How Prisma Cloud Data Security Helps Prevent Storage Breaches
In cloud infrastructure security, platform-as-a-service (PaaS) storage services like Amazon Simple Storage Service (S3), Microsoft Azure Blob Storage and Google Cloud Storage are perhaps the most common source of data breaches. The prevalence of these breaches demonstrates that users struggle to implement well-known best practices for securing these services. While there are a lot of things users can do immediately to improve security posture, it’s often too difficult to manage those interventions when a cloud footprint comprises thousands of workloads.
Let's look at how Prisma Cloud can help.
How Does Prisma Cloud Protect Data?
Prisma Cloud taps into cloud providers’ APIs to analyze network traffic, user activity and configurations of systems and services, then correlates these disparate data sets to help users quickly prioritize risk and reduce their time to remediation (TTR). Agents can also be deployed to secure your host, container and serverless computing environments against vulnerabilities, malware and compliance violations across the entire software lifecycle.
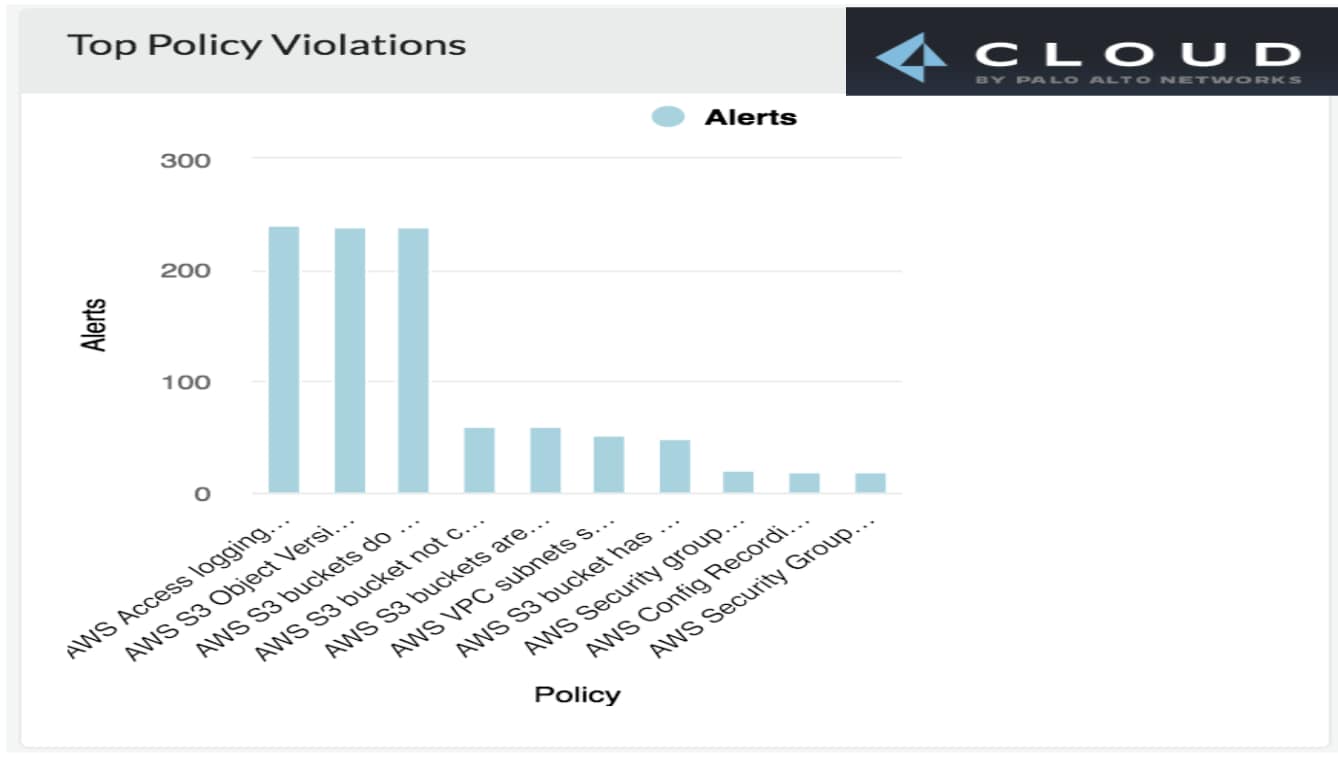
The chart above shows the most common policy violations discovered by Prisma Cloud. Unsurprisingly, the top violations are on Amazon S3 policies, so let’s now take a deeper look into how Prisma Cloud can help customers avoid the costly mistakes that other companies have already made.
