Take the IoT Guesswork Out of Your NAC Solution
The need to create value, reduce costs and optimize operations is driving enterprises towards massive digital transformation. Our Unit 42 IoT Threat Report found that unmanaged internet of things (IoT) makes up more than 30% of the devices on enterprise networks. One downside of IoT devices is that they pose immense cybersecurity risks as they are largely unregulated. 57% of these devices, which often ship with vulnerabilities, are susceptible to medium- or high-severity attacks—especially concerning when they are network-connected with unfettered access. Almost 20% of the organizations experienced an IoT- based attack in the last 3 years. To secure their networks from device-borne threats, such as preventing unauthorized devices from accessing the corporate networks, many organizations use Network access control (NAC) to enforce security policy compliance. A NAC solution’s fundamental goal is to ensure that the users and devices authenticate per policy before they get access to their authorized network resources. Device visibility is a prerequisite to achieve that goal. NAC solutions bring value to administer network access for the managed campus, data center, and infrastructure devices and appliances. But reigning in unmanaged and unagentable IoT and OT devices procured by different departments in the organization in your NAC strategy is an altogether different ball game and requires particular domain expertise. While some of the NAC solutions in the market provide rudimentary IoT and OT device visibility, the NAC policies and segmentation based on limited IoT and OT visibility, device context, and risk assessment can prove risky to organizations.
Don't get me wrong; I am in no way recommending replacing your NAC solution with anything else. But, since IoT/OT devices are unmanaged and in many cases do not have users associated with them, it can be tricky to use NAC to authenticate those devices for their designated resource access. Relying entirely on a NAC solution in controlling IT, IoT, and OT device access to the network can have trickling effects on an organization’s overall cybersecurity posture. Here are some examples of those trickling effects:
- Since IoT devices are needed business enablers, network teams have to allow them [ by adding them to the MAC Authentication Bypass (MAB) list] and give access without thoroughly understanding their risk posture and assessment.
- A continual need to update the IoT “allow list” is another operational and security nightmare. Updating is a manual process. Over the years, with employee turnover, the allowed list of IoT devices keeps growing without anyone knowing if all the IoT devices listed are still operational or retired.
- Outdated IoT allow list can also lead to MAC spoofing. Attackers can mask a long-forgotten IoT device’s identity as a threat vector to launch an attack without anyone noticing it.
- There is no visibility into device risk and threats; after they connect to the network. A NAC solution can not monitor IT, or IoT devices for threats post connect.
- NAC is not meant for threat identification and containment and requires third-party integrations for the prevention of known and unknown threats resulting in more operational processes to manage.
These observations are echoed and reflected in our Unit 42 IoT Threat Report as well. Lack of accurate visibility and classification has caused 72% of healthcare VLANs to mix IoT and IT assets, allowing malware to spread from users’ computers to vulnerable IoT devices on the same network.
This is where Palo Alto Networks comes in. We stitch together NAC and IoT to elevate your overall security posture and enable your digital transformation without causing any friction. We have built-in integration with NAC solutions so that you don’t have to spend time planning and implementing API-led resource-intensive integrations.
Palo Alto Networks’ IoT Security is the industry’s most comprehensive and only solution to use machine learning with our leading App-ID technology and crowd-sourced telemetry to profile all IoT, OT, and IT devices for discovery, risk assessment, vulnerability analysis, anomaly detection, and trust-based policy recommendations. IoT Security accurately identifies and classifies all IoT and OT devices in your network, including those never seen before. IoT Security combines Palo Alto Networks App-ID™ technology for accuracy with a patented three-tier machine learning (ML) model for speed in device profiling. These profiles classify any IoT, OT, and IT device to reveal its type, vendor, model, and more than 50 unique attributes, including firmware, OS, serial number, MAC address, physical location, subnet, access point, port usage, applications, and more. IoT Security automatically and natively, cross-references with your NAC solution, updates the NAC with broad and deep IT and IoT device visibility and risk context, and eliminates the need for error-prone manual upkeep of MAB/allow lists.
