Multi-Extortion Techniques: Data Theft and Harassment on the Rise
Today’s ransomware gangs are constantly evolving their tactics to pressure organizations to pay ransoms. These tactics often use multi-extortion techniques. Based on extensive research from the Unit 42 threat intelligence and response teams, the 2023 Unit 42 Ransomware and Extortion Report exposes how active ransomware groups are increasing the pressure on targeted organizations.

Our findings highlight that ransomware now involves more than encrypting files. This means that the traditional advice of maintaining backups is no longer sufficient. Organizations need to be prepared for the added extortion techniques and pressure used by modern-day ransomware gangs, which requires a more in-depth incident response plan to achieve resilience.
The State of Ransomware and Extortion

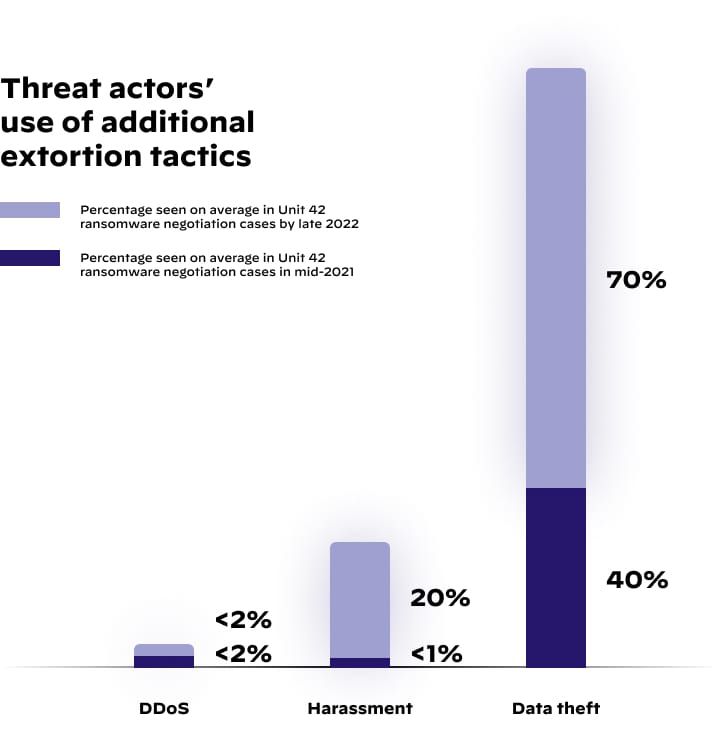
In late 2022, threat actors engaged in data theft in 70% of Unit 42 ransomware incidents on average, compared to about 40% in mid-2021.
Ransomware incidents extend beyond just stealing data. Unit 42 has also observed an increase in harassment as an extortion technique. During a period of 18 months, from May 2021 through October 2022, harassment as an extortion tactic grew from an average of less than 1% of Unit 42's monthly ransomware cases to a monthly average of approximately 20%.
Key Takeaways from The 2023 Unit 42 Ransomware and Extortion Report
Among the extensive research and analysis in the report, there are three takeaways that stand out. These takeaways are related to the way the ransomware landscape is changing, how organizations are responding, and what the future might hold as security and attack tactics evolve.
Willingness to Pay the Ransom Is Going Down
Ransomware has been around for over 15 years and has grown in popularity over the last few years. This growth in ransomware attacks has caused organizations to pay attention and take actions to protect themselves. Organizations have improved their ability to create and recover from backups, especially given redundancy capabilities in the cloud.
The cyber insurance industry has also increased the level of scrutiny on organizations in order to qualify for insurance coverage. In general, the cyber insurance industry will only insure an organization that shows evidence of data backups.
Multi-Extortion Is Increasing — Companies Are Harassed for Ransom
Victims’ willingness to pay for incidents that just involve encryption has decreased. In response, attackers have adapted and are changing tactics. They have realized that encryption alone might not be compelling enough to force an organization to pay a ransom. So, attackers will steal data first and then encrypt files. They then threaten to sell stolen data or make it public if an organization does not pay the ransom.
If victims refuse to pay, attackers escalate to harassment, where they often target employees and customers.
