Today’s Attack Trends — Unit 42 Incident Response Report
This post is also available in: 日本語 (Japanese)
Each year, Unit 42 Incident Response and Threat Intelligence teams help hundreds of organizations assess, respond and recover from cyberattacks. Along the way, we collect data about these incidents.
Our 2024 Unit 42 Incident Response Report will help you understand the threats that matter. It's based on real incident data and our security consultants' experience.
Read the report to learn how to safeguard your organization's assets and operations:
- Threat actors, their methods and their targets.
- Statistics and data about the incidents our team worked on.
- A spotlight on the Muddled Libra threat group – one of the most damaging ransomware groups today.
- How artificial intelligence affects cybersecurity now and in the future.
- In-depth recommendations for leaders and defenders.
As an executive responsible for safeguarding your organization, you'll find analysis and recommendations to help you make strategic decisions about where to invest your time, resources and budget.
Use the following takeaways to start a conversation with your leadership team and encourage them to download the 2024 Unit 42 Incident Response Report to review the expert analysis in full.
Key Takeaway — Speed Is Critical
Speed matters. Attackers are acting faster, not only at identifying vulnerabilities to exploit, but also stealing data after they do.
- In 2023, the median time from compromise to data exfiltration fell to just two days, which is much faster than the nine days we observed in 2021.
- In approximately 45% of cases this year, attackers exfiltrated data within a day of compromise.
- For non-extortion-related incidents in 2022 and 2023, the median time to data exfiltration has consistently remained under one day, meaning defenders must react to a ransom attack in less than 24 hours.
Attacker "dwell time" (the duration between when an attacker was detected and the earliest evidence of their presence) has also accelerated. The median dwell time was just 13 days in 2023 – half of what it was in 2021.
But, that's not necessarily a bad thing. Other data in our report indicates it may be that defenders are improving.
Key Takeaway – Software Vulnerabilities Remain Important
In 2023, attackers used internet-facing vulnerabilities to get into systems more often. This tactic occurred in 38.6% of our IR cases, making it the leading method of initial access.
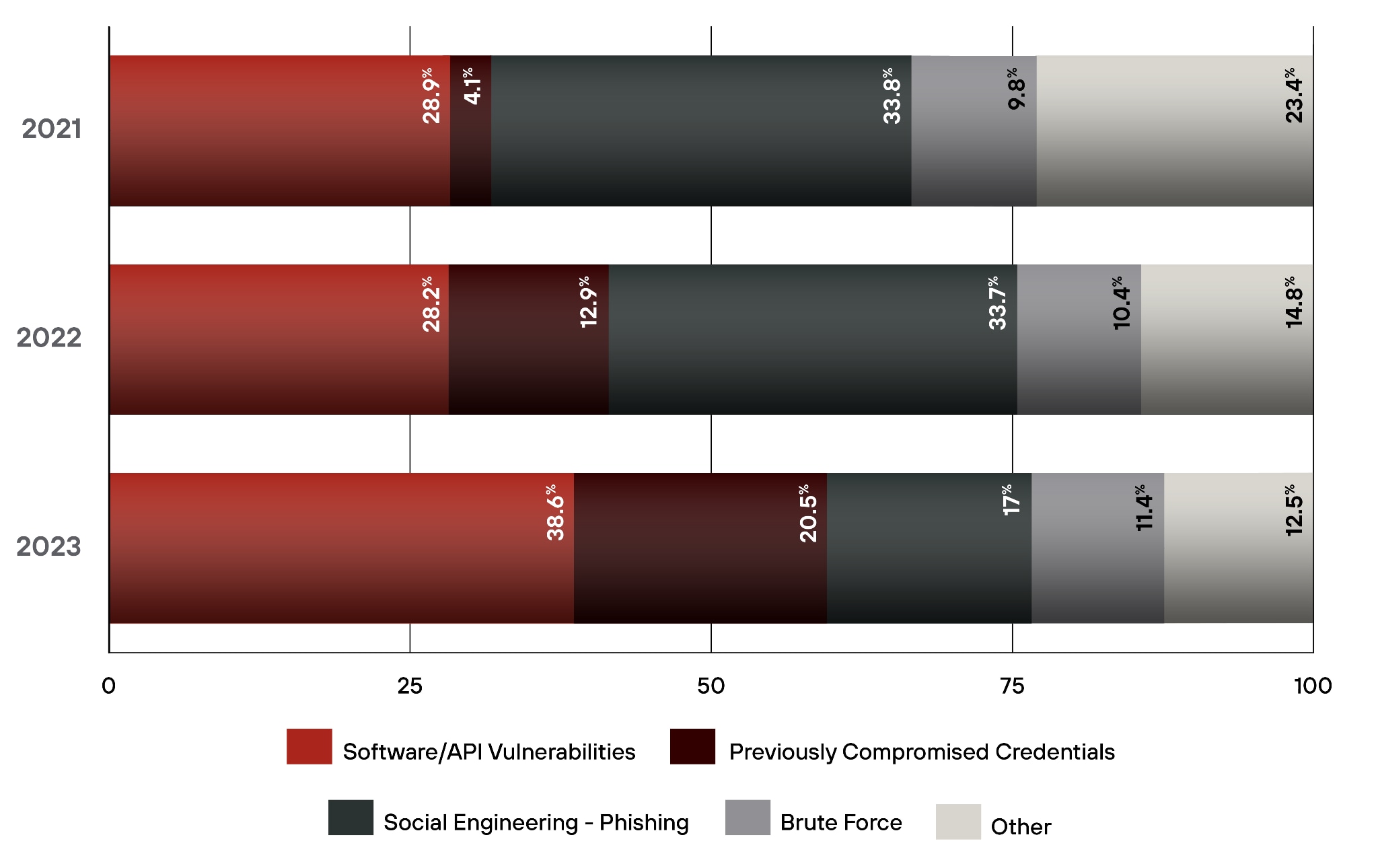
Vulnerability exploitation surpassed phishing as the leading initial access method. Exploiting weaknesses in web applications and internet-facing software played a significant role in some of the largest and most automated cyberattacks.
This change emphasizes the importance of good patching practices and attack surface reduction. While that work can be challenging for large organizations to implement comprehensively, organizations must act swiftly and use multiple layers of defense to protect themselves. If you don't find and fix the exposure, attackers will.
Key Takeaway – Threat Actors Continue to Use Sophisticated Approaches
Cyberthreat actors are adopting sophisticated strategies, organizing into specialized teams and effectively leveraging IT, cloud and security tools. They've become more efficient, defining and repeating processes for quicker results.
