Remediating PrintNightmare (CVE-2021-1675) Using Cortex XSOAR
Executive Summary
On June 29, 2021, proof of concept code for CVE-2021-1675 was posted on Github. This CVE was patched by Microsoft on June 8, 2021 as a part of the June 2021 Patch Tuesday, which was described as local privilege escalation. On Jul 1, Microsoft published another advisory to the Print Spooler service (CVE-2021-34527, AKA PrintNightmare) which included remote code execution with SYSTEM privileges and the CVE severity to critical.
The CERT Coordination Center (CERT/CC) further released a VulNote for this critical remote code execution vulnerability in the Windows Print spooler service, suggesting that the available updates do not address the public exploits that also identify as CVE-2021-1675, meaning an attacker can still exploit this vulnerability to take control of an affected system. CVE-2021-1675 is a vulnerability that allows remote code execution (RCE) on Windows Print Spooler. This blog will help you implement automated response and remediation measures using Cortex XSOAR.
What are some known ways this vulnerability can be exploited?
The Microsoft Windows Print Spooler service fails to restrict access to the RpcAddPrinterDriverEx() function, which can allow a remote authenticated attacker to execute arbitrary code with SYSTEM privileges on a vulnerable system. To be able to use this exploit it requires the attacker to authenticate as a domain user. The Print Spooler service is normally enabled, so the compromise of any DC user could likely result in RCE. Successful exploitation will allow the attacker to gain remote code execution with SYSTEM-level privileges.
How can Cortex XSOAR help?
Our mission has been to help our customers automate security operations to the extent that is possible by technology – a key part of staying ahead of today’s automated attackers. To help with this, we provide playbooks for specific types of response actions and maintain an ecosystem where others can contribute playbooks as well – and we advise our customers to add our playbooks to their SecOps process to automate what they can.
