Introducing Prisma Access Traffic Replication
Enterprises are on an accelerated SASE journey. Prisma Access, our flagship cloud-delivered security platform, allows global organizations to seamlessly adopt Security Service Edge (SSE) and transition to Secure Access Service Edge (SASE). Prisma Access combines ZTNA, Cloud SWG, CASB, and FWaaS in a unified product and provides customers with the complete ZTNA 2.0 solution in a cloud-native environment using multi-cloud architecture.
While cloud transformation has benefits, one of the often overlooked gaps is the lack of recording traffic in a cloud security stack. This lack of complete packet capturing results in the inability to perform forensic analysis, postmortem analysis, or troubleshoot network performance issues. These critical capabilities to a robust security structure are often lost when migrating from on-premises to a cloud solution.
Introducing Prisma Access Traffic Replication
Prisma SASE is the first SASE solution to offer traffic replication with no performance impact to the regular inline security processing by taking full advantage of the Google Cloud Packet Mirroring to allow for a seamless cloud transformation.
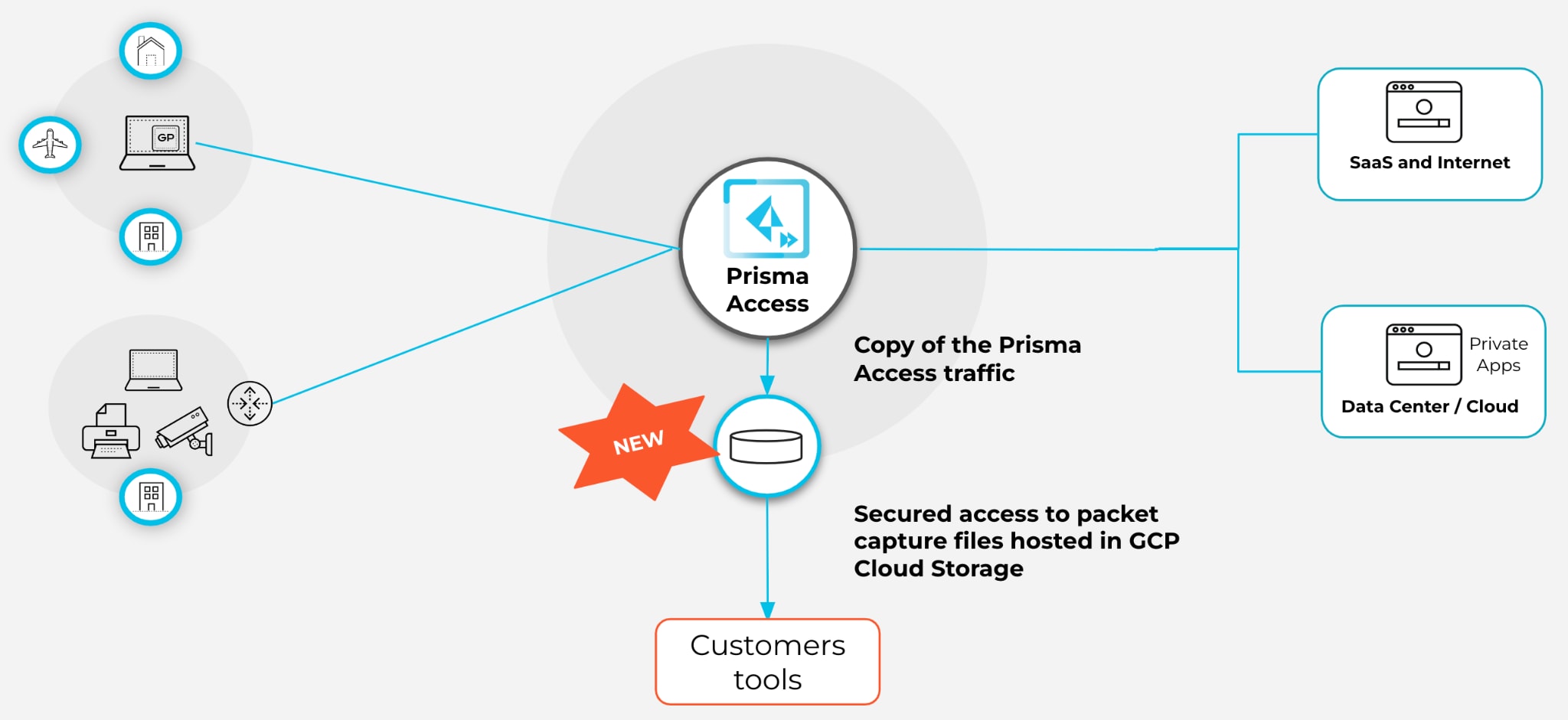
Organizations can enable traffic replication across all Prisma Access regions or specific regions based on their configuration.
Prisma Access can replicate all traffic from remote users, branch locations, or both and securely store the captured packets of decrypted traffic. Organizations can use these captured packets to reconstruct the traffic flows for forensic analysis or to analyze network and performance issues that are impossible to detect just by using traffic logs.
Google Cloud Platform (GCP) is Instrumental in Delivering Prisma Access Traffic Replication at Scale
We partnered with Google Cloud Platform (GCP) to enable Google Cloud Packet Mirroring outside the Prisma Access security processing node so it wouldn’t interfere with the security inspection efficacy and overall performance of Prisma Access.
Google Cloud Packet Mirroring clones the traffic and delivers a line-rate performance with zero impact on current operations. As with any GCP service, traffic cloning enables Prisma Access Traffic Replication to elastically manage the scale of traffic volume for any of the largest organizations.
When handling data at scale, sovereignty and security are critical concerns for organizations to ensure regulatory compliance. Google Cloud Packet Mirroring delivers security and confidentiality for traffic replication by enabling a safe, secure way of sharing sensitive data access across projects and storing the data in the same regions where inspection occurred in the first place. Prisma Access adds additional mechanisms to secure extreme scenarios involving insider attacks adding to GCP best practices, like encryption at rest and in transit.
5 Key Scenarios for Traffic Replication
- Enabling forensic analysis through deeper visibility. Traffic replication provides deeper visibility than logs which do not offer a complete view. Customers would see an incomplete view of an attack journey without traffic replication through partial or missing logs.
- Maintaining compliance with government regulations. Through deep packet inspection, companies can fulfill requirements set by government institutions that require a copy of the traffic generated by the users for a certain amount of time. The packet capture would qualify as legal evidence to prove if an event happened or didn’t happen.
- Application performance visibility. Enabling deep packet-level analysis allows more visibility in debugging application performance and behavior issues. For example, the networking team can understand the TCP window size at a certain moment or the content of the server response.
- Reduce mean time to remediation (MTTR). Empower your SOC with visibility to reduce the MTTR through deep packet inspection. For example, your SOC team can reconstruct user flows, including files and emails, and conclusively filter out false positive alerts through malicious behavior.
- Cloud-native integrations. Customers can deploy their preferred on-premises, a third-party tool to analyze packets in the cloud in the same regions where the data resides. This allows seamless integration and familiarity with their existing tool, simplifying and allowing usage of the current investment to maintain its current configuration.
Related Blogs
Subscribe to Sase Blogs!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.