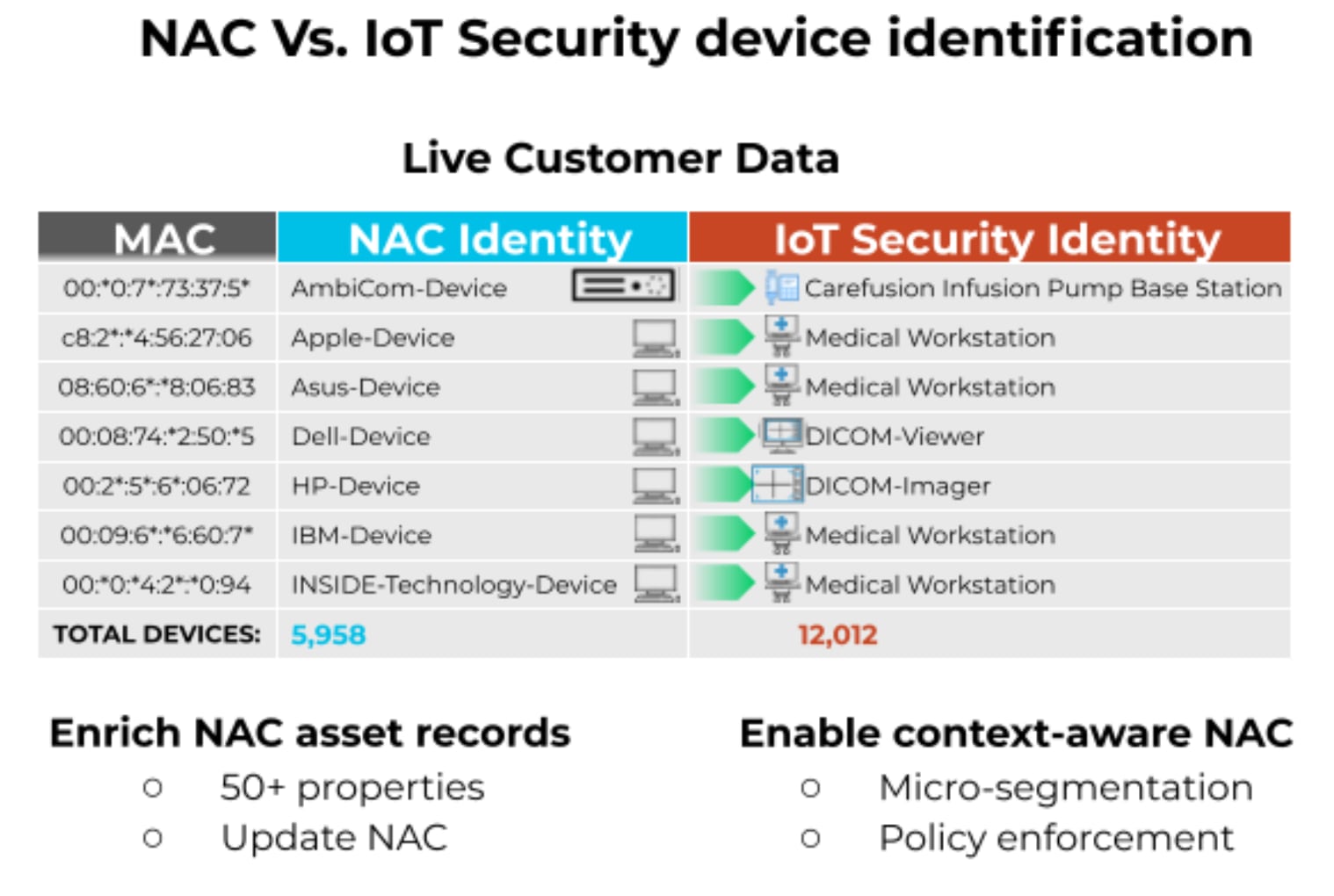
And you don't have to take our word for it. Here is a sample of how IoT Security takes the IoT guesswork out of your NAC solution. The following data is from an actual customer implementation. Just knowing the device vendor name for a device is not enough to create security policies. Would you assign the same network segment with access to the same resources to both an HP server and an HP DICOM imager? The answer is “definitely no.”
IoT Security also shares extensive risk assessment with policy recommendations for your NAC to easily implement trust-based controls. The before “IoT Security" scenario that involved multiple steps in identifying IoT devices, comparing behaviors over time, creating policies manually, requiring integrations for enforcement is now after the “IoT Security” scenario all automated and enforced with just one click.
