Secure Vulnerable Images Found in IaC Templates With Prisma Cloud
Image Referencer extends Prisma Cloud’s existing scanning capabilities to provide more complete visibility into all images that may exist in an application.
In modern, cloud-native teams, developers frequently stitch together a variety of code components to build their applications. While this improves efficiency and helps maintain release velocity, it also introduces code security risks because each component may contain hidden vulnerabilities. Open-source software is notorious for introducing vulnerabilities because it’s not secure by default, and other often-overlooked components, such as container images, can contain hidden vulnerabilities.
To ensure they’re identifying all vulnerabilities within their applications, teams need to employ security tooling that proactively surfaces vulnerabilities at any depth and with the context-aware prioritization that developers and security teams need to efficiently manage security issues. As part of this process, each code component, including container images, needs to be proactively scanned for issues. This is a critical part of any comprehensive security strategy, especially considering that public images might not have been scanned before.
But it’s only possible to scan images if you know those images exist in the first place. So how can you ensure that all your images pulled into deployments or test environments are being properly identified and secured?
Identify Vulnerable Images Pulled From IaC and CI/CD Files With Prisma Cloud
Failing to identify and remediate vulnerabilities in images early in the software development cycle introduces significant challenges down the line.
Let’s assume that you’re using infrastructure as code (IaC) and CI/CD pipelines to pull in images to run as application components or testing environments. In this scenario, an IaC file may pull a container to be deployed in a managed container orchestrator environment. Or, a CI/CD pipeline may pull multiple containers with different operating systems to test that the new code works properly in multiple distributions.