Continuous Configuration Monitoring
Prisma Cloud ships with over 650 out-of-box protection policies and provides continuous resource monitoring. The following shows the types of policies that can help prevent S3 data breaches:
- Detect publicly exposed S3 buckets
- Detect overly permissive IAM roles, ACLs and bucket policies
- Detect S3 buckets without encryption enabled
- Detect S3 buckets without versioning, configured without MFA Delete
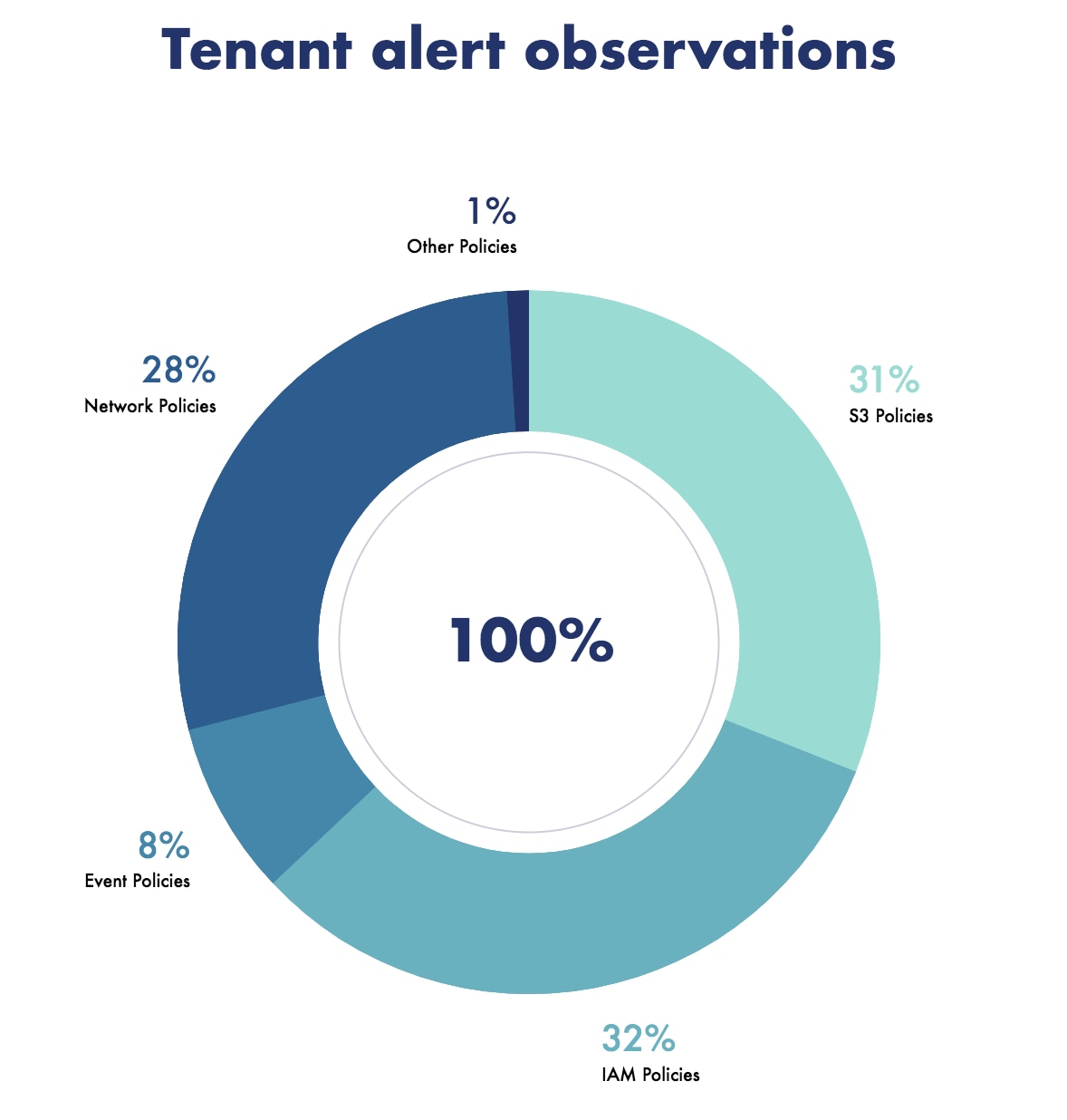
The following chart shows the top misconfiguration policy alerts amongst all our customers. Our stats show that 31% of customers have had alerts for misconfigured S3 settings and 32% have them for misconfigured IAM policies.
