Prevent Lateral Movement With Prisma Cloud
Lateral movement refers to a technique adopted by attackers to maneuver within a network or cloud infrastructure to obtain unauthorized access to sensitive data. Free from the detection of conventional network security measures, attackers can move surreptitiously from one virtual machine or container to another in search of critical resources.
This poses a significant threat, as cloud environments grow more intricate and challenging to safeguard against malicious activities.
Impact of Undetected Access
Lateral movement can result in serious damage. Once attackers gain access to an unauthorized resource, they can exploit lateral movement techniques to move deeper through the compromised environment, seeking high-value assets. Sensitive data may be exposed, valuable intellectual property could be stolen, and essential applications or services might be disrupted.
Common attack vectors exploited in lateral movement include compromised credentials and misconfigurations of resources, especially for the initial breach. But attackers who have found compromised identities to impersonate will leverage the permissions of the identity and attempt to escalate privileges. If successful, they will persist indefinitely — undetected — moving through multiple systems in the network until they accomplish everything they set out to do.
Identifying and adjusting over-permissive privileges to cloud resources is key to arresting lateral movement.
Preventing Lateral Movement
While preventing lateral movement isn’t easy, it can be stopped with proper preventive mechanisms in place. Identity and access management (IAM) governs access to the cloud environment, providing certain access for specific resources, and is pivotal to detecting and preventing lateral movement.
Prisma Cloud provides granular visibility into cloud resources, allowing organizations to identify over-permissive privileges and take actions to correct them.
As illustrated in image below, Prisma Cloud helps detect resources that IAM policies allow access from one account to another. This knowledge helps prevent lateral movement attackers from acquiring multiple environments.
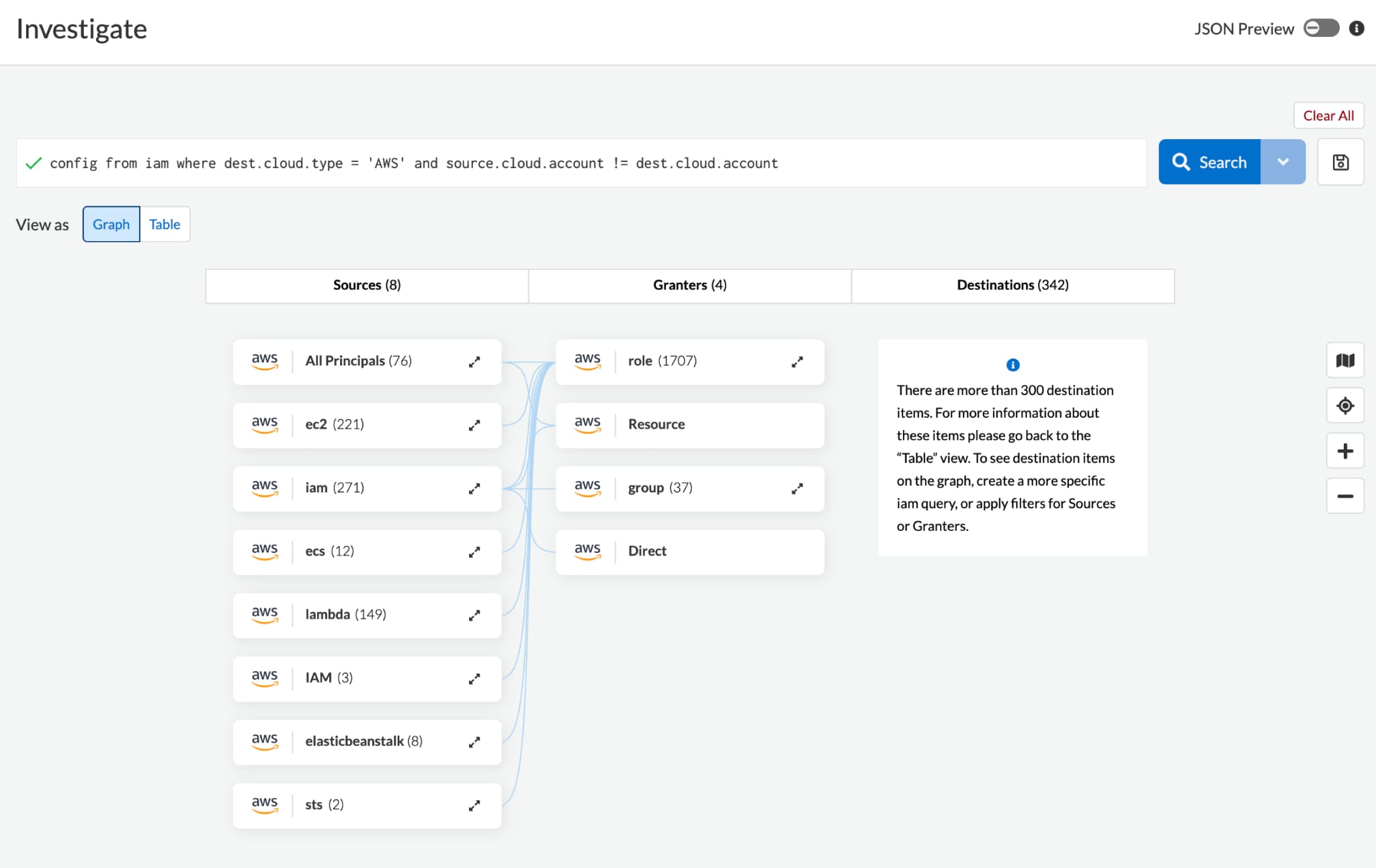
Because IAM policies can be exploited by malicious actors to gain unauthorized access to other cloud accounts, it’s important to be aware of these multi-account privileges to stop attackers from exfiltrating confidential data and causing further harm.
