Implementing NSA/CISA Kubernetes Hardening Guidance
On August 3, 2021 the National Security Agency (NSA) and the Cybersecurity and Infrastructure Agency (CISA) released the Kubernetes Hardening Guidance Cybersecurity Technical Report. The document, which is intended for wide distribution, details common threats to Kubernetes environments and provides configuration guidance to minimize the risks they present.
We have independently reviewed the report and produced a whitepaper that explains at length how to implement the guidance using Palo Alto Networks technologies. We invite you to download the paper, Implementing NSA/CISA Kubernetes Hardening Guidance with Prisma Cloud, to familiarize yourself with the best practices outlined in the report and to understand how Prisma Cloud, industry’s only comprehensive Cloud Native Security Platform, effectively supports a defense-in-depth approach.
Why NSA and CISA Created Guidance for Kubernetes
Kubernetes is a portable, extensible platform for managing containerized workloads and services. It has seen a meteoric rise since it was first released in 2015, and today Kubernetes deployments, called clusters, are running in almost every computational environment you can imagine. From managed Kubernetes services offered by public cloud service providers to isolated and classified environments, even within datacenters and on bare metal, Kubernetes powers some of the internet’s most widely used applications. This popularity is driven, in large part, by its unsurpassed ability to manage computational resources rapidly and automatically (i.e., scale up or down based on demand).
But, because it is so commonly used, and there are so many moving parts, Kubernetes deployments have become a large target for cybercriminals. As federal organizations continue to adopt cloud native development methodologies, it is important that they have a standardized set of recommendations for managing these security challenges.
The NSA/CISA Kubernetes Hardening Guidance, then, describes security challenges that administrators will likely face setting up and securing a Kubernetes cluster, and lists strategies for hardening development pipelines. While it is primarily intended to guide system administrators and developers of National Security Systems, the recommendations are applicable to any Kubernetes environment.
How Prisma Cloud Aligns with NSA/CISA Guidance on Kubernetes
Palo Alto Networks developed Prisma Cloud, a cloud native security platform, to consolidate what had previously been disparate functionality for securing cloud native applications and development pipelines.
Among other functions, it combines tools for cloud visibility and governance with specialized protections for containerized application development, including Kubernetes. The platform can be delivered via SaaS, or, more importantly for federal organizations, it can be self-hosted and thus deployed in isolated or air-gapped environments. Prisma Cloud is purpose built for cloud native security and has been structured to support the best practices outlined in the NSA/CISA guidance. It is also a FedRAMP authorized software-as-a-service (categorized for moderate impact).
The following are a few examples in which existing Prisma Cloud capabilities align with the NSA/CISA guidance:
Kubernetes Pod Security
Cloud Workload Protection delivers holistic protection across hosts, containers, and serverless deployments in any cloud, throughout the application lifecycle—again, including isolated environments. The platform is API-enabled and capable of protecting cloud workloads regardless of underlying compute technology or operating environment, including Kubernetes.
For example, the NSA/CISA guidance encourages developers to build containers to execute as a non-root user. Within Prisma Cloud, you can simply turn on pre-built security policies to alert on and/or block the instantiation of containers attempting to run as root.
