Open Source License Detection and Expanded Git Repo Scanning
A March 2021 report by Forrester, The State Of Application Security, 2021, showed that almost 99% of codebases it audited contained open source components. Further, as of 2019, the average codebase of those audited was 70% open source components. These open source libraries speed up development by relying on code contributed and vetted by the community. However, developers need to understand the licensing and security of these dependencies to provide proper attribution, use, and security.
With the latest release for Prisma Cloud, we have extended our platform with two new capabilities for advanced licensing detection and software composition analysis (SCA) via our command line interface tool, twistcli. These features provide developers and compliance teams the capability to understand the impact that licenses may have on application dependencies. Additionally, we have extended our SCA capabilities to let developers run scans locally or in custom environments, such as Jenkins. Meanwhile, security teams can view the legal requirements for a given license and understand potential effects on security posture in a single place.
Understanding Open Source License Compliance
Licensing for open source products is highly nuanced, which can make it difficult to understand. Some, such as "copyleft" licenses, require the release of source code, which is incompatible with many enterprise policies. Others, such as MIT, are less restrictive, but require attribution. SCA then is the capability to identify open source components used by a software service, for the purposes of security and compliance.
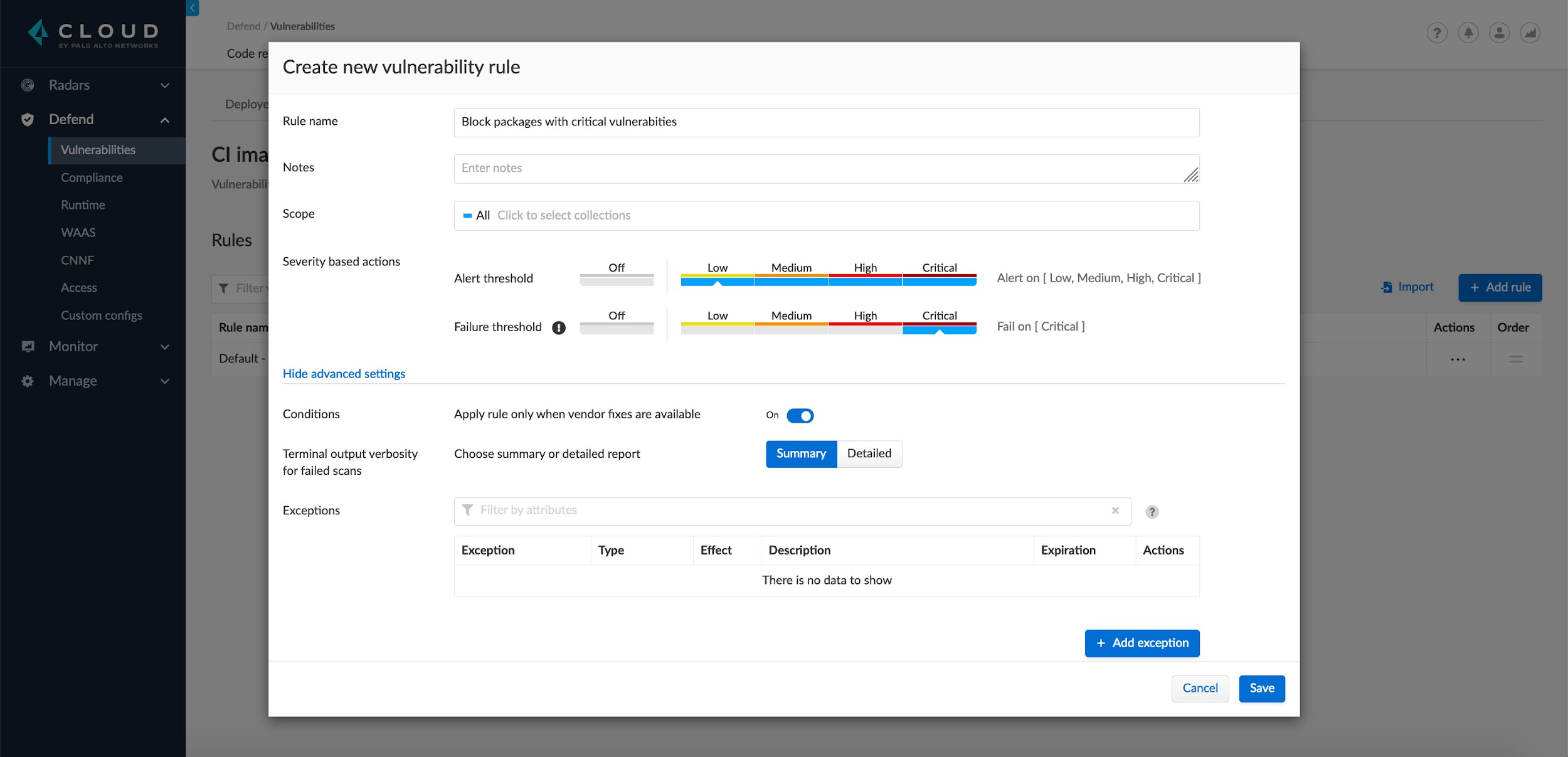
Prisma Cloud allows developers to identify open source packages in their services, the vulnerabilities and compliance violations within those packages, and helps identify packages that need to be updated. It's all achieved using plugins with developer tools such as interactive development environments (IDE) or continuous integration (CI) and source code management (SCM) tools.
