Ransomware as a Service: Criminal “Entrepreneurs” Evolve Ransomware
This post is also available in: 日本語 (Japanese)
Ransomware, ransomware, ransomware. Like Jan Brady complaining about her sister with the famous line, “Marcia, Marcia, Marcia,” sometimes I feel like I can’t escape the topic of ransomware – its meteoric rise in popularity with attackers, its prevalence in news articles and its damage to organizations all over the world. There’s a reason ransomware is at the forefront of my (and many others’) thoughts lately. It's proven to be an effective mechanism for cybercriminals to hit a pay day in one shot: big payouts, big names, big attention. This has led to an evolution in the ransomware scene as entrepreneurial threat actors respond to growing demand by providing “ransomware as a service” (RaaS) – platforms for budding cybercriminals looking to make it in the "industry.”
In the first installment of this two-part series, I cover how the ransomware-as-a-service model evolved and how it lowers the technical barrier for entry for cybercriminals – but also how this includes a silver lining for defenders.
The Ransomware-as-a-Service Model: Lowering the Technical Barrier of Entry
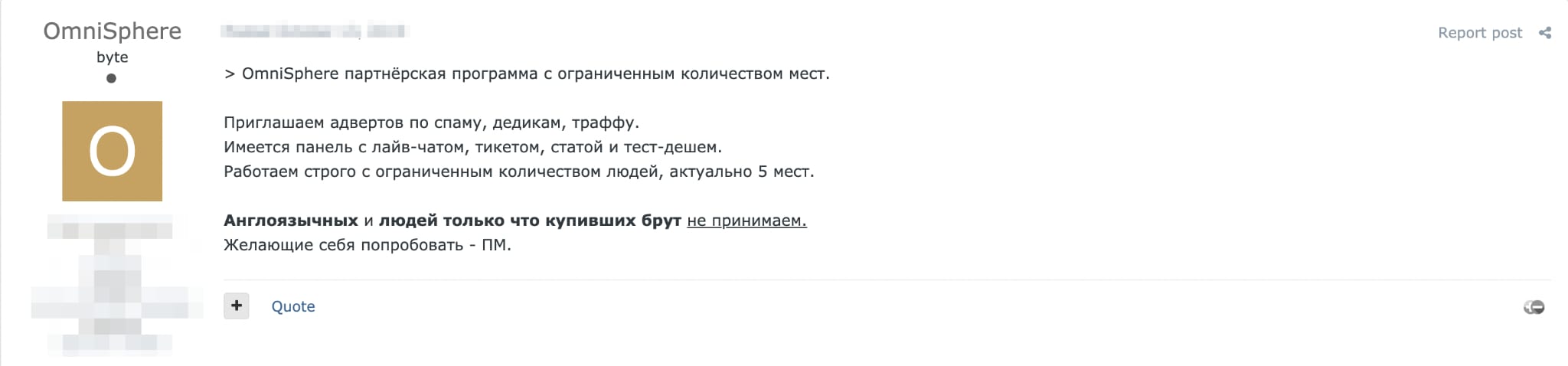
Cue the commoditizing of all bad things and creating digital marketplaces to facilitate almost every stage of cyberattacks, resulting most recently in the birth of RaaS. If you're unfamiliar with RaaS, then just know that it's a business for criminals, by criminals to make carrying out ransomware attacks that much easier. The operators who run the RaaS develop and provide the actual ransomware to affiliates, usually with monthly fees and agreements, like a perverted version of a media streaming service – delivering new content directly to their subscribers.
The RaaS model provides a lot of benefits to an attacker. First, it makes it easier for attackers to mix things up. Ransomware being detected? Payments taking too long? Too much attention from law enforcement? Not a big deal; roll the dice on a new RaaS. We find that attackers are being presented with a plethora of marketplaces where they can pick and choose tools, malware and even direct corporate access. This flexibility increases their capabilities and allows them to adapt through trial and error until they find the right mix for their use case. It also makes it significantly more challenging for defenders to attribute attacks to particular criminal organizations – you aren't necessarily dealing with one entity anymore but a combination of several, each with potentially different characteristics that are also evolving independently of each other. This makes it easier for threat actors to remain anonymous due to the decentralization of services.
More importantly – and the main topic here – RaaS lowers the technical barrier of entry for conducting these cyberattacks. The easier it becomes to acquire these services, the more appealing they become to potential cybercriminals looking to break into the game. RaaS frees individuals from needing the technical knowledge and know-how to craft their own ransomware or even to break into an organization's network. Everything can be purchased, and enterprising attackers just need to connect the dots. When media headlines start making waves about a single attack being able to secure tens of millions of dollars in a ransom payment, this becomes an extremely powerful motivator for those who otherwise might not have gone down this path. RaaS offers would-be threat actors a jumpstart into a criminal career, and even skips them a few steps ahead.
The Silver Lining for Defenders
What does this mean for defenders? Since RaaS can sound increasingly worse the more you hear about it, what’s the silver lining in all of this?
Ethical Considerations Matter (Somewhat) for RaaS
For starters, it's important to recall that RaaS is a business for cybercriminals and they are starting to treat it as such. To run a successful business, you have to think about issues that typically aren't in the normal purview for consideration in traditional attacks. For example, ethical implications have become a major focal point. It's one thing to steal someone's money, but it's another thing entirely to be responsible for someone's death. That's now a very real concern with hospitals and emergency services being hit by ransomware. As such, some RaaS operators and underground forums are now explicitly forbidding the sale of ransomware lockers entirely or trying to limit the potential targets for attacks and exclude specific industries such as healthcare and critical infrastructure.
