What Does the Latest Linux Kernel Vulnerability Mean for Kubernetes Users and How Prisma Cloud Protects Against it?
Executive Summary
On 01/18/2022, an Integer Underflow vulnerability was discovered in the Linux Kernel. The vulnerability, assigned CVE-2022-0185, lies in the legacy_parse_param linux kernel function. If used correctly, the vulnerability can be leveraged to an infinite kernel heap overflow, by bypassing some of the checks implemented in the Linux kernel.
The vulnerability can be triggered by any user with the CAP_SYS_ADMIN privileges. However, the privilege only needs to be granted to the current namespace, so most unprivileged users could achieve it by creating a new namespace with the capability granted, making the exploitation of this vulnerability possible with low privileges. Prisma Cloud can alert on the use of privileged containers in your environment.
Most Docker instances are not affected by this exploit as Docker’s seccomp profile blocks unshare, the command that is used to start a program in a new namespace, by default.
Kubernetes clusters are likely affected by the vulnerability as the seccomp filter is disabled in it by default. The simplest remedy is upgrading all clusters to use a fixed Linux kernel; more advanced mitigations are described further in this article. Prisma Cloud can detect vulnerable instances and alert on the use of a vulnerable kernel.
In addition, another local privilege escalation vulnerability was discovered on 01/25 in the Linux polkit toolkit. The vulnerability was named PwnKit by the researchers and was assigned CVE-2021-4034. polkit is an application-level toolkit for defining and handling the policy that allows unprivileged processes to speak to privileged processes. The vulnerability tracks back all the way to the initial commit of the pkexec command, over 12 years ago, so all versions of polkit are affected. This vulnerability is easy to exploit and there are already several public exploits available. Prisma Cloud alerts on use of a vulnerable kernel.
Background
We would like to focus on CVE-2022-0185 in this article as it had recently been a subject for concern in the cloud security community. CVE-2022-0185 was discovered by security researchers while fuzzing the Linux kernel. Only later, and after an exploit was already developed, the researchers decided to use this vulnerability to try to break out of Google’s Kubernetes CTF platform (also known as kCTF). This platform allows researchers to experiment with vulnerability exploitation for containers in general and Kubernetes in particular.
This vulnerability, while being severe as any other local privilege escalation (LPE) vulnerability, is not related to containers or Kubernetes any more than any other kernel vulnerability is.
Technical Summary
The problem lies in the kernel function legacy_parse_param which is used to add a new parameter to the legacy file system context structure.
What exactly this function does, or how to get it executed is outside the scope of this post. A full explanation of the exploitation chain can be found in the original paper by the researchers who discovered this vulnerability.
Suffice to say that any unprivileged user with a CAP_SYS_ADMIN capability in his current namespace can exploit this vulnerability.
The Offending Line
The vulnerability is caused by a single insufficient if condition:
if (len > PAGE_SIZE - 2 - size)
return invalf(fc, "VFS: Legacy: Cumulative options too large");
Starting from the left, len represents the length of the value the user wants to add to the kernel structure, PAGE_SIZE is 4096 and size is the current size of the structure. This structure can hold up to “PAGE_SIZE” (4096) bytes of data, so the condition tries to make sure the added parameter won’t overflow it.
The problem lies in the way the comparison is made. For a size big enough, the right side of the equation can actually underflow and result in a negative value, which means there isn’t enough space in the kernel buffer for the new parameter.
However, because both len and size are unsigned integers, a negative value is actually a very big positive value. This means that if PAGE_SIZE - 2 - size results in a negative value, the condition isn’t met and the function execution continues, regardless of len size.
Later in the function, the provided input from the user is copied to the kernel structure, which completes the heap overflow vulnerability.
The Fix
The vulnerability fix is the following:
- if (len > PAGE_SIZE - 2 - size)
+ if (size + len + 2 > PAGE_SIZE)
By simply removing the minus instruction, the condition won’t be possible to be passed as before, and because len is unsigned, it can’t be negative either.
Who’s Affected
This bug affects all kernel versions since 5.1 in systems where an unprivileged user can create new namespaces (default behavior), this includes most recent Kubernetes versions.
Mitigations
Host
The easiest way to fix the problem is to update your distribution. For example, Ubuntu fixed the issue in version 5.13.0-27.29 and 5.11.0-49.55. Other distributions might have different versions.