Advanced Open Source License Detection in Prisma Cloud
With the launch of our advanced license detection capability, developers can use twistcli in combination with plugins for continuous integration (CI) and source code management (SCM) tools to scan their Node.js, Python, Java and, with the latest release, Go-based applications. Scans can be kicked off locally on-demand during development, or at regular intervals in pipelines and repositories.
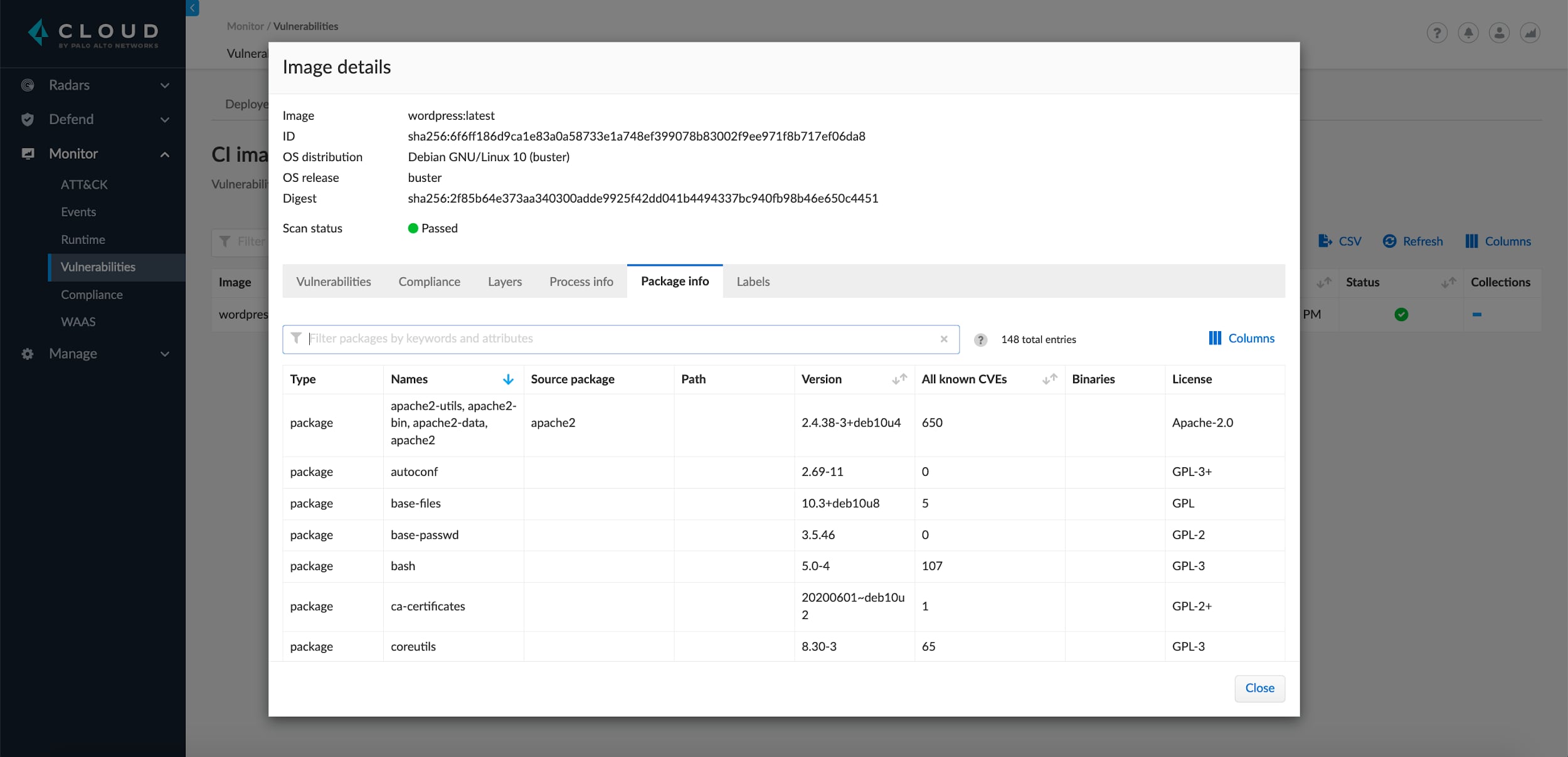
The result is clear visibility of the licenses in use. Understanding which licenses helps ensure proper use and attribution to avoid potential legal issues. Additionally, application scan results are sent to Prisma Cloud, where security and risk teams gain broad visibility of the licenses in use across their environments. There they can use controls to alert or block dependencies that contain certain licenses that don’t meet internal compliance requirements.
