Playbook of the Week: Automate Anything with the Default Playbook
With Cortex XSOAR, the automation possibilities are only limited by your imagination (and API integrations). If you have explored our hundreds of out-of-the-box playbooks in the Cortex Marketplace but still need to build your own, consider starting with the Default playbook - the most widely used playbook in our Cortex Marketplace.
Enhanced and improved with Cortex XSOAR 8.2, the Default Content Pack consists of a playbook and layout which can be used together or separately for any kind of incident you’re ingesting or creating manually.
The Default playbook incorporates the core elements in any incident investigation while drawing from out-of-the-box content items included in the common packs, which means users do not need to install additional packs to start using it.
The Default Playbook Workflow
The playbook starts by extracting and enriching the details of the incident. If you are not yet comfortable with setting up field extraction rules for your incidents within XSOAR, this is a good option to have as the playbook will automatically extract indicators from all data associated with the incident, including information in unmapped fields.
The playbook also deduplicates similar incidents based on general incident metadata such as name, type, and other incident details. So deduplicating should work regardless of the type of incident you’re investigating. It also saves your team the need to create custom deduplication playbooks or pre-processing scripts to handle duplicates. In addition, duplicate incidents will be automatically closed and linked to the current incident, so they can be found easily from the layout.
If the incident includes a file hash and an endpoint, the playbook will attempt to retrieve the sample from the endpoint that triggered the incident. In addition, it searches for the hash on other endpoints to locate additional infected endpoints.
If the incident includes a file or a file was retrieved during the execution of the playbook, it will detonate the file and extract indicators from it. Additionally, suspicious URLs are also detonated in sandbox integrations. It then enriches all the indicators that came with the incident and additional indicators revealed throughout the investigation.
Lastly, the playbook determines the severity of the incident based on various factors - determining if the incident is a false positive or a true positive and remediates the incident by blocking malicious indicators. A summary report is then generated and is attached to the incident.
The Default Playbook Layout
