Integrating Threat Detection with XDR in Google Cloud
Introduction
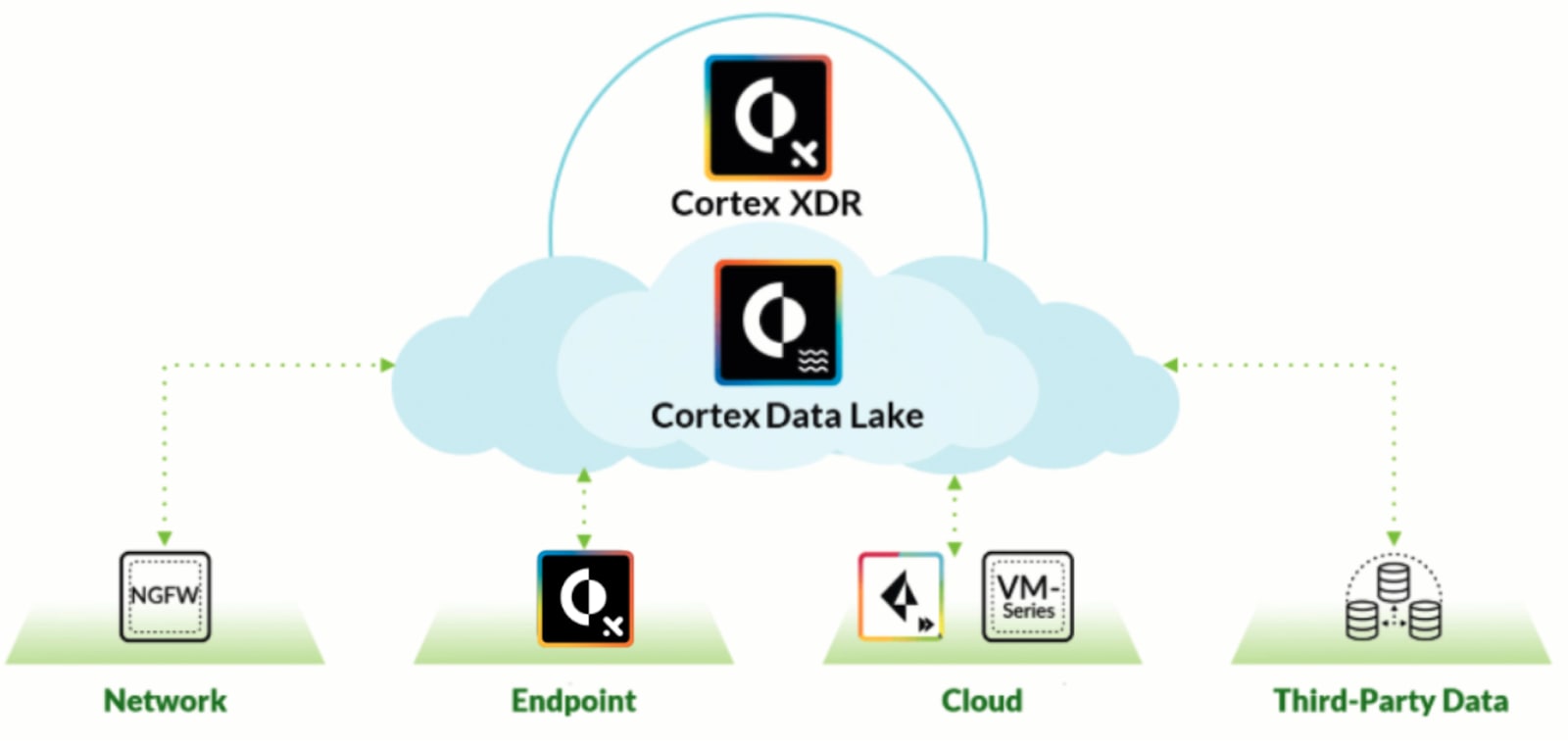
The recently announced Google Cloud IDS is a next-generation and cloud native intrusion detection service (IDS) that provides threat detection for intrusions, malware, spyware and command-and-control attacks. The native Google Cloud service – built with Palo Alto Networks threat detection technology – catches signature-based threats at the network level, gains complete Layer 7 visibility into intra- and inter-VPC application traffic, and helps you to meet compliance requirements with ease.
Until now, detecting threats in traffic between workloads within the trust boundary of a VPC has been a significant hurdle for security teams. Furthermore, taking action on those threats was even more challenging as information from hosts and endpoints was difficult to access at scale, preventing teams from quickly responding.
