Playbook of the Week: Automated Ghost Busting with Cortex XSOAR
“Those houses haunt in which we leave / Something undone.” So begins Ghosts, a lyrical sonnet on haunted houses, by Elizabeth Jennings, a major figure in The Movement, a 1950s British poetry movement, and ranked as one of the finest British poets.
Have we left “ghosts” in our cyber homes, be they disconnected assets or former employee accounts with privileged access to internal systems?
In this blog, we will cover a collection of playbooks to pique your interest in automation as a means to address the unwanted guests in your network and ensure nothing is left undone.
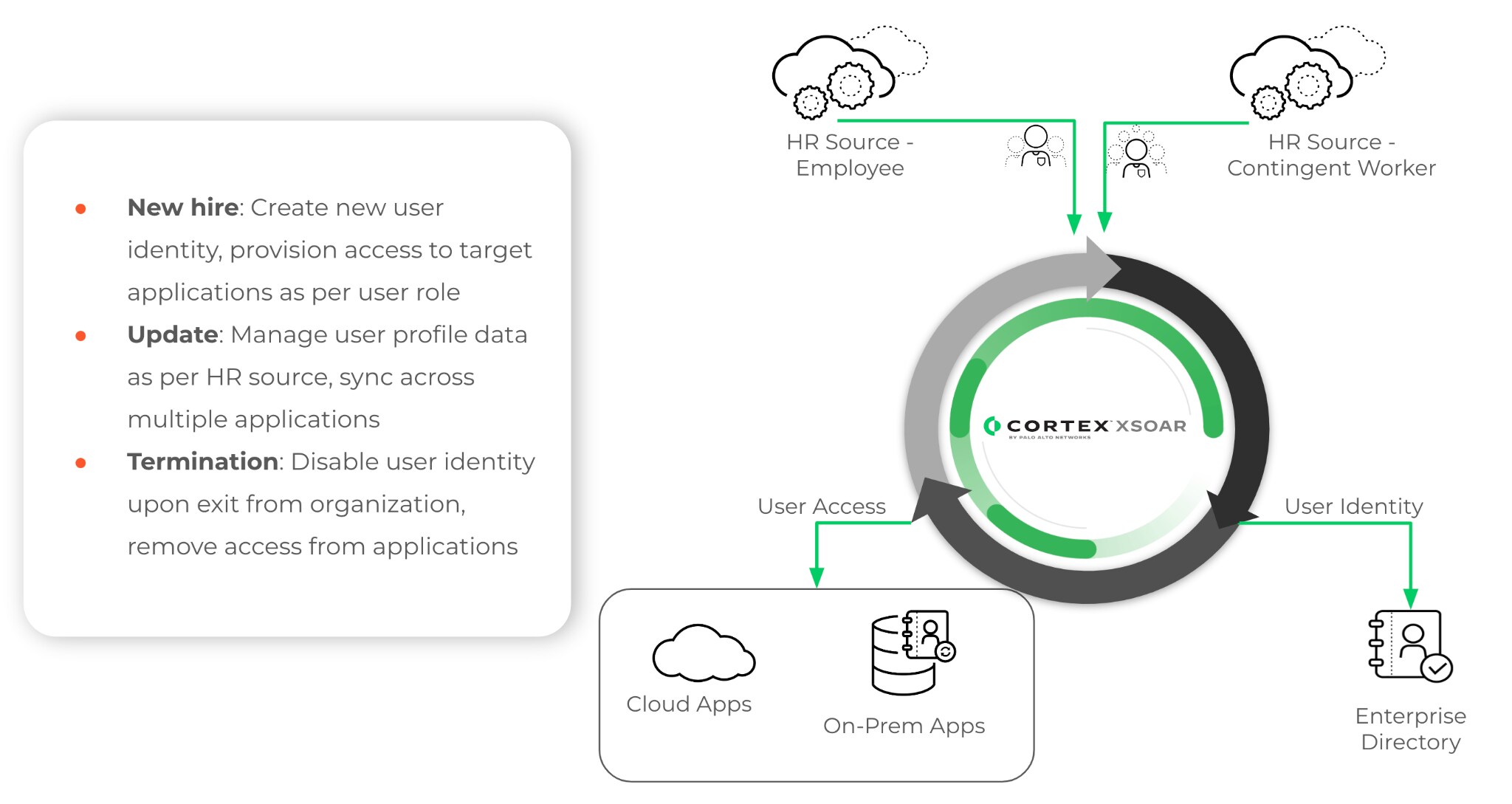
Employee Offboarding
The process of employee offboarding is time-consuming and involves multiple processes across multiple departments. If the offboarding process is incomplete and actions are missed, this potentially exposes a company to data leaks and unauthorized access. Recent Unit42 research analyzing 680K identities from 200 organizations found that nearly all (99%) lacked proper IAM policy controls to be secure. By leveraging the Cortex XSOAR employee offboarding content pack, you can streamline the process, track your offboarding checklist, and automate any tasks that don’t require physical human interaction. These tasks can include:
- Scheduling a time for the offboarding process to begin.
