Modernize Your Infrastructure Management by Removing IoT Blind Spots
Market forecasts suggest that by 2030 around 50 billion Internet of Things (IoT) devices will be in use worldwide, creating a massive web of interconnected devices spanning everything from connected google glasses to office cafe appliances.
The lines between the corporate and public networks are already blurred with the“work from home” trend and the shift to cloud environments, and this is only compounded by the massive influx of IoT - your traditional perimeter is already becoming a relic of the past.
Most organizations are still relying on traditional infrastructure visibility solutions to enable IT and Security, a great example of this is Network Access Control (NAC). NAC is good for profiling managed users and devices to minimize the network security risk but has limited visibility into the unmanaged and unagentable IoT and OT devices. Since it uses visibility as an enabler for enforcement, accurate discovery, identification and context of all devices including burgeoning IoT and OT devices become critical to make sure that your network is segmented properly and their associated security risks are reined in.
Given these macro trends, do you think you are prepared for the risk of unmanaged devices? Can you segment your network confidently? Does your security team get device details so they can prioritize and make decisions? Are you detecting new devices as they are added to your network? Is your NAC enforcing the right controls on the right devices or are all devices created equal?
To answer these questions, one needs to apply the below foundational cybersecurity best practices to devices, not just users, apps and data.
- Visibility in to all devices (IT, IoT, OT) connecting to your network
- Segmentation and separation of different device types
- Granular policy creation to limit devices based on their role and function
- Controlling device access to the network to limit risk
As mentioned before, current NAC solutions are not fundamentally designed to discover modern devices to enable these best practices, they can however help with enforcement and segmentation. The prerequisite to applying segmentation is to understand the device's true identity and behavior. For this machine learning (ML) and artificial intelligence (AI) is the preferred approach to identify and profile devices, even those not known before. ML/AI is no longer a next-gen technology for us—it is here and available. We have coupled ML with the largest crowdsourced pool of big IoT device data to identify devices quickly, accurately, and to understand their behavior- what, why and where it is trying to connect. This analysis produces accurate device information and recommends policies to enforce control specific to that device and its placement on your network, informing NAC, and IT/security teams to make decisions when the time comes. For example, imagine a scenario in healthcare wherein a newly FDA approved DICOM imager is purchased by the clinical department. The security team uses NAC visibility to identify it as only a “HP device”, but with Palo Alto Networks’ superior IoT device visibility, the same HP device is identified as an HP DICOM Imager and goes a step further to show what this device is communicating with. Palo Alto Networks IoT Security solution compliments and enhances NAC policies and implementation by providing additional visibility and context across all traditional IT and modern day IoT and OT devices. This combination results in elevating your overall security posture.
The combined use of these advanced technologies also comes in handy when a device type is used for multi purposes. A great example is Apple iPads. People and organizations are coming up with innovative ways to use iPads. Retail industry is using them as a form filler, as an edge credit card processing device, or even to look for customer’s profile data. Even if a NAC identifies the device as an Apple iPad, not knowing the behavior would still result in placing the iPad device in the wrong network segment causing customer transaction disruption. But Palo Alto networks can again enhance the NAC policies by sharing extensive details on the iPad device and its behavior thus helping NAC to segment the device accurately without causing business disruption.
Palo Alto Networks is the only solution in the market today that helps you protect every IT, IoT and OT device on your network, even unknown ones with industry’s most comprehensive IoT Security solution delivering ML-powered visibility, prevention, and enforcement in a single platform.