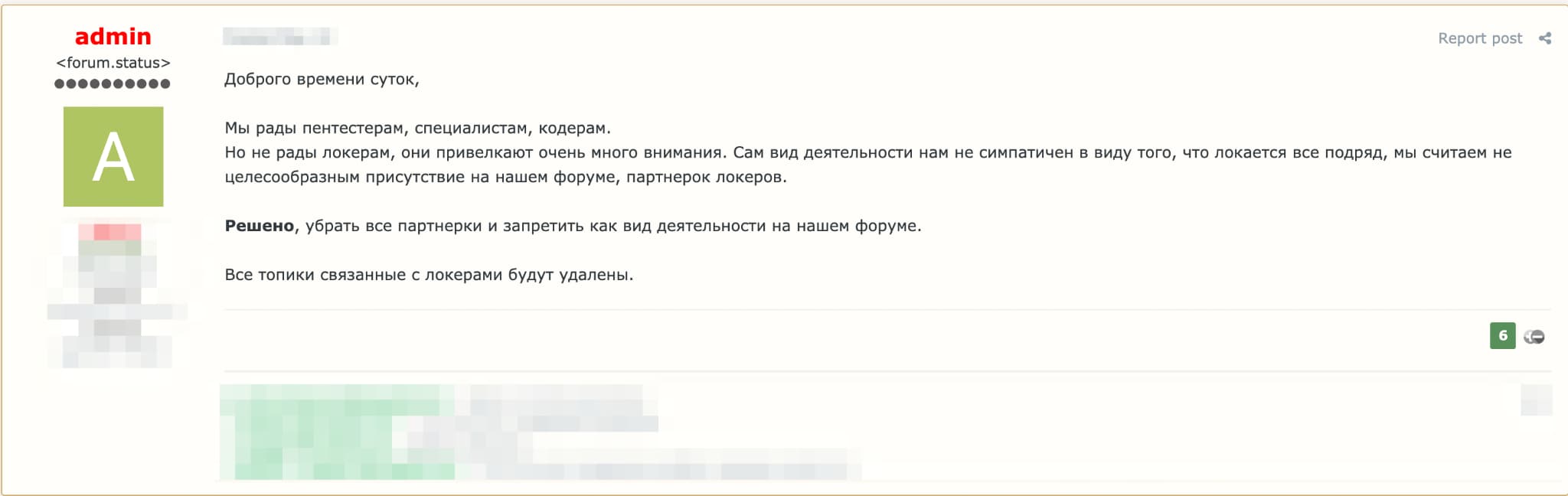
This puts an additional onus on the attackers when considering potential targets. I do suspect more limits will be imposed by RaaS operators as attacks continue to escalate and different types of organizations get hit. I wouldn't bet on ethics being a guiding light for most of these individuals at the end of the day, but they seem to need to at least nod to the idea of ethics the more they operate as businesses.
Less Sophisticated Attackers May Be Easier to Stop
Lowering the technical barrier also means that we'll see cybercriminals carrying out attacks that lack the sophistication that traditional attackers may have had. This means that when they've purchased access into your network from a marketplace to deploy the ransomware they didn't develop themselves, roadblocks they didn’t account for have a higher likelihood of disrupting their attack and their ability to proceed within your network. Getting around these barriers usually generates more noise and delays action, and – if there are enough walls built – it may be enough of a deterrent to make them give up altogether. Roadblocks, roadblocks, roadblocks! This isn't a new concept but instead a fundamental tenet in information security.
Ensuring that the basics are covered has always been a chronic problem for defenders, effectively since the dawn of computers introduced the need for securing information. There are many reasons for this, but one is that the practical application of the "basics" usually uncovers many unforeseen problems and challenges. Businesses often don't want to tackle these since the investment in them can be steep and hinder other areas of operation. Ransomware, for better or worse, is aiding in changing that as the investments needed for the basics of defense typically pale in comparison to an entire business being brought to its knees for weeks on end or paying tens of millions in ransom – not to mention the lasting damage to reputation. My point is, companies have been scrambling to shift focus to preventing these attacks through a myriad of different ways the past few years. However, they often seek a silver bullet product and overlook the power of focusing on the basics.
Defense in Depth Remains Key for Stopping RaaS
The reality is that there is no surefire way for stopping ransomware, and we see time and time again that layered security only goes so far in protecting an organization. There are always ways to bypass point security solutions, but this is where defense in depth comes back into focus – the roadblocks that can be placed in the path of attackers. It offers a more realistic approach wherein we accept the fact that there is no true, completely holistic security product or feature that will protect us completely all by itself. Instead, we must implement best practices and opt to hinder and slow attackers. The strategy is to make them consume resources, waste time, increase the signal-to-noise ratio for detection, slip up and expose themselves. We try our hardest to make sure threat actors have a bad enough experience that we become an unappealing target. This concept is nothing groundbreaking, but it helps in reframing the problem of RaaS in another light. If we think of it from this perspective, we can subsequently ask what roadblocks are of value that we can erect for a more comprehensive defense in depth strategy.
Learn more about making a plan for defending against ransomware attacks.
Jeff White is a principal threat researcher for the Unit 42 Threat Intelligence team. This is the first of a two-part series on ransomware as a service.
Related Blogs
Subscribe to the Newsletter!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.