High-Severity Vulnerabilities Discovered in WebM Project’s Libraries
Two high-heap overflow vulnerabilities were discovered in the libwebp and libvpx libraries. These vulnerabilities, which CISA identified as CVE-2023-4863 and CVE-2023-5217 in their Known Exploited Vulnerabilities (KEV) catalog, are now actively exploited in the wild.
Because CVE-2023-4863 and CVE-2023-5217 pose a significant risk, we recommend that you take immediate action to apply patches and protect your systems. In this blog, we’ll outline why the vulnerabilities are of critical concern, and we’ll provide best practices to help you protect your organization from attack.
What Are the Libwebp and Libvpx Libraries?
The libwebp library, developed by Google, is an open-source implementation of the WebP image format. WebP is a modern image format that supports both lossless and lossy compression for web images, enabling the delivery of high-quality images with smaller file sizes.
The libwebp library encodes and decodes images in the WebP format. It’s used extensively in various applications such as web browsers and image processing tools.
The libvxp library, an open-source project by the WebM project, provides reference implementations of the VP8 and VP9 video coding formats.
Vulnerability Discovery Timeline
On September 11, 2023, Google released a security fix for a heap buffer overflow vulnerability, CVE-2023-4863, that affected Google Chrome’s WebP. The vulnerability received a high common vulnerability scoring system (CVSS) score of 8.8.
Two weeks later, Google released another vulnerability, CVE-2023-5129. Google indicated that this new vulnerability affected the libwebp library. Then, on September 27, 2023, Google rejected CVE-2023-5129 as a duplicate of CVE-2023-4863 and added the libwebp library vulnerability to the original Chrome vulnerability.
On that same day, Google released a security fix for a new vulnerability, CVE-2023-5217, that impacted Google Chrome’s libvpx library. This vulnerability received a high CVSS score of 8.8. The day after that, the CVE-2023-5217 vulnerability was connected to the libvpx library — which is a component of many applications in addition to Chrome.
What Is CVE-2023-4863?
CVE-2023-4863 is a buffer overflow vulnerability in the libwebp library. To exploit this vulnerability, a remote attacker creates a malicious WebP image file. When an application that uses the libwebp library processes the WebP file, it triggers an overflow. This overflow, in turn, allows attackers to compromise the affected system through either remote code execution (RCE) or a denial of service (DoS) attack.
This vulnerability is likely related to CVE-2023-41064, a zero-click vulnerability that bad actors exploited in the BLASTPASS attack.
What Is CVE-2023-5217?
CVE-2023-5217 is a heap buffer overflow in VP8 encoding in libvpx library. When an attacker controls a malicious VP8 video stream, they can corrupt the heap and crash the application.
Google first disclosed CVE-2023-5217 as a Chrome vulnerability. However, in a similar way to CVE-2023-4863, experts realized the root of this vulnerability was in libvpx library itself. Given the location of the vulnerability, it affects dependent applications such as Telegram, FFmpeg and others. Currently, it appears less widespread than the libwebp vulnerability.
Who Is Affected by CVE-2023-4863 and CVE-2023-5217?
Experts assumed these two vulnerabilities only affected browsers like Google Chrome, but recent information indicates the scope of the vulnerability is wider. CVE-2023-4863 and CVE-2023-5217 affect any software or system that relies on the libwebp library for image processing.
The CVE-2023-4863 vulnerability, in other words, impacts web browsers like Microsoft Edge and Mozilla Firefox, Chromium-based applications such as Electron and applications that utilize web browsers such as 1Password and Telegram. CVE-2023-4863 also affects operating systems that rely on the libwebp library, in addition to applications that use the libwebp library itself. Affected applications include Pillow (Python), node-webp (Nodejs), ImageIO (Java), MiniMagick (Ruby), go-webp (GoLang) and others. Usage of the libvpx library is less widespread, but there are some notable libraries and applications — such as FFmpeg, Natron and more — that depend on libvpx.
