Automated Container Image Scanning with the Prisma Cloud GitHub Action
GitHub Actions offer an easy way for customers to automate software workflows as a CI/CD pipeline built into their repository platform. This simplifies adding tests, such as security tests, to inform developers of vulnerabilities and block code that doesn’t meet the organization’s policies from getting added to a repository or deployed to production. Prisma Cloud’s image scanning identifies vulnerabilities and compliance issues in container images during the development process. We’re excited to enable this functionality for your CI/CD pipeline using our container image scanning GitHub Action.
How We Built It
At the core of the action is twistcli, which speaks to the extensibility of the tool. When added to your workflow, the action gathers the necessary variables, scans your container image, then outputs the results in both the standard twistcli output format and SARIF.
To do this, we start by gathering your credentials, Console address, and image name specified in the with section of the scan action’s YAML. Using the GitHub Actions Toolkit Node.js modules, we then make sure that the correct version of twistcli is available in the workflow’s tool cache, pulling it from the Console and saving it if not. We scan the specified container image using the cached twistcli tool. This identifies vulnerabilities and compliance violations in the image.
The action outputs both a standard JSON output file directly from twistcli and generates a separate SARIF output file after reformatting the standard output. You can optionally upload the SARIF to GitHub using the upload-sarif action in your workflow if you want to leverage code scanning alerts in your repository.
Automated Image Scanning
Adding the Prisma Cloud Scan Action to your existing image build pipeline is simple. Add another step that uses our action and pass in the required inputs. For example, after building the image, add a step like this:
- name: Build image
run: docker build -t $IMAGE_NAME
- name: Scan image
uses: PaloAltoNetworks/prisma-cloud-scan@v1
with:
pcc_console_url: ${{ secrets.PCC_CONSOLE_URL }}
pcc_user: ${{ secrets.PCC_USER }}
pcc_pass: ${{ secrets.PCC_PASS }}
image_name: ${{ env.IMAGE_NAME }}
In-workflow Feedback and Guardrails
Using the Defend settings in the Prisma Cloud console, you can set the threshold for alerts and failures. This creates an automated way to both inform developers about the posture of their images as they integrate code into the repository and block code that is too vulnerable.
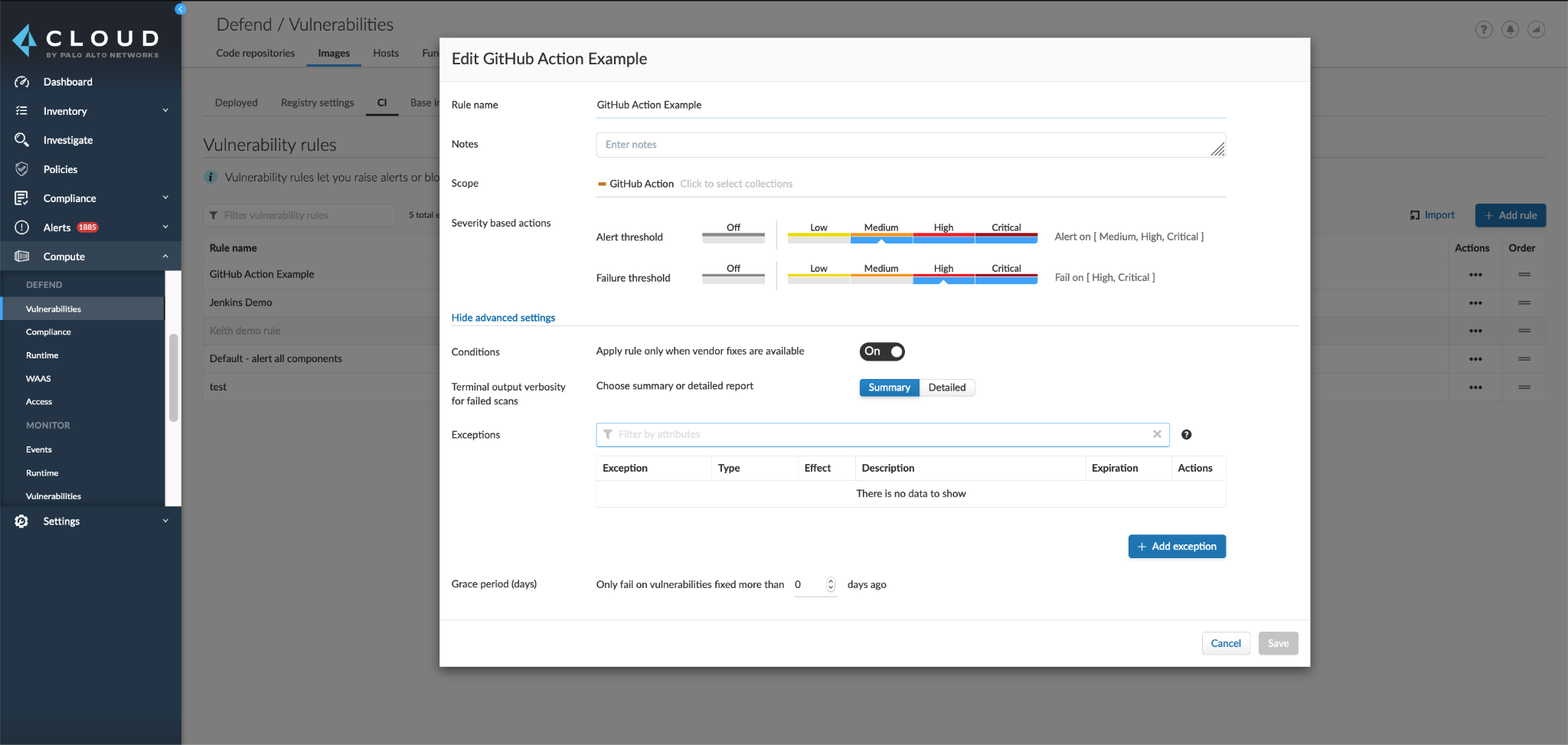
The next time you run your workflow, your image will be built and scanned for vulnerabilities and compliance violations. The results of the scan will show up for developers in the GitHub workflow log and all scans across environments will be aggregated in the Prisma Cloud Console.
