Securing Your Metadata from Cloud Heists with Prisma Cloud’s Attack Path Policies
Many businesses today rely on cloud computing, and AWS is a significant player in this space. Using AWS, though, can be tricky. If not set up correctly, you can unknowingly create a security risk.
Take, for example, the increasingly prevalent scenario involving an EC2 instance. Far too often an EC2 instance is left accessible to anyone on the internet. And still common, this accessible EC2 instance exists among other misconfigurations — giving bad actors the opportunity they covet and creating a potential perfect storm for the organization.
In this post, we’ll look into these misconfigurations, as well as their risks and mitigation strategies.
Technical Details of the Attack Path
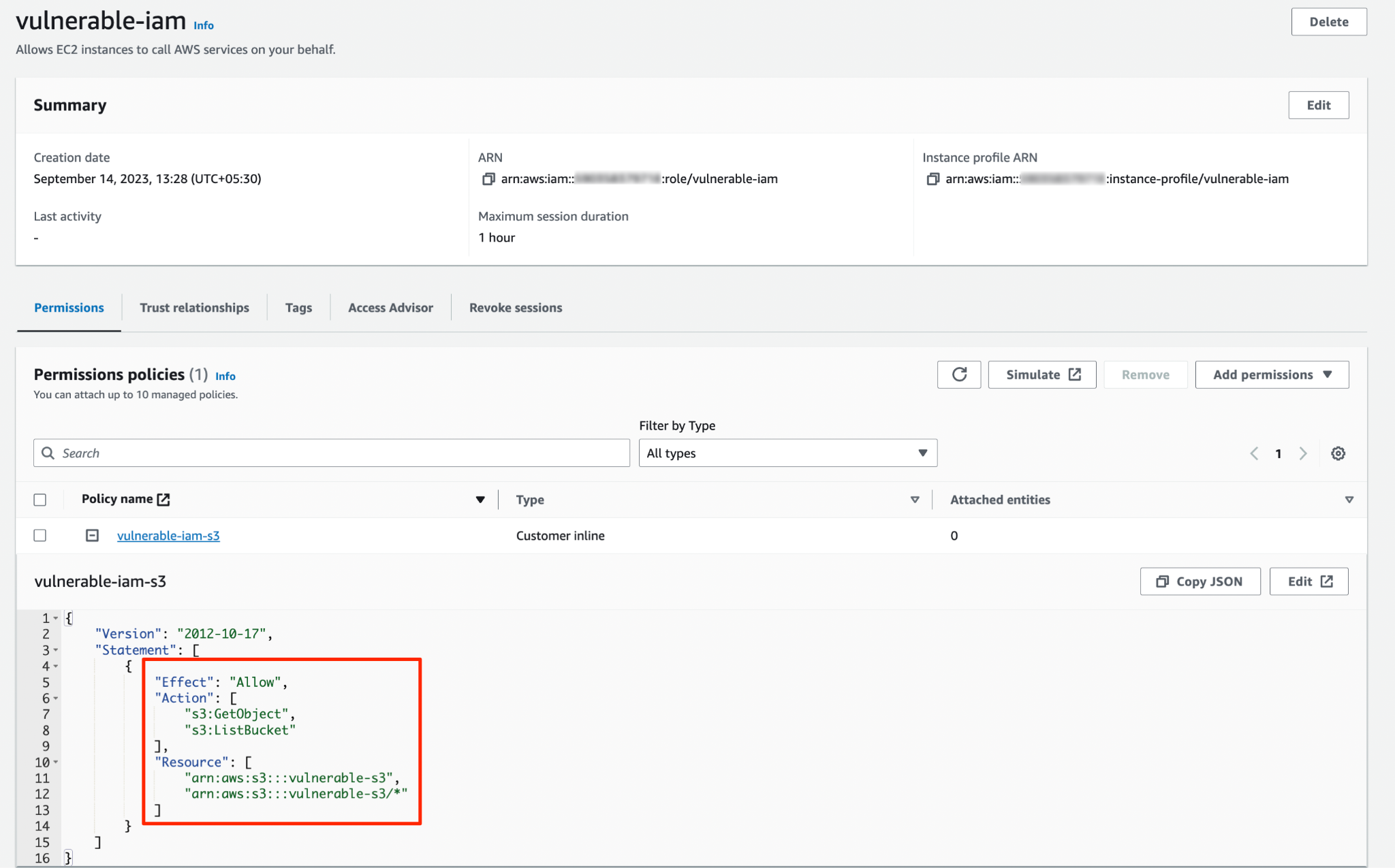
When left publicly exposed and compounded with other vulnerabilities, an EC2 instance can lead to significant problems. Specifically, an EC2 instance endowed with s3:GetObject and s3:ListObject permissions and lacking the shield of IMDSv2 can result in data exfiltration.
