Building a Zero Trust Framework for Cloud Native Applications
Companies have entered a digital pivot: applications driving business impact are increasingly moving to the cloud. Organizations moving to the cloud are finding themselves navigating new challenges. While development and DevOps teams have modernized their applications with cloud native development workflows and modern architectures, cybersecurity teams struggle to deploy new tools and technologies every time a new security risk is highlighted. This is where Zero Trust makes a difference.
According to the Gartner Predicts 2022: Consolidated Security Platforms Are the Future report, “Organizations have manually stitched together DevSecOps with 10 or more disparate security tools — some old and some new — each with siloed responsibility and view of application risk.”
Managing risk in cloud native environments becomes overwhelming based on poorly integrated solutions. Organizations need a strategic cybersecurity approach that fits their cloud transformation. Zero Trust is an opportunity to modernize and rebuild security.
What is Zero Trust?
Zero Trust is a strategic approach to cybersecurity that secures an organization by eliminating implicit trust and continuously validating every stage of a digital interaction.
The added advantage of Zero Trust in cloud native environments is simplicity. Instead of deploying new point tools to address new security risks, security teams can continuously run the same security checks regardless of the situation.
At Palo Alto Networks, our framework encompasses identity, devices/workloads, access, and transactions to enable a Zero Trust enterprise for users, applications, and infrastructure.
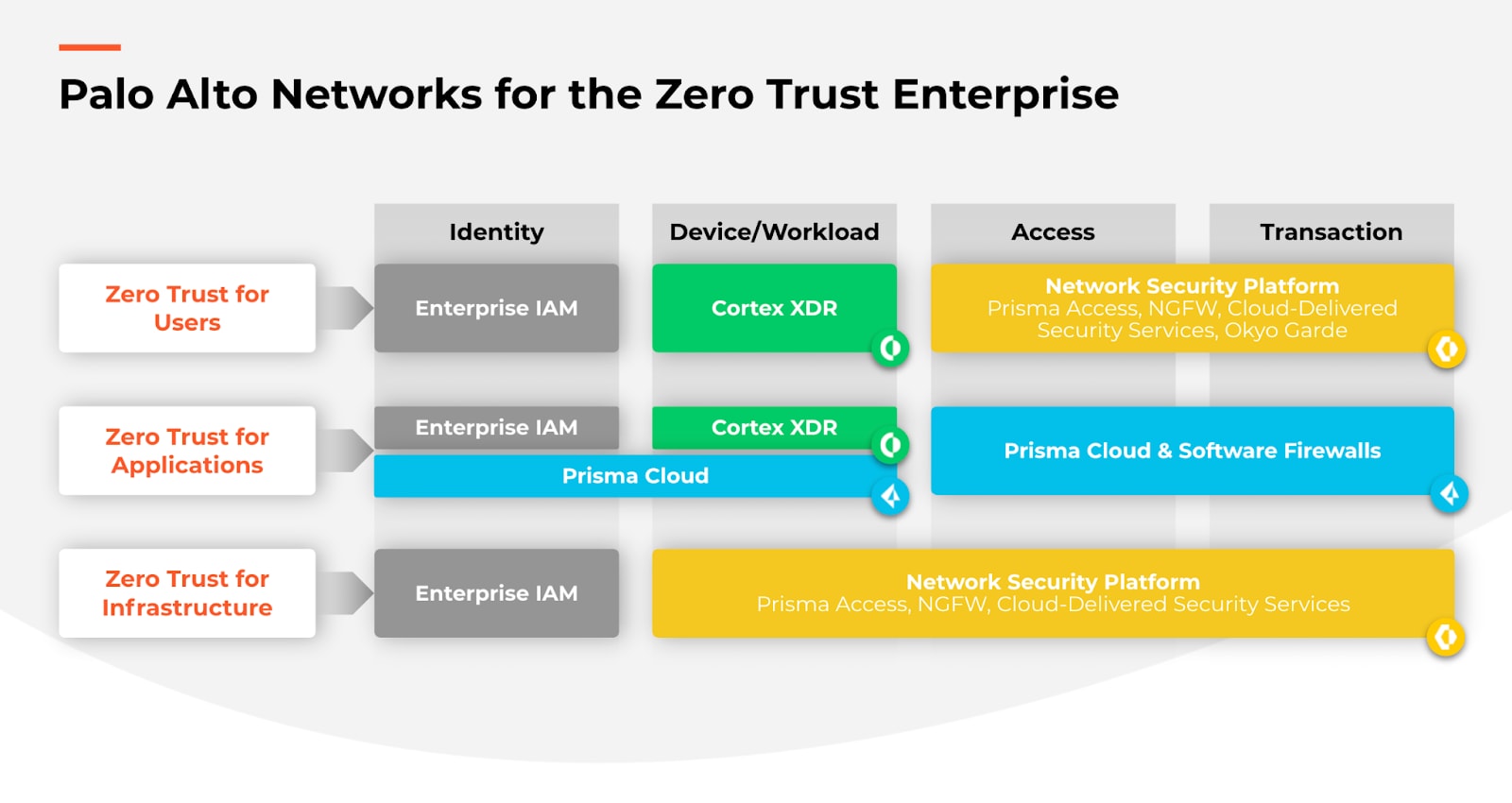
How Can I Make Zero Trust an Integral Part of My Cloud Transformation?