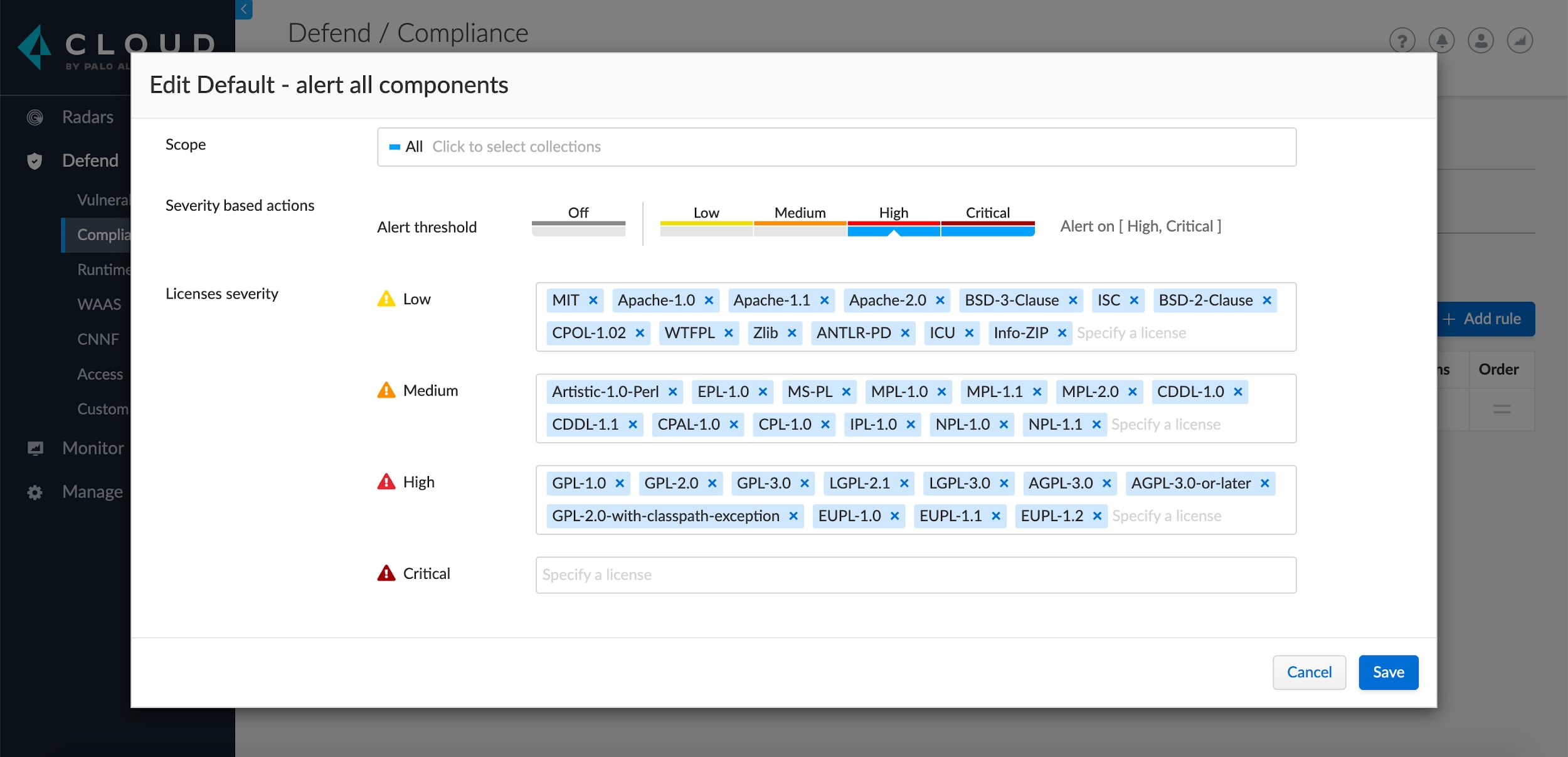
Extending Software Composition Analysis Coverage
In addition to licensing, this release extends the ways you can leverage existing SCA capabilities. Previously, our SCA capabilities only supported GitHub, however twistcli can now scan for vulnerabilities in dependencies in both git-based and non-git-based environments.
