Open Source Vulnerability Management for Cloud Security
Executive Summary
These days, as there are many different strategies and architectures for building and running applications, and there are many different components involved, the mission of securing them all has become increasingly difficult. The open-source world has evolved in the last few years, and these days most enterprises rely on open-source libraries in their services. While the majority of open-source code is widely used and maintained, it is still vulnerable to security issues, making open source vulnerability management an essential part of any cloud security strategy.
Securing your software from vulnerable open-source components is not easy. One of the difficulties is managing and controlling your dependencies; each imported package contains both dependencies and sub-dependencies, so they are not all visible at first glance. There is also no standardization for open-source security integrity.
Prisma Cloud creates visibility and provides information about vulnerabilities in your used open-source projects and their installed dependencies, with an always up-to-date threat feed that is enriched with pre-filled CVEs and PRISMA-IDs. With this capability, Prisma Cloud customers are protected from new vulnerabilities faster than any other tool.
Vulnerability Management
Using a tool for open source vulnerability management is necessary for protecting and securing your application platforms. Detecting, processing, and evaluating security vulnerabilities in a system is mandatory for achieving a secured environment.
Runtime protection is crucial for identifying components that have already been compromised. Knowing and understanding your attack surface, and mitigating security holes, can prevent attacks before they occur. This is especially important when using open-source projects in your applications.
Prisma Cloud provides an up-to-date threat feed on both OS distribution packages and open-source packages. This helps you detect the packages and products in your application that are vulnerable to security vulnerabilities.
The main strength of Prisma Cloud is that in addition to the information collected from official vulnerability feeds, our dedicated research team enriches Prisma Cloud feeds with vulnerability data they curate. We detect vulnerabilities that were quietly patched, as well as new vulnerabilities that were only recently disclosed.
Open Source and its Security Challenges
Open source tools are widely known and used by organizations; they are convenient and easy to use, maintained, visible, and save time and money. But while they are widely visible and maintained, it does not simply imply they are well secured. Once there is a security vulnerability in one of the imported packages in your project, your project may be at risk as it can be exposed.
Security is not always the top priority for open-source developers, as their goal is to use their limited resources to create the best technology possible. In fact, many projects do not use a security scanner to scan their code for possible vulnerabilities and security weaknesses. And even if it is a concern for them, when finding a vulnerability, many project maintainers don't want to go through the CVE process to file a CVE or don’t even know how to do so. In some cases, the maintainers might fix a bug without publishing it as a security issue (they might not even realize they fixed a security issue), so the users of the package don’t know they need to update.
There is also no default and standard way of documenting security vulnerabilities in the open-source world. The National Vulnerability Database (NVD) is the main official source for CVEs - but there is no standardization for the CPE (Common Platform Enumeration) configurations when it comes to open-source packages. CPE is a structured naming scheme that specifies the affected packages and versions for each CVE. Let’s have a look at the python package named rsa for example - in CVE-2016-1494 the CPE configuration is python:rsa (which is deprecated), while in CVE-2020-25658 the CPE is python-rsa_project:python-rsa. As you can see, there are 2 configurations for the same package, and the package name can’t be simply inferred from it.
GitHub tried to create a solution for this problem and provides a platform for the projects’ maintainers to publish security advisories - after collaborating on a fix for the security vulnerability.
This feature is quite new, thus not fully filled and still lacks information with old CVEs and security vulnerabilities, and currently contains about 4,000 vulnerabilities. Furthermore, it puts the responsibility on the maintainers to publish their advisories through Github - however, there is no assurance that open source maintainers will do that.
Another thing that makes the security task difficult is dependencies. Each project has dependencies, and they also depend on other projects, and so on. You cannot fully know and understand the security state of your project when you are familiar with only part of the picture - as the packages you use can use older and vulnerable packages.
Vulnerability Feeds
One of the main challenges in open source vulnerability management remains finding a reliable source for security vulnerability data. NVD is a well-founded and trustworthy source for vulnerability data, however, in most cases it cannot be used on its own. Linux distributions usually maintain software packages on their own, make their own security evaluation for every product they supply, and apply security patches to their own releases. By relying only on NVD, we could miss the correct version range for a particular vulnerability the distribution fixed, thus alerting on vulnerabilities not affected (false positives). We could also miss specific vulnerability data released by the distribution itself (false negatives). In addition, some software vendors release vulnerability advisories in their own dedicated web pages or feeds, sometimes in parallel to issuing CVEs, or without issuing CVEs at all.
One of the main strengths of Prisma Cloud is its well established vulnerability data feed. Our feeds combine multiple official sources, from NVD, Linux distributions, as well as from a variety of vendor security advisories and feeds. Prisma Cloud has a state-of-the-art mechanism to match software releases and alert on all the relevant vulnerabilities in each package or binary based on our vulnerability database.