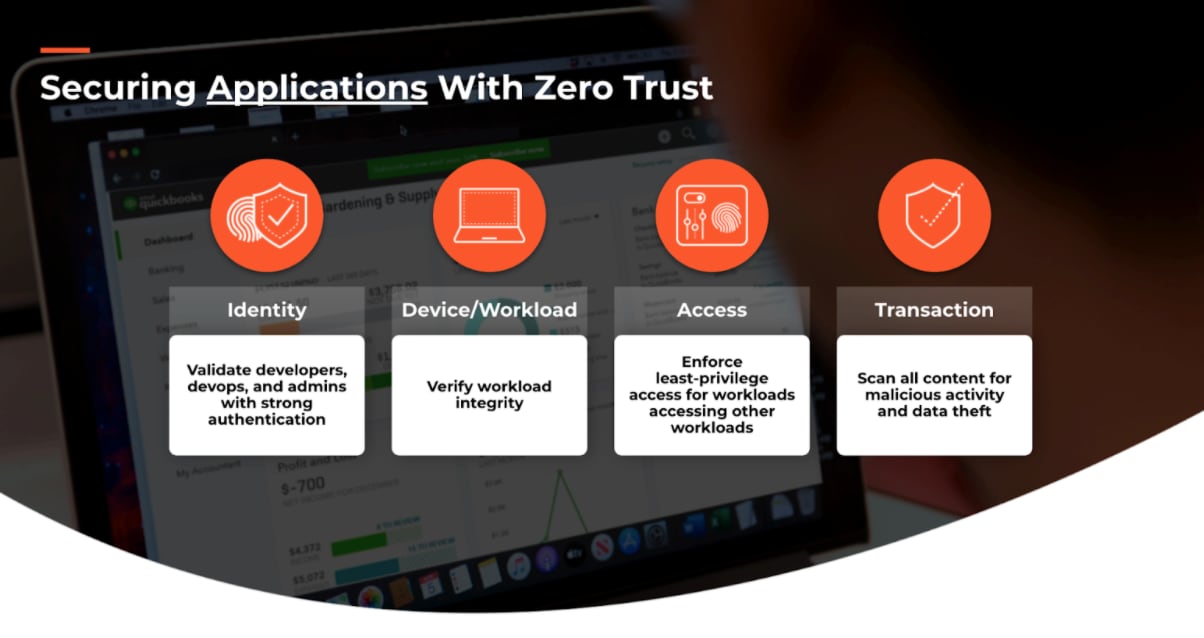
To secure cloud environments and applications, organizations must remove all implicit trust and enforce cybersecurity checks across the entire application development lifecycle. Security teams need to partner with DevOps and cloud infrastructure teams to implement Zero Trust principles:
Validate all cloud identities: Always validate the identity and entitlements granted to the developers, devops, and admins who seek access to cloud infrastructure. Ensure there are no excessive or outdated permissions.
As cloud environments are increasingly deployed using Infrastructure as Code (IaC) templates, security teams must engage developers and DevOps teams to integrate security and compliance checks into development and DevOps workflows. Provide actionable feedback and guardrails to prevent misconfigurations in IaC templates from ever turning into insecure infrastructure.
Protect the cloud workloads: Continuously secure all hosts, containers, and serverless functions running across any private or public cloud. It is imperative that the integrity of workloads is continuously monitored for any misconfigurations, vulnerabilities, or indicators of compromise.
Apply context-based network access: Verify all network access between microservices and enforce microsegmentation. As workloads access other workloads in the cloud, they must mutually verify workload identity and, if authorized, apply least-privilege connectivity to the application.
Secure all cloud transactions: Once network access is granted, inspect all content and proactively prevent any threats or malicious behavior to ensure the transaction is safe and secure. Security can further be extended to web applications and APIs across the application lifecycle for any cloud-native architecture to protect against modern threats.
How We Can Help
At Palo Alto Networks we’ve designed Prisma Cloud, our Cloud Native Application Platform (CNAPP), to reliably secure your cloud transformation with a Zero Trust architecture, while also positioning across the portfolio to further enable zero trust principles.