When your IaC and CI/CD files interact with containers in this way, it’s possible that your platform engineer never saw the vulnerabilities in a specific image because another team built that image. In this situation, your team needs the ability to identify all images pulled from IaC and CI/CD files so that you can fully understand all sources of vulnerabilities and have an informed discussion about acceptable risks within your applications.
To address this need and expand on its new Software Composition Analysis (SCA) capabilities, Prisma Cloud recently released Image Referencer, which is a new capability that can identify images sourced in IaC and CI/CD files. Once the platform identifies those images, it can scan them for vulnerabilities and then automatically surface findings in the platform, CLI outputs, and IDE integrations. Image Referencer extends Prisma Cloud’s existing scanning capabilities to provide more complete visibility into all images that may exist in an application.
Identifying and Scanning Hidden Images With Prisma Cloud
Base Image Scanning
Most containers rely on base images as the foundation for the rest of the image. If you start with an insecure image, it’s difficult to manually repair all issues. Prisma Cloud now identifies the vulnerabilities in base images throughout the development lifecycle, making it easier to proactively upgrade the image or remediate issues within an image.
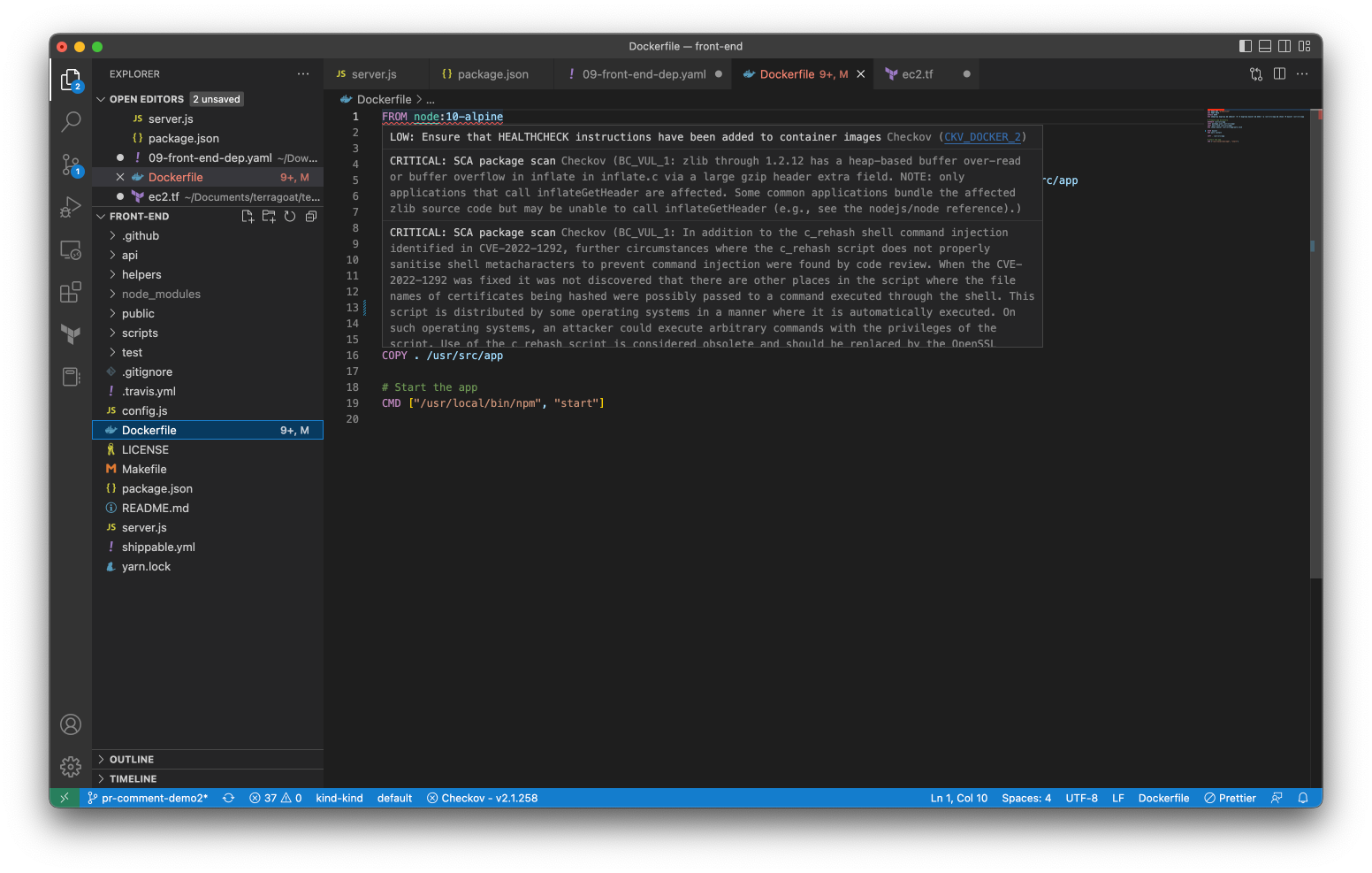
Images in IaC Templates
Kubernetes manifests are used to define the images that should be deployed in a cluster. Additionally, some containers as a service or managed orchestration environments managed by IaC frameworks like Terraform and CloudFormation pull in images. Prisma Cloud will proactively scan those images and surface them next to IaC misconfigurations, which will give you the added context you need to understand the combination of misconfigurations and vulnerabilities within a template.
Images in CI/CD Definitions
Many CI/CD pipelines, like GitHub Actions, can pull images to run unit or integration tests in separate environments. If those images have vulnerabilities, they can be exploited to instigate a supply chain attack. Identifying those otherwise hidden vulnerabilities is an important step to securing your supply chains.
Image Referencer in Prisma Cloud and Checkov
Now let’s walk through how Image Referencer works in practice.