- Gathering employee and manager information from various sources such as Active Directory, Okta, Duo, Google, ServiceNow, and more.
- Delegating permissions and access from the offboarded employee to the manager.
- Revoking roles, security, and access permissions for the offboarded employee and resetting passwords.
- Retaining important employee information for legal purposes, for a configurable period of time.
- Removing employee information from all systems or applying special policies for offboarded employees.
In fact, our own Palo Alto Networks Identity Services department uses XSOAR to onboard and offboard users across multiple applications including Slack, Zoom, ServiceNow, etc. The team leveraged pre-built XSOAR connectors and playbooks to build custom automated workflows and apply automation to over fifty applications.
Of course, the converse is true and you can apply automation to the onboarding process, but today we are talking about departed users.
If you happen to use Code42 for insider threat hunting, the Code42 Insider Threat Remediation content pack helps you determine sanctioned from unsanctioned activity and take automatic actions to shut down suspicious activity. We will be covering that content pack in more detail in an upcoming blog. As a preview, one of the playbooks included in this pack adds a departing employee to your Code42 Departing Employee list from your ticketing system ensuring your list is always kept up-to-date.
Bringing Rogue Assets Under Management
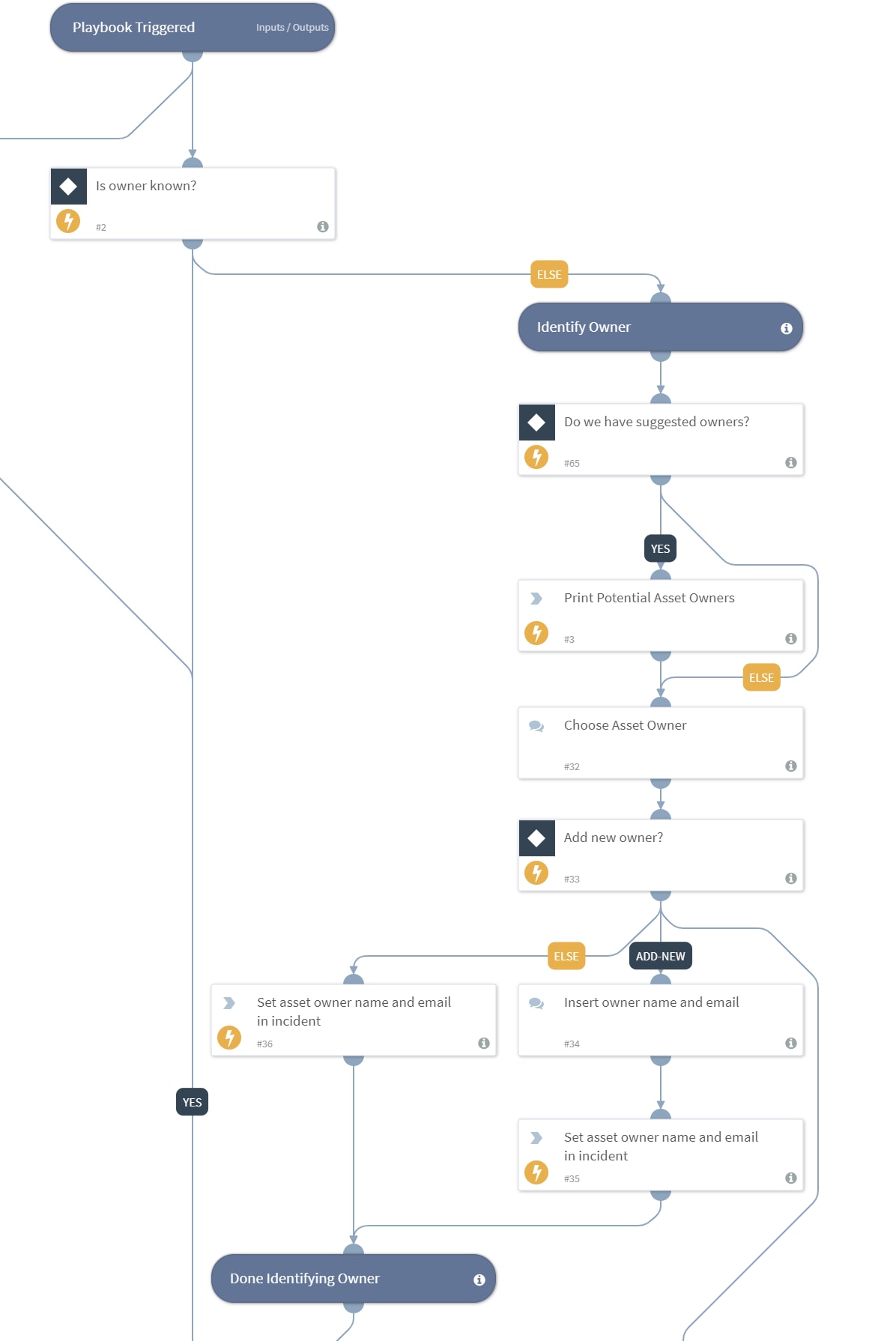
The Shadow IT content pack helps you chase down unsanctioned resources when an alert comes in. For example, the Handle Shadow IT Incident playbook in this pack helps the analyst to find the owner of the resource based on existing evidence. The playbook then marks the service indicators (IP or FQDN) with a Shadow IT tag. The possible owner and their manager are notified and onboarding of the asset on Prisma Cloud is triggered through a decision made by the analyst.
Corralling Unmanaged Cloud Assets
