How to Balance the Zero Trust Journey with the Speed of the Mission
It's been over a year since President Biden signed the Executive Order on Improving the Nation’s Cybersecurity, and we see many federal agencies making significant progress on their Zero Trust journey. Some are well-positioned to accelerate their efforts because of investments in digital transformation, which include rebuilding and improving their security approach. But, even these federal agencies are feeling more pressure to speed their Zero Trust journey, following the January release of the federal Zero Trust architecture strategy from the U.S. Office of Management and Budget. The federal Zero Trust architecture strategy outlines aggressive Zero Trust implementation deadlines over the next two-and-a-half years.
To protect government networks, infrastructure and data from growing digital threats, we’re working with Booz Allen Hamilton to assist federal agencies with implementing a Zero Trust roadmap and transforming how their users securely protect their data in a way that’s tailored to the agency’s mission and unique needs.
Let’s explore the concept of Zero Trust and considerations for IT leaders in the federal space.
Zero Trust: A Complete Reevaluation of Security
Zero Trust is a strategic approach to cybersecurity, not a single product. It secures an organization by eliminating implicit trust and continuously validating every stage of a digital interaction. By adopting Zero Trust principles and architecture, organizations can build resilience into their IT networks and environments, simplify risk management, and improve operational efficiency.
“Zero Trust is becoming especially critical in distributed, multicloud environments, and IT leaders across government are starting to take a security-first approach to all parts of implementation and architecture,” explained Imran Umar, director of Zero Trust at Booz Allen. But, Imran cautions that Zero Trust isn’t a solution that you apply or a technology that you adopt. Zero Trust covers everything from policy to operations, allowing the approach to truly permeate an organization.
Applying a consistent, robust policy that secures users and data wherever they reside ensures overall safety from our digital society to our nation’s security. In order for any organization to strengthen the protection of its most critical assets, it must accept that a compromise or breach is not an if, but a when reality. They must focus on limiting the impact of that risk.
Ultimately, Zero Trust isn’t a “flip-the-switch” effort to enhance cybersecurity. It will take time. And in truth, it’s a continual journey. The good news is that your agency can start implementing the Zero Trust process anywhere, and you can use existing tools and capabilities to establish a starting line.
Where to Start Your Multiyear Zero Trust Journey
As an organization adopts additional and more diverse cloud and mobile technologies, the defined “perimeter” that is core to a traditional, perimeter-based, defense-in-depth strategy evaporates. Instead, the organization is left with a collection of many smaller surfaces to protect.
By extending current firewall policies to the edge to support cloud and mobile users, organizations can migrate to a new Zero Trust architecture more seamlessly. Palo Alto Networks helps organizations integrate and unify advanced security into their cloud infrastructure, so users don’t have to go through on-premises functionality.
Booz Allen’s Imran Umar recommends starting with a Zero Trust maturity assessment to understand the current state of your security and determine which key areas to tackle first. By conducting an audit of the tools and capabilities that your agency has now, then optimizing those products and solutions, you can jump-start your Zero Trust journey. If you have Palo Alto Networks Next-Generation Firewall, for example, turn on relevant features to get full visibility into users, devices and apps. Broad visibility is a must for implementing a Zero Trust strategy and best practices.
Many of our customers in the federal government are also currently looking at Palo Alto Networks Prisma Access SASE solution as an easy entry point into Zero Trust. We’re generally seeing increased interest throughout the federal government in adopting innovative solutions, like secure access service edge (SASE). More agencies are starting to shift away from a point-product perspective and adopt unified platforms that provide many services with reduced administrative overhead.
How to Balance the Move to Zero Trust with the Speed of the Mission
Having a clear roadmap for the Zero Trust journey and a maturity model to measure progress against is vital for federal agencies to help ensure continued leadership support for the journey. By leveraging the technical acumen of a combined Palo Alto Networks and Booz Allen Hamilton team, we can help agencies create both through a Zero Trust Professional Services engagement. We can help with discovery and asset identification, your first Zero Trust implementation, process improvement and more. A Professional Services engagement can help condense the timeline of your agency’s move to Zero Trust and provide several benefits:
- A repeatable and predictable security strategy.
- Significant risk reduction with fewer breaches.
- Higher confidence in security controls.
- Simplified operations through automation.