The likelihood of exploit via the remote code execution attack path depends on several factors — the specific vulnerability, the targeted software and the bad actor’s knowledge of the targeted software. That being said, bad actors generally have a low probability of successfully exploiting heap overflow vulnerabilities via RCE due to the heap's unpredictable nature and the absence of return addresses.
Modern systems employ security measures such as address space layout randomization (ASLR) — a technique that randomizes memory locations — and heap integrity checks to detect abnormal changes. When combined with the heap's dynamic layout, security measures make it much more difficult for bad actors to successfully instigate remote code execution attacks.
Despite the low probability of bad actors completing a successful remote code execution attack, we recommend that you apply a fix to your affected assets as soon as possible. CISA has already recorded examples of bad actors exploiting these vulnerabilities in the real world, and it’s possible that bad actors will use other methods like a Denial of Service (DoS) attack to access your systems.
The open-source projects webmproject/libwebp and webmproject/libvpx released fixes (in version 1.3.2 and 1.13.1, respectively), and other operating systems either patched their affected artifacts or are running an ongoing analysis of the issue now.
In addition to patching your systems, we recommend that you get visibility into your affected workloads and artifacts so that you can ensure you’re fully patched and protected from exploit. Let’s walk through how Prisma Cloud helps simplify this process.
Responding to CVE-2023-4863 and CVE-2023-5217 with Prisma Cloud
To find affected workloads in your environments, you can use Prisma Cloud’s Vulnerability Explorer. Simply search for CVE-2023-4863 to view at-risk workloads:
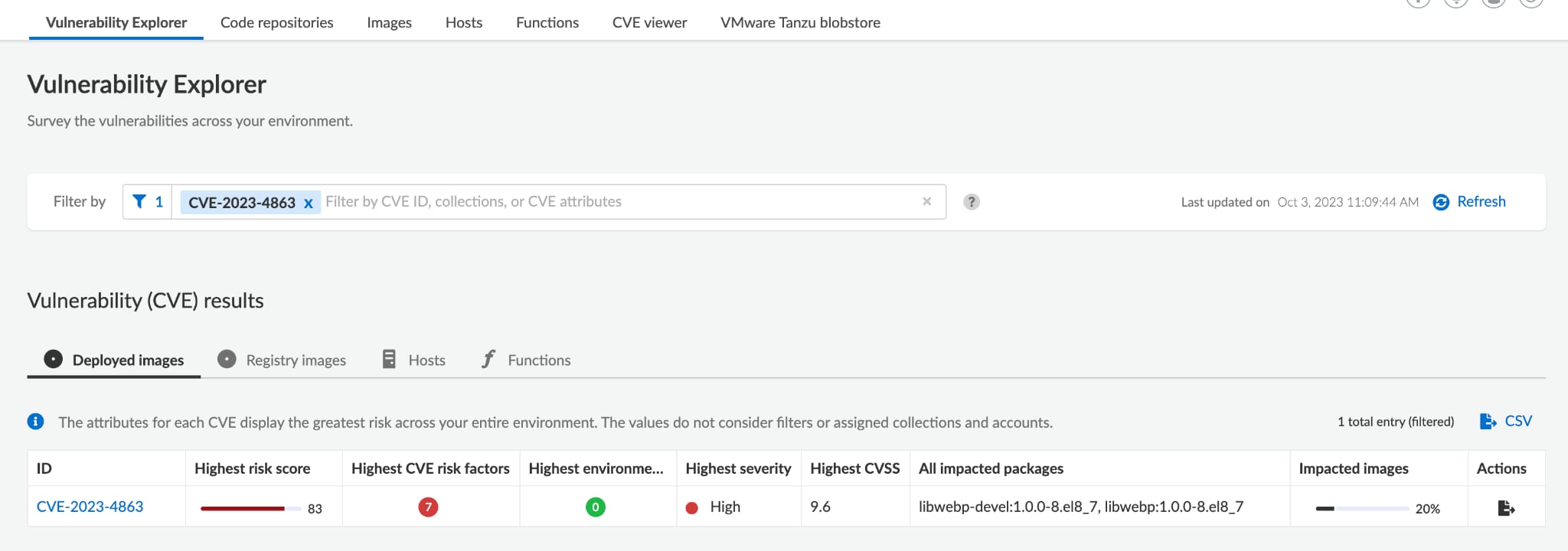
You can also check the CVE viewer to find all of your affected artifacts:
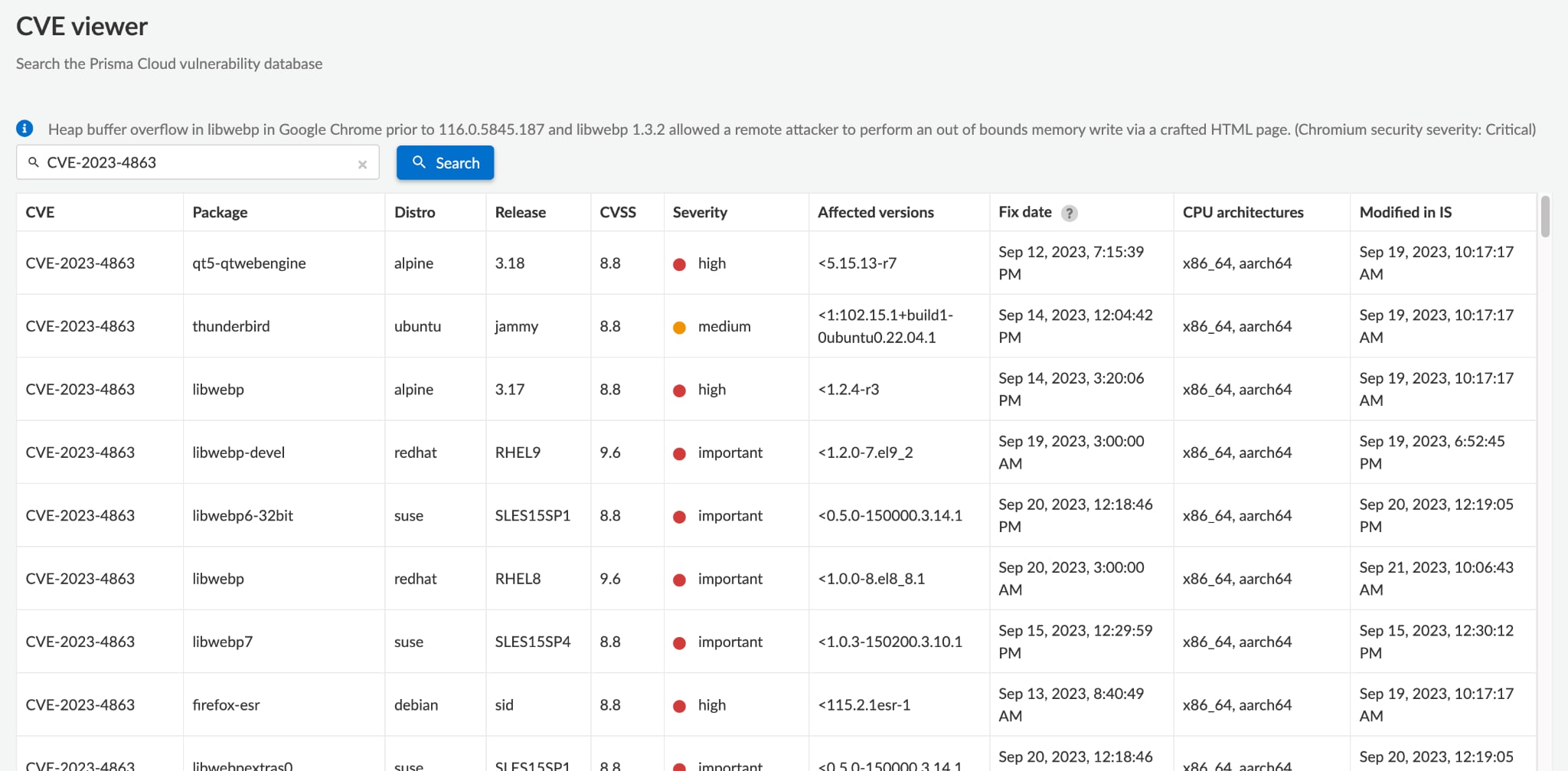
With Prisma Cloud, you can detect, block and remediate these vulnerabilities across all of your code repositories.
