Playbook of the Week: Incident Case Management with Cortex XSOAR
When it comes to incident case management, SOC teams are often challenged to find a balance between using a standardized incident response for high-volume attacks versus customized response for sophisticated one-off attacks. Additionally, the overwhelming amount of alerts and fires that security teams must attend to on a daily basis can distract from efforts to make continuous improvement to security resilience.
This is where Cortex XSOAR comes in. Using the XSOAR Case Management Content Pack, our full incident case management capabilities combined with our security orchestration and automation functionalities provide quicker triage, response, coordination and collaboration to combat rising attack numbers.
With incident case management you get:
- Virtual War Rooms where analysts are able to perform investigations and collaborate in real time using incident-specific data and layouts.
- Customized Dashboards and Reports that give full visibility and flexibility. Analysts are able to use both out-of-the-box and user-created widgets that meet their operational needs. It also allows users to tailor response to attack types, whether it’s granular metrics and response workflows, or incident flows and fields.
- Playbook Automation and Auto-Documentation that eliminates the need for manual reporting and post-investigation rollups.
- Real-time ChatOps for maximum technical chat support and collaboration.
- Built-in Machine Learning insights that also prime users for continuous learning with suggestions for incident ownership, task assignment, related incidents, and commonly run commands.
- Integrated Threat Intel Management (TIM) that automates the ingestion, aggregation, and tuning of threat feed data for added context during investigations, using both external intel data and internal alerts to identify future critical threats.
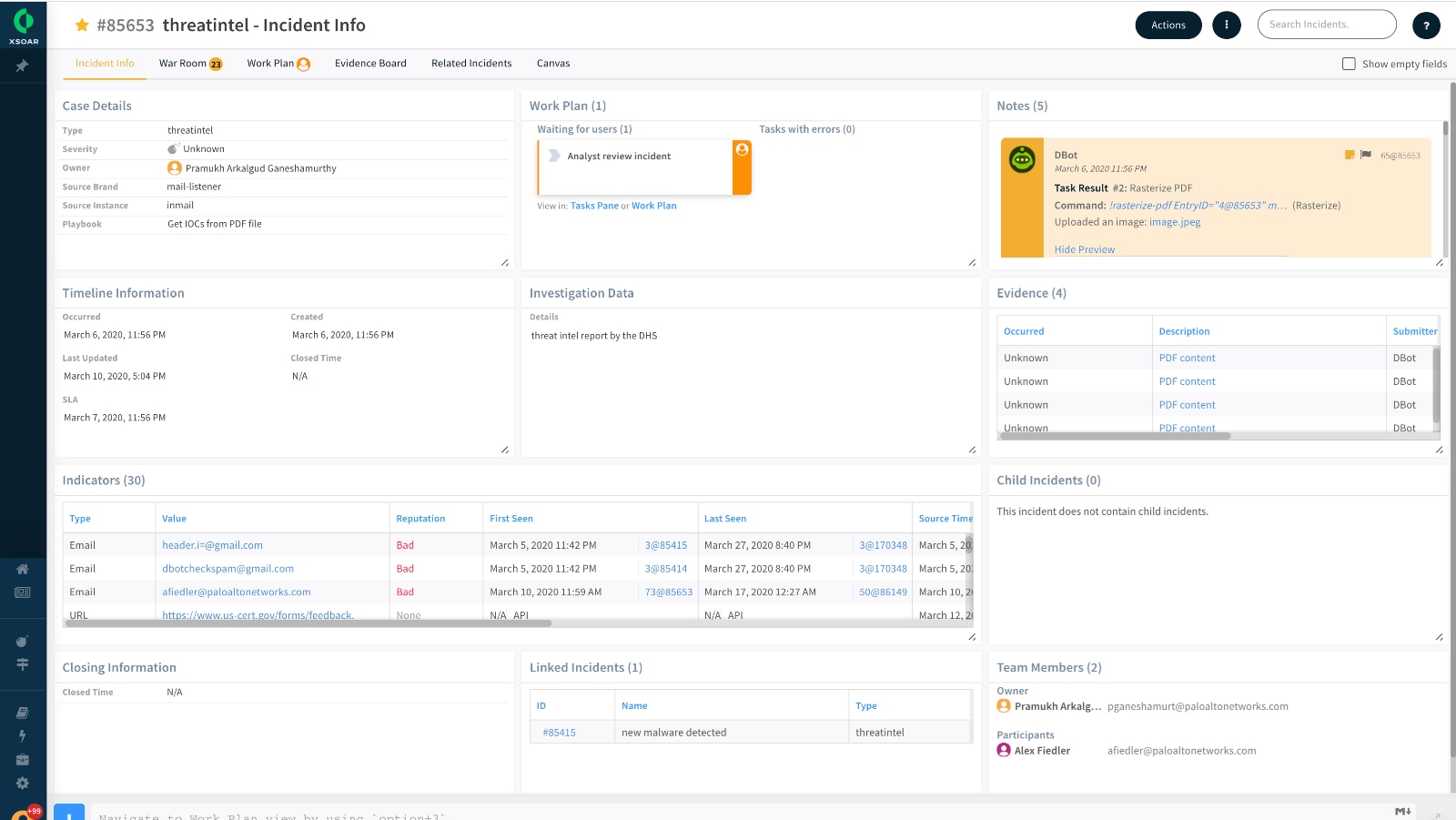
The Case Management content pack provides high-level visibility through the incident overview dashboard which gives a summary of all incidents in the system, by type, severity, owner, etc., as well as detailed reports such as a Case Report, Incident Summary and Investigation Summary. It also includes a more analyst-focused dashboard for SOC teams to manage and work on incidents assigned specifically to them or collaborate on other incidents or War Room chats they may be participating or mentioned in.
To learn more about the associated integrations, playbooks, scripts, commands, and automations, please refer to the Palo Alto Networks Developer Doc.
Conclusion
This content pack is seen as one of the core default functionalities of Cortex XSOAR. It is the foundation upon which SOC teams can customize their incident ingestion and case management with various integrations that suit their needs. This means no additional mapping and classification is required, as data from the incoming incident will be displayed in the labels section of the dashboard, allowing teams to quickly bring in alerts from various systems, and then further tune the data, layouts, and playbooks for future improvements. So, whether you're creating incidents manually in XSOAR or fetching from a SIEM, this pack provides helpful content for accelerating incident response by unifying alerts, incidents and indicators from any source on a single platform for lightning-quick search, query and investigation.
Don’t have Cortex XSOAR? Download our free Community Edition today to test out this playbook and hundreds more automations for common use cases you deal with daily in your security operations or SOC.
Please Suggest Other Ideas or Vote!
If you like these ideas or would like to suggest other ideas, please collaborate with us through the Cortex XSOAR Aha page: https://xsoar.ideas.aha.io/ideas.
Related Blogs
Subscribe to Security Operations Blogs!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.