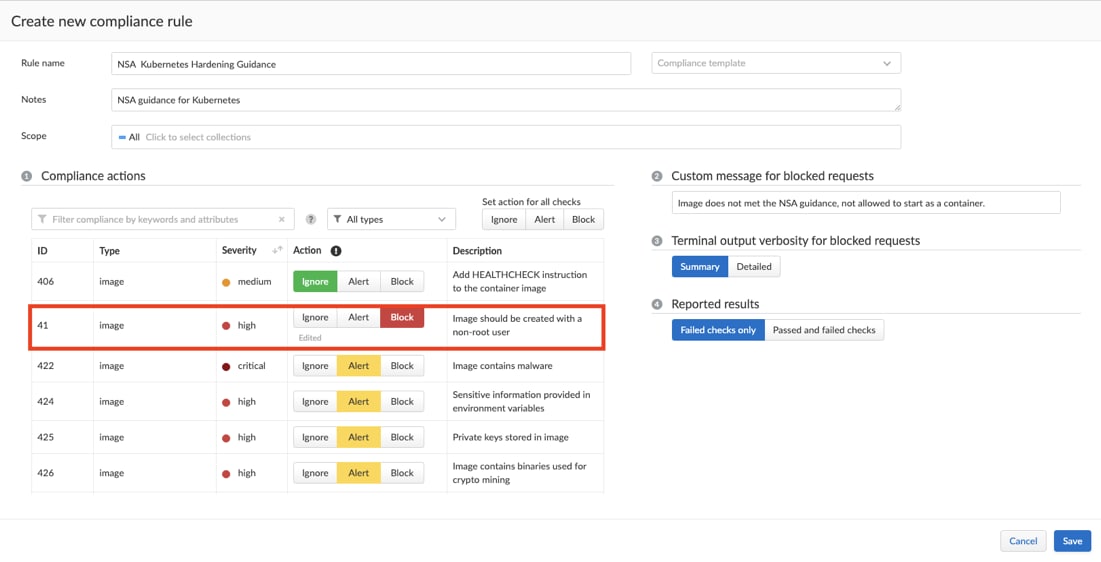
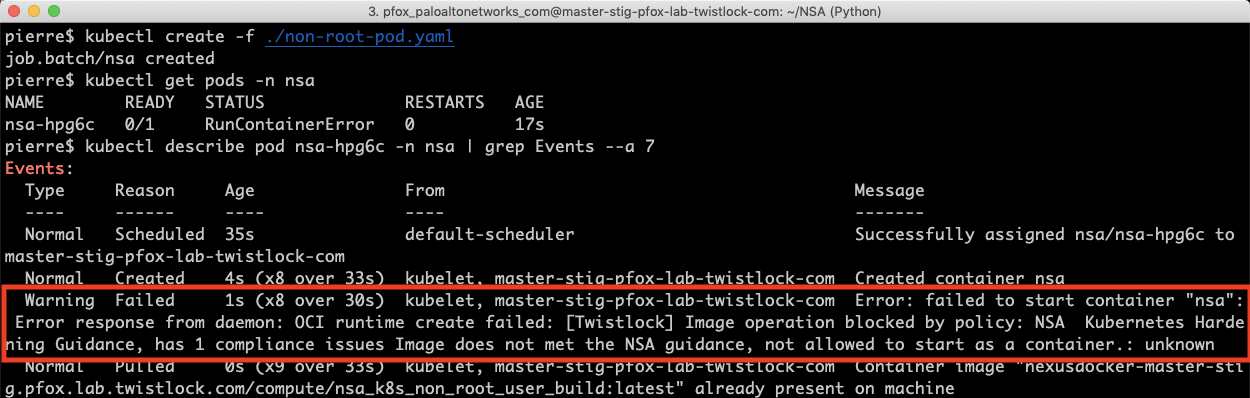
Protecting Sensitive Cloud Infrastructure
A significant number of Kubernetes clusters run on public cloud service provider (CSP) environments (e.g., Amazon Web Services, Google Cloud, Microsoft Azure). A complete defense-in-depth approach to securing Kubernetes requires that you first secure your implementation of a given CSP’s services. The cloud security posture management (CSPM) functionality within Prisma Cloud provides the necessary visibility and control over the security posture of every cloud resource, regardless of the CSP.
Network Separation and Hardening
As mentioned, organizations benefit most from a comprehensive approach to securing Kubernetes clusters, including at the network-level. Depending on your particular architecture, the Palo Alto Networks VM-Series and CN-Series Next Generation Firewalls are both excellent solutions for monitoring and protecting all communications traveling in and out of the cluster.