In this trifecta opportunity, attackers exploiting the exposed EC2 instance hit pay dirt. Finding s3:GetObject and s3:ListObject permissions gives them the keys to the bank vault, allowing them to list and retrieve whatever they wish from the specified S3 buckets. In many cases, this means access to sensitive data and “hidden” flags.
Optional IMDSv2 Configuration
AWS's Instance Metadata Service (IMDS) provides data about EC2 instances. Its enhanced version, IMDSv2, requires session-oriented requests, adding an extra layer of security. In other words, IMDSv2 makes gathering information about the EC2 instance more difficult, which reduces the likelihood of a successful attack.
Conversely, the absence of IMDSv2 opens a nearly unobstructed path to metadata containing insights into the infrastructure of the organization, possibly revealing more vulnerabilities and even direct paths to additional data.
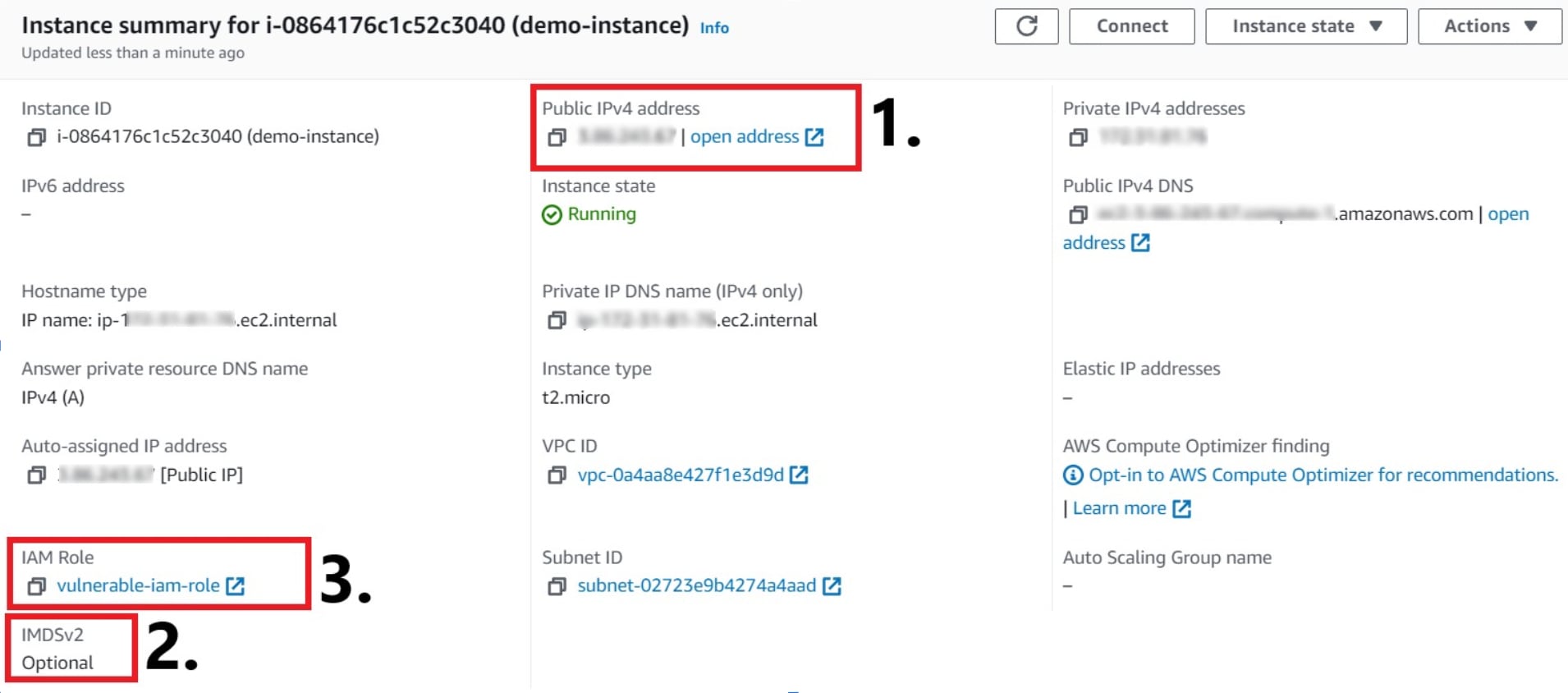
As seen in figure 2, security teams need to watch for the combination of three misconfigurations, as they open an entrypoint for attacks ranging from data breach and exfiltration to system takeover as the attacker with liberal access moves laterally through the organization’s network.