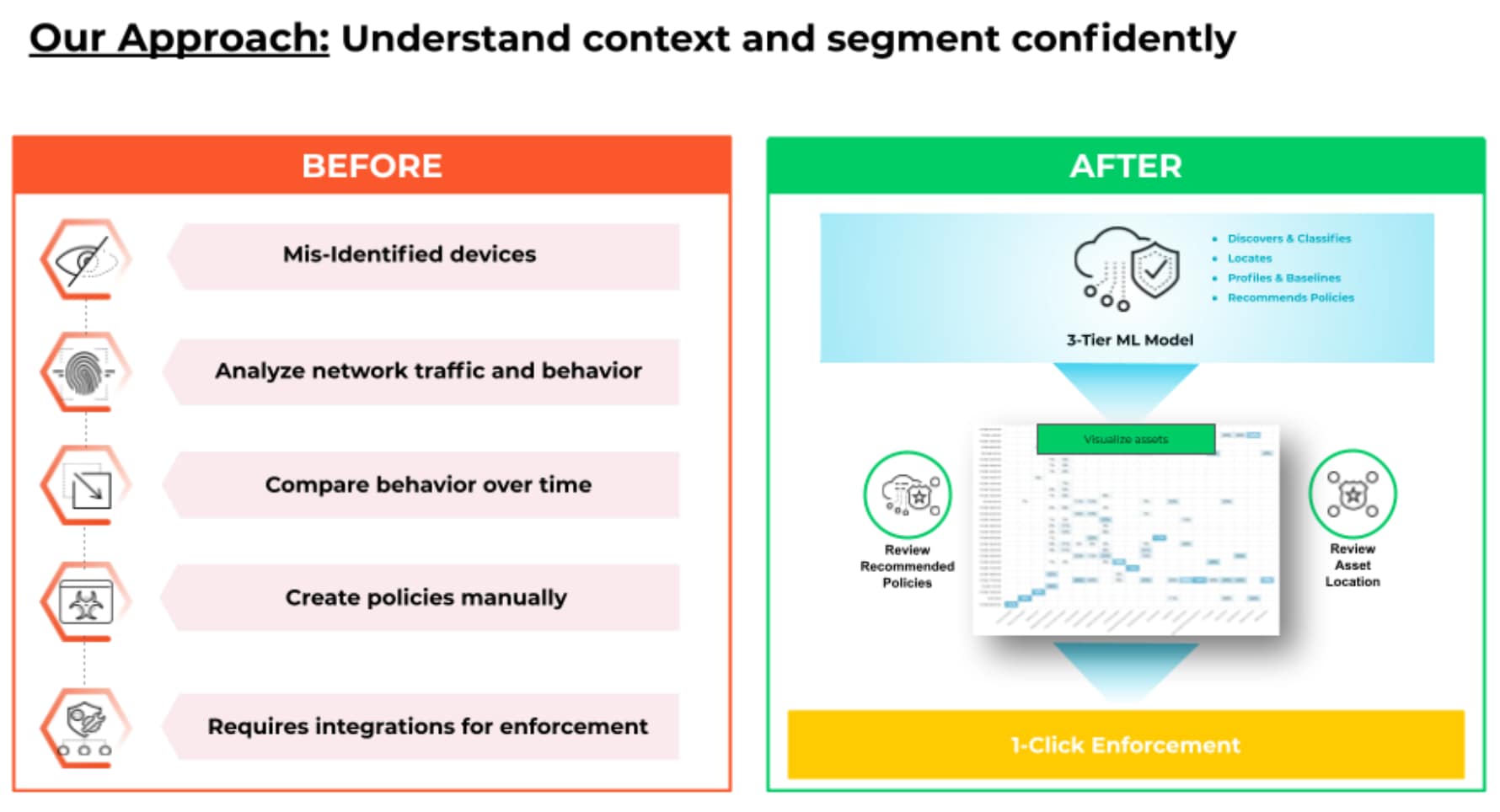
To sum up, Palo Alto Network’s IoT Security enhances your NAC as follows:
- Shares device profile and risk information with NAC to create the "zero trust" segmentation policy.
- Provides IoT device context such as device’s network placement and communication patterns and provides the visualization to accelerate segmentation design, planning, and deployment.
- Triggers NAC to quarantine a risky device in real-time based on a security alert from IoT Security.
You can now trust your NAC-guided “zero trust” policy implementation and segmentation, knowing that IoT Security from Palo Alto Networks powers your NAC.
Read our IoT Security Solution Brief to learn more.
Related Blogs
Subscribe to Network Security Blogs!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.