What Is a Remote Access VPN? | Remote Access VPN Explained
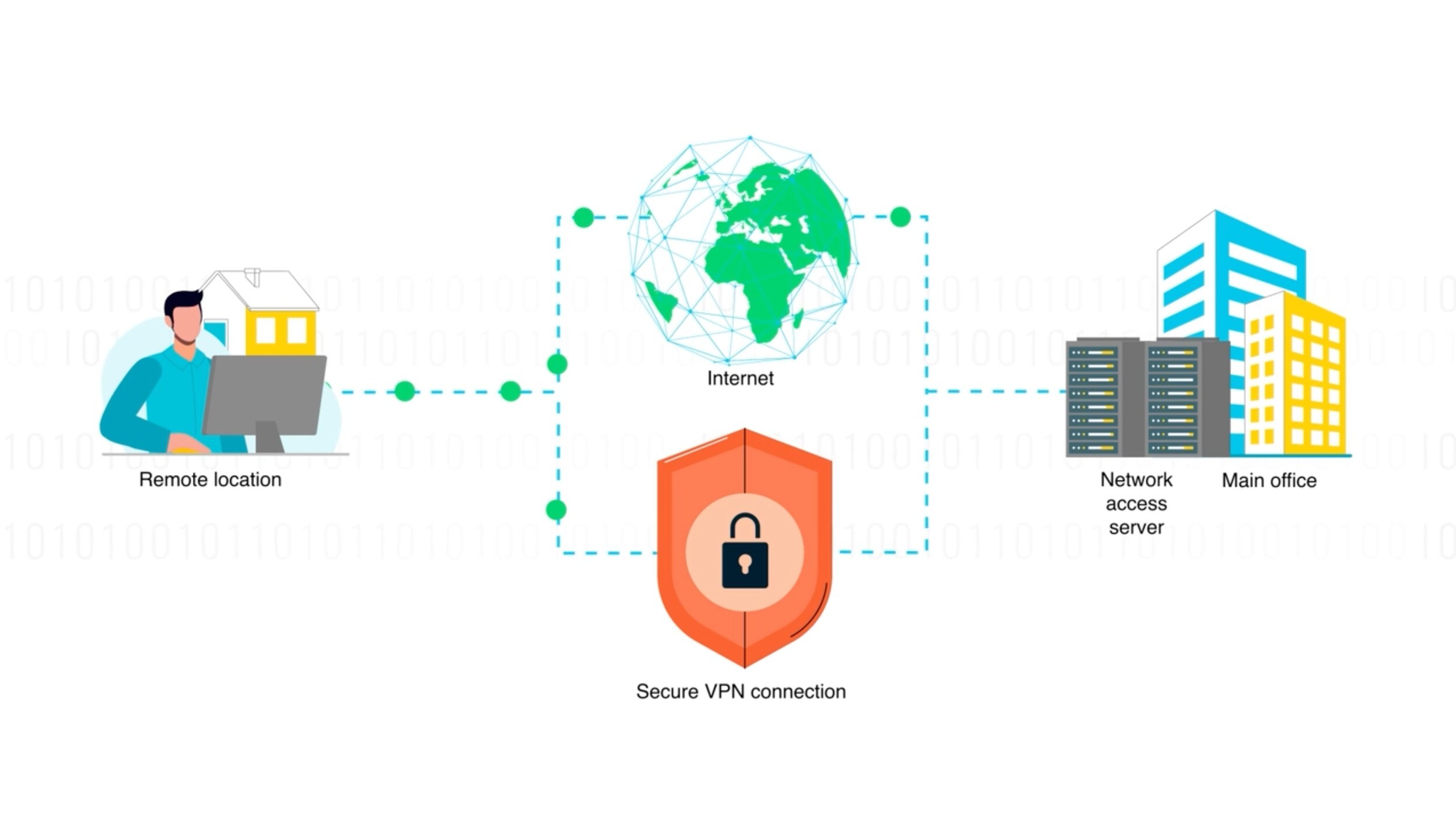
A remote access virtual private network (VPN) enables users who are working remotely to securely access applications and data that reside in the corporate data center and headquarters, encrypting all traffic users send and receive.
A secure remote access VPN creates a tunnel between the network and a remote user that is virtually private. Traffic is encrypted, which makes it unintelligible to eavesdroppers. Users in remote locations can securely access and use the network in much the same way as in the office. Using remote access VPNs, data can be transmitted without the risk of interception or tampering.
How Does a Remote Access VPN Work?