Prisma Cloud can either automatically remediate these misconfigurations or just alert users to a vulnerability or misconfiguration, potentially saving organizations from a devastating breach and data exfiltration.
Console and API Activity Monitoring with Anomaly Detection
Prisma Cloud ingests AWS CloudTrail logs from cloud providers to monitor all console and API access to your cloud environments. This helps security teams monitor privileged activities and detect anomalous events. This enables customers to:
- Detect malicious activity from a user or IAM-role that is accessing the buckets from an unknown or unusual location inside/outside of a cloud provider boundary.
- Craft a custom query to create alerts for activities that pertain to a specified cloud activity.
The following shows tracked activities and events specific to Amazon S3, Elastic Compute Cloud (EC2) and IAM resources. Our research shows that:
- About 8% of all alerts are related to event policies.
- The most malicious activities tracked are deletion of buckets, changing bucket policies and ACLs, attaching roles and deleting roles by unauthorized entities.
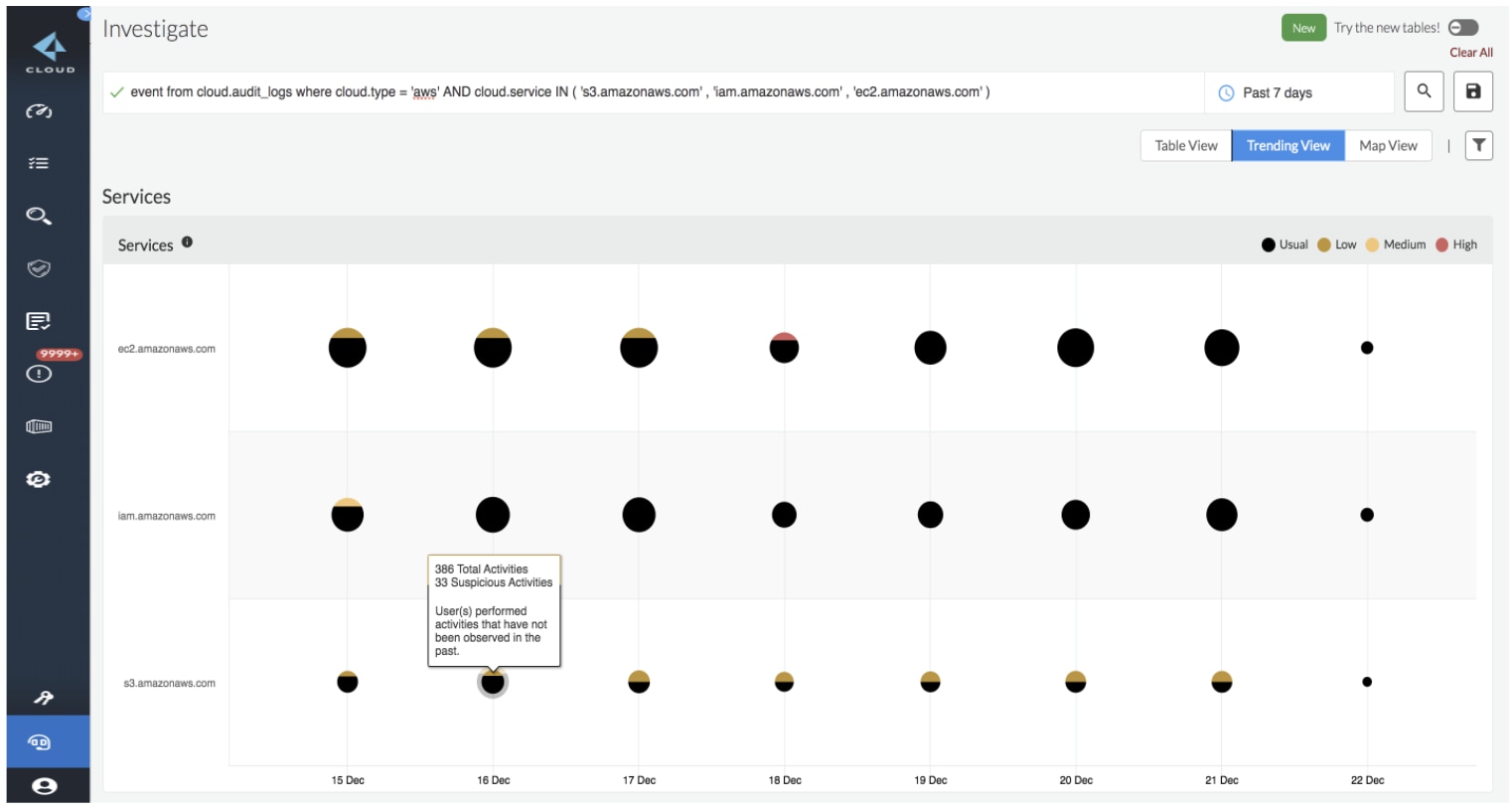
Prisma Cloud delivers high fidelity alerts that can detect malicious activities before a breach occurs. Adding in the new IAM Security capabilities, users can tighten up their IAM policies to further reduce their risk potential.