This capability shifts scanning activity further left, by letting developers run their scans locally or in the CI or SCM environment of their choice. Now developers won’t be surprised by security reviews, because they are empowered to find vulnerabilities in their own development environments.
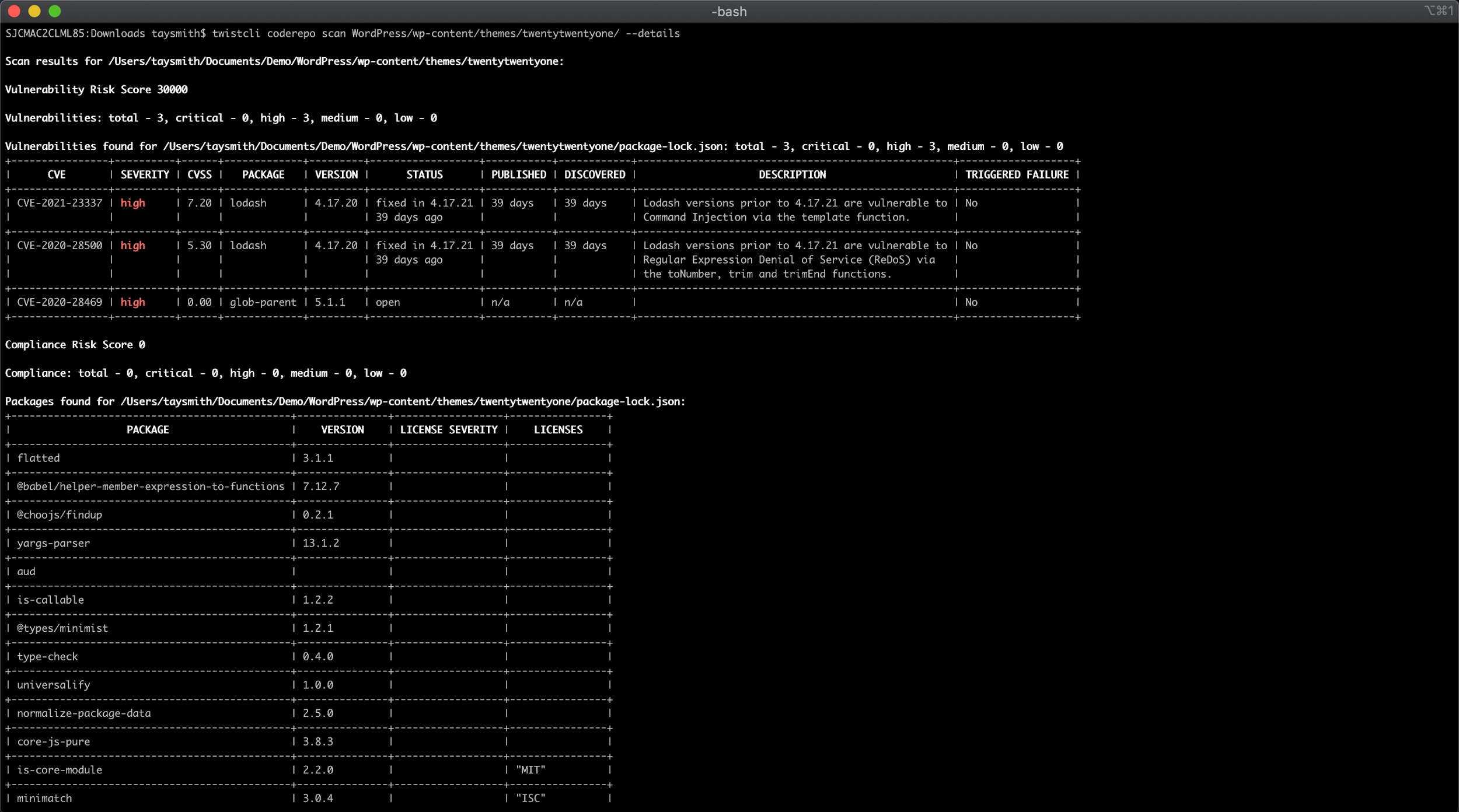
Just like the advanced licensing feature, all results show up in our UI. Central security teams can enforce guardrails and track the posture of codebases over time, providing developers earlier feedback, and increasing the likelihood of patching.