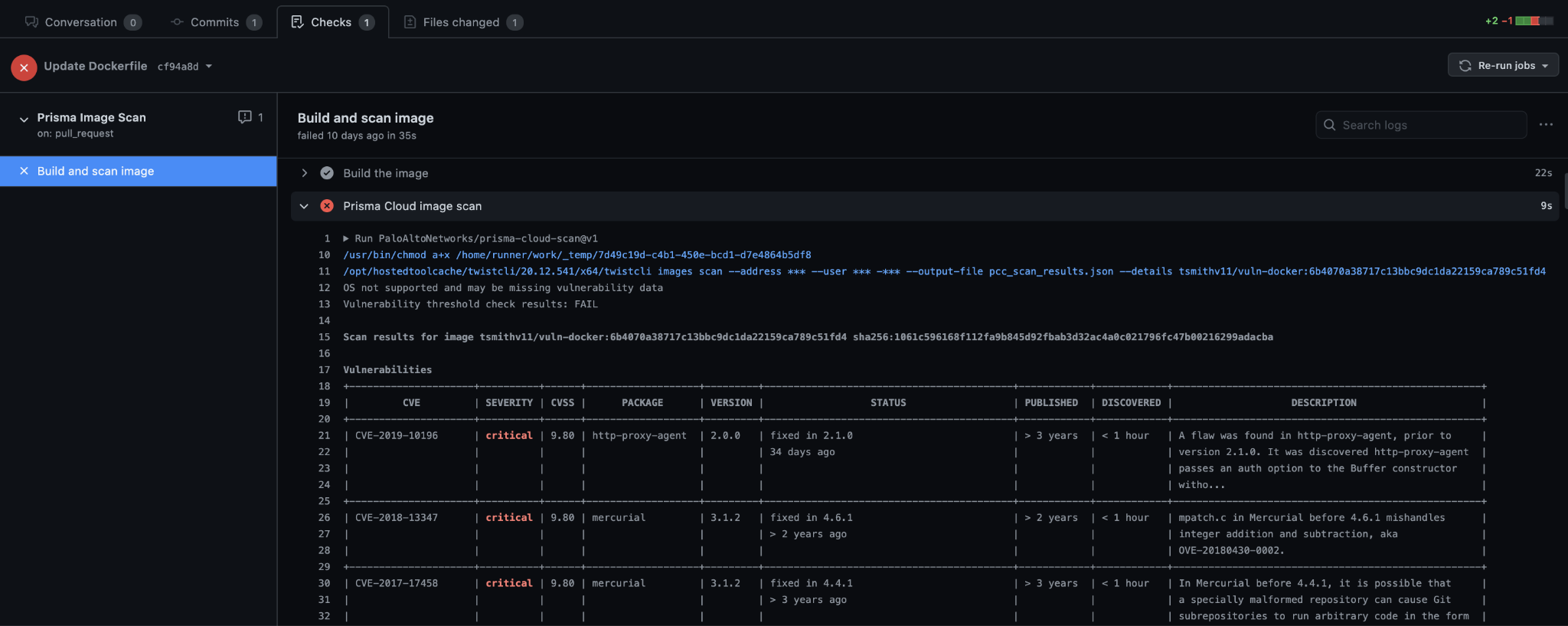
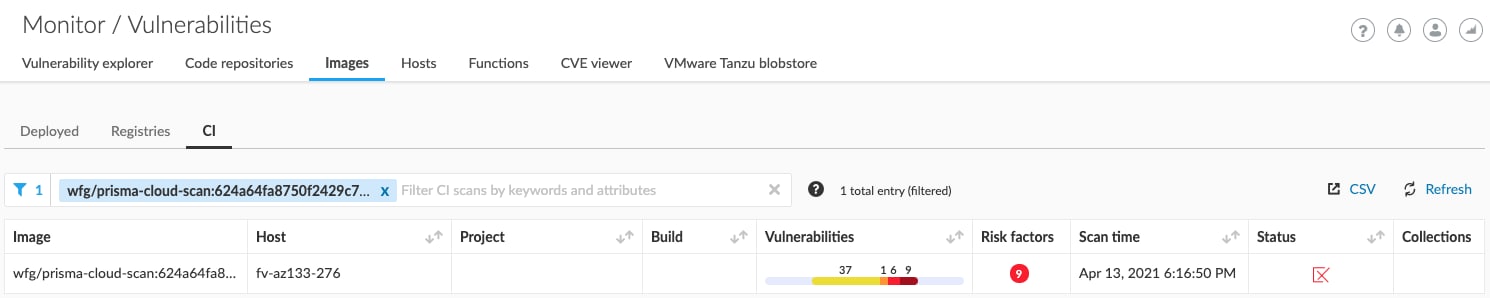
Optionally, you can have your vulnerabilities and compliance violations sent to your repository’s code scanning alerts for easy tracking. To do this, use GitHub’s upload-sarif action to upload the file containing the scan results in SARIF by adding the following after the image scan step.