For this CVE-2021-34527 - PrintNightmare and many others, organizations can leverage the power of automation with Cortex XSOAR to help speed up the discovery and remediation of known vulnerabilities. XSOAR’s automated playbooks also help in unifying threat feed ingestion, indicator enrichment and incident management workflows, helping your team to respond to sophisticated attacks at machine speed.
Cortex XSOAR released two playbooks to address the PrintNightmare vulnerability: CVE-2021-1675 | CVE-2021-34527 - PrintNightmare playbook and a detection and response playbook with the Cortex XDR:
The CVE-2021-1675 | CVE-2021-34527 - PrintNightmare playbook includes following tasks:
- Mitigation actions - to mitigate the exploit, recommended actions to disable Print Spooler services if possible, restricting the ACLs, and Install Microsoft patches.
- Run vulnerability scan - to detect any vulnerabile device in the organization network.
- Search for compromised devices based on Windows event IDs related to the exploit (Windows event IDs 808 and 31017.
- Query firewall logs to detect network activity.
- Run dedicated detection and response playbook for Cortex XDR
The Cortex XDR - PrintNightmare Detection and Response includes following tasks:
- Containment of files, endpoints, users and IP Addresses
- Enrichment of indicators
- Data acquisition of system info and files using Cortex XDR
- Eradicating compromised user credentials
The investigation data is documented automatically within the Cortex XSOAR case management, making it easier for the security teams to use this data as reference.
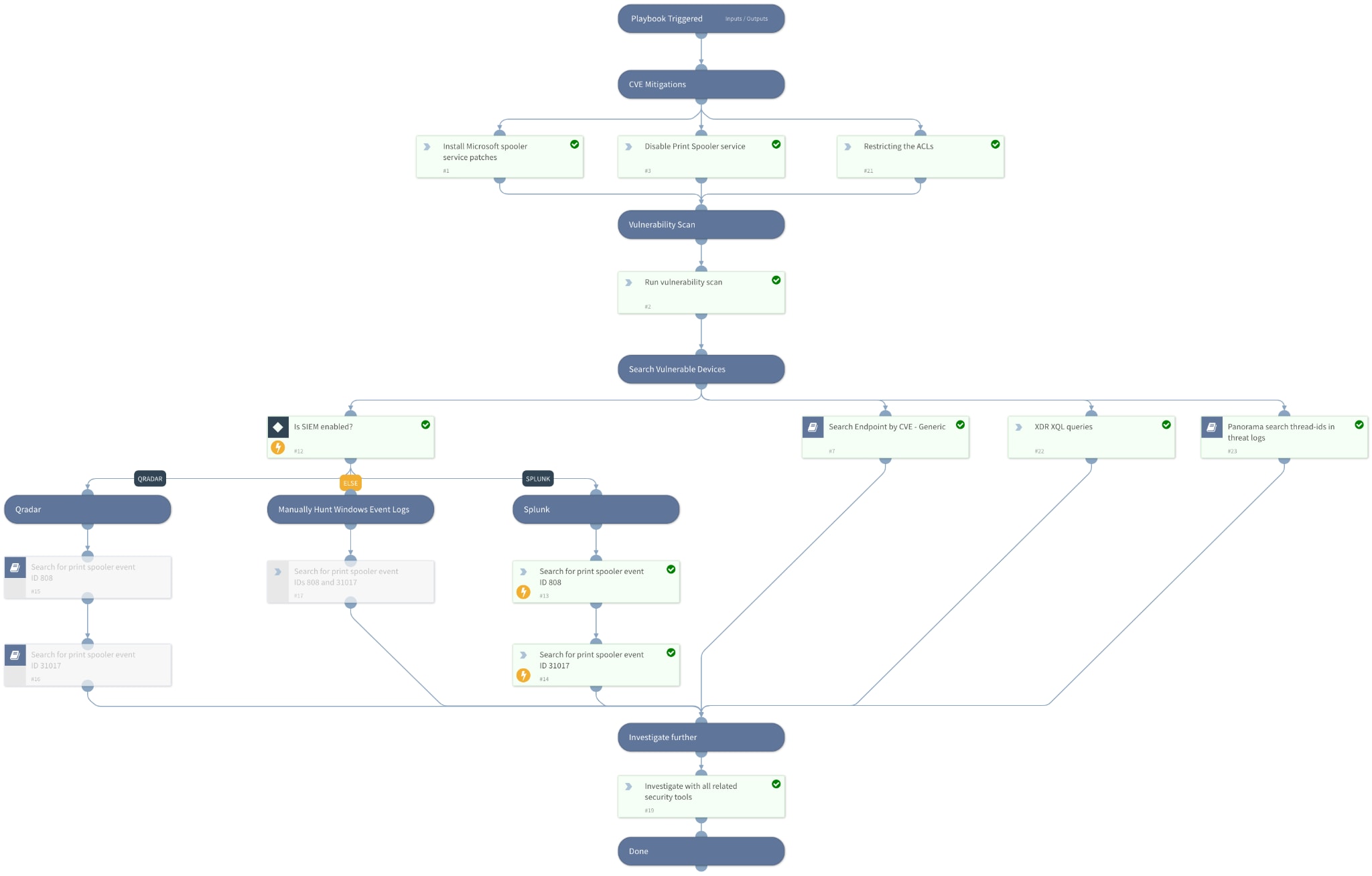
Figure-1. The CVE-2021-1675 - PrintNightmare playbook in action
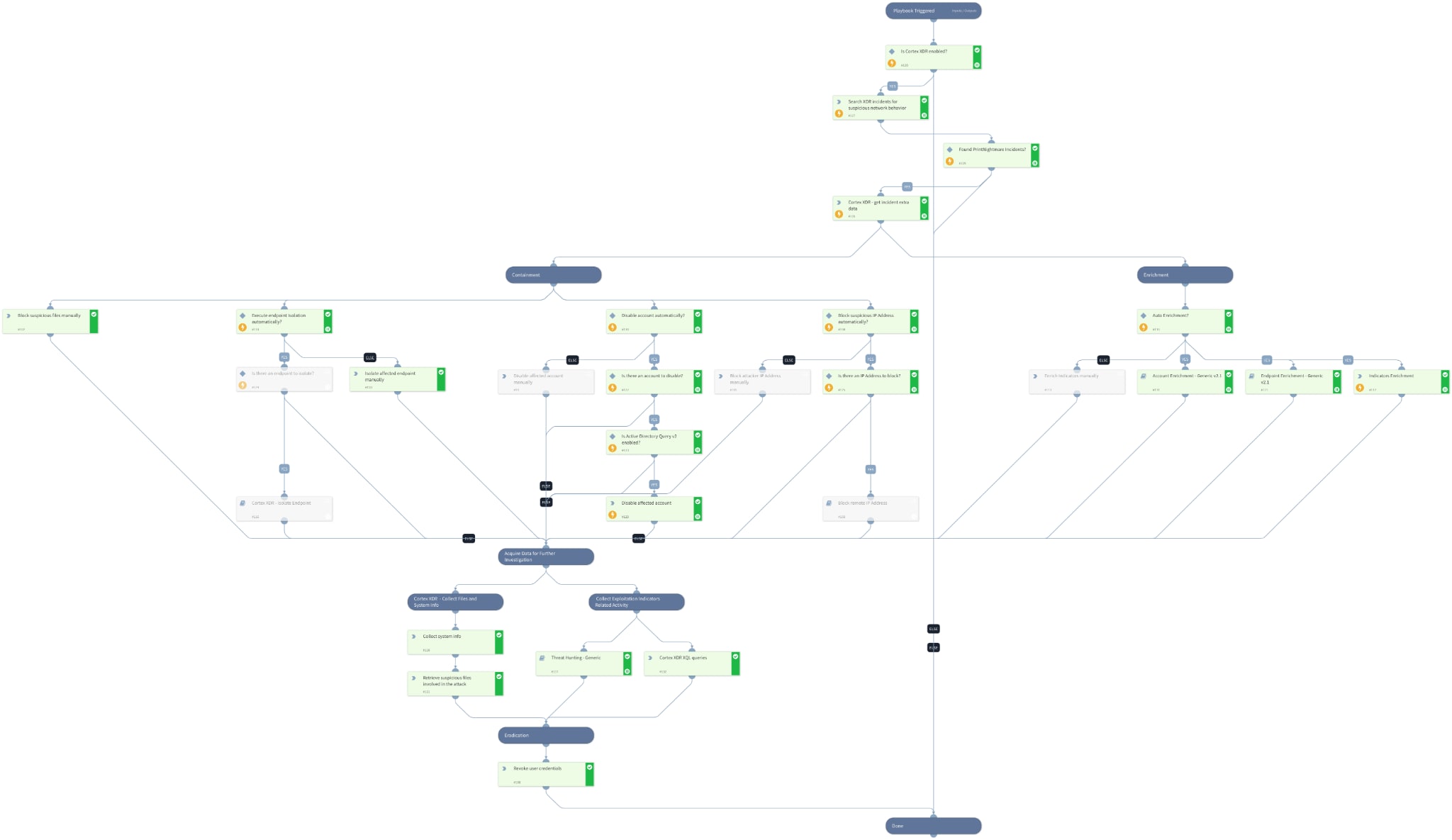
Where can I find this playbook?