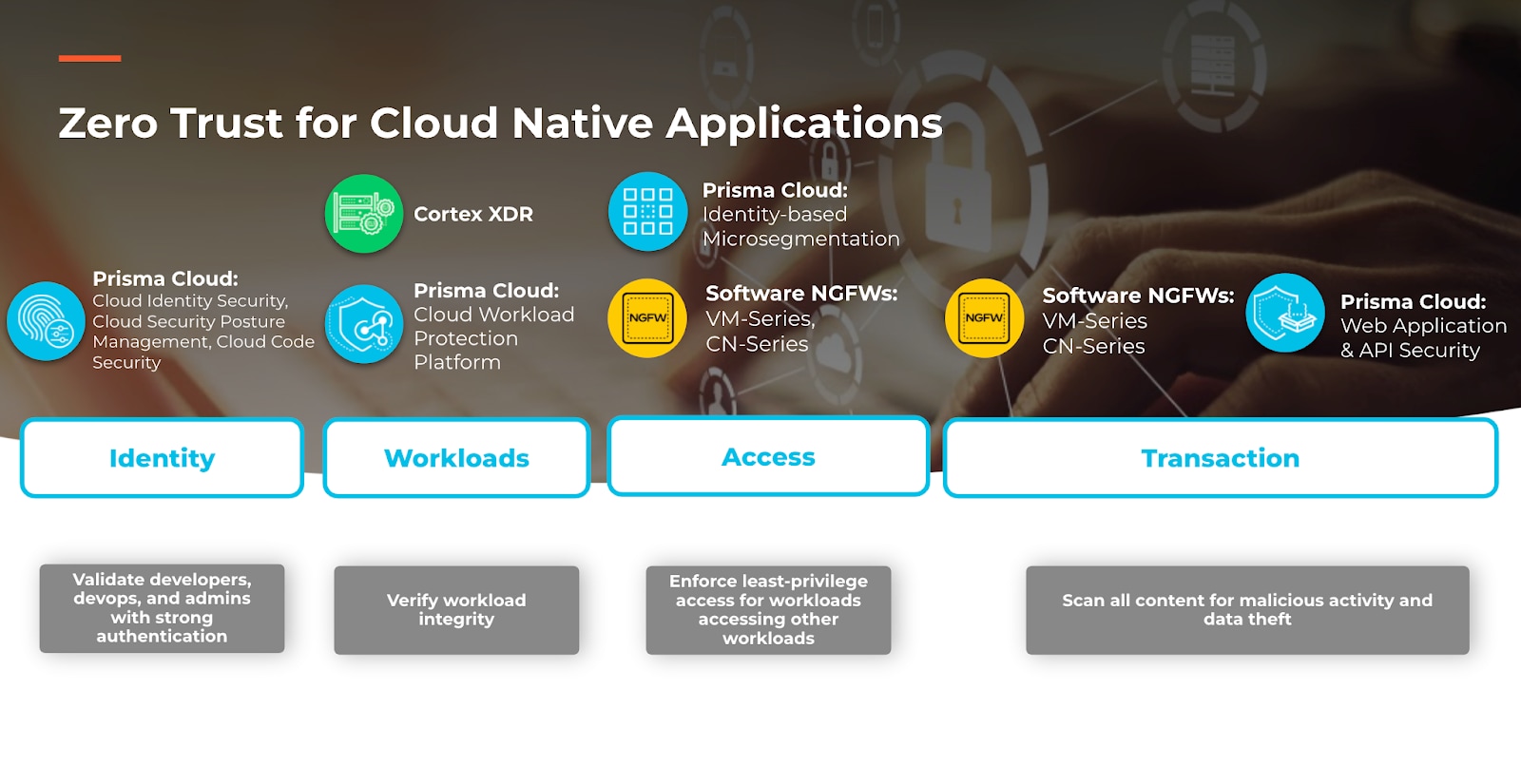
To secure identities, we’ve developed Cloud Identity Security to continuously monitor cloud permissions and entitlements across multiple cloud service providers and apply least-privileged access to cloud infrastructure. And our Cloud Code Security functionality helps security teams identify and fix vulnerabilities in cloud native application code and ensure only secure code is deployed in the cloud. This results in a full lifecycle approach to security that ultimately secures applications by design.
To secure workloads, Prisma Cloud offers Cloud Workload Protection which comprehensively secures workloads across private and public clouds by applying vulnerability management, compliance monitoring, and runtime protection. We’ve integrated these capabilities with CI/CD pipelines to enforce security checks across the entire application lifecycle. To further enable Zero Trust workload security, Cortex XDR offers threat prevention, detection, and response capabilities on workloads. The Cortex XDR agent proactively blocks cyberattacks such as malware and ransomware, as well as the exploits that lead to compromise. The agent gathers rich data to power detection and response across all assets, including cloud workloads.
To secure access, we’ve engineered Cloud Network Security to enforce least-privileged microsegmentation between workloads. As workloads communicate with other workloads, Prisma Cloud ensures all connectivity is verified for authenticity before granting network access to application data. In addition to microsegmentation, VM-Series and CN-Series software next-generation firewalls (NGFWs) bolster access controls with industry-leading App-ID, which classifies and restricts traffic based on application context.
To secure transactions, our software NGFWs and Prisma Cloud Web Application and API Security (WAAS) deliver complimentary protections. VM-Series and CN-Series inspect all content in network traffic to proactively block known threats, zero-day attacks, and data loss across private and public clouds. The WAAS functionally built into Prisma Cloud secures all your web applications and APIs on any cloud native architecture.
Whether you’re lifting and shifting applications or adopting a cloud-native approach in your cloud transformation, Palo Alto Networks is uniquely positioned to deliver on the promise of Zero Trust.
If you want to get your hands on Prisma Cloud to see how we can secure your clouds and enable Zero Trust principles, then request a 30-day trial.
Related Blogs
Subscribe to Cloud Native Security Blogs!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.