Shift-Left with IaC Build Policies in Prisma Cloud
Infrastructure as Code (IaC) has become the most common method for building cloud environments – and for obvious reasons. You can create a complete infrastructure for your application in less than an hour.
Beyond the ability to quickly set up a new infrastructure using just code or scripts, IaC template files have other advantages, like easily tracking code changes and providing consistency in configuration across environments.
Following best practices such as AWS Well-Architected Framework or Azure Architecture Framework can help teams rapidly deliver stable, repeatable environments at scale that avoid manual configuration dependencies. However, it’s essential to implement visibility and real-time feedback for developers using IaC before deploying cloud environments containing security or compliance flaws. Prisma Cloud can help you do just that.
Build Policies in Prisma Cloud
Prisma Cloud IaC Build policies identify insecure configurations in your IaC templates, including:
- AWS CloudFormation Templates (JSON or YAML format).
- HashiCorp Terraform templates (HCL or JSON format).
- Kubernetes App manifests (JSON or YAML format).
This helps ensure security issues are identified before actual resources are deployed in runtime environments. Build policies also include remediation instructions on how to fix particular security issues once they are detected. Here’s how:
Integrated Plugins/Extensions
Prisma Cloud DevOps plugins provide real-time feedback for DevOps/developers, enabling them to scan and fix security issues directly in their DevOps processes, going from integrated developer environment (IDE) → Git Repository → CI/CD without needing any additional security tools to detect problems.