With the introduction of Cloud IDS, cloud network security teams finally have a native threat detection service for their Google Cloud environments. Further integration with the Google Cloud Logging service enables threat logs generated from the service to be sent to the Google Cloud Pub/Sub messaging service. Accordingly, if you use the Pub/Sub messaging service from Global Cloud, you can now send logs and data from your Google Cloud instance to Cortex XDR. This enables data and information from Google Cloud to be searchable in Cortex XDR, providing additional detail and context for threat investigations.
Cortex XDR delivers holistic protection by integrating all key security data to stop sophisticated attacks. It simplifies threat investigation by correlating logs from Cloud IDS to reveal threat casualties and timelines. This enables you to easily identify the root cause of every alert.
With the integration of this new IDS service and XDR application, you have the unique ability to perform immediate response actions from threat data. Beyond reactive behavior, you can look to the future and define indicators of compromise (IOCs), or behavior-based indicators of compromise (BIOCs) for detection and response around malicious activity.
How to configure the integration
Create a Pub/Sub topic and subscription
- Log in to your Google CloudGCP account.
- Select LoggingLogs > Logs Router.
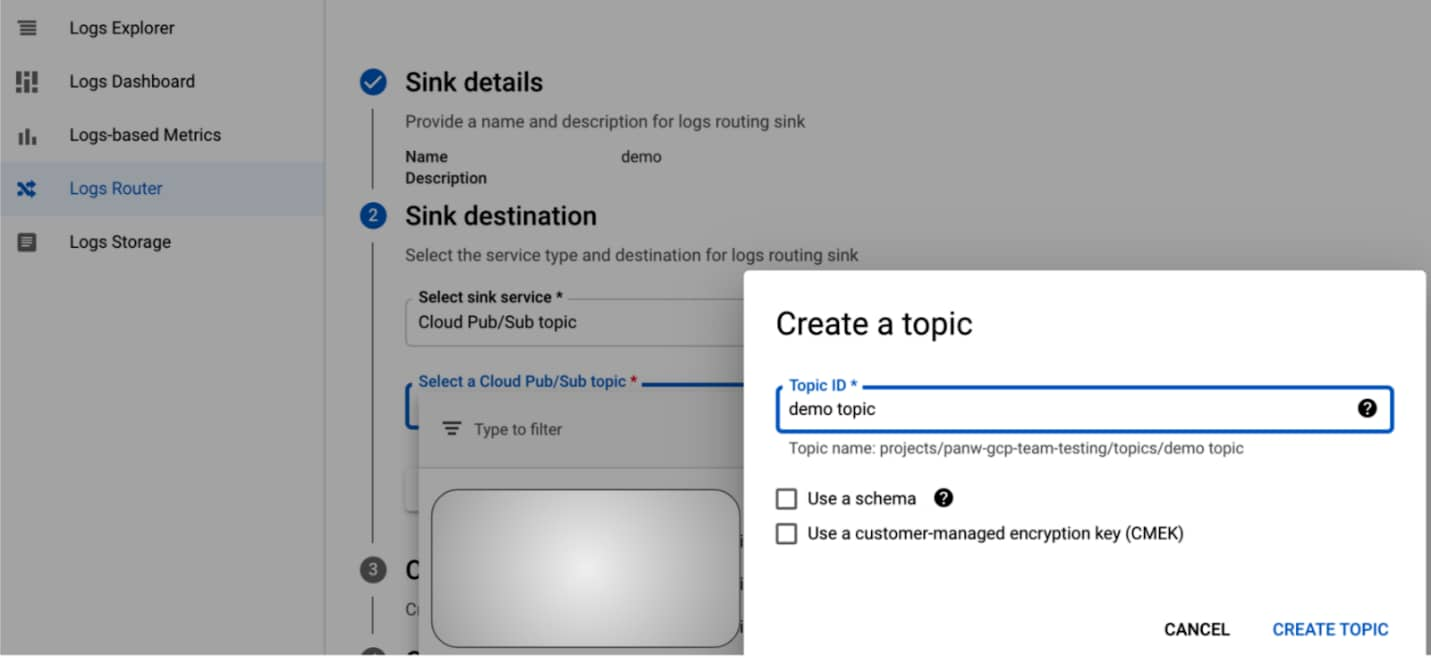
- Select Create SinkCloud Pub/Sub topic and then click Next.