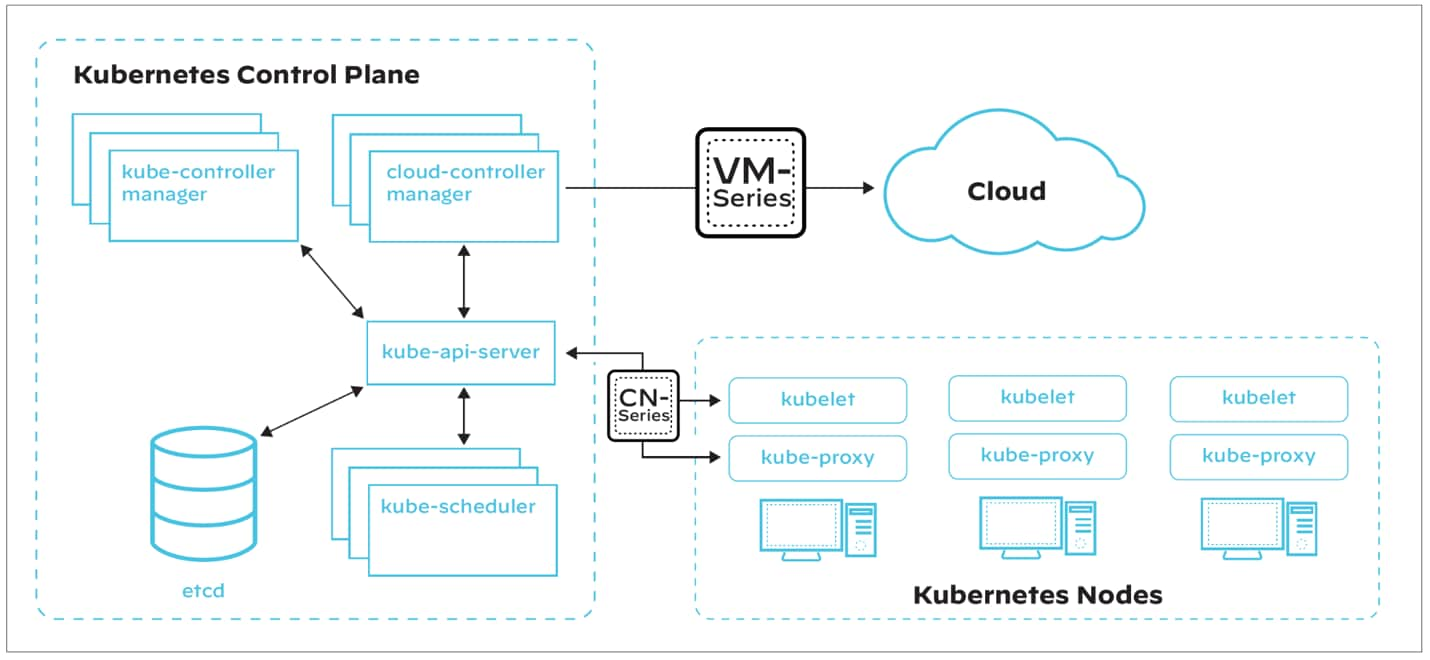
Industry Leadership
Our team has been deeply involved in container security for many years. Palo Alto Networks is a member of the Cloud Native Computing Foundation’s Governing Board, and we were a major contributing author to the National Institute for Standards and Technology Special Publication 800-190, Application Container Security Guide.
In addition, Palo Alto Networks Unit 42 cloud threat team actively researches emerging threats to ensure Prisma Cloud offers the absolute latest protections. For example, the team recently discovered Hildegard, a malware that attempts to discover and collect Kubernetes service account tokens as part of its Credentials Access process.