High-Volume Data Transfer Activity
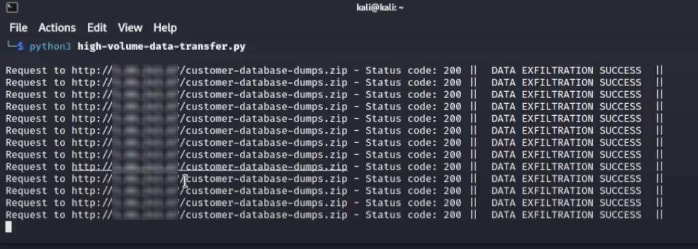
High-volume data transfer can signal data exfiltration — or data theft, the covert and unauthorized extrusion of data, which typically involves sensitive data given its targeted blackmarket value. For organizations, data breach comes with long-term costs in the way of regulatory penalties, legal liabilities, reputational damage and remediation via agreement or voluntary.
Resource owners need to remain vigilant and act swiftly when detecting malicious activity. Without continuous monitoring that can detect relevant anomalies, arresting data exfiltration is left to chance. An aberrant spike in data transfer goes unnoticed.
Exploitation and Misuse
Once attackers spot vulnerabilities such as a publicly accessible EC2 instance, they’re quick to capitalize on the opportunity. Using an array of sophisticated tools, they can easily infiltrate the system. Permissions like s3:GetObject and s3:ListObject become their gateway.
If a publicly exposed EC2 instance has excessive permissions, any application running on that instance can access the S3 buckets. The real danger lies in the misuse of the instance metadata service (IMDSv), as an attacker can easily extract IAM role credentials associated with the instance.
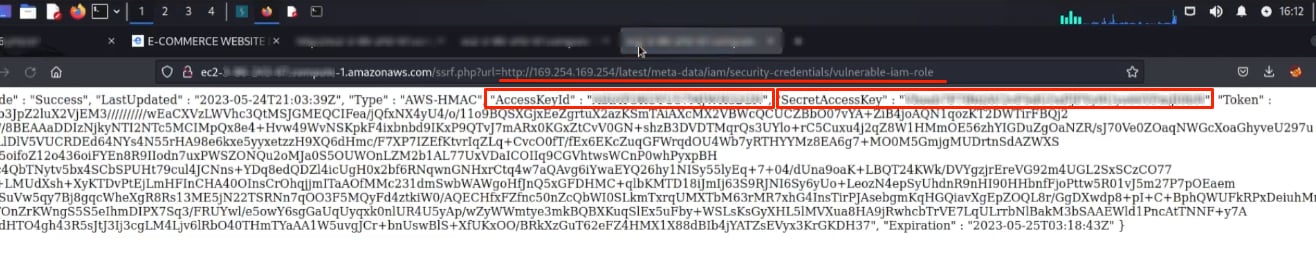
Attackers often initiate their unauthorized access by infiltrating a publicly exposed EC2 instance through an exposed service or by utilizing search engine dorks to filter and locate public instances. Once inside, attackers usually attempt to exploit vulnerabilities to interact with the metadata service endpoint (for instance, http://169.254.169.254/latest/meta-data).
In scenarios configured to Metadata Service v1 (IMDSv1), the extraction of sensitive information is unencumbered by IMDSv2’s protective authentication layer. This exploitation can snowball from a breach to escalated privileges should the breach yield secrets and credentials of the attached IAM roles.
Armed with IAM role credentials, the attacker can make authenticated AWS API requests. If the IAM role has s3:GetObject and s3:ListBucket permissions, they can list and fetch objects from S3 buckets, leading to data exfiltration.
Mitigation
Protecting digital assets in a cloud environment requires a multilayered approach to address the nuanced vulnerabilities associated with EC2 instances and their associated permissions.
Step 1
Never leave EC2 instances publicly accessible by default. Instead, apply the principle of least privilege (PoLP), granting only those permissions required for the user — machine or human — to do the job. Judiciously assign and regularly review permissions. In this context, that means s3:GetObject and s3:ListObject.
Step 2
Activate IMDSv2. Requiring a valid token to access instance metadata is good security and goes a long way in preventing unauthorized data access.
Step 3
Don’t skimp on monitoring. Watch for and respond to anomalies in data transfer patterns. Organizations need to consistently track and analyze EC2 data transfer activity.
Step 4
Awareness is the first line of defense. Regular security audits, combined with continuous education and training, will help to ensure your teams can both recognize and rectifie potential misconfigurations before they become breaches.
The Right Security Technology
Effective security begins with the right capabilities. Prisma Cloud offers a robust mechanism to tackle EC2 challenges head-on. With its unique attack path policies, it goes beyond identifying isolated vulnerabilities to connecting the dots, giving users a holistic view with insights into potential attack paths. By offering combined insights, Prisma Cloud enables organizations to not just plug individual gaps but proactively block entire attack vectors.
In a dynamic cloud environment, Prisma Cloud’s interconnected risk view ensures that security teams can prioritize and remediate the most potent threats, significantly reducing the window of opportunity for attackers.
Learn More
If you haven’t tried Prisma Cloud and would like to test drive best-in-class code-to-cloud security, we’d love for you to experience a free 30-day Prisma Cloud trial.
Related Blogs
Subscribe to Cloud Native Security Blogs!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.