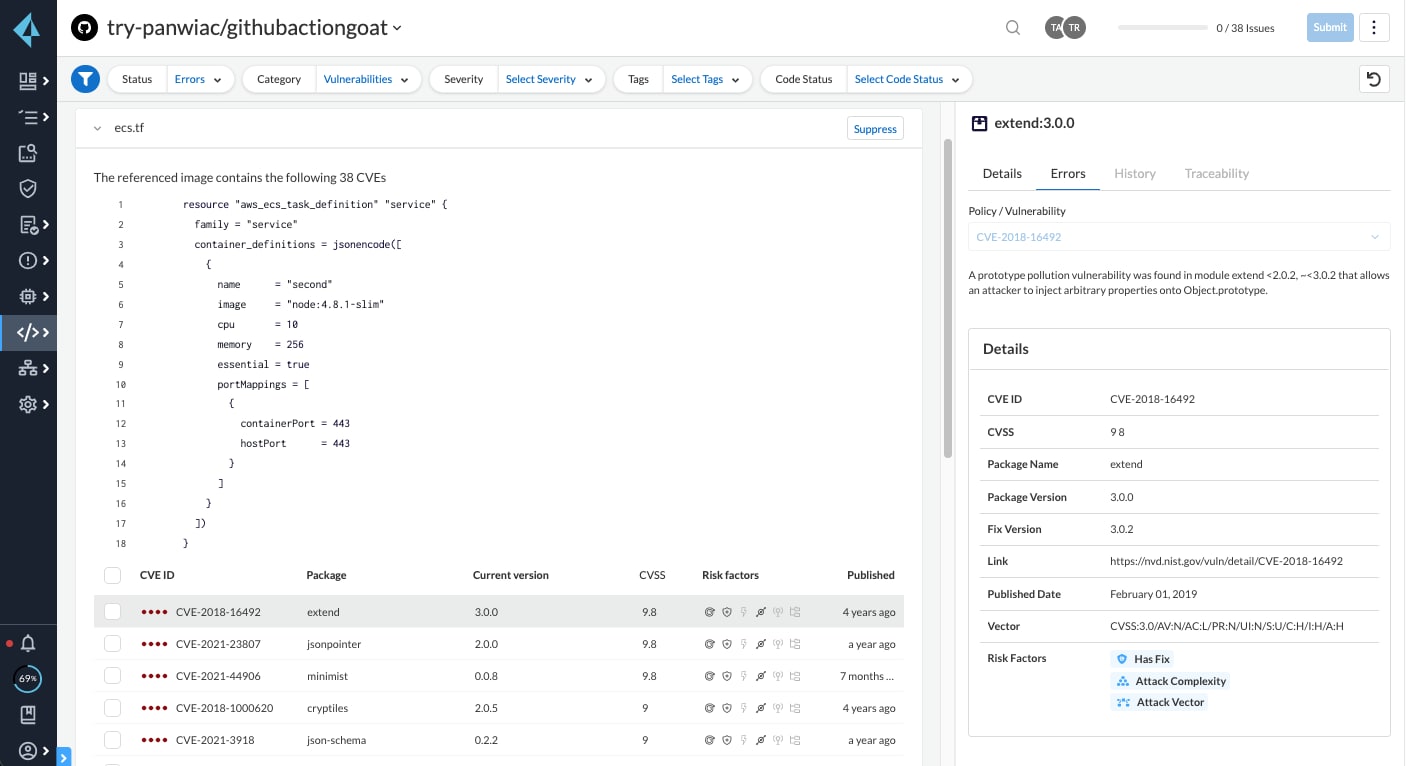
In Prisma Cloud’s Code Security module, navigate to the Projects screen. Image Referencer findings will show up as a violation block that lists all CVEs sorted by severity. Let’s say that we use Image Referencer, and the platform finds an ECS resource block in Terraform from an onboarded repository. The platform recognizes that the file pulled a container image, so the platform will surface all the CVEs in that file by severity level. The Projects screen would display the findings below:
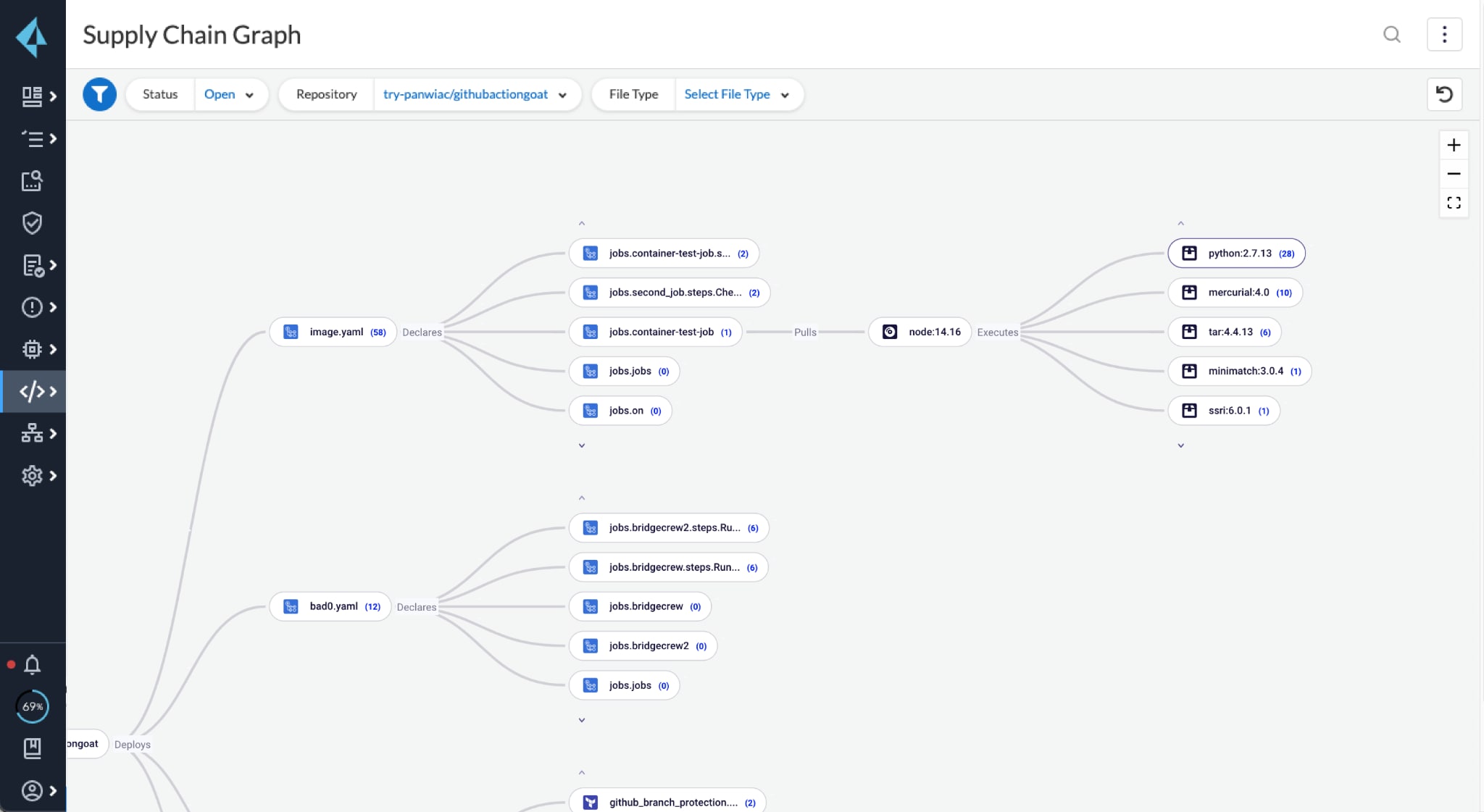
If we head over to the platform’s Supply Chain screen, we can see that images are attached to the resource that called them. Let’s say that a GitHub Action used the image node:14.16 to run steps in the CI/CD pipeline. Prisma Cloud automatically scans the image and identifies that it includes Python:2.7.13, which has twenty-eight vulnerabilities. The scanning results are displayed as follows:
And if we wanted to view surfaced issues from the IDE, we can see that image vulnerabilities are surfaced inline with IaC scanning findings for resource blocks.
