Cortex XDR Blocks Undiscovered UAC Bypasses
Cortex XDR researchers recently found new UAC (User Account Control) bypasses on a fully patched Windows 10. While the method used is not new, the abused binaries that can be used with that method were previously unknown. Cortex XDR’s prevention logic was designed to identify and prevent attacks of this kind in a generic way, so when the new UAC Bypasses were tested against the solution, it identified the incidents as UAC bypass attempts and prevented them.
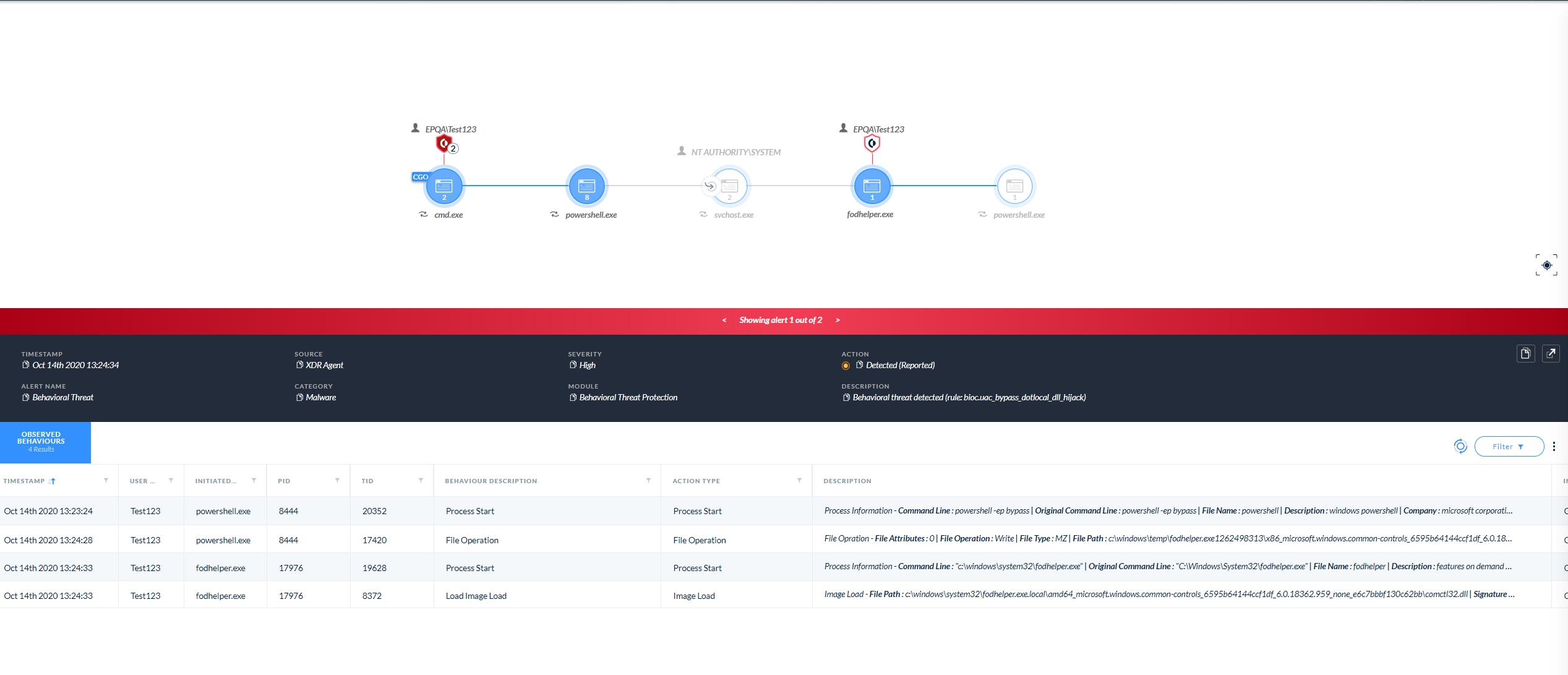
Windows User Account Control (UAC) permits a program to elevate its privileges to execute a task under administrator-level permissions. If the UAC protection of a computer is set to the default level, the user will be prompted through a notification box to confirm the elevation request change. In many cases, however, Windows programs can elevate privileges or execute tasks without prompting the user for confirmation. Cyber criminals abuse those mechanisms to run their malware with administrative privileges without the user prompt, achieving UAC bypasses.
How This UAC Bypass Works
This method works by abusing a Windows Side-By-Side (WinSxS) DLL loading issue and an auto-elevated IFileOperation COM Object. When those auto-elevated binaries search for a WinSxS library, they first search inside a .local folder, which are used legitimately for library redirection by developers.
Often, the .local folder doesn't exist, so if an attacker can create that folder and the targeted library before the auto-elevated binary runs, he can set up a malicious DLL to be loaded inside the auto-elevated binary. This is a form of DLL Hijack.
The attacker can create the folder and move its DLL without privileges thanks to the IFileOperation auto-elevated COM object.
As we were testing auto-elevated binaries for this vulnerability, we realized it's a lot more common than people might think. The binaries we found include:
wusa.exe
Taskmgr.exe
SystemSettingsRemoveDevice.exe
shrpubw.exe
recdisc.exe
pwcreator.exe
odbcad32.exe
MultiDigiMon.exe
MSchedExe.exe
lpksetup.exe
iscsicpl.exe
fodhelper.exe
dccw.exe
msconfig.exe
CompMgmtLauncher.exe
Note that this is not an exhaustive list -- just the ones that we found during our proof-of-concept. We expect that there are likely a number of additional vulnerable binaries.
Cortex XDR provides extensive coverage against UAC bypass attacks. The platform stops threats on endpoints and coordinates enforcement with network and cloud security to prevent successful cyber attacks. To prevent the exploitation of UAC Bypasses, the Behavioral Threat Protection (BTP) and Local Analysis Protection modules in Cortex XDR monitor for malicious behaviors across a sequence of events and immediately terminate the attack when detected.
To learn more about Cortex XDR, go to: https://www.paloaltonetworks.com/cortex/cortex-xdr
Related Blogs
Subscribe to Security Operations Blogs!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.