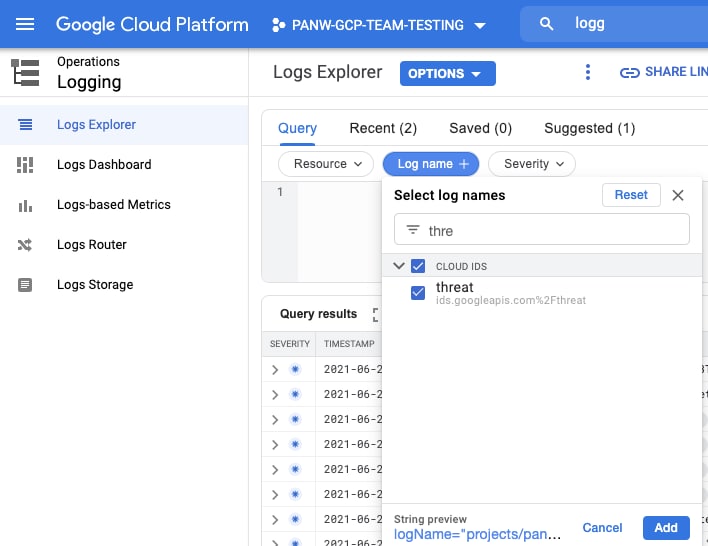
- To filter only specific types of data, select the filter or desired resource. You can set a filter to select Cloud IDS threat logs.
- In the Edit Sink configuration, define a descriptive Sink Name.
- Select Sink DestinationCreate new Cloud Pub/Sub topic.
- Enter a descriptive Name that identifies the sink purpose for Cortex XDR, and then click Create.
- Choose Create Sink and then Close when finished.
- Select the hamburger menu in G Cloud, and then select Pub/SubTopics.
- Select the name of the topic you created in the previous steps. Use the filters if necessary.
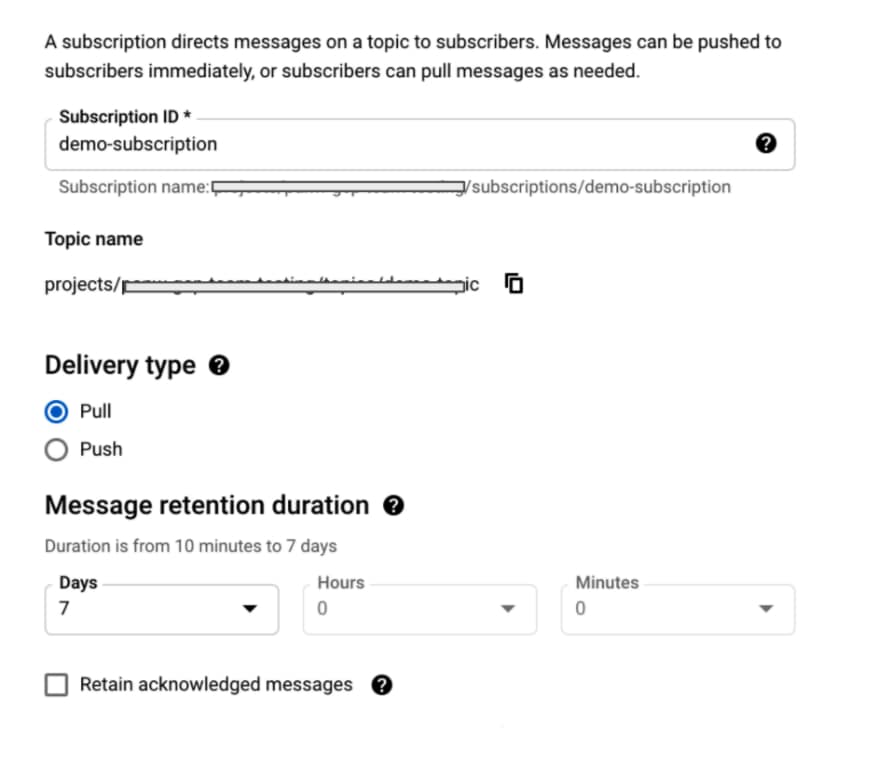
- Create SubscriptionCreate > Subscription.
- Enter a unique Subscription ID.
- Choose Pull as the Delivery Type.
- Create the subscription.
- In the subscription details, identify and note your Subscription Name.
Create a service account and authentication key
- Select the hamburger menu, and then select IAM & AdminService > Accounts.
- Create a Service Account.
- Enter a Service account name and then Create.
- Select a role for the account: Pub/SubPub/Sub > Subscriber.
- Click Continue > Done.
- Locate the service account by name, click the Actions menu identified by the three dots in the row for the service account, and then Create Key.
- Select JSON as the key type, then Create, and save to your local compute.
In Cortex XDR, set up Data Collection
- Select Settings Configurations > Data Collection > Collection Integrations.
- In the Google Cloud Platform configuration, click the here link.