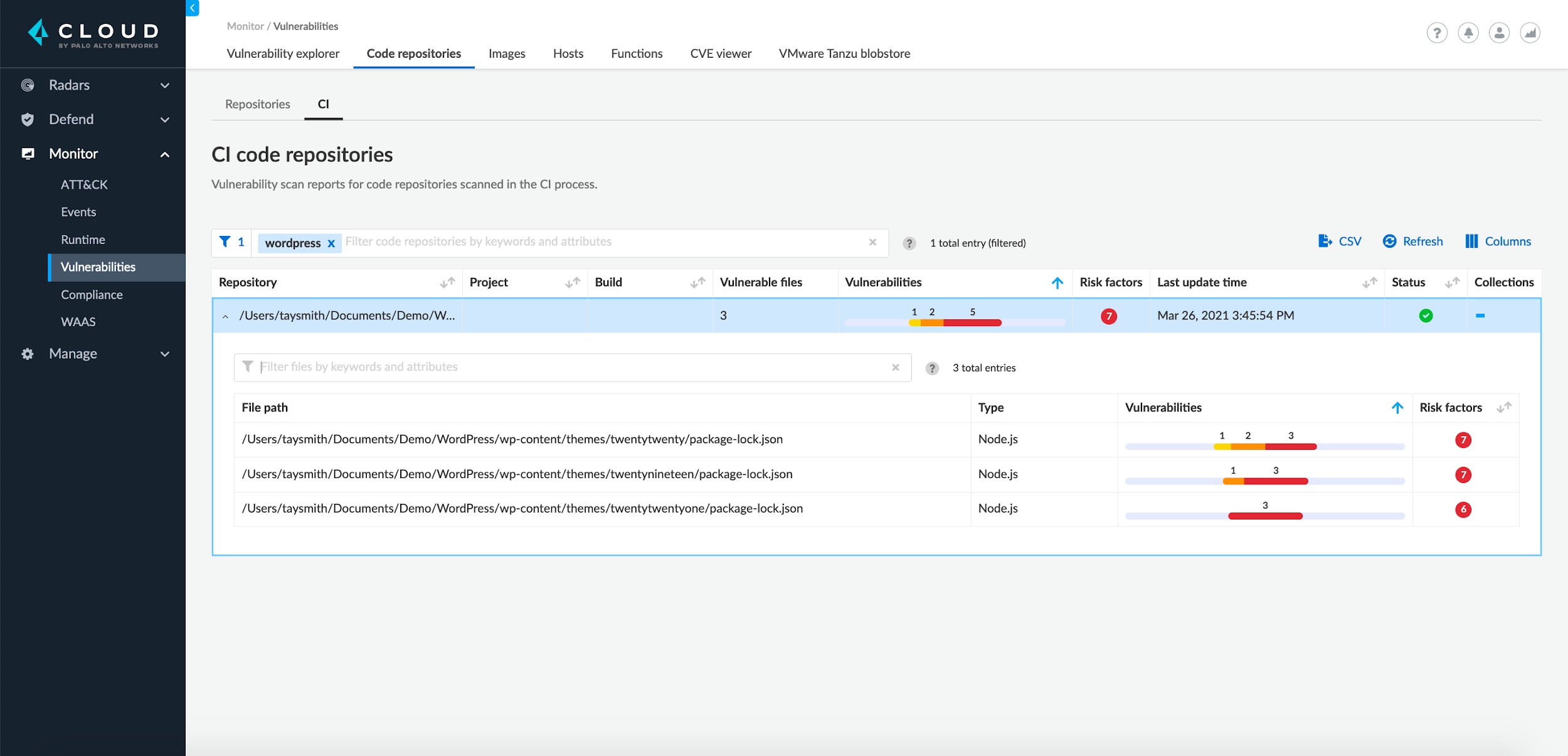
Empowering Developers With Security Capabilities
Both of these features help users improve their security and risk posture with the least amount of friction.
Developers can continue using their existing environments while gaining better insights into the licenses and vulnerabilities of open source packages. Security teams scale their efforts by providing automated feedback to the developers.
For the vulnerabilities that may still make it into production, Prisma Cloud defenders still protect your application from exploits. We cover your security from left to right, build time to runtime.
For more information about this and other recent features, check out our announcement blog.
Related Blogs
Subscribe to Cloud Native Security Blogs!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.