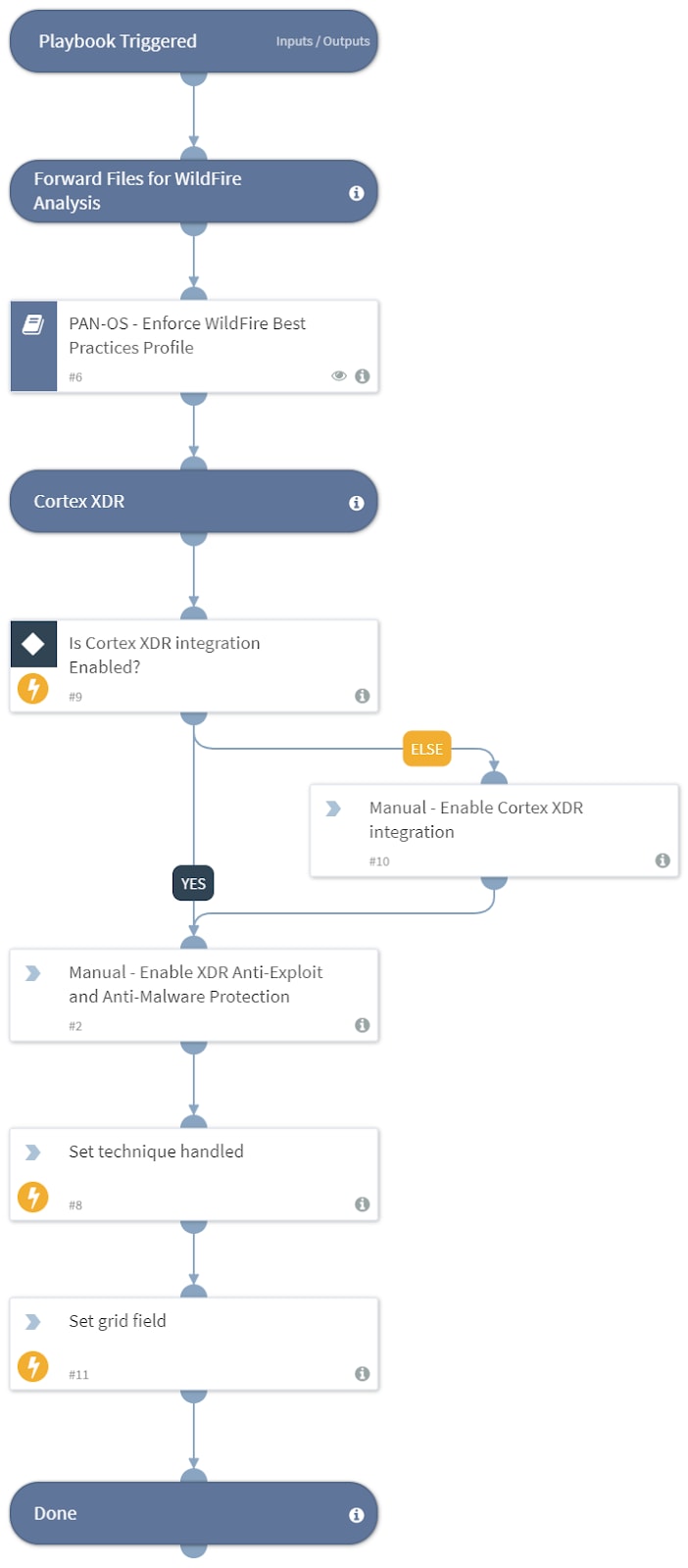
Image 3: MITRE ATT&CK—Courses of Action Sample Playbook
For more information on the MITRE ATT&CK Courses of Action Content Pack, refer to the developer article here.
Don’t have Cortex XSOAR? Download our free Community Edition today to test out this playbook and hundreds more automations for common use cases you deal with daily in your security operations or SOC.
Please Suggest Other Ideas or Vote!
If you like these ideas or would like to suggest other ideas, please collaborate with us through the Cortex XSOAR Aha page: https://xsoar.ideas.aha.io/ideas.
Related Blogs
Subscribe to Security Operations Blogs!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.