Performing Network Analytics
Prisma Cloud monitors "north-south" as well as "east-west" traffic. This helps users detect risks such as network intrusions, cryptojacking and insider threats. Additional network monitoring includes:
- VPC flow log analysis to help identify the amount and type of data exfiltrated, and forensics data such as which IP address accessed the environments.
- Graph network topology to discover what resources were accessed by whom.
The following map shows how much data specific resources receive from unknown sources. Our stats show that 28% of alerts are network policy violations. Specifically, unauthorized accessing of ports, requests from suspicious/internet IPs, database access from malicious users, and so on.
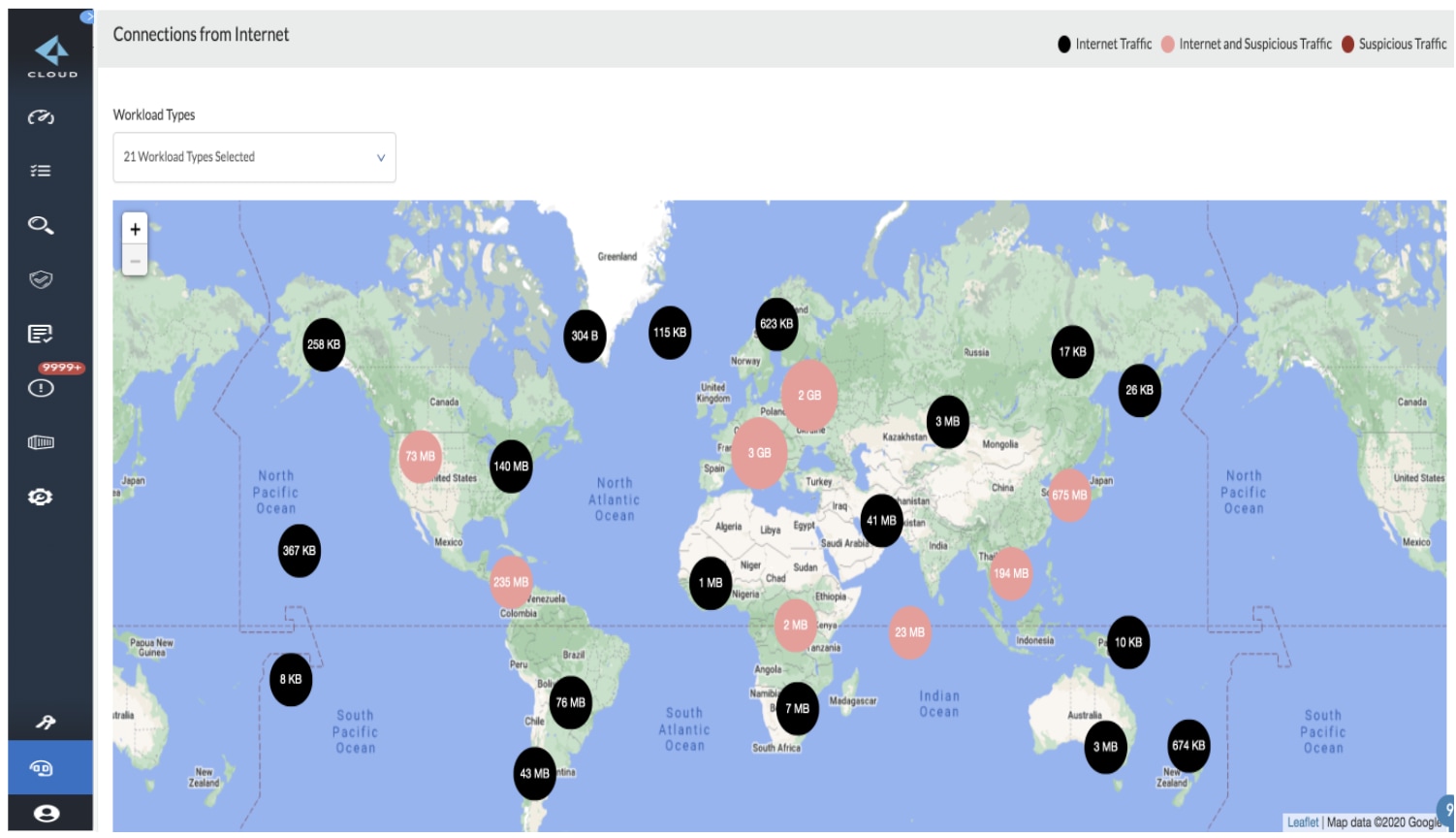
Prisma Cloud helps customers detect VPC network anomalies so they can stop suspicious or malicious activities such as port scans, port sweeps and spambot activities, amongst others.