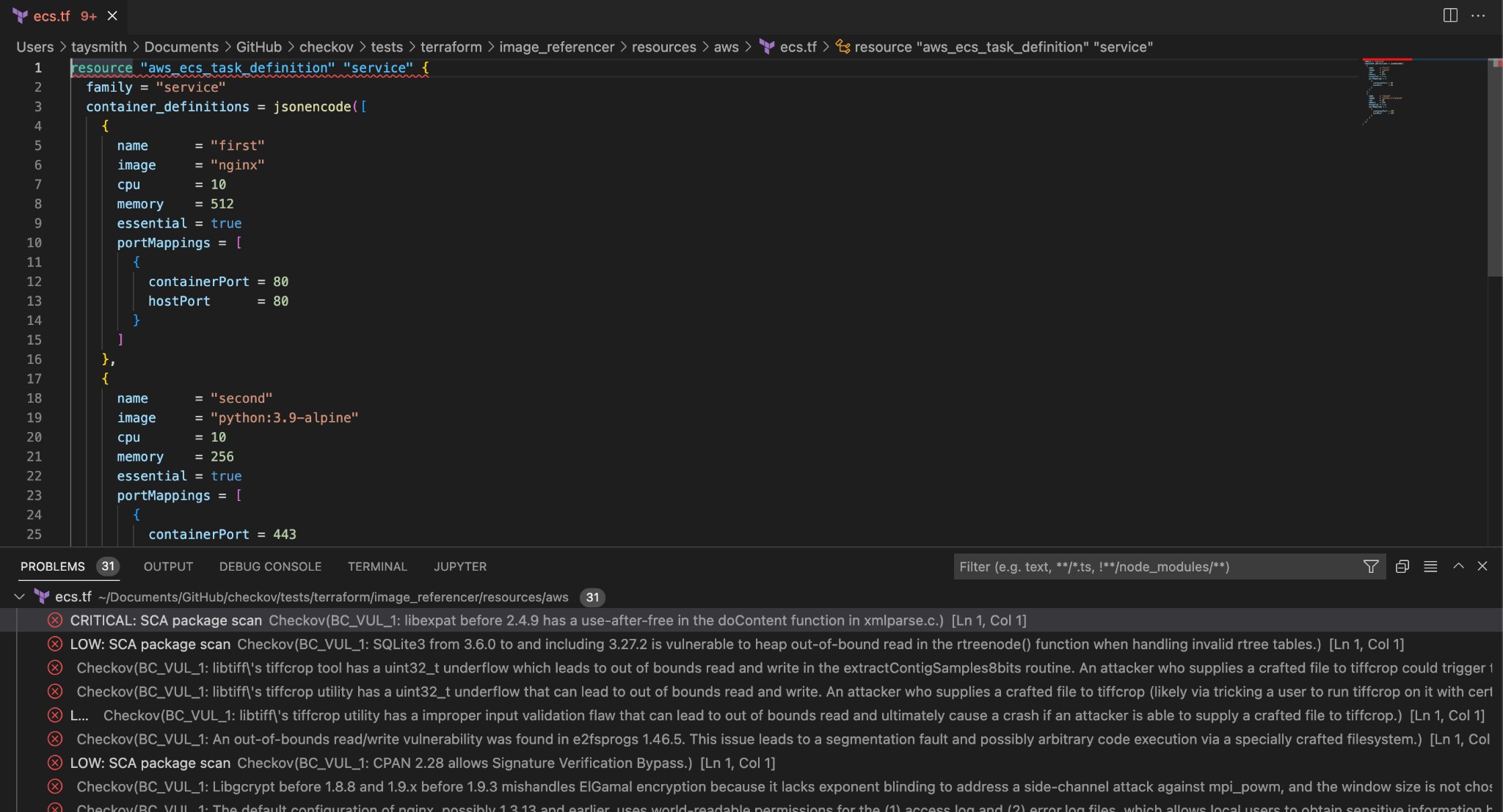
When using Checkov, the open-source IaC scanning tool, scanning results will be surfaced as long as we include a valid API key from Prisma Cloud.