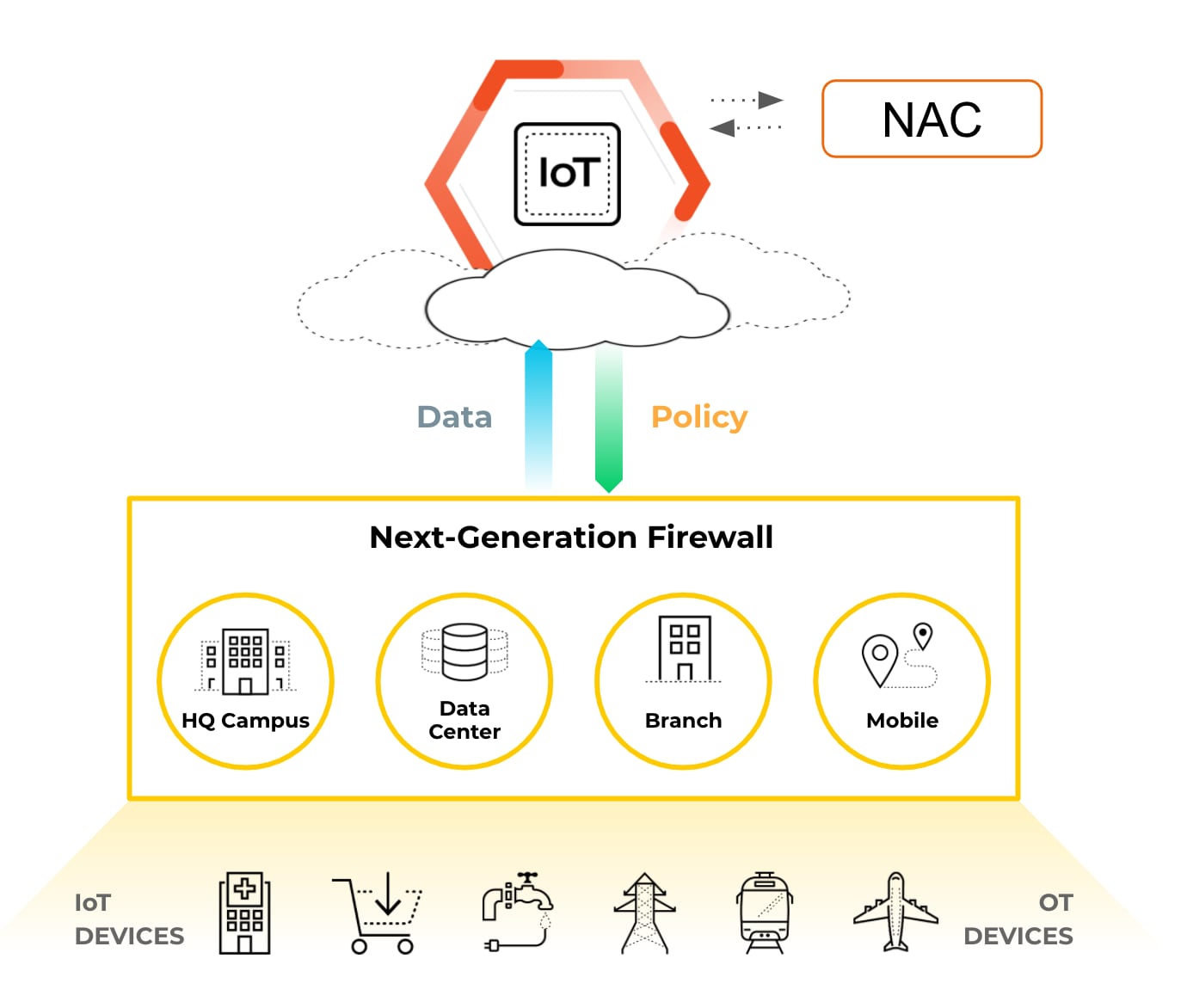
Palo Alto Networks is revolutionizing the IoT security industry by delivering a cutting edge and yet a simplified holistic solution with security at its core. We have delivered best-in-class IoT Security that makes your NAC smarter. It natively shares IT, IoT and OT device information with your NAC, provides policy recommendations and is effortless to deploy with just a simple SW subscription. The IoT Security solution is delivered from the cloud that can be deployed across any architecture or any sensor or enforcement point across hardware, software and cloud. The whole solution will scale linearly for you. Our cloud delivered model provides new innovations and threat detection techniques with no customer operational impact.
Securing your network with NAC from IoT threats is like navigating across a maze of unknown and unmanaged devices with a compass. Palo Alto Networks is the modern day GPS that will automatically navigate through risks and protect every IoT device on your network!
Read for more information on IoT Security from Palo Alto Networks.
Related Blogs
Subscribe to Network Security Blogs!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.