Harassment Tactics
- Calling or emailing employees, customers, and even the executives' family members constantly
- Thwarting business deals and product launches
- Telling customers to leave
- Crashing websites
Preparation is key. Organizations that take additional steps to prepare for multi-extortion attacks will set themselves up for being a less tempting target.
Gangs Willing to Ransom Schools and Hospitals
Vice Society is the gang behind a recent attack at a LA school District. They have targeted at least 137 school systems and local governments since 2021. This group has demonstrated that no organization is off limits for their attacks, and they’re willing to hit victims wherever valuable data is held.
In the Los Angeles school district attacks, threat actors published student mental health records. In this situation, the gang aimed to make people's lives difficult. Schools are tasked with protecting a treasure trove of sensitive data, without the resources to keep it safe from attackers.
(For more on Vice Society, watch our discussion with Nasdaq TradeTalks.)
Our Advice to Leaders: Take a More Proactive Approach to Your Security Strategy
As threat actors continue to use various extortion methods to coerce organizations into paying, it is imperative to evolve your defenses. Your incident response plan needs to safeguard your organization’s reputation and to protect your employees or customers who may become targets.
Prepare a Playbook for Multi-Extortion
In an extortion incident, quick support from an Incident Response team and legal counsel is crucial. A comprehensive incident response plan with crisis communication protocols can help reduce uncertainty and clarify decision-making. The plan should also address how to handle employee and client harassment, and staff should receive ransomware awareness training.
After an incident, you should conduct a post-mortem assessment to ensure any remaining backdoors or indicators of compromise are removed to prevent follow-up attacks.
Help Ensure Complete Visibility via XDR Technology
To protect your organization from threats, it’s important to increase visibility in your environments. Endpoint Detection and Response (EDR) tools provide effective protection against endpoint attacks, but an Extended Detection and Response (XDR) solution, offers a proactive approach to threat detection and response.
With XDR, cybersecurity teams can prevent threats in multiple ways:
- Identify hidden, stealthy and sophisticated threats proactively and quickly.
- Track threats across any source or location within the organization.
- Increase the productivity of the people operating the technology.
- Get more out of their security investments.
- Conclude investigations more efficiently.
Implement a Threat Intelligence Program
With a chartered, funded and staffed threat intelligence program in place, you can learn about the tactics, techniques and procedures (TTPs) that attackers use. This program can provide your defenders with specific indicators to monitor for the latest TTPs to quickly detect and mitigate a ransomware attack. Unit 42 consultants can help design or enhance a threat-informed security program based on lessons learned from our incident response investigations.
Proactively Manage and Reduce Your Attack Surface Inventory
At least 75% of ransomware attacks and breaches fielded by Unit 42’s Incident Response teams result from attack surface exposures. The key is to continuously identify, monitor and manage all internet-connected assets, both internal and external, for potential attack vectors, exposures and risks.
Cortex Xpanse’s Active Attack Surface Management can discover unknown exposures and provide contextualized results to prioritize findings and align security concerns with your organization’s critical assets.
Implement Enterprise-Wide Zero Trust Architecture
You can reduce the impact of cyberattacks by rapidly containing your attack surface and implementing an effective Zero Trust Network Architecture (ZTNA). A refined version called ZTNA 2.0 creates layers of security, slowing down attackers and providing more time for detection and response. This makes an attacker’s job harder and increases the chance of proper threat containment and remediation.
Pressure Test Your Incident Response Plans and Programs
Regularly reviewing, testing and updating your incident response plans improves your ability to respond to attacks quickly. Conducting incident simulation and testing exercises, as well as partnering with Unit 42 security consultants, can strengthen your organization’s preparedness and communication cadence. This will also improve the likelihood of early detection and containment, as well as identify opportunities for improving your overall security posture.
Get the Ransomware and Extortion Report
Get the full 2023 Unit 42 Ransomware and Extortion Report for the latest insights on multi-extortion techniques, including those that ransomware gangs are using to increase pressure on their victims. For an in-depth set of recommendations by Unit 42 incident responders, read our special publication, Mitigating Cyber Risks with MITRE ATT&CK. It includes both strategy and practitioner-focused recommendations, so you can put these insights into action.
Related Blogs
Subscribe to the Newsletter!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.