The Default playbook layout is built in a manner that would work for all types of incidents. For example, the Incident Overview tab provides important information about the time of the incident, who is investigating it, related incidents, whether any task needs human input, why the incident was closed if it’s closed, and buttons to help with some quick actions related to the incident.
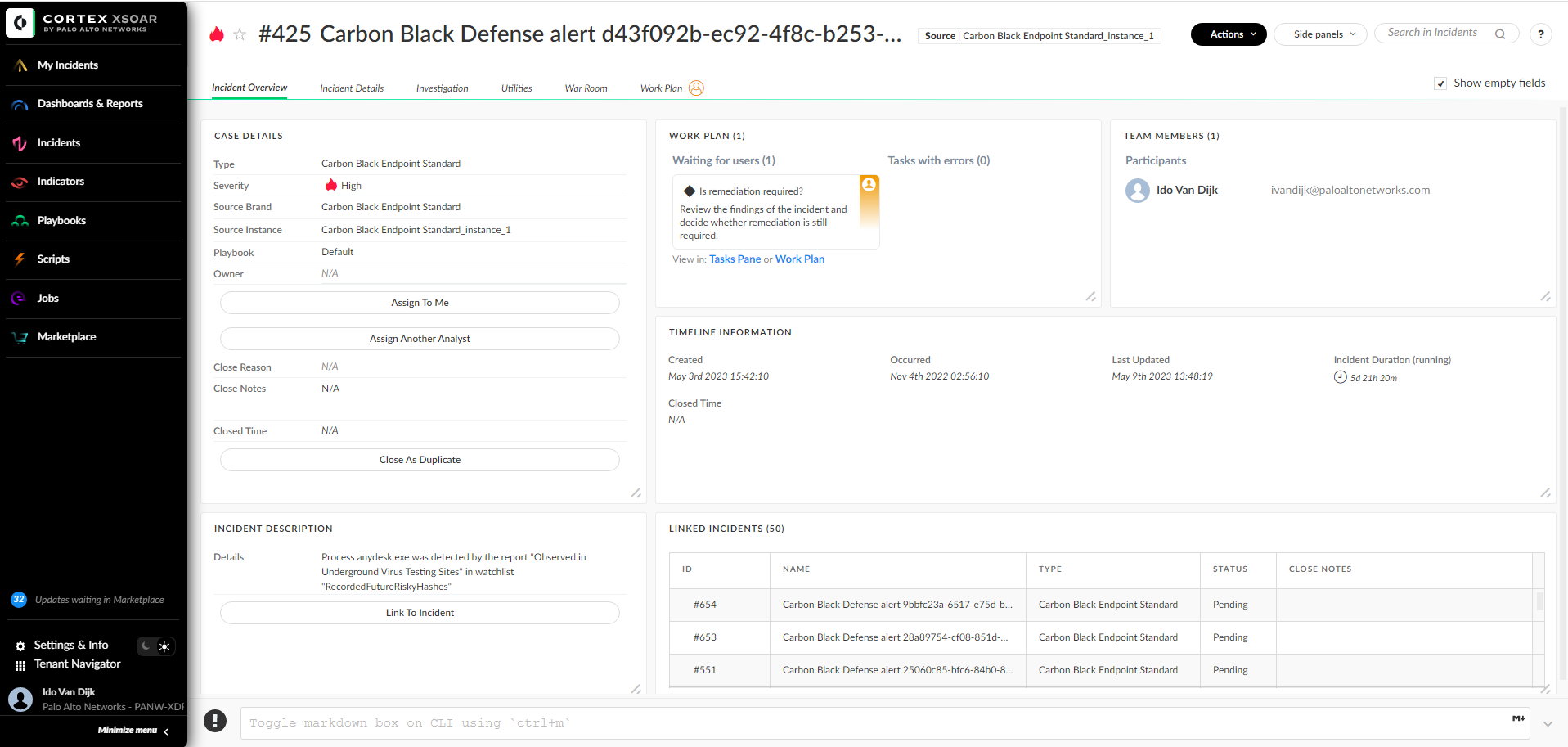
The Incident Details tab holds all the information about the incident. This includes mapped fields, unmapped fields, and files. Since these sections are dynamic, they will always present the most up-to-date information, and they do not require the user to do any editing for them to work out of the box for any incident type.
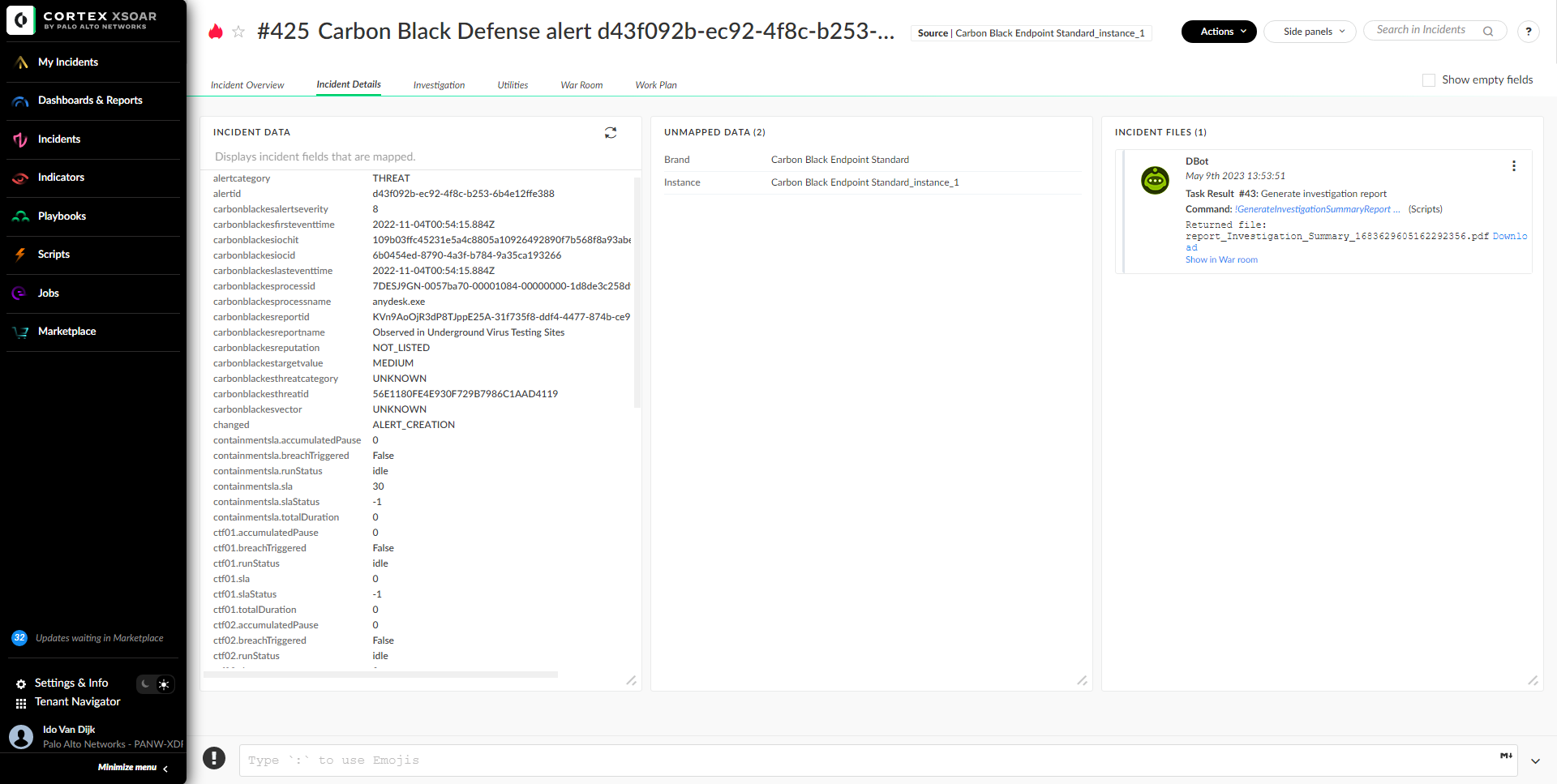
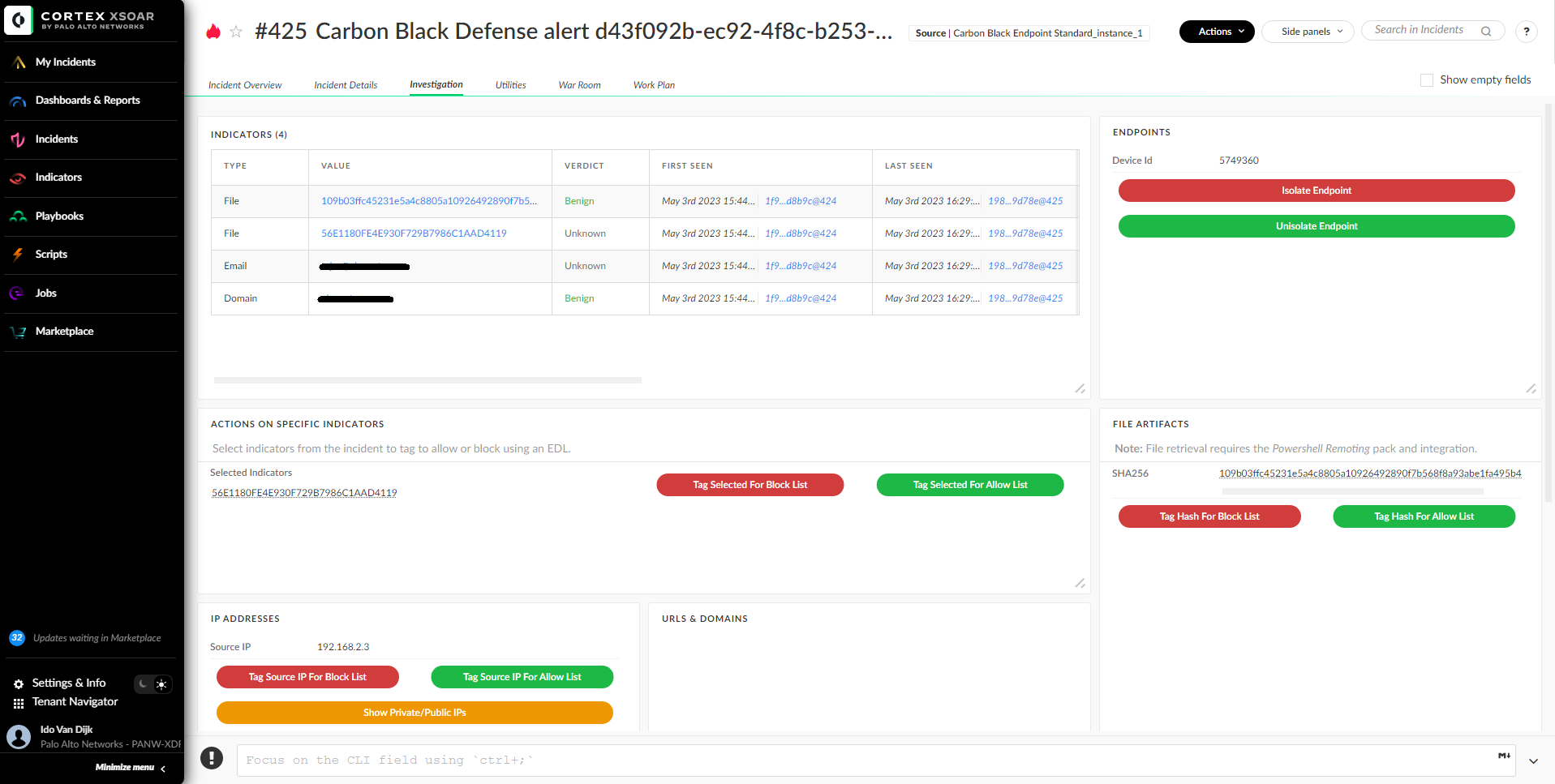
The Investigation tab lets users find information about the indicators and assets associated with the incident. The information on this tab can be populated by the setIncident task in the playbook or by incident type mapping. Data that is populated will be displayed as buttons for easy drill down into the data. The user can tag indicators for blocking or allowing said indicators using an External Dynamic List (EDL) and isolate or unisolate endpoints using quick action buttons. In addition, domains and IP addresses can be categorized and tagged as internal or external using an XSOAR list that holds the organization's internal IP ranges and domains/subdomains.