Our Cortex Xpanse content pack provides full coverage of the Xpanse Expander product capabilities to allow SOCs to automate the discovery, management, and defense of their company's attack surface. The integrations included in the pack enable fetching and mirroring of Xpanse Issues into Cortex XSOAR incidents and ingestion of indicators (IPs, domains, and certificates) referring to the corporate network perimeter as discovered by Xpanse. Through a collection of playbooks, you can correlate the discovered information with data provided from internal security systems (Palo Alto Networks Cortex Data Lake, Prisma Cloud, and Panorama, Active Directory, Splunk SIEM, etc.) to help pinpoint the right owners of assets and automate remediation.
Channeling the Disconnected
This playbook, which is a part of the Cortex XDR content pack, helps you run jobs to periodically query for disconnected Cortex XDR endpoints. The playbook can output a CSV report that can be emailed to recipients. A handy tool for XDR customers to monitor their XDR agents.
Another playbook along the same lines is the Palo Alto NGFW TS Agent Cleanup playbook which is part of the NGFW TS Agent Deployment content pack . With this playbook, you can run jobs to clean up disconnected terminal server (TS) agents. This is especially handy in dynamic Virtual Desktop Infrastructure (VDI) environments if you are leveraging terminal servers to deliver virtual desktops to users.
To protect these critical resources, NGFW TS agents are deployed to each virtual server. Since terminal server capacity is dynamic, terminal servers are constantly spun up and down and each agent has to be registered and deregistered with NGFW. If these agents are not deregistered, it can result in thousands of log errors. So the TS Agent Cleanup playbook ensures you don’t have these TS agent “ghosts” lying around spooking up your logs. And, if this use case is of interest to you, the content pack automates the full deployment, registration, and deregistration process.
We hope this collection will inspire ideas for automating various housekeeping tasks associated with keeping ghost assets and users under control.
As for things that go bump in the night in your house, well let’s just say you are on your own here. Happy Haunting!
Don’t have Cortex XSOAR? Download our free Community Edition today to test out this playbook and hundreds more automations for common use cases you deal with daily in your security operations or SOC.
Related Blogs
Subscribe to Security Operations Blogs!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.