To identify packages that need patches, navigate to either the Prisma Cloud’s Projects, software bill of materials (SBOM) or Supply Chain pages and view the banner at the top of the page. The platform will surface an alert with information detailing where it identified the vulnerability across both your direct and transitive dependencies.
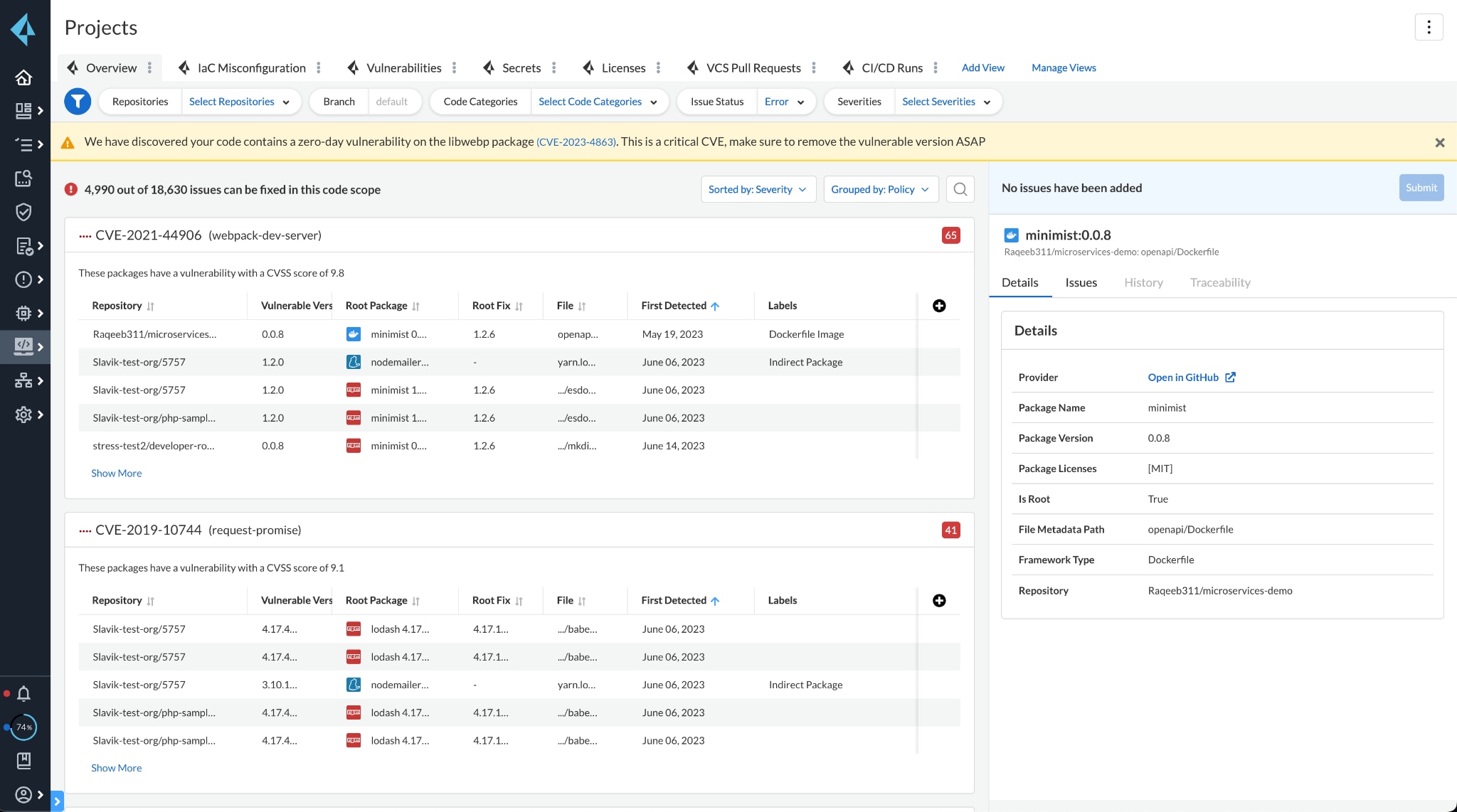
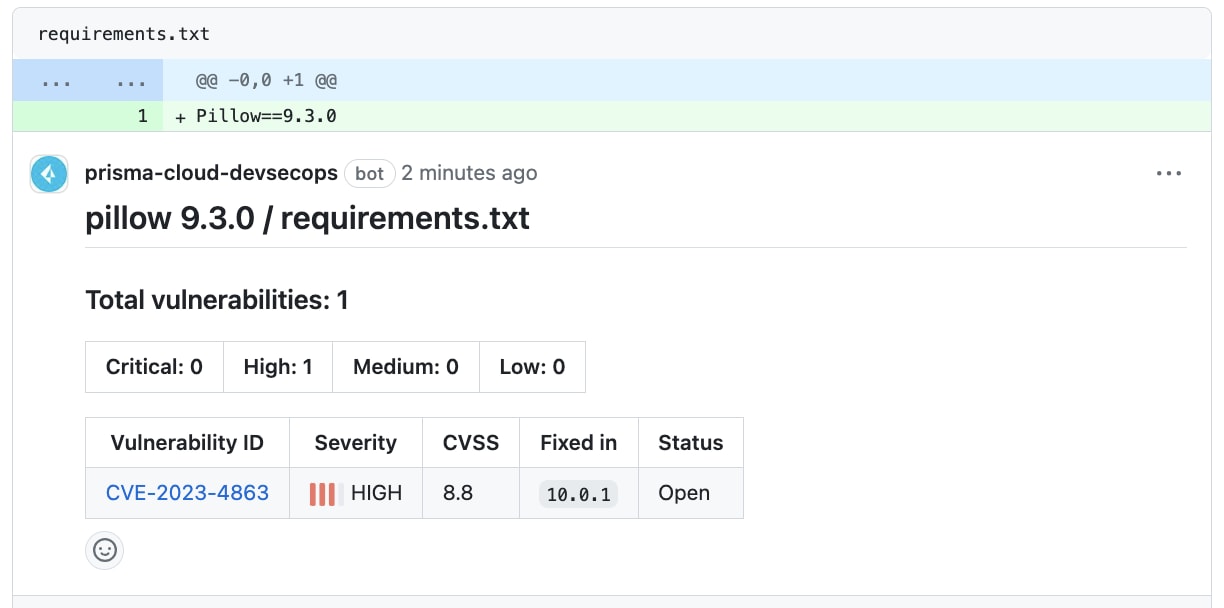
You can set up additional guardrails by setting your Enforcement Settings to hard-fail on High, which blocks all impacted packages until they’re updated.
Proactively Responding to Vulnerabilities with Prisma Cloud
Given the impact of CVE-2023-4863 and CVE-2023-5217, we strongly recommend that you patch libwebp, libvxp and any applications or services that use the vulnerable version of these libraries as soon as possible. With Prisma Cloud, you can quickly respond to these newly-discovered vulnerabilities and protect your organization from attack.
If you haven’t tried Prisma Cloud and would like to test drive best-in-class code-to-cloud security, we invite you to experience a free 30-day trial.
Related Blogs
Subscribe to Cloud Native Security Blogs!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.