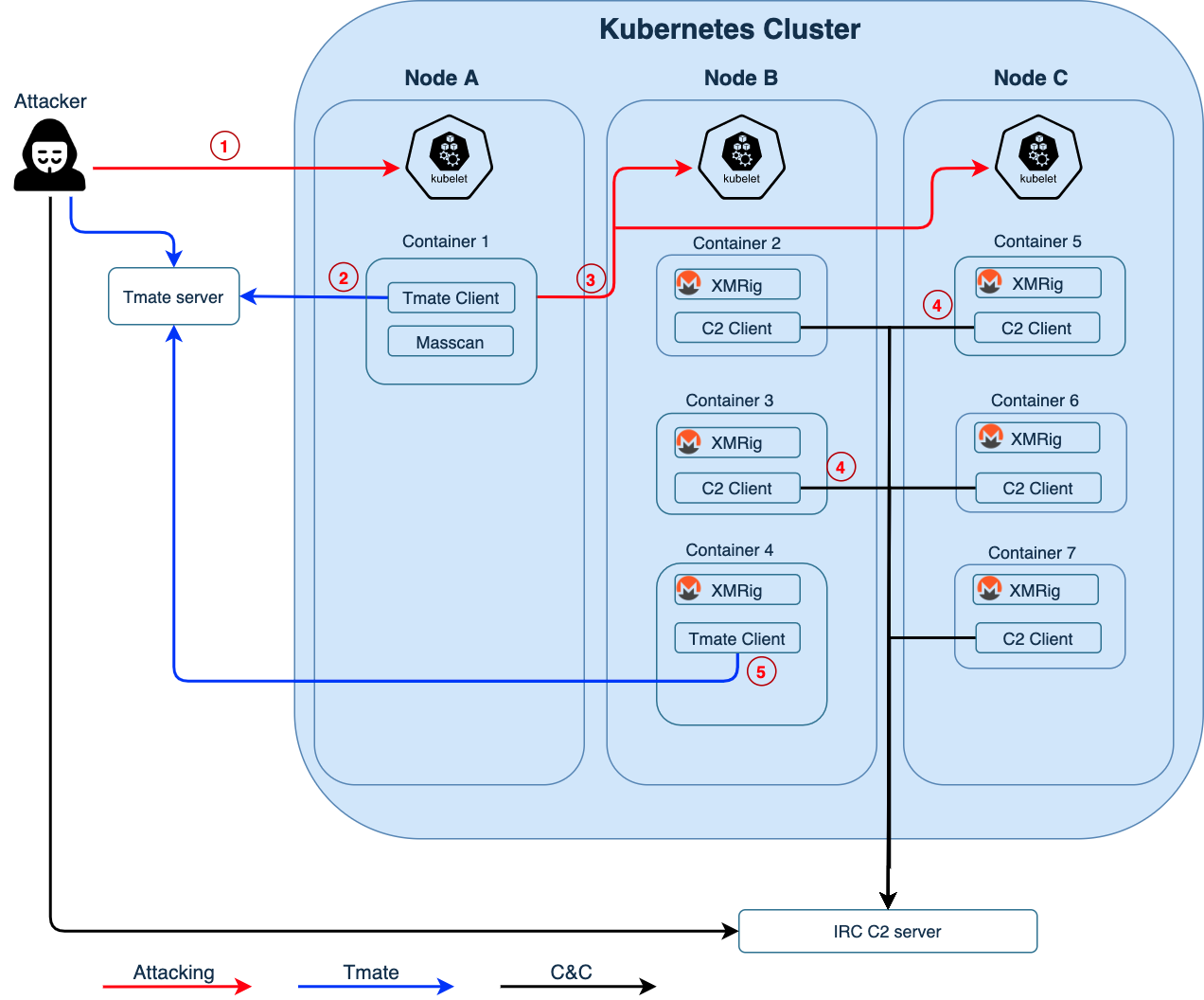
Illustrating attack paths used with the Hildegard malwareAs microservice-based attacks are uncovered, our guidance and platform capabilities are automatically updated to help secure your environments without additional effort.
Read All About It
The integrated Prisma Cloud platform enables security operations and DevOps teams to stay agile, collaborate effectively and accelerate cloud native application development and deployment across hybrid and multi-cloud architectures—even within isolated and air-gapped environments.
We invite you to download the Implementing NSA/CISA Kubernetes Hardening Guidance with Prisma Cloud whitepaper to learn more about Kubernetes security best practices and how Prisma Cloud is uniquely positioned to implement them.
Related Blogs
Subscribe to Cloud Native Security Blogs!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.