Attackers are now using defenders' own security tools against them, compromising highly privileged accounts and infrastructure to access tools and move within their target network. Vigilance and proactive defense are crucial as threat actors adapt and innovate.
Five Recommendations to Better Protect Your Organization from Cyberthreats in 2024
Here are five key recommendations from our cybersecurity consultants to enhance your cybersecurity posture based on our insights from 2023's cyber incidents:
- Improve Organizational Visibility: Prioritize comprehensive visibility across your network, cloud and endpoints. Actively monitor unmonitored areas, manage vulnerabilities effectively with robust patch management and secure internet-exposed resources such as remote desktops and cloud workloads. Insufficient and incomprehensive visibility makes incidents more frequent and more severe.
- Simplify: Streamline the complexity of cybersecurity operations by consolidating point products. Centralize and correlate security telemetry data from various sources into an analytics platform. The best strategy enhances threat detection and response efficiency with machine learning (ML) and analytics.
- Enforce Zero Trust Principles: Implement a Zero Trust security strategy. Deploy robust authentication methods, network segmentation, lateral movement prevention, Layer 7 threat prevention and the principle of least privilege. Prioritize comprehensive multifactor authentication (MFA), passwordless solutions and single sign-on (SSO). Regularly audit and update authentication systems.
- Control Application Access: Control application usage and eliminate implicit trust between application components. Restrict access to specific applications, especially those exploited by threat actors. Emphasize monitoring and alerting on remote management applications and unsanctioned file-hosting services.
- Segment Networks: Employ network segmentation to reduce the attack surface and confine breaches to isolated zones. Implement Zero Trust network access (ZTNA) to verify users and grant access based on identity and context policies to ensure users or devices are not trusted until continuously verified.
In addition to the findings outlined here, the report spotlights current threats as well as the impact of emerging technologies, including artificial intelligence (AI) Social Engineering, Large Language Models (LLMs), DevSec and DevSecOps, as well as the continued use of cloud-based technologies.
Download the complete 2024 Unit 42 Incident Response Report to learn more in-depth recommendations for improving your security posture and focus on the risks you need to mitigate.
Get in Touch
Want help preparing for or responding to a cyber incident? Call in the experts.
If you think you may have been impacted by a cyber incident or have specific concerns about any incident types discussed here, please contact Unit 42. The Unit 42 Incident Response team is available 24/7/365. If you have cyber insurance, you can request Unit 42 by name. You can also take preventative action by requesting our cyber risk management services.
Related Blogs
Subscribe to the Newsletter!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.