Install and configure the Prisma Cloud plugins for popular IDEs such as VScode and IntelliJ; Source Control Management systems such as Github and GitLab; and CI/CD tools such as Jenkins, CircleCI, Azure DevOps and GitLab.
Prisma Cloud IaC API
Interact with the Prisma Cloud IaC scanning API endpoint using tools such as Curl, shell scripts, or Postman to inspect IaC templates. The Prisma Cloud team recommends that you use the published plugins/extensions to perform IaC scanning, but you can use the IaC APIs directly for integrating with custom tools or specific use cases. See the documentation for Prisma Cloud IaC Scan REST API for more detail.
IaC Scan via twistcli
If you prefer CLI for IaC scan functionality in your DevOps processes, we have recently added support for IaC Scans in twistcli. Currently, there are more than 100 build policies available out-of-the box that map to CIS standards for AWS, Azure and Google Cloud. In addition, you can create custom build policies that can be utilized during IaC scans.
An Example Policy
When you navigate to the Policy tab in Prisma Cloud, you will see filters to identify build policies with just an IaC scan component or “run and build” policies that include both relational query language (RQL) rules and IaC scan rules. In this example, I’ve chosen to surface Kubernetes policies.
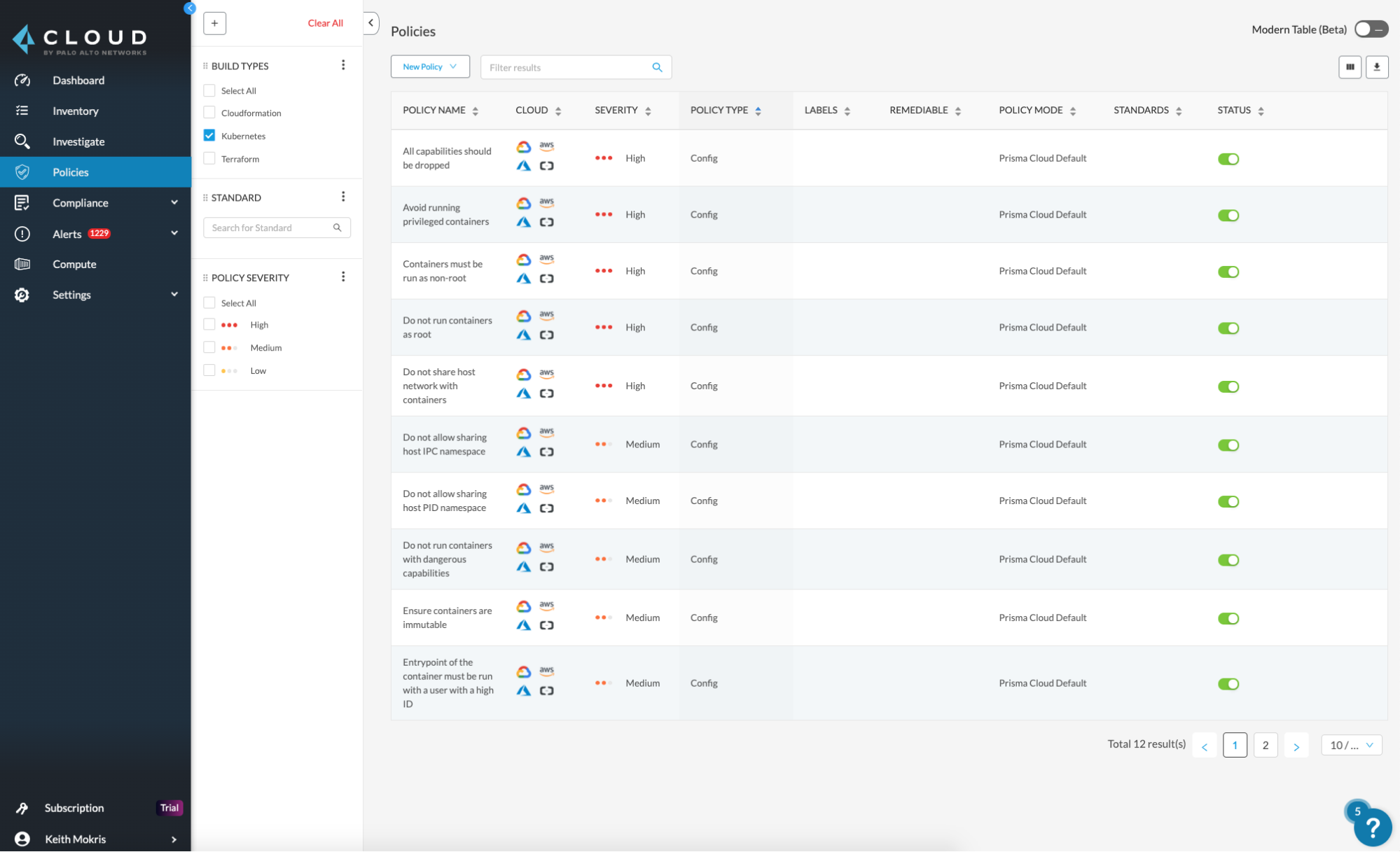
Next, you are shown all policies, which cloud platform they can cover and additional details like policy severity. In my example, I am going to add a policy on running privileged containers, as shown in the screenshot below:
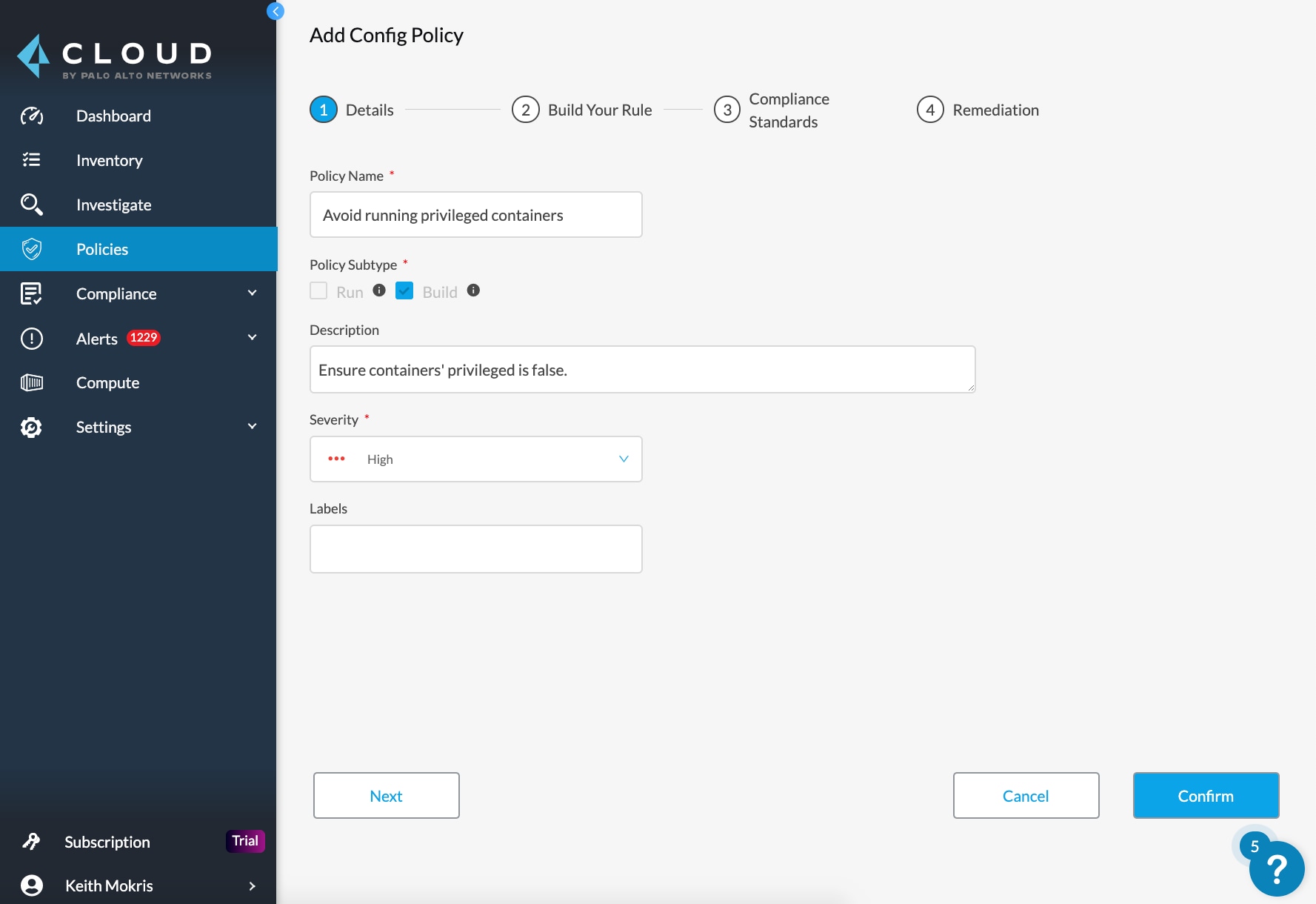
More Prisma Cloud Capabilities
Support for Terraform 0.12
We have also added support for new Terraform 0.12 features – new expression syntax, iteration constructs and generalized type systems. A new, improved IaC scan now supports multiple file scans as zip archives, multiple modules, custom variables files and runtime variables.
GitLab Plugins
We have also released two plugins for GitLab. The GitLab SCM plugin offers IaC scan check during merge request creation and updates. The GitLab CI/CD plugin offers IaC scan during GitLab pipelines as a custom task. Like all our other Prisma Cloud DevOps plugins for CI/CD, GitLab plugins allow users to set pipeline failure criteria to include security scans as a pass or fail step in the pipeline.
The Importance of Integration
The benefits of IaC for DevOps are well known. It’s important to ensure your new infrastructure is secure and compliant as early as possible, especially since detecting security issues or misconfigurations in the early build stages can save significant resources and greatly reduce the security burden on SecOps. When choosing security solutions for IaC, make sure they integrate with your current pipeline to avoid losing the automation and agility you’ve already built into your daily DevOps workflows. You can read more about the risks and benefits of IaC templates in the spring 2020 Unit 42 Cloud Threat Report.
Related Blogs
Subscribe to Cloud Native Security Blogs!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.