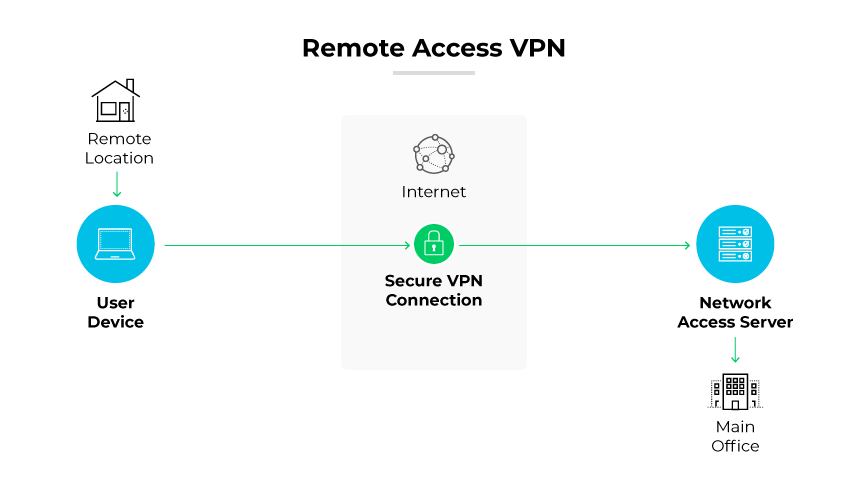
A remote access VPN works by establishing a secure, encrypted connection from a user's device to the corporate network. This process begins with a VPN client that manages the initial authentication process, confirming that only authorized users can establish a connection. Once authenticated, the VPN client software creates an encrypted tunnel to the VPN gateway. The gateway acts as the VPN server, facilitating a secure path for data transmission.
Even over public internet networks, all data transmitted through the tunnel is encrypted, preserving its confidentiality and integrity. The secure tunnel extends the network's perimeter to the remote user, essentially placing them within the corporate network. This process allows for safe access to internal resources like applications, file servers, and databases.
A remote VPN often includes security features including multi-factor authentication and advanced encryption standards. Additional layers of security ensure the connection remains private and protects the corporate network from potential threats introduced by remote devices.
Benefits of Remote Access VPN
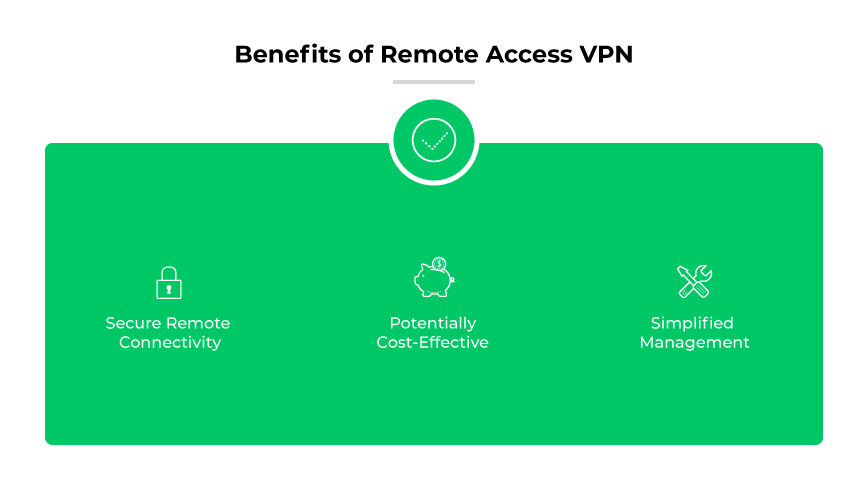
Secure Remote Connectivity
A remote access VPN secures connections to the corporate network for remote workers and mobile users. It encrypts data traffic, ensuring confidentiality and protecting the integrity of sensitive information.
Potentially Cost-Effective
Implementing a remote access VPN can sometimes be a cost-effective solution for expanding network access beyond the physical confines of the office. For some companies, it can delay the initial need for extensive infrastructure investments.
Simplified Management
Remote access VPNs simplify network management by providing a single point of control for user access and security policies. Administrators can easily manage connections, monitor security, and enforce policies without the need for complex on-site configurations.