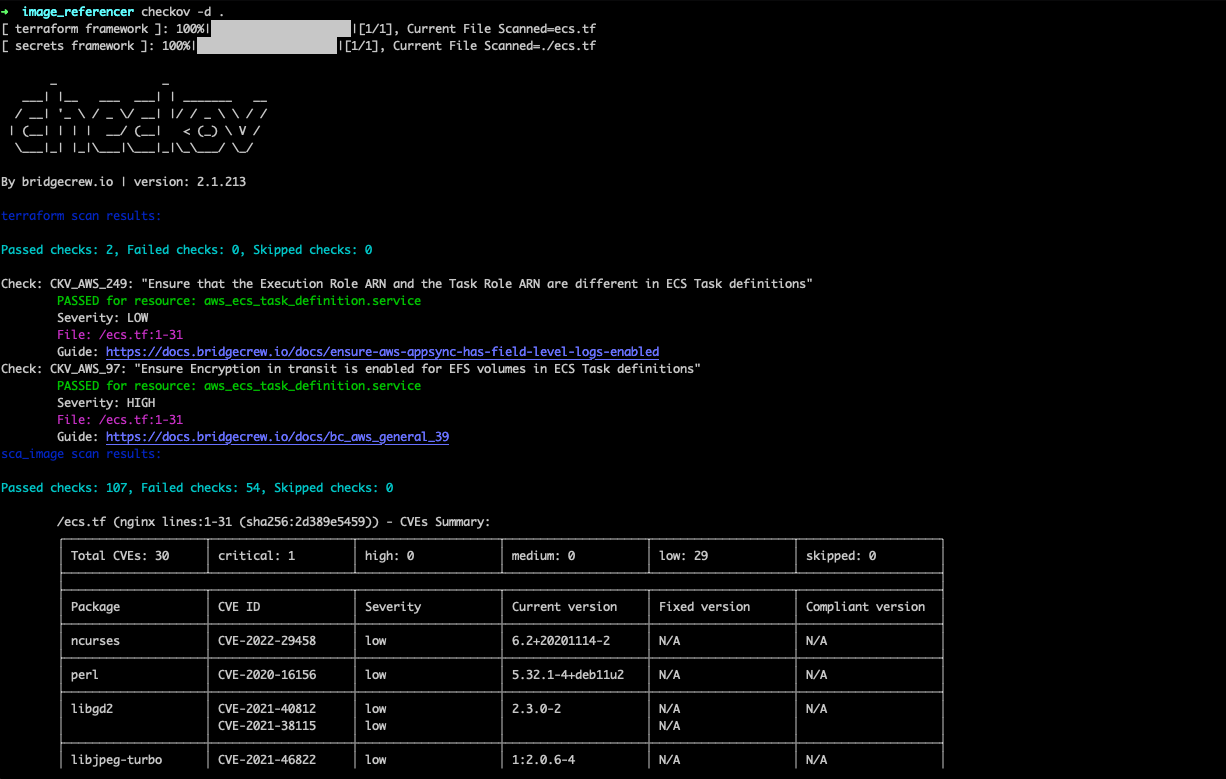
…
Prisma Cloud’s Image Referencer identifies images sourced in other files and gives you the contexts for different images so you can get complete visibility into all your images. This way, you can proactively scan your images for vulnerabilities and get a deeper understanding of all the sources of risk in your applications.
See Image Referencer for yourself by requesting a free trial of Prisma Cloud.
Related Blogs
Subscribe to Cloud Native Security Blogs!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.