Incorporating a policy for Azure, as well, Prisma Cloud identifies excessive permissions that, when compromised, can allow an attacker to move between subscriptions.
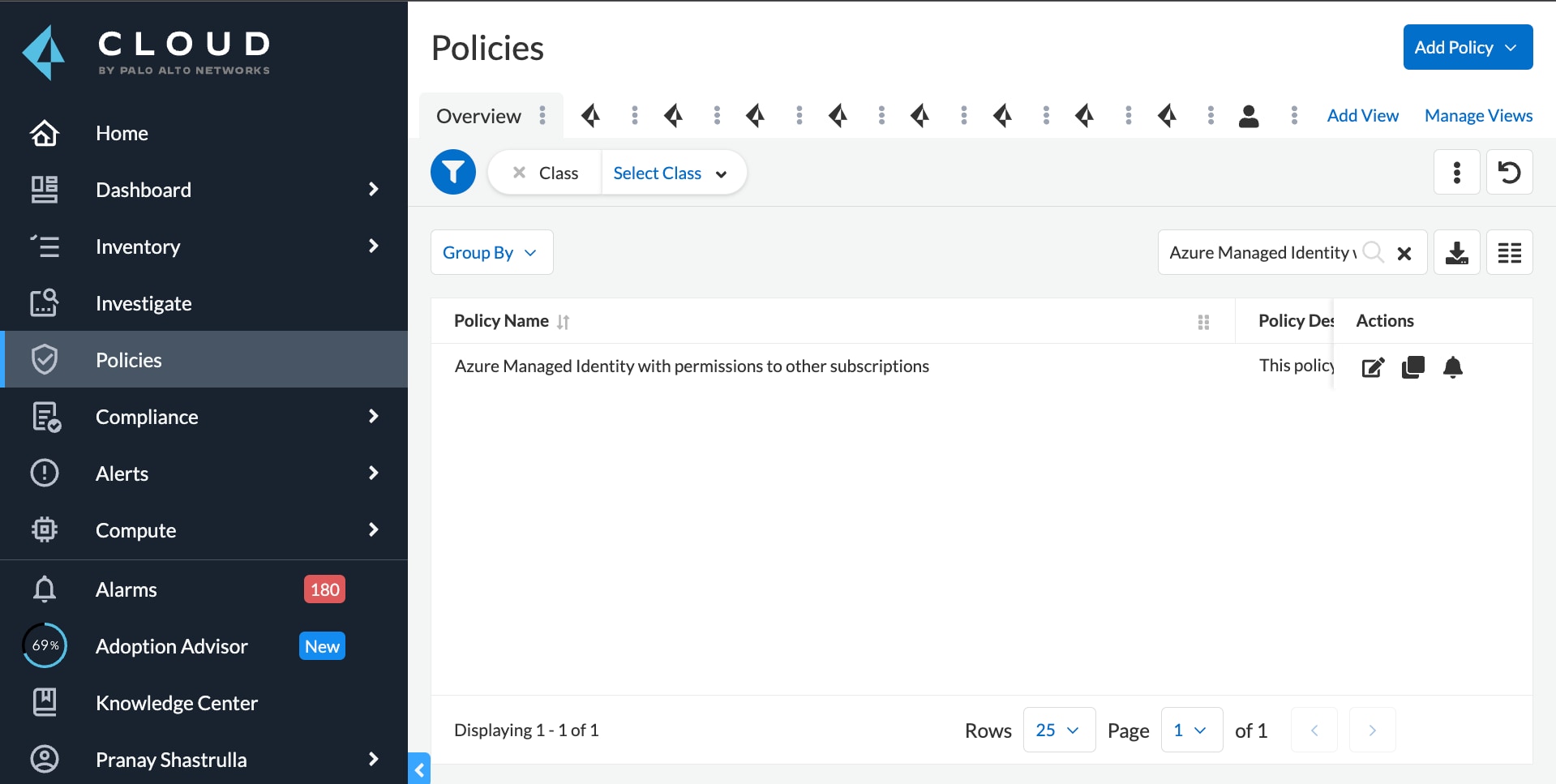
As organizations continue to move workloads to the cloud, lateral movement attacks will remain a significant threat. Gaining in-depth understanding of attack vectors and limiting the radius of the attack by implementing network isolation, remediating vulnerabilities, and controlling access to cloud resources will aid in preventing lateral movement in your cloud environment.
Prisma Cloud delivers a robust solution, helping organizations to prevent lateral movement by enforcing least privilege access policies and providing continuous monitoring and threat detection capabilities.
Learn More
Interested in learning more about Prisma Cloud? Take it for a free 30-day test drive and experience the advantages for yourself.
Related Blogs
Subscribe to Cloud Native Security Blogs!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.