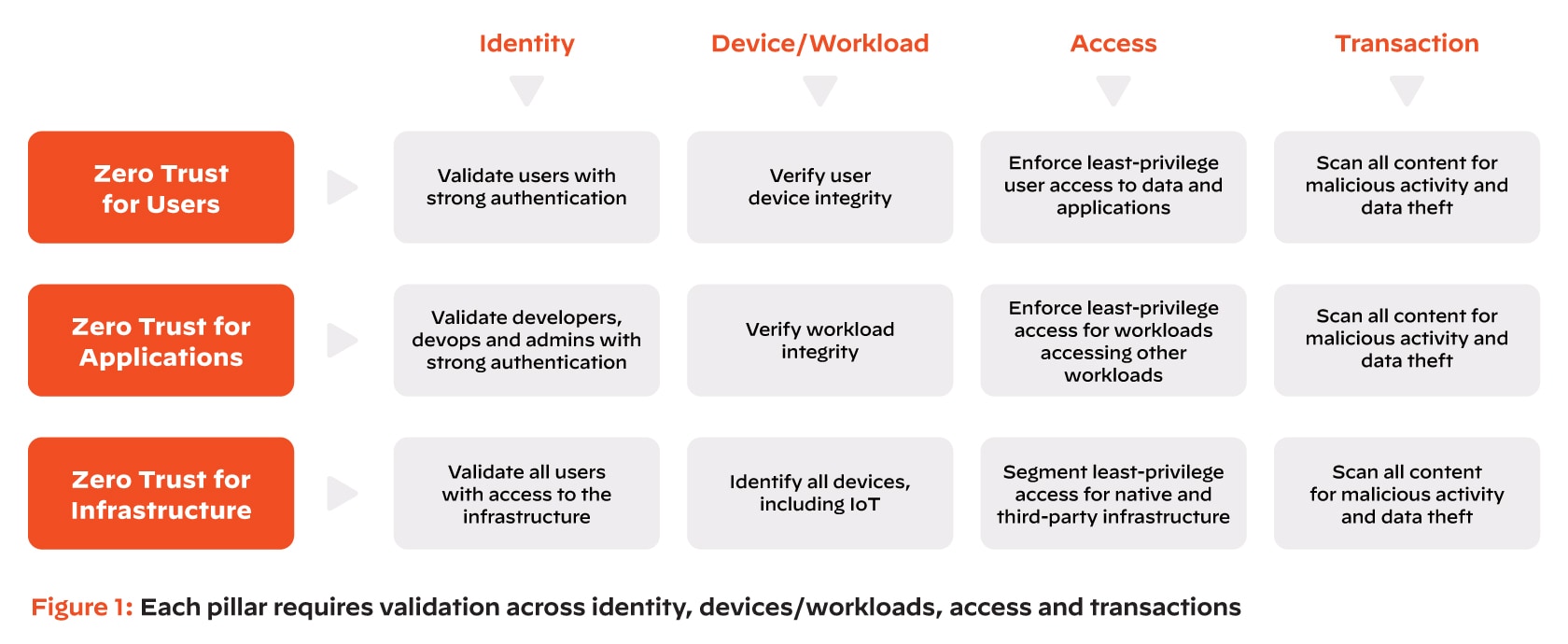
We often hear from the agencies we work with that they’re concerned about disrupting their speed, performance and mission assurance as they deploy Zero Trust. Separating the journey into three areas – users, applications and infrastructure – can help to control the scope and impact of the journey.
At Palo Alto Networks, we refer to these areas as the three “pillars” of a Zero Trust Model. The figure below outlines the actions that must be taken consistently with these pillars: establishing identity by using the strongest authentication possible – verifying the device and workload, securing access and securing all transactions.
Automation as a Zero Trust Accelerator
Zero Trust is a methodology, but it needs to be supported by the right tools, including those for orchestration and automation. When the administrative burden of a Zero Trust strategy becomes too great, it runs counter to the original goal of simplifying security. To help minimize the impact of that strategy, including mission timelines and performance, look to automate and orchestrate any tasks you can. Palo Alto Networks Cortex XSOAR – our security orchestration automation and response platform – can help. In fact, we use it in our own internal execution of Zero Trust.
Here’s another tip for speeding and amplifying your agency’s Zero Trust journey: Formulate your strategy in parallel with your overall efforts to transform digitally, including network transformation, data center and cloud migration, as well as SecOps transformation, so you can modernize and rebuild IT while meeting your Zero Trust objectives.
Why Work with Palo Alto Networks and Booz Allen Hamilton on Zero Trust
Government and military leaders turn to Booz Allen Hamilton to solve their most complex problems. They rely on the firm’s agility and mission-specific technical expertise to bring together unique teams of subject-matter experts who partner with them in the design, development and implementation of powerful solutions.
Palo Alto Networks provides a platform approach to security that enables the consistent application of security posture wherever a user, data, application, asset or service resides. Our technology architecture is single plane, and with our nearly universal integration across products in the Zero Trust solution area, our combined team can build an architecture that meets the needs of your organization.
Together, Palo Alto Networks and Booz Allen Hamilton can equip your federal agency with the insight it needs to deploy Zero Trust intelligently while optimizing for speed, performance and mission assurance to transform how your users securely access the cloud. Whether it’s for a free Zero Trust informational workshop, a maturity assessment or a Professional Services engagement, get in touch with our cybersecurity solutions experts to see how we can help your organization balance Zero Trust with the speed of the mission.
Related Blogs
Subscribe to the Newsletter!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.