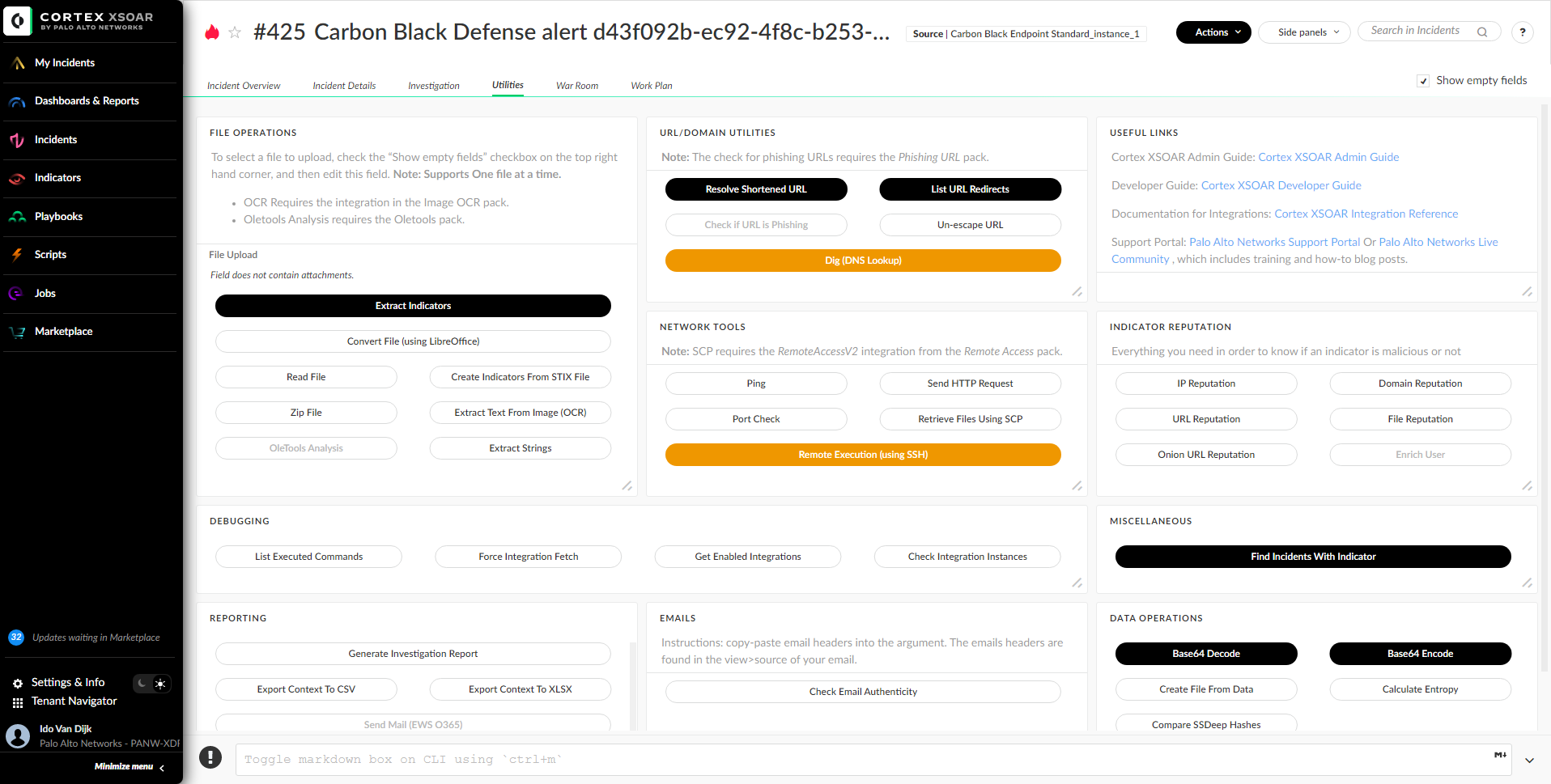
The Utility tab provides the most commonly used tools the analyst will need to investigate the incident - from file conversion scripts and network tools to debugging tools and documentation reference links.
To learn more about this playbook, check out the video and technical documentation.
Don’t have Cortex XSOAR? Download our free Community Edition today to test out this playbook and hundreds more automations for common use cases you deal with daily in your security operations or SOC.
Related Blogs
Subscribe to Security Operations Blogs!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.