- Enter the subscription and upload the json file you created for the service account. Subscription sample: projects/<project_name>/subscriptions/<subscription_id>
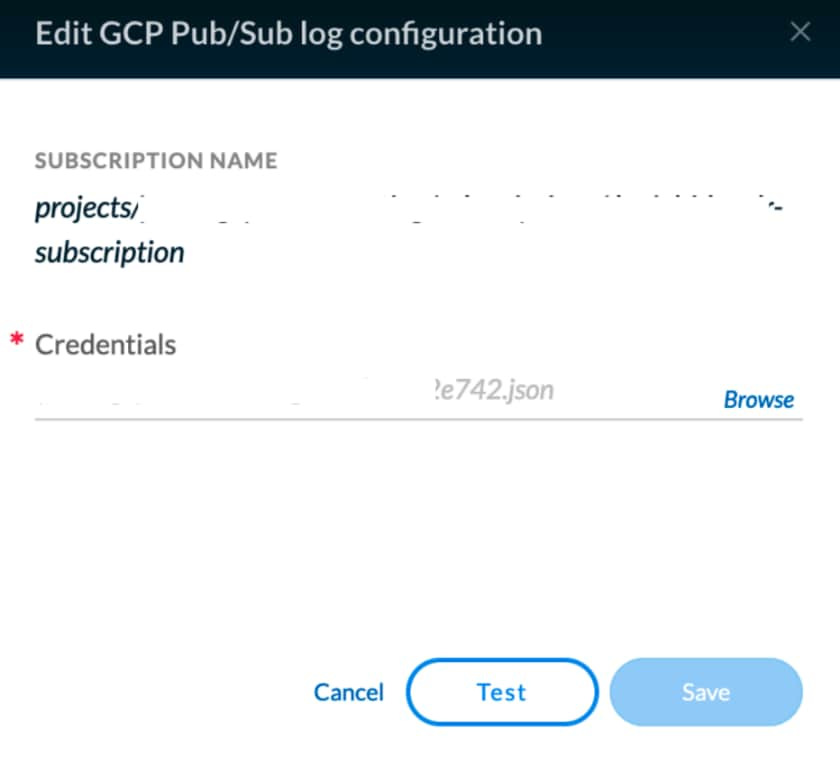
- Test the provided settings and, if successful, proceed to Enable log collection.
- Go to Menu, Investigation > Query Builder.
- Select XQL Search.

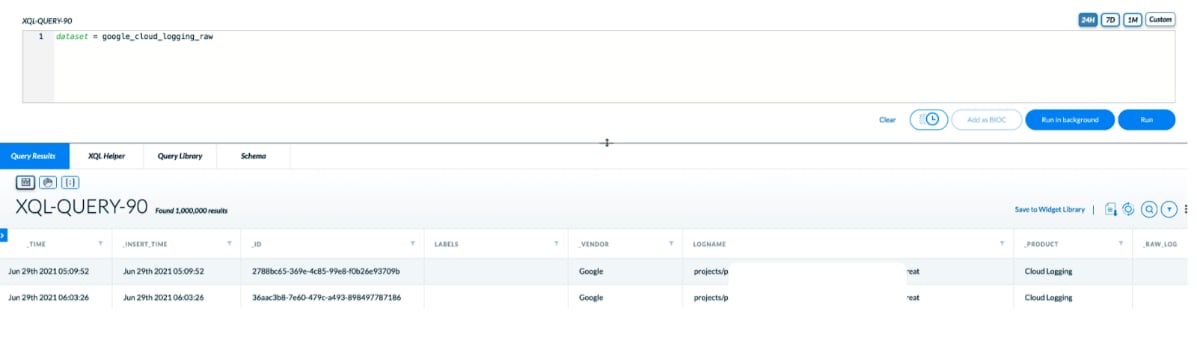
- Enter your query in the XQL-Query-90 box to get the logs from GCP Pub/Sub subscription. For example:
dataset = google_cloud_logging_raw
- You can further filter for more specific logs you want. For example:
dataset = google_cloud_logging_raw | filter logName = "projects/xxxxxxx/logs/ids.googleapis.com%2Fthreat"
Combining cloud threat detection inside a VPC with an integrated response solution provides a powerful option for securing additional layers of your cloud environment. This is a unique offering made possible by the joint vision, design and engineering of Google Cloud and Palo Alto Networks.
You can learn more about Google Cloud IDS and sign up for access to the preview or take a deeper look at how Cortex XDR can protect your cloud operations.
Related Blogs
Subscribe to Security Operations Blogs!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.