Prisma Cloud provides visibility for security holes in your environment, by:
- Detecting the open-source components in the application, including their installed dependencies
- Identifying the vulnerable packages
- Offering mitigation steps when there is an available fix
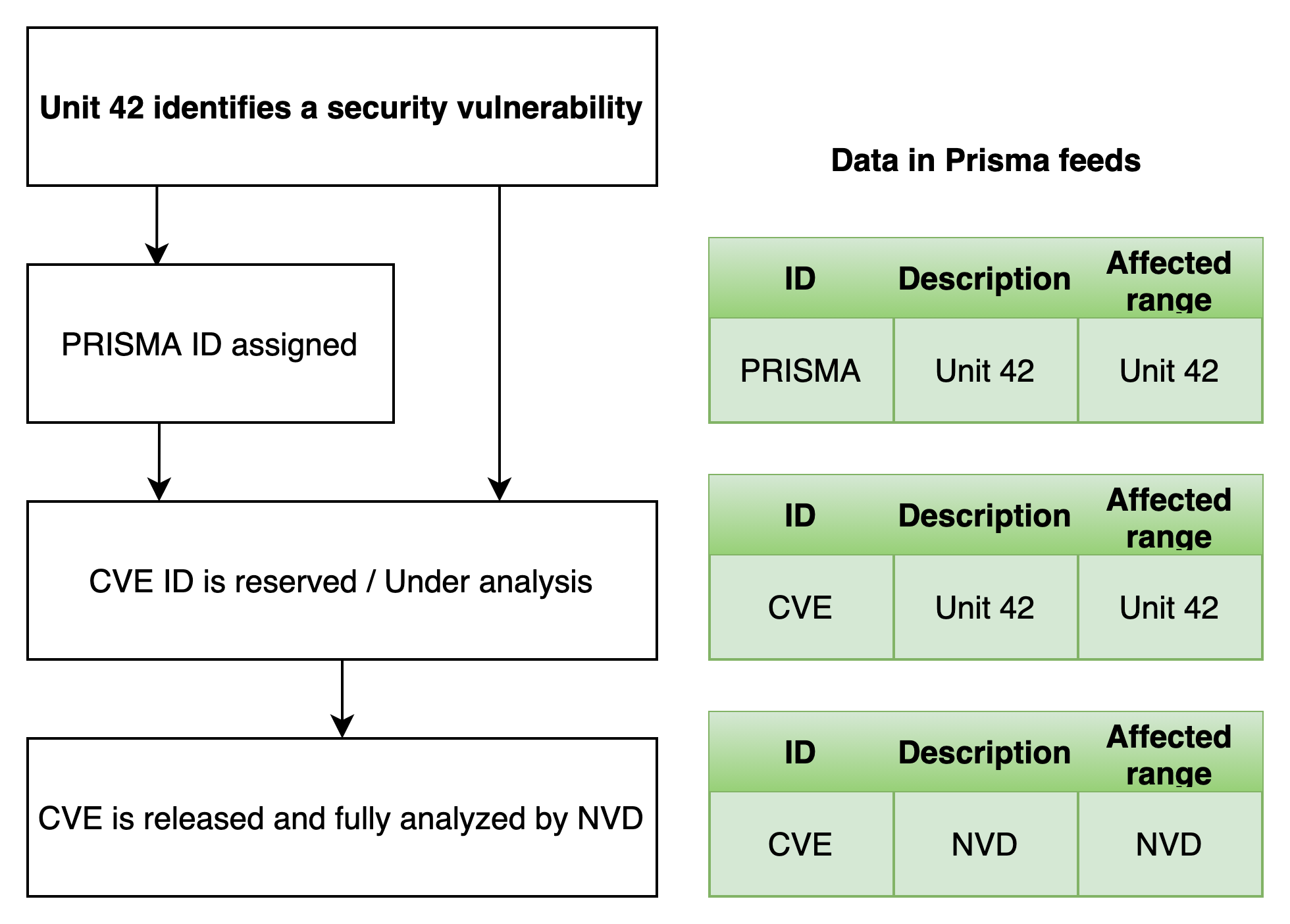
PRISMA IDs and Pre-filled CVEs
In addition to official feeds, our Unit 42 researchers also monitor cloud and open-source projects to identify security issues through a variety of automated and manual means. We can detect new vulnerabilities that were only recently disclosed, and even vulnerabilities that were quietly patched.
Our researchers manually review the details of each vulnerability, identify the correct range of affected releases and deliver the data to our feeds. As a result, Prisma Cloud customers are provided with information about CVEs that are not yet to be reported in NVD or MITRE. The same applies to vulnerabilities that are still under analysis by official feed maintainers, such as NVD or distribution vulnerability feeds.
As mentioned above, many vulnerabilities are publicly discussed or patched without a CVE ever being assigned to them. For creating the best visibility and protection for our customers, our researchers identify those kinds of vulnerabilities and assign a PRISMA ID for them.
PRISMA IDs are security vulnerabilities that are found before being assigned with a CVE ID. These could relate to a security issue that is publicly discussed, a CVE that is still in process, a bug that has been quietly patched that actually discloses a security vulnerability—anything that you need to be concerned about. As of now, PRISMA IDs are only visible for Prisma Cloud customers. Prisma Cloud encourages open-source projects to assign and populate CVEs related to vulnerabilities in their code. The purpose of PRISMA IDs is not to replace CVEs, but to fill in the gap between a public disclosure of a vulnerability to its addition to NVD, which takes days or sometimes several weeks.
Let’s have a look at some examples:
- CVE-2020-13924 for the
Apache Ambaripackage in java. While it was published in NVD only on 03/17/2021, our researchers identified it more than a month before on 02/08/2021. Affected customers of Prisma Cloud were alerted of this vulnerability before it was published. - PRISMA-2021-0033 was assigned for a vulnerability in the nodejs
handlebarspackage on 02/22/2021. CVE-2021-23369 was assigned to this vulnerability only on 04/12/2021, almost two months after.
Start Securing Open Source Tools
Since open-source tools are widely used, open source vulnerability management has become more important than ever.
Prisma Cloud creates visibility and provides information about vulnerabilities in your imported open-source projects and their installed dependencies. Thanks to our Unit 42 researchers’ work, our customers can map their attack surface and protect themselves from new vulnerabilities much faster than with any other tool. To learn more about what Prisma Cloud can do for your team, request a free trial today.
Related Blogs
Subscribe to Cloud Native Security Blogs!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.