Prisma Cloud Data Security
Prisma Cloud Data Security provides three key capabilities: public exposure scanning, sensitive data scanning and malware detection scanning. One challenge for many cybersecurity professionals is public objects stored in private buckets. Often these publicly accessible objects go undetected as they are obfuscated by the private buckets that are hosting them. With Prisma Cloud, our customers can detect these “hidden” public objects, determine if these objects contain sensitive data and uncover if these objects contain any malware.
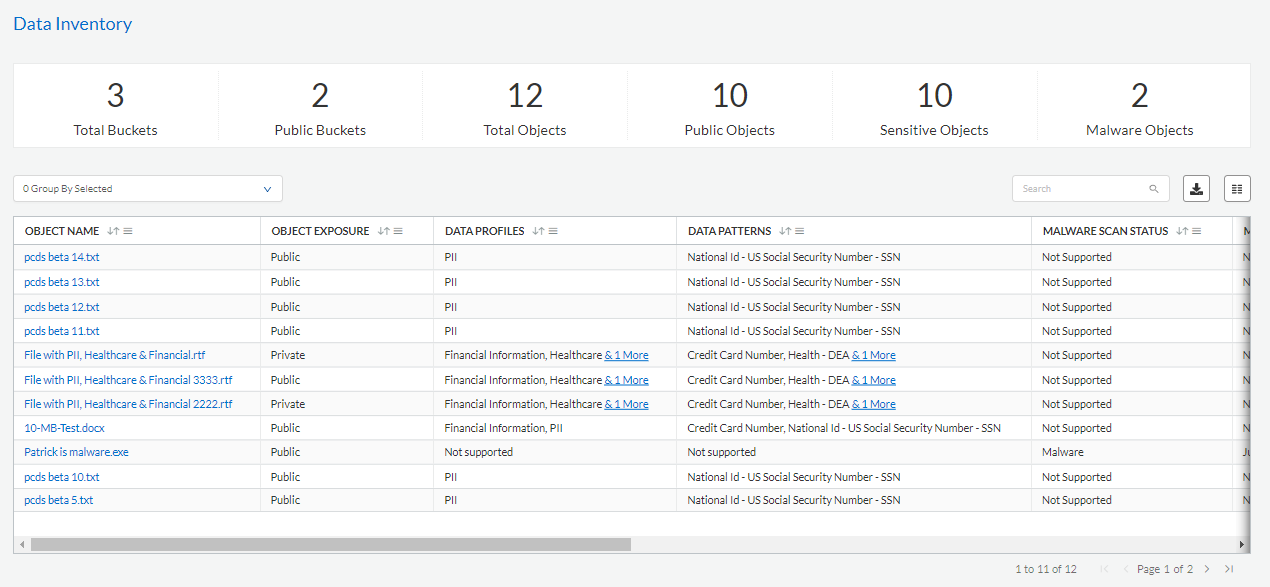
With more than 100 predefined data profiles and patterns, users can immediately start scanning their data for any sensitive data like personally identifiable information (PII), healthcare information, intellectual property or financial data.
Conclusion
Prisma Cloud provides security at all stages of the software delivery process. It provides visibility into all your resources deployed across different environments, and checks adherence against compliance standards and security best practices for your assets at runtime, including IaC templates and container images, even before resources are deployed.
It monitors your resources deployed in cloud environments for security and compliance risks. Because the platform automatically discovers new resources as they are deployed, it enables teams to implement policy guardrails and ensure resource configurations adhere to best practices. It also integrates seamlessly into DevOps and SecOps workflows to quickly resolve issues. This streamlines the process of identifying issues, detecting and responding to a list of prioritized risks to maintaining an agile development approach.
For more information on protecting your cloud data, visit our Prisma Cloud Data Security product page.
Related Blogs
Subscribe to Cloud Native Security Blogs!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.