CVE-2021-1675 | CVE-2021-34527 - PrintNightmare is part of the Rapid Breach Response content pack available for download from the Cortex XSOAR Marketplace. Rapid Breach Response is a collection of playbooks developed by our security research teams in response to high-profile breaches and attacks, such as HAFNIUM - Exchange 0-day Exploits and SolarStorm. You can find the Rapid Breach Response content pack playbooks in our Cortex XSOAR Marketplace.
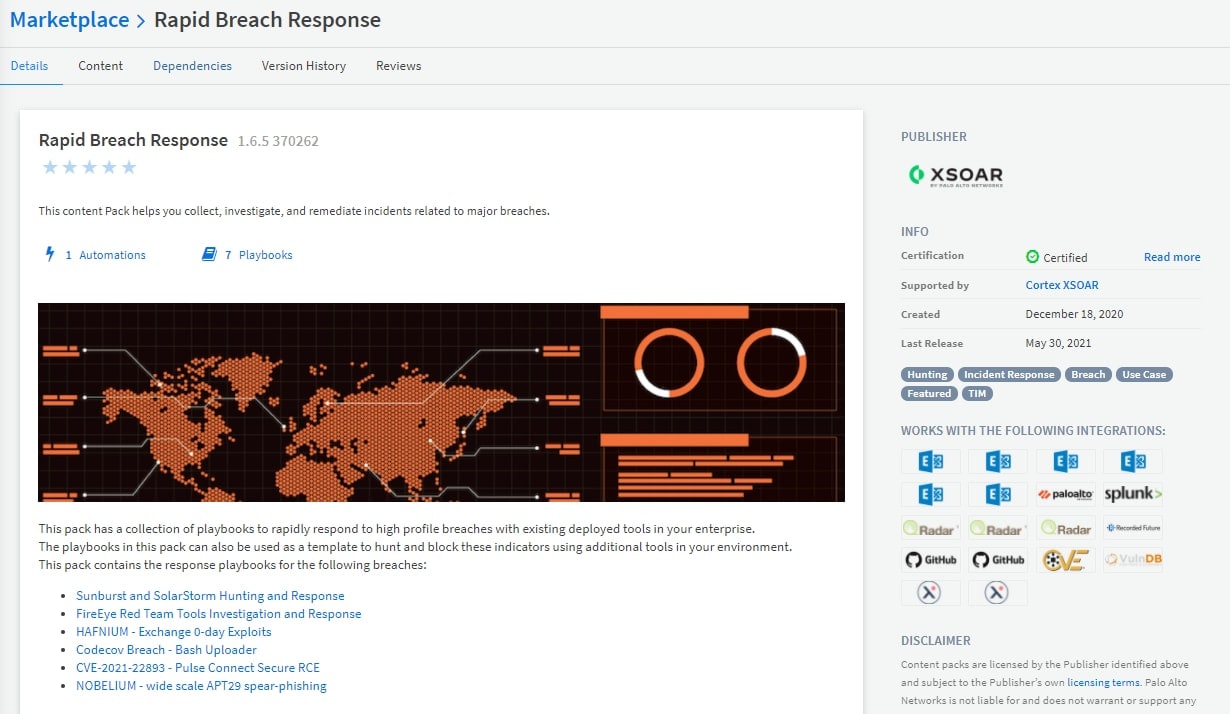
Figure-2. The Rapid Breach Response collection of playbooks in the Cortex XSOAR Marketplace can help organizations respond to high-profile breaches and attacks.
Conclusion
With the help of the Rapid breach response content pack and Cortex XSOAR core capabilities and integrations, incident response, SecOps, and threat intel teams can save many hours of manual labor trying to piece disparate sources of information together from multiple tools. Cortex XSOAR can automate several remediation and response actions so that security teams can quickly respond to vulnerabilities such as the PrintNightmare, and mitigate them to reduce its impact on the enterprise.
Don’t have Cortex XSOAR yet? Try the free Community Edition today.
Leverage the Cortex XSOAR’s CVE-2021-1675 - PrintNightmare Playbook to Remediate
Related Blogs
Subscribe to Security Operations Blogs!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.