Another possibility is to remove the capability of unprivileged users to create namespaces. These commands may affect the host’s ability to run containers, depending on the configuration.
On Ubuntu and most other distributions:
sysctl -w kernel.unprivileged_userns_clone = 0
Om Red Hat:
echo "user.max_user_namespaces = 0" >> /etc/sysctl.d/userns.conf
sysctl -p /etc/sysctl.d/userns.conf
Kubernetes
A possible mitigation for Kubernetes is to use the securityContext field of the workload definition.
Moreover, there is a new feature, currently in alpha stage, that will allow the use of the CRI’s defaults (RuntimeDefault) as the default seccomp profile for all workloads. To use this feature, one needs to opt in the feature flag. More information about this can be found in the link above.
How does Prisma Cloud Protect Against this Issue?
Prisma Cloud Compute alerts or completely blocks its users from running privileged containers, which is required in most cloud environments for an attacker to take advantage of this vulnerability.
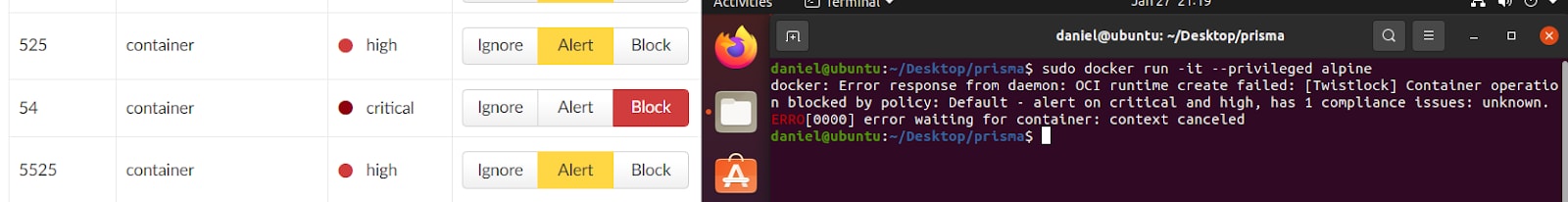
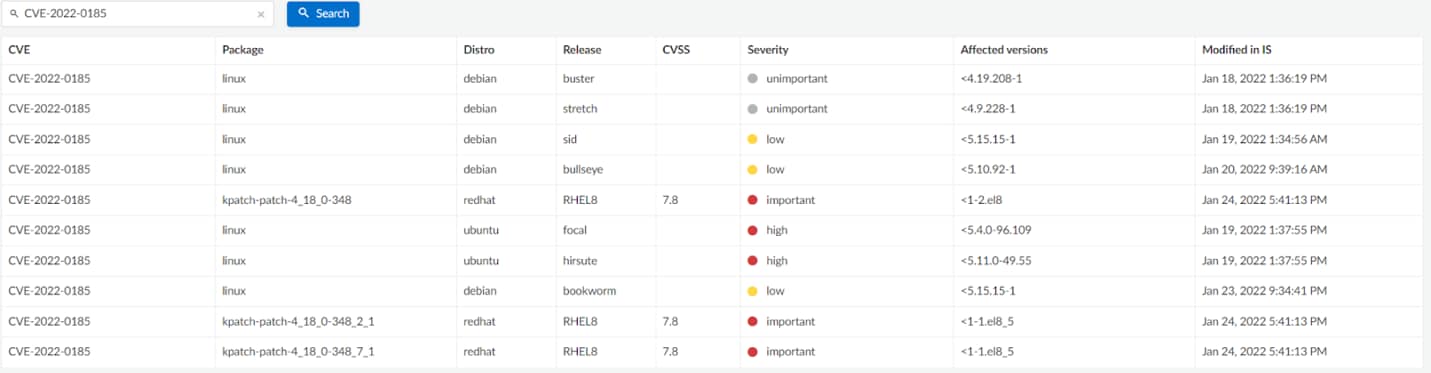
Moreover, Prisma Cloud Compute alerts users running vulnerable applications or kernel versions.
Get Started with Prisma Cloud
Existing customers can protect against privileged containers with a few clicks in their environment with Prisma Cloud Compute. New customers can see Prisma Cloud’s Compute capabilities in action, by requesting a free trial here.
Related Blogs
Subscribe to Cloud Native Security Blogs!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.