Navigating Federal Data Protection Compliance Requirements in the Cloud
Government contractors and military suppliers are increasingly utilizing cloud services in the execution of their contracts. Many assume that if the cloud service provider’s (CSP) underlying infrastructure is compliant then their work is complete.
However, while the CSP’s underlying infrastructure and services may meet Federal requirements, government contractors and suppliers must establish that they have cloud services configured in compliance with NIST 800-171. The challenge typically lies in the cloud’s infamous shared responsibility model.
When using cloud services to process, store or transmit data related to work with the Federal government, contractors and vendors must ensure they are Defense Federal Acquisition Regulation Supplement (DFARS) 252.204-7012 compliant. Doing this in the cloud across multiple accounts and service providers can be a challenge without the proper processes and tools in place.
History
In 2010, the White House issued Executive Order (EO) 13556 to address the hodgepodge of controls and processes surrounding the protection of Controlled Unclassified Information (CUI). Following this Order, the Department of Defense (DoD) published its Final Rule in 2013, revising DFARS 252.204-7012. Originally relying upon NIST 800-53 r4 as the standard set of controls, this was later revised to use NIST 800-171. NIST 800-171 provides a list of controls through 14 control families. It also addresses cyber incident reporting. All of this is squarely directed at government contractors whose systems process, store or transmit CUI.
Cloud Impact
NIST 800-171 compliance is challenging for many in the Federal community for two primary reasons. Suppliers often use multiple public clouds across their various business units, and contractors regularly use multiple subcontractors in the execution of their contracts. Regardless of size, many are increasingly using cloud services to process, store or transmit CUI. In these cases, each and every cloud environment must be NIST 800-171 compliant for each of the 14 control families.
Continually monitoring compliance with NIST 800-171 is challenging, but this is made increasingly complex by the dynamic nature of cloud environments. Consider that in the on-premises world, the lifespan of an application could often be measured in years. In the cloud, this lifespan drops to an average of just two hours! This means that for many cloud resources if you are not continually monitoring compliance with NIST 800-171, it’s highly likely you will miss key changes that could create potential compliance challenges. While each of the cloud vendors offer some native security services within their platforms, this has proven to be insufficient for compliance and security across multiple cloud accounts and vendors. When it comes to anything outside their ecosystem, the cloud vendors have little incentive to provide the visibility and compliance government contractors need with a multi-cloud strategy.
Multi-cloud Continuous Compliance Monitoring
When looking to ensure their multi-cloud strategy is compliant with NIST 800-171 and other Federal standards, it is important that security leaders and their teams keep visibility, compliance and security in clear focus. This is where cloud-agnostic security tools such as Prisma Cloud by Palo Alto Networks can help.
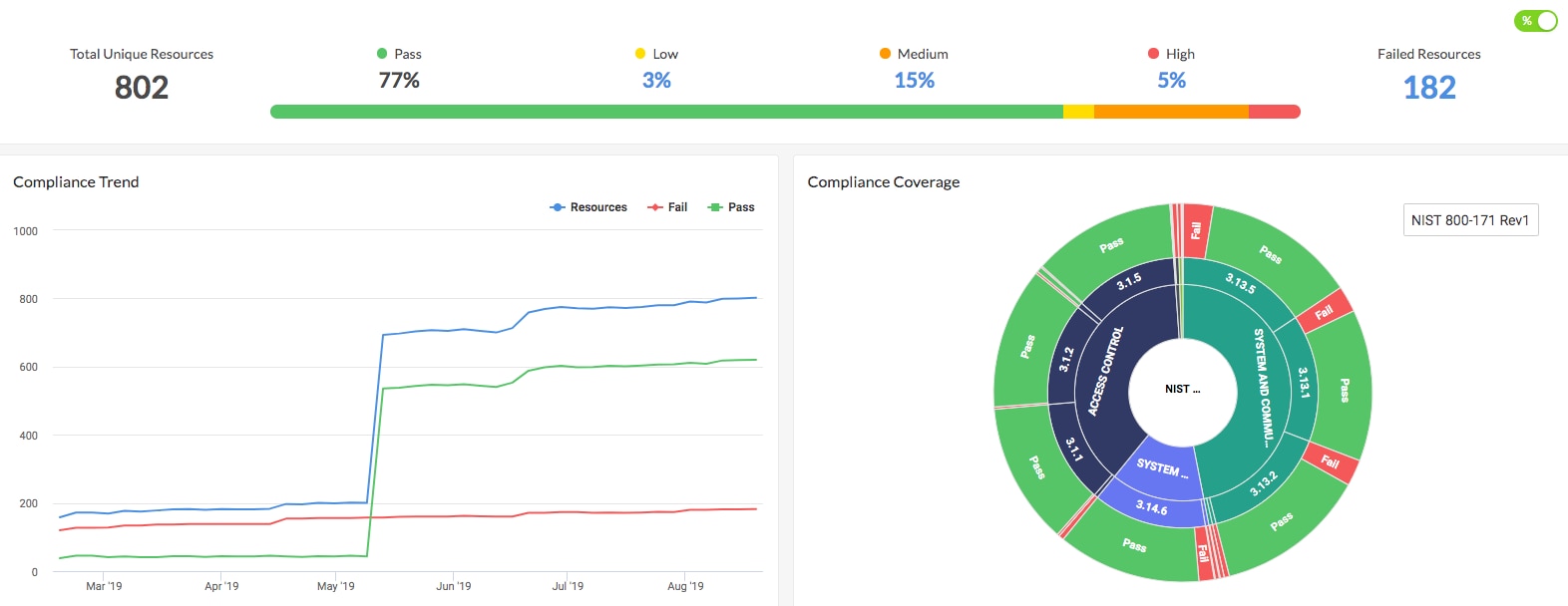
Figure 1 - Prisma Cloud shows real-time compliance status of NIST 800-171
Prisma Cloud is a comprehensive cloud-native security platform with broad security and compliance coverage—for applications, data and the entire cloud-native technology stack—throughout the development lifecycle and across multi- and hybrid cloud deployments. The Prisma Cloud integrated approach enables security operations and DevOps teams to stay agile, collaborate effectively and accelerate secure, cloud native application development and deployment.
Prisma Cloud also simplifies compliance by utilizing a comprehensive library of industry compliance standards and policies, including NIST 800-53, ISO 27000, SOC 2, NIST CSF and many others. If your organization is subject to DFARS 252.204-7012 and NIST 800-171, Prisma Cloud is a powerful tool to help you navigate your regulatory obligations. For those who require Federal Risk and Authorization Management Program (FedRAMP) security controls, Prisma Cloud is part of Palo Alto Networks Government Cloud Services, which is currently In Process with FedRAMP. This important milestone indicates progress for Prisma Cloud toward a FedRAMP Moderate Agency Authorization.
Learn more about how Palo Alto Networks and its cloud products, including Prisma Cloud, can help secure federal networks.
Related Blogs
Subscribe to the Newsletter!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.