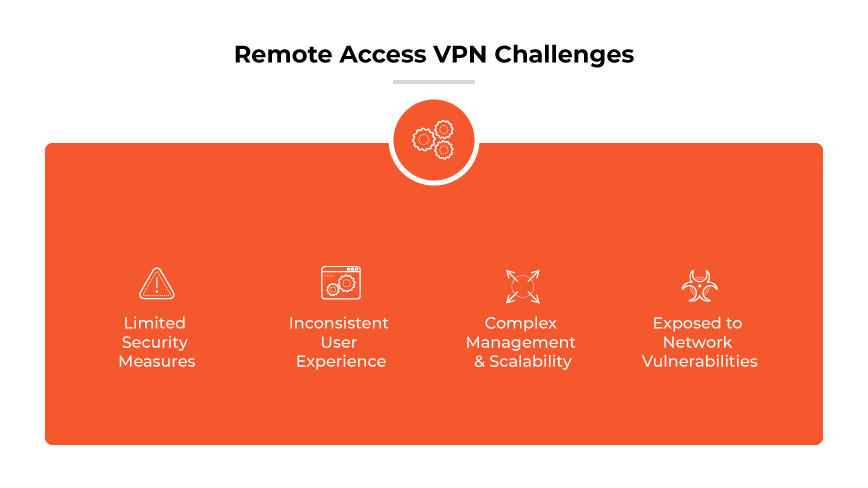
Remote Access VPN Challenges
Historically, remote access VPNs were a staple in providing remote workers with access to corporate resources. However, as network architectures evolve and security threats become more sophisticated, these VPNs can sometimes present challenges, particularly when compared to more modern solutions.
Limited Security Measures
Traditional remote access VPNs do not provide sufficient security controls beyond the basics of encryption and authentication. They may lack the ability to enforce granular access controls, leaving sensitive corporate resources potentially exposed to unauthorized access.
Inconsistent User Experience
The user experience with remote access VPNs can be inconsistent and sometimes cumbersome, depending upon the provider and platform. Connectivity issues and the need for manual logins can hinder productivity and frustrate remote employees.
Complex Management and Scalability
As organizations grow, managing a remote access VPN can become complex and time- consuming. Scaling to accommodate an increasing number of remote work users often requires additional hardware and can lead to significant administrative overhead.
Exposed to Network Vulnerabilities
Remote access VPNs can expose networks to vulnerabilities, particularly if endpoint devices are compromised. Since VPNs typically do not assess the security posture of devices, they can inadvertently become conduits for malware or other cyber threats.
Remote Access VPN vs. Site-to-Site VPN
The main differences between site-to-site and remote access VPNs are network connection architectures and use cases.
Site-to-site VPNs link entire networks together. They secure traffic at the edge of the network, allowing different sites to share resources as if they were part of the same network.
Remote access VPNs cater to individual users looking to access a network from distant locations. These VPNs utilize client software installed on each user's device which creates a secure tunnel to the network.
SASE as the Modern Alternative to Remote Access VPN
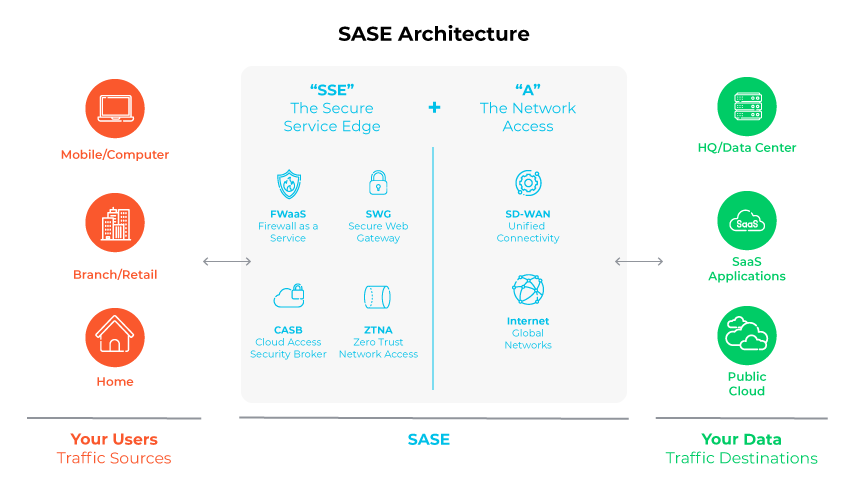
The increasing trend of remote workforces and the growth of Software as a Service (SaaS) has led to a change in the flow of digital traffic. Rather than primarily being directed toward data centers, traffic is increasingly routed toward internet and cloud-based services.
Secure Access Service Edge (SASE) has emerged as a solution to ensure continuous, secure access for remote workers. SASE combines the functionality of a wide area network (WAN) with robust, enterprise-grade security measures to form an integrated, cloud-native service. This approach effectively merges an organization's networking, security protocols, and operational procedures into one streamlined system.
SASE represents a significant shift where security fragmentation is concerned. It moves away from the traditional model of multiple, on-premises security solutions from various vendors, focusing instead on a unified cloud-based network security structure. This architecture not only enhances security but provides the adaptability to integrate diverse security services.