- name: Upload SARIF file
if: ${{ always() }}
uses: github/codeql-action/upload-sarif@v1
with:
sarif_file: ${{ steps.scan.outputs.sarif_file }}
This provides a central place in your repository to view the currently-open vulnerabilities and compliance violations. Once these issues are addressed, for example, if a package is upgraded removing a vulnerability, the alert will be cleared automatically after you scan the updated image.
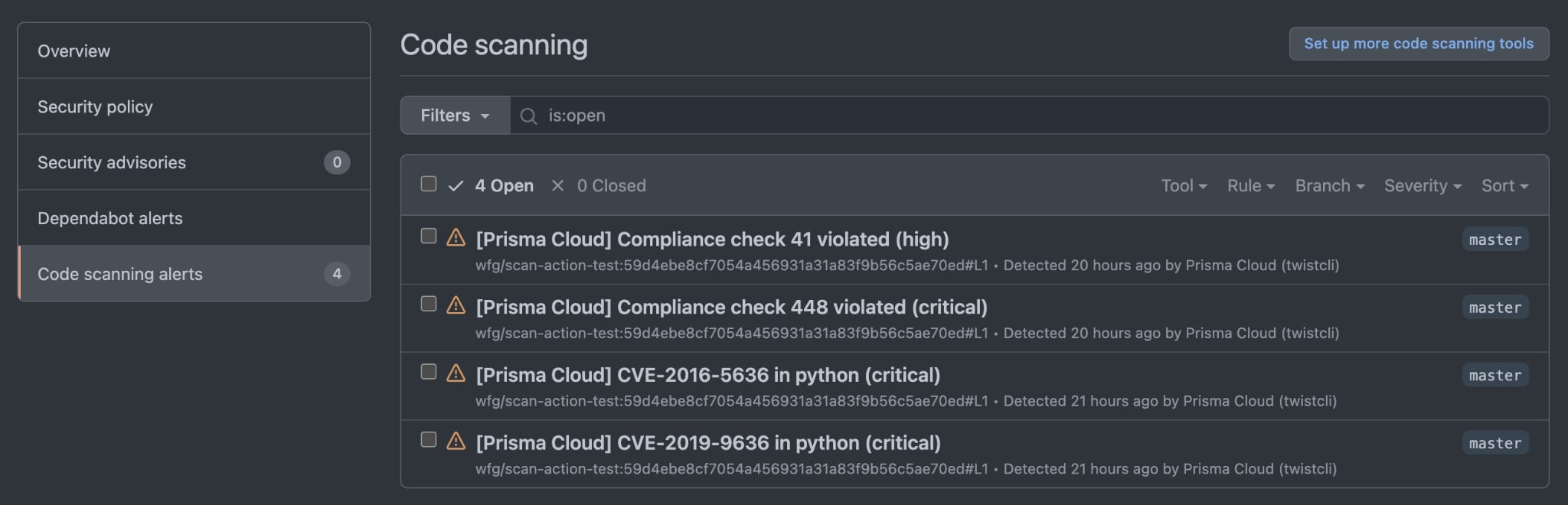
Available Now in the GitHub Marketplace
GitHub Actions can be leveraged to create fully automated workflows, including CI/CD pipelines. Together with Prisma Cloud image scanning, development teams can build, secure and deploy their applications all from GitHub. Access our Action from the GitHub Marketplace.
To learn more about this and our other native integrations, see our integration documentation.
Related Blogs